Security access device and method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
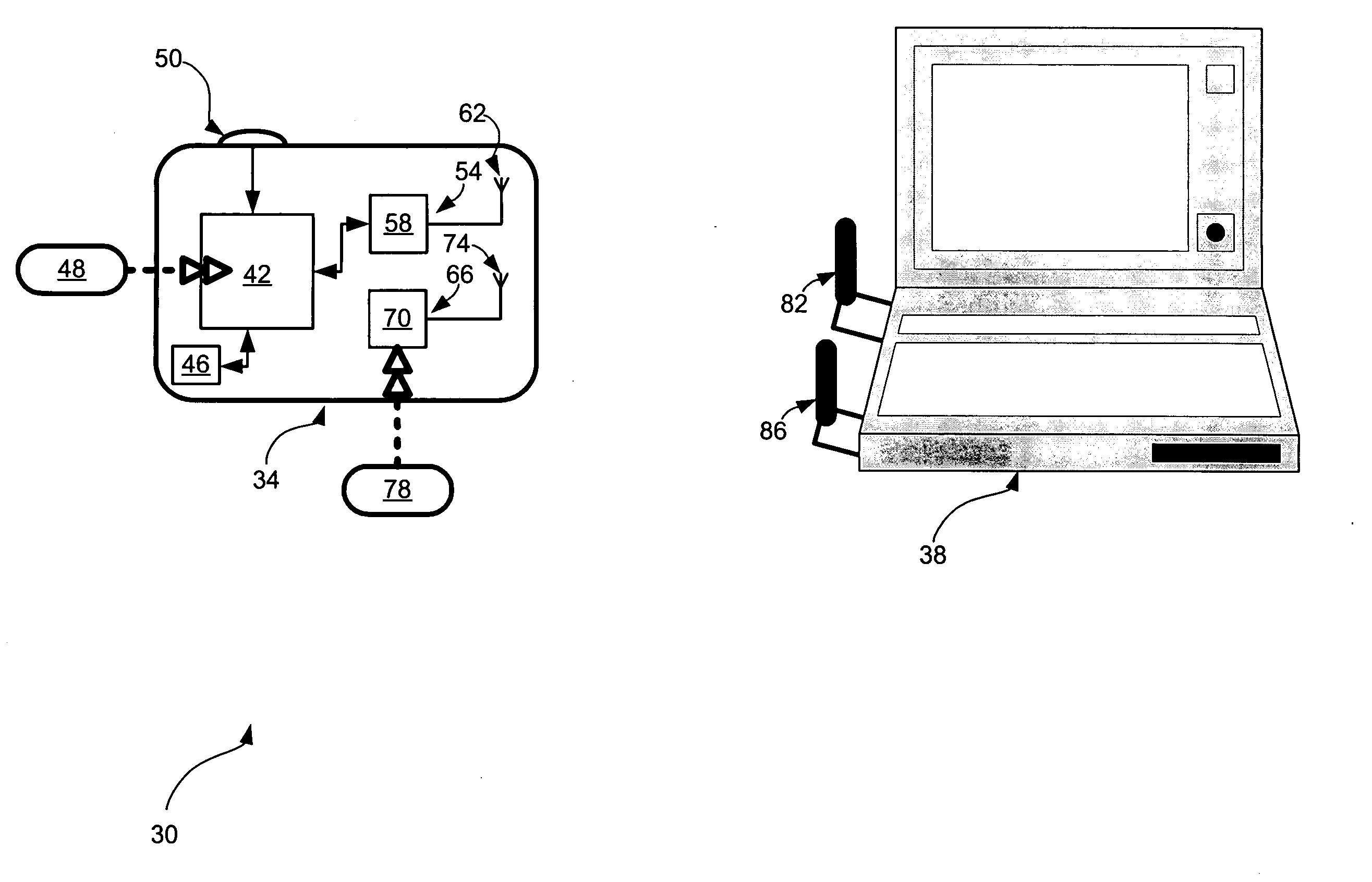
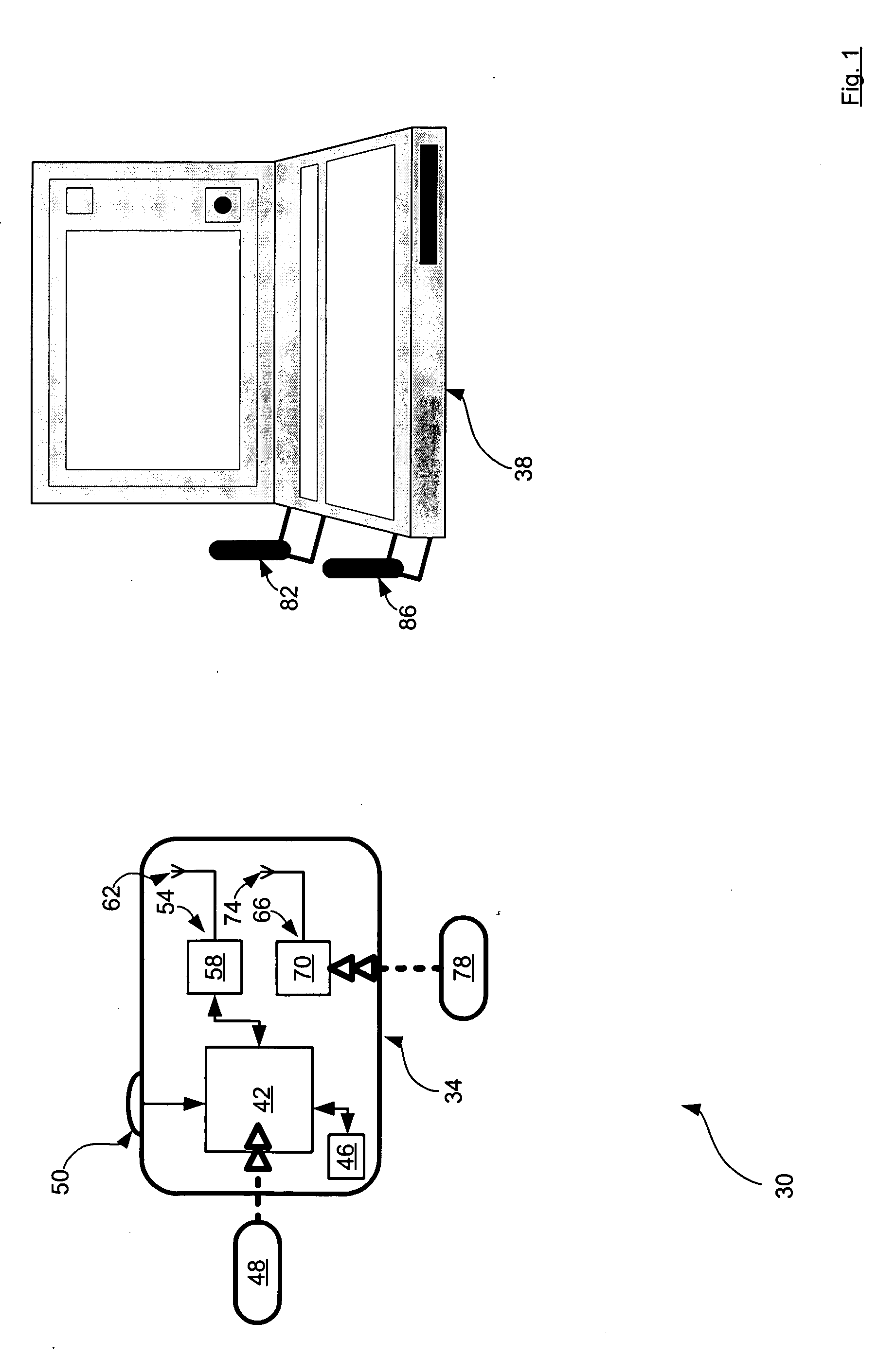
[0058] Referring now to FIG. 1, a security access system is indicated generally at 30. System 30 includes a security access device 34 and a laptop computer 38.
[0059] While not required, it is presently preferred that the form-factor of security access device 34 render device 34 portable—for example, being attachable to a key-chain, or able to fit easily into the user's pocket, or readily wearable by the user. As shown in FIG. 1, security access device 34 is represented in block-diagram format, and thus it is to be understood that the appearance and shape of device 34 is not particularly limited. As will be explained in greater detail below, the user of device 34 is able to use device 34 to gain and maintain access to computer 38.
[0060] Device 34 contains a microcontroller 42 that is powered from a self-contained power supply 46, such as a lithium battery. Microcontroller 42 includes a processing unit (not shown) and a persistent storage device (not shown) that stores operating ins...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com