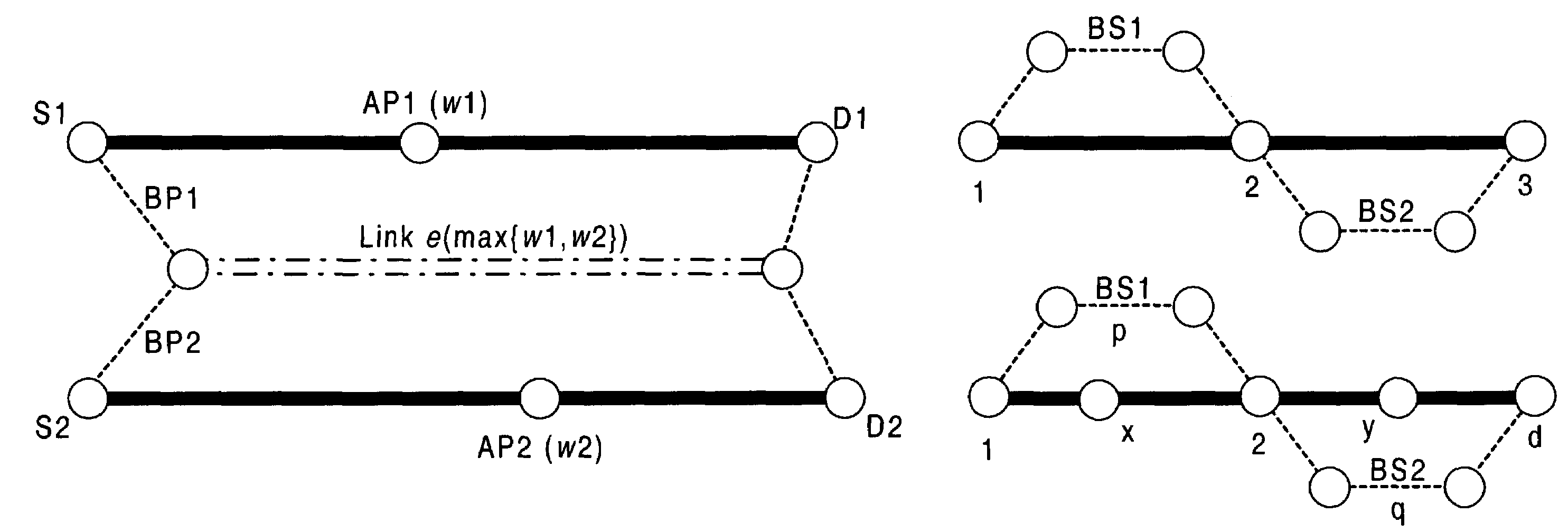
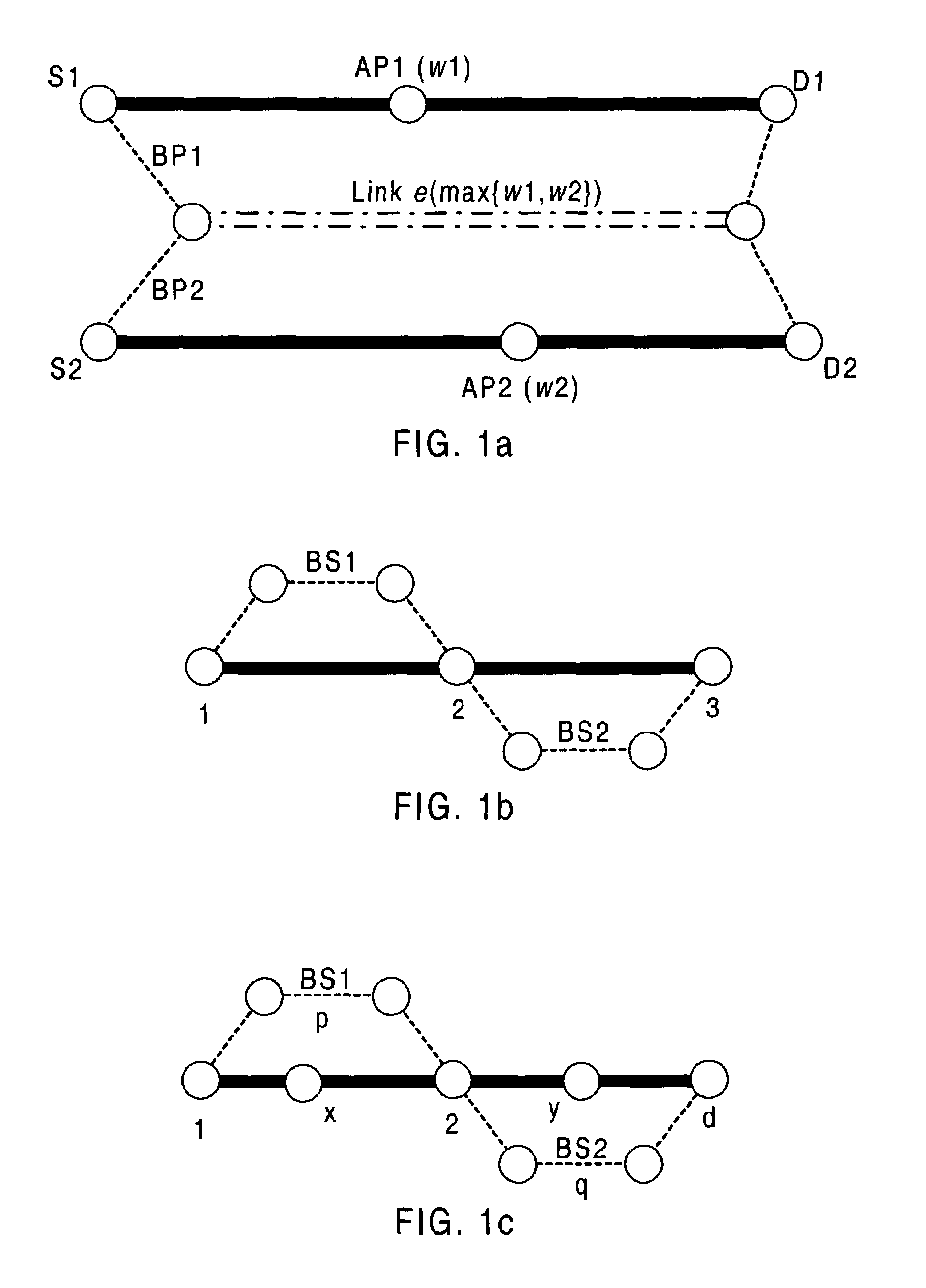
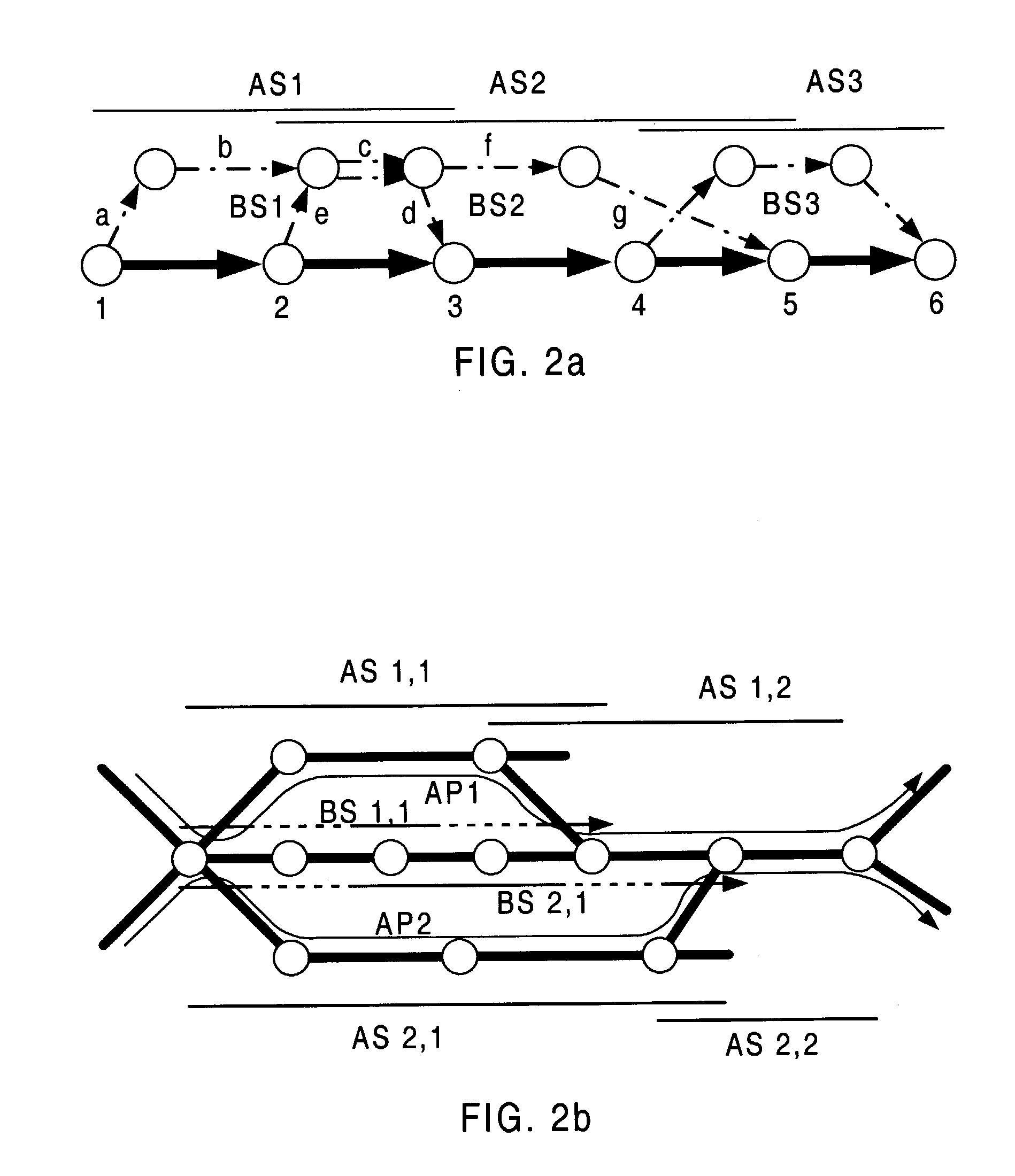
In general, protection schemes can recover more quickly as the detour is already determined (as long as the detour is not broken), but are less
bandwidth efficient than restoration schemes.
On the other hand, restoration schemes can survive one or multiple failures (as long as the destination is still reachable, and there is sufficient bandwidth), but they cannot guarantee the
recovery time (including the time to find a detour), and / or the amount of
information loss for real-time applications, making them unsuitable for mission-critical applications.
These issues are challenging because the objectives to optimize bandwidth usage,
algorithm complexity and recovery time often conflict with each other.
However, finding an optimal pair of link (or node) disjoint paths that minimizes the total bandwidth consumption by the request, given that
bandwidth sharing is possible, is an NP-hard problem.
In addition, the optimal pair, (if found, by using
branch-and-bound techniques), often includes a long BP (consisting of many “zero or super low cost” links on which the bandwidth allocated to existing BPs can be shared), and this results in a long recovery time.
Existing efforts in achieving maximal bandwidth efficiency often resort to integer
linear programming (ILP) which is not tractable / feasible for large-scale networks.
