Computer system of bottom identity identification and method therefor
A computer system and identity authentication technology, applied in the field of the underlying identity authentication computer system, can solve problems such as heavy workload, limitation, complexity, etc., and achieve the effect of powerful supporting functions, practical realization of value, and making up for security loopholes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
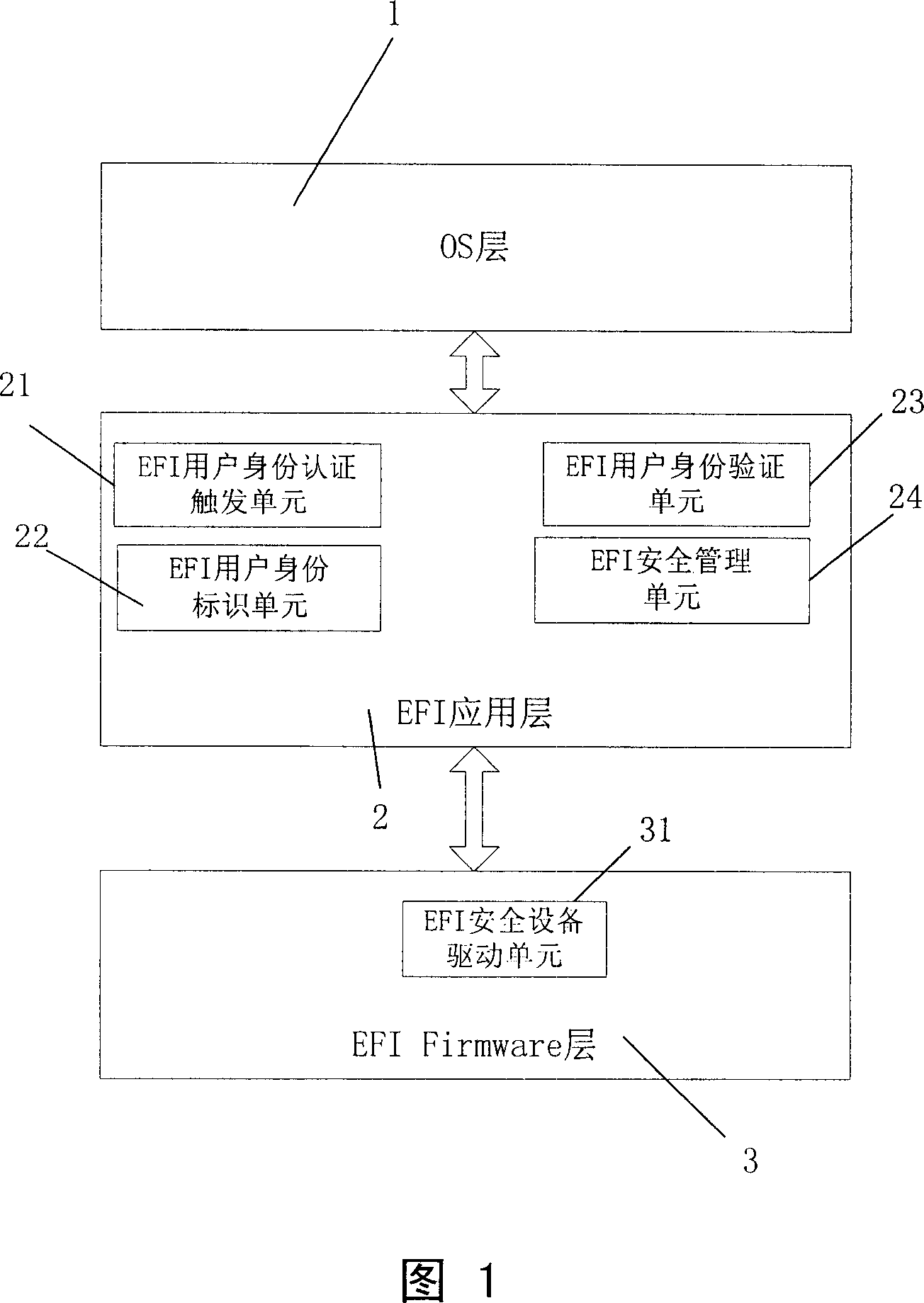
[0084] As shown in Figure 1-2, the underlying identity authentication computer system in this embodiment includes hardware and software, and the hardware includes a motherboard, a central processing unit (CPU), memory, hard disk and peripherals.
[0085] The motherboard and the CPU are respectively a motherboard and a CPU supporting the EFI specification, and the hard disk includes an EFI memory storing the EFI specification.
