Dll injection detection method based on memory forensics
A technology of memory forensics and detection methods, applied in the field of dll injection detection based on memory forensics, can solve problems such as inability to obtain effective digital evidence, and achieve the effect of good versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to clearly and completely describe the technical solutions in the embodiments of the present invention, the present invention will be further described in detail below with reference to the accompanying drawings in the embodiments.
[0034] Step 1 The process of obtaining the memory dump file is as follows:
[0035] Take Windows 10 64-bit system host as an example.
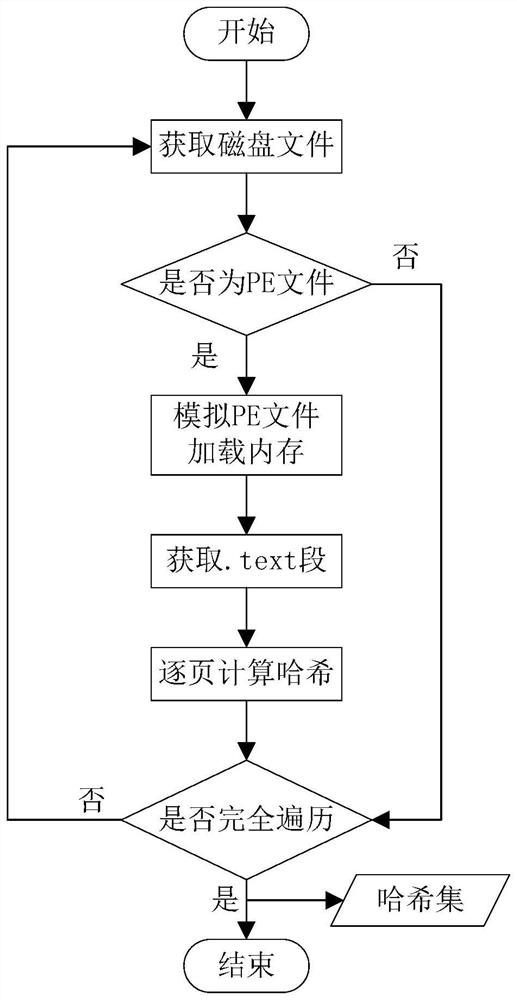
[0036] The flow chart of calculating the hash set of the disk PE file according to the embodiment of the present invention is as follows: figure 1 shown, including the following steps.
[0037] Step 1-1 Traverse the file system to obtain all files;
[0038] Steps 1-2 determine whether the file is a PE file;
[0039] Steps 1-3 simulate the loading of the PE file into the memory, and calculate the hash value of the text code segment in units of 0x1000;
[0040] Steps 1-4 integrate and save the hash values into a hash set file.
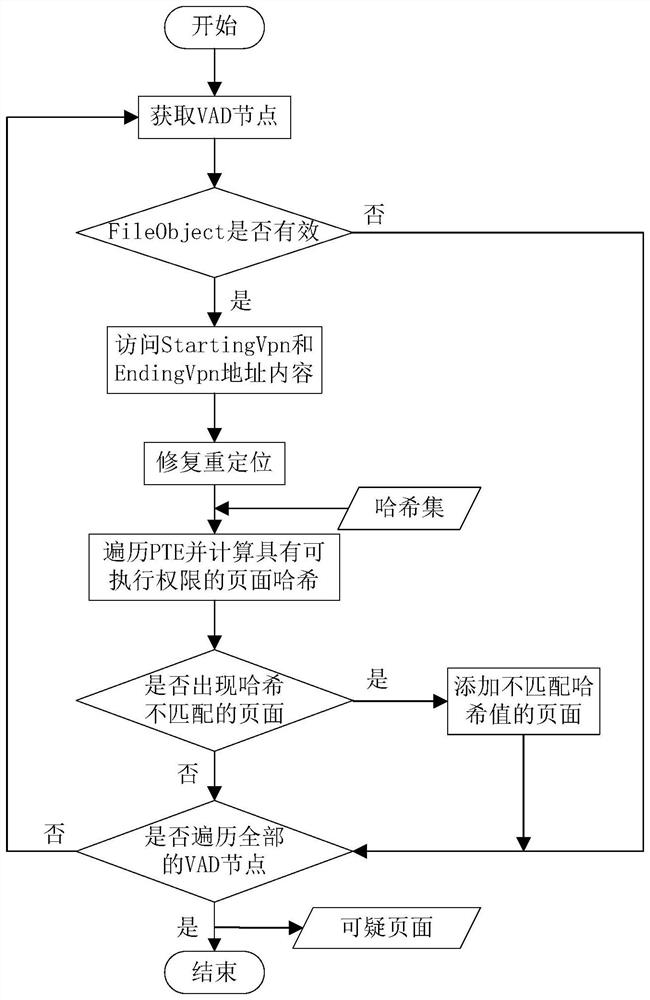
[0041] Step 2 Obtain the dump file of the physical memory of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com