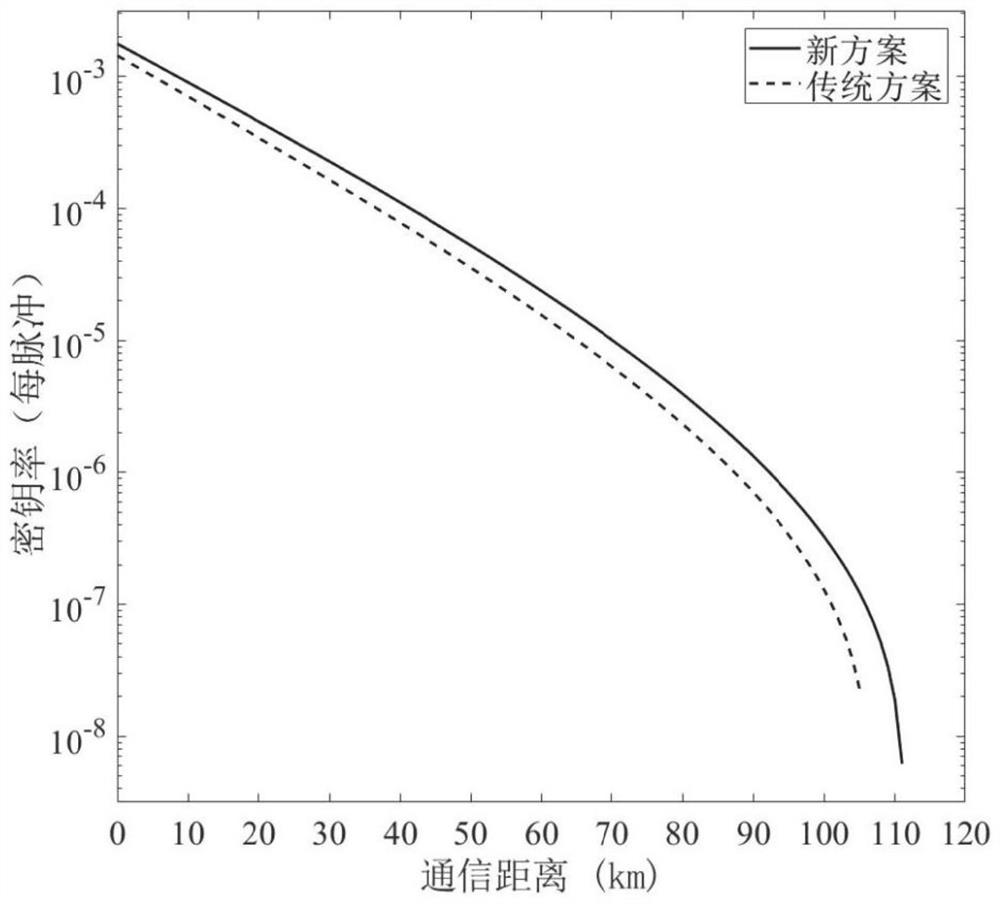
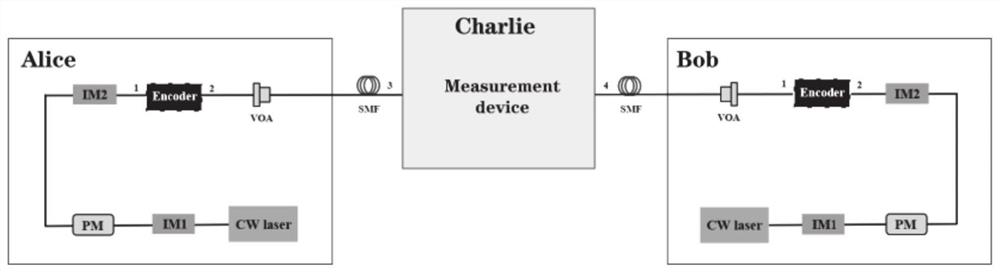
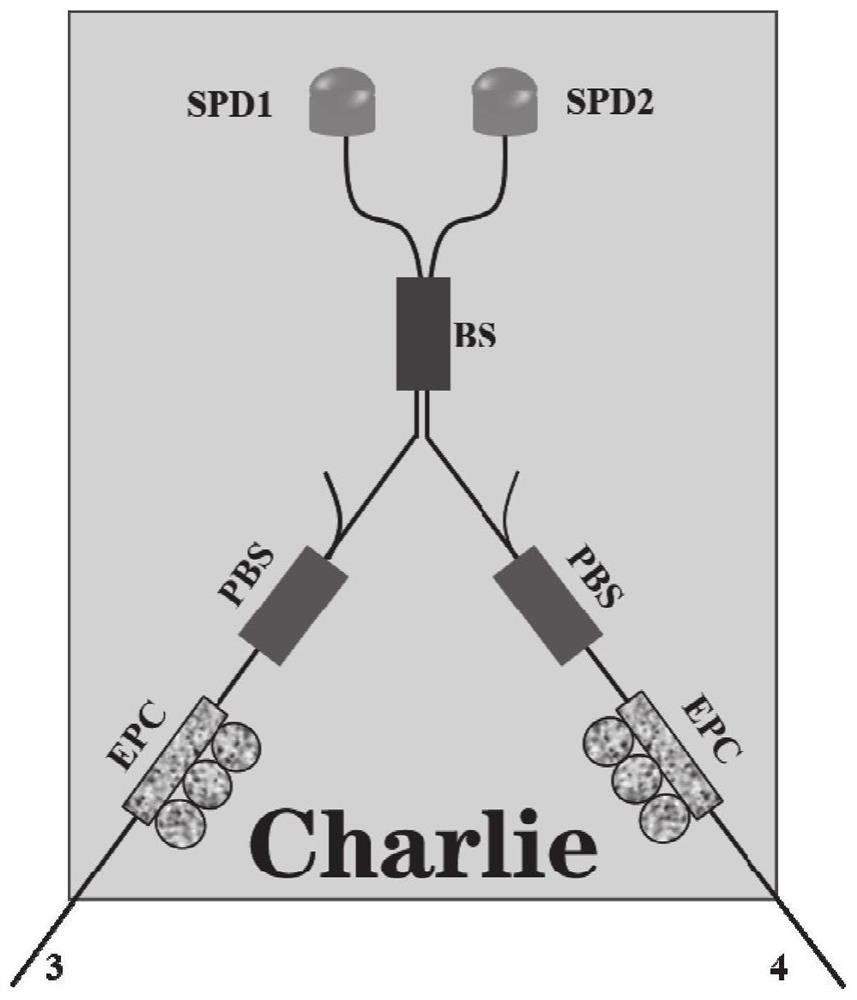
Phase post-selection-based decoy state MDI-QKD method and system
A decoy state and post-selection technology, applied in key distribution, can solve the problems of constraints and the upper limit of single-photon phase inversion bit error rate, and achieve high key rate, which is beneficial to long-distance quantum key distribution. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0058] In the traditional decoy state MDI-QKD system, the state of weakly coherent state (WCS) light source emitting pulse can be expressed as a form related to intensity μ and phase θ:
[0059]
[0060] where |m> denotes the m photon state. According to the assumption of protocol security, the phase θ of Alice and Bob's pulses is required to be randomized in the range of (0, 2π] and not published.
[0061] In the decoy-state MDI-QKD system based on phase post-selection provided in this embodiment, Alice and Bob at the light source end respectively send a series of strong reference pulses, and each strong reference pulse is followed by a signal pulse (signal pulse can be split from a strong reference pulse), then the states of the signal pulses of Alice and Bob can be expressed as:
[0062]
[0063]
[0064] where a and b represent Alice and Bob at the source end, j represents the time window of the jth pulse sent, γ represents the public phase related to the strong ...
Embodiment 2
[0082] This embodiment is applicable to a polarization encoding system.
[0083] The system consists of three parts: Alice, Bob and Charlie. Alice and Bob, as the sender, have the same structure and send pulses to the third party Charlie at the same time. As the measuring party, Charlie performs Bell state measurement on the received pulse pair, and Charlie can also be an untrustworthy eavesdropper (Eve).
[0084] The difference with Embodiment 1 is:
[0085] The Charlie detection structure adopts such as Figure 5 In the structure shown, the detection end includes an electrically controlled polarization controller respectively connected to each light source end, a beam splitter connected to two electrically controlled polarization controllers, and two polarization beam splitters connected to both beam splitters, Each polarizing beam splitter is connected to two independent single-photon detectors. Encoding modules can be used as Image 6 The Sagnac interferometer structur...
Embodiment 3
[0100] A decoy state MDI-QKD method based on phase post-selection, from the light source side, includes the following steps:
[0101] Modulate multiple strong reference pulses, and follow each strong reference pulse with a signal pulse of random intensity adjacently; keep the data under the measurement results of the effective response, and discard other data;
[0102] Carry out base vector comparison, retain the corresponding data when both light sources choose Z base vector, and obtain a string of bits for generating the original key, and other data are used for decoy state estimation;
[0103] Publish the signal pulse intensity when the Z base vector is not selected at both light source ends;
[0104] According to the published signal pulse strength, publish the private phase of the first decoy state pulse in the X base vector sent by both light source ends;
[0105] Select the signal pulse pairs that meet the set conditions in the private phase to form a subset,
[0106]...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com