Other existing
heuristic approaches sacrifice bandwidth efficiency, or trade recovery time for bandwidth efficiency.
The former chooses a set of rings that can cover all the nodes in a mesh network, but the traffic carried on any uncovered links in the mesh network cannot be protected against failure.
Even for a
planar graph, it is difficult, if possible at all, to have small protection cycles (so that recovery can take place along shorter detours).
However, detours can also be long, and in addition, the number of p-cycles needed can be large, which requires complicated co-ordination amongst these p-cycles for the purpose of recovery.
More specifically, because it requires that the protection paths for all APs that terminate at a given
egress router be determined simultaneously, one cannot take
advantage of the bandwidth available somewhere else to support efficient dynamic establishment of connections.
This improves the bandwidth efficiency significantly, but results in longer detours and associated degradation of
signal transmission quality.
In addition, the bandwidth efficiency of both approaches, especially the first, can be low due to the need to find a detour for each link, and neither approach, especially the second, made any attempts to limit the length of the detour.
Again, only rudimentary exhaustive search algorithms (with
backtracking) and
heuristics were suggested, and no
performance results in terms of bandwidth efficiency, and recovery time (or the length of the detours) were provided.
But none of them contains, (or is supposed to contain), any implementation details such as algorithms or
performance results, and it is clear that much work needs to be done in exploring the
advantage of these protection schemes.
The bandwidth inefficiency problem is further exacerbated by the need to
upgrade the bandwidth on all the links in a SDH / SONET ring (called the “fork-lift” requirement).
In addition, detours (loopbacked routes) can be very long, which not only wastes bandwidth, but also affects
signal transmission performances such as
signal-to-
noise ratio (SNR) and bit-error-rate (BER), making all-optical data communications difficult.
As a variation of link or path protection, ring-based approaches generally are not
bandwidth efficient.
In addition, they do not adapt well to the changes in the
network topology due to their need to perform major reconstruction of the desired set of rings.
367-375, that they result in a significantly poor performance in terms of the ability to recover from subsequent failures.
As for existing non-ring based protection schemes, no existing schemes can achieve better bandwidth efficiency than shared path protection while having a much shorter
backup segment, as well as a scalable
algorithm.
 Login to View More
Login to View More  Login to View More
Login to View More