[0086] The hardware also includes a safety device, the safety device is a peripheral device connected to the local control bus, and the device has a safe protected storage area for supporting the safe storage of user identity information. The device can be a USB-connected Ikey equipment, such as ikey USB key of SafeNet company, fingerprint reader, such as fingerprint identification system products of BIOSCRYPT (BII) company and other identity authentication hardware devices.
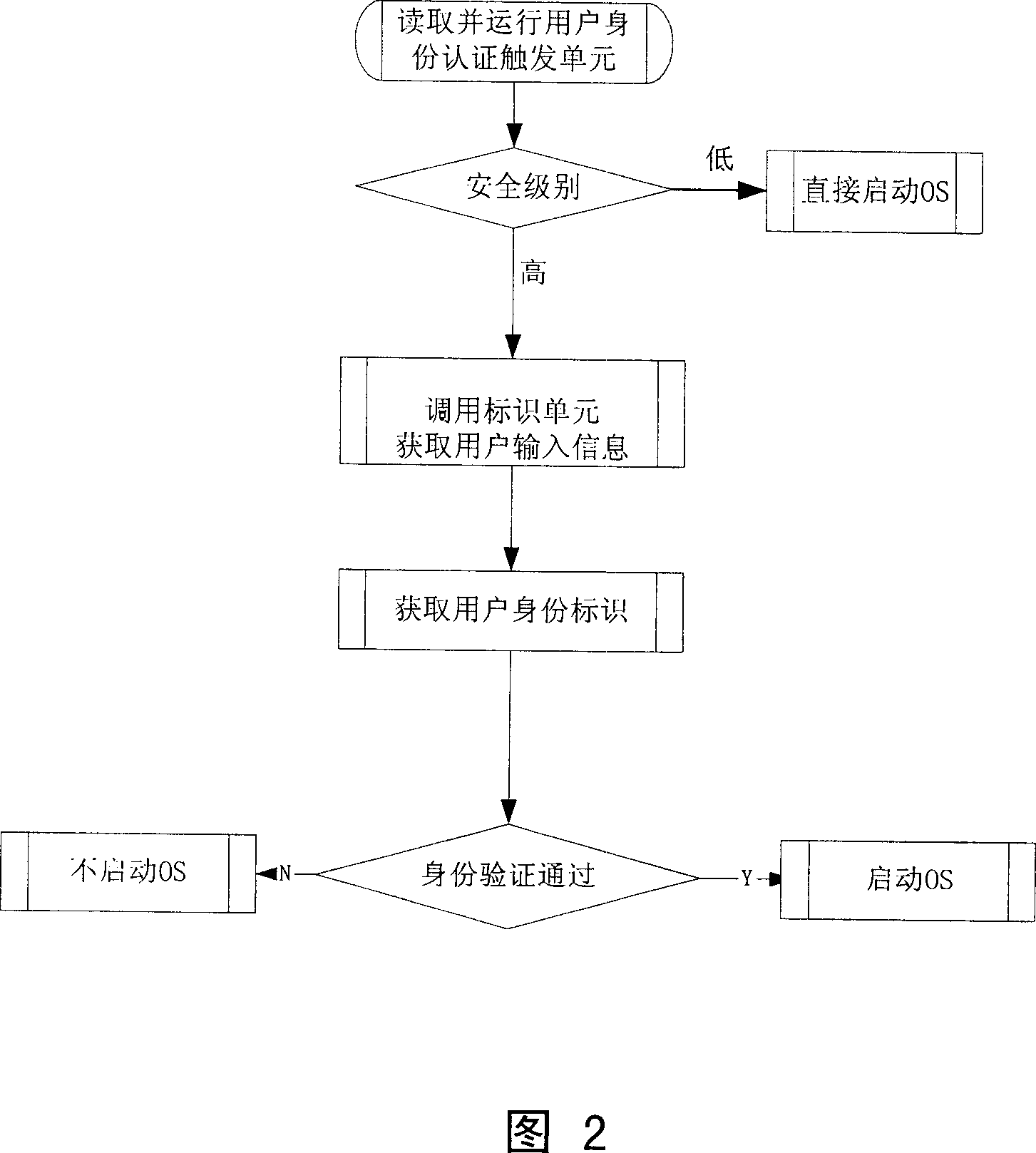
[0087] Described software comprises EFI Firmware layer 3, EFI application lay...
