Data privacy protection and security search method in cloud environment
A data privacy and cloud environment technology, applied in digital data protection, network data retrieval, other database retrieval, etc., can solve problems such as unable to meet the needs of fast and high-precision search, difficult to meet the needs of big data applications, and achieve the effect of preventing leaks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to facilitate the understanding of those skilled in the art, the present invention will be further described below in conjunction with the embodiments and accompanying drawings, and the contents mentioned in the embodiments are not intended to limit the present invention. The present invention will be described in detail below in conjunction with the accompanying drawings.
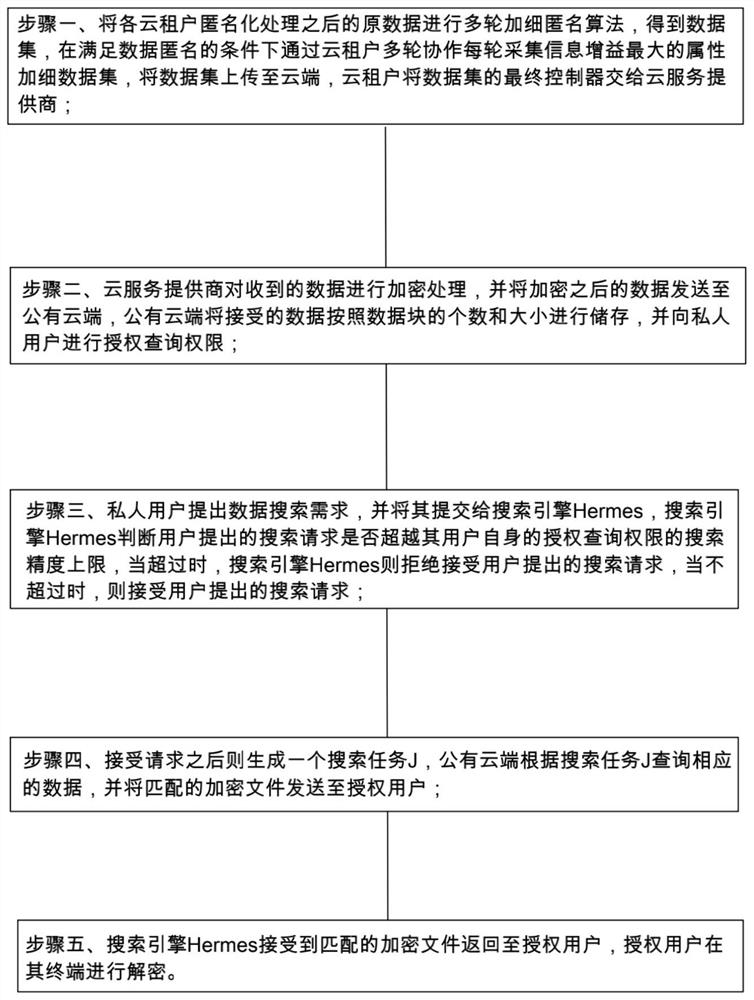
[0029] Such as figure 1 As shown, a method for data privacy protection and safe search in a cloud environment provided by the present invention includes the following steps: Step 1: Perform multiple rounds of fine-grained anonymization algorithms on the original data after each cloud tenant has been anonymized to obtain a data set , under the condition of satisfying data anonymity, through multiple rounds of cloud tenant collaboration, each round collects the attribute with the largest information gain and refines the data set, uploads the data set to the cloud, and the cloud tenant hands o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com