Embodiment 2
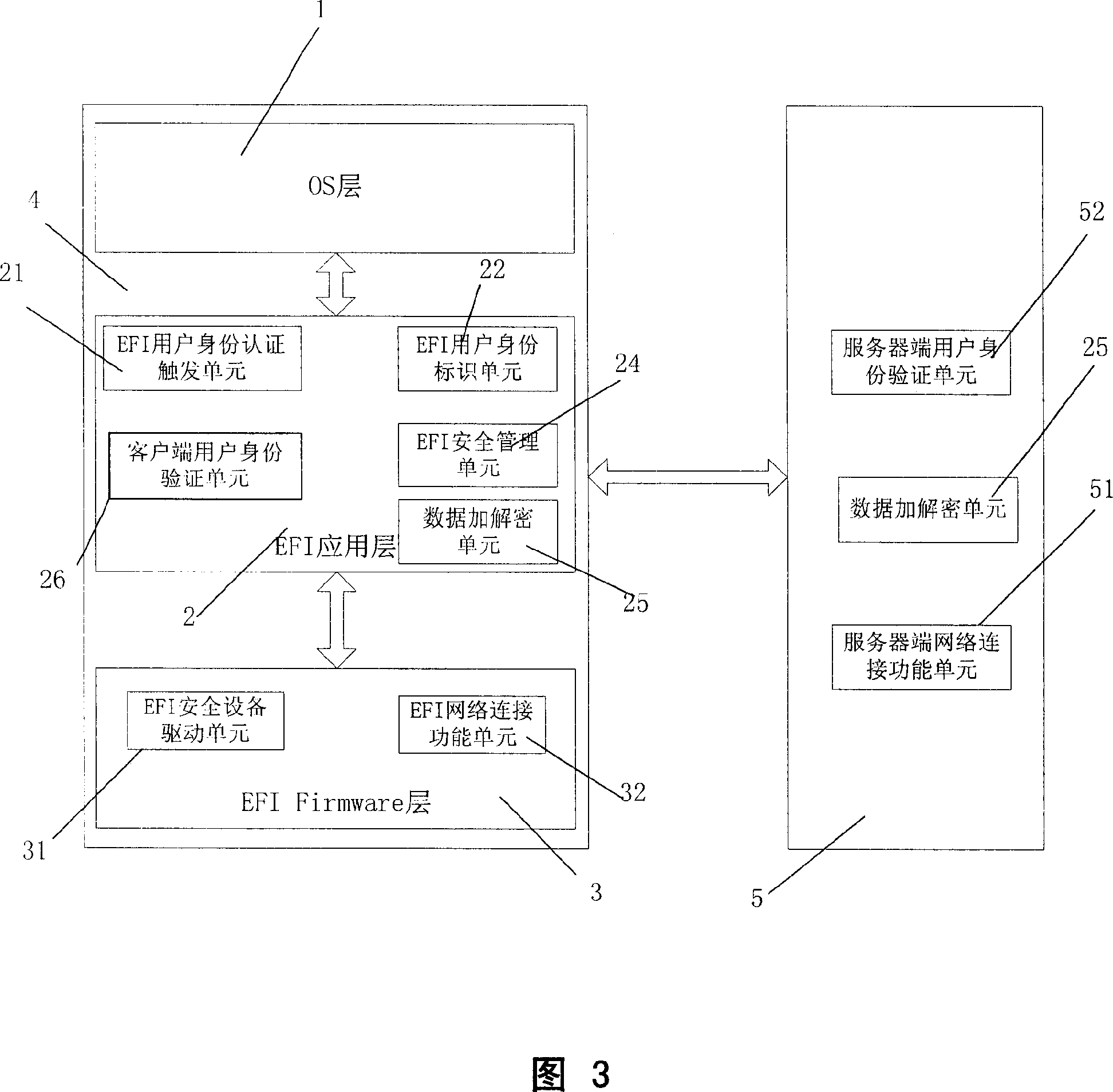
[0118] The present embodiment will be described in detail below in conjunction with accompanying drawings 3-6.
[0119] The underlying identity authentication computer system client 4 and server 5 of this embodiment.
[0120] The server end 5 is used for verifying the identity of the user in the remote network, it responds to the authentication request sent by the client end 4, decrypts the identity authentication information, and verifies the legitimacy of the information through the server end 5. The server end includes three units: the server end network connection function unit 51 , the server end user identity verification unit 52 , and the data encryption and decryption unit 25 .
[0121] The server-side network connection function unit 51 responds to the connection request of the client 4 through the network protocol TCP / IP unit, so that the client can access and control the server 5 .
[0122] The user identity verification unit 52, in response to the received authent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com