E-mail encryption transmitting-receiving system
A technology for sending and receiving systems and e-mails, applied in electrical components, transmission systems, digital transmission systems, etc., and can solve the problems of no detailed description of encryption algorithms, insecure AES algorithms, and inappropriate AES algorithms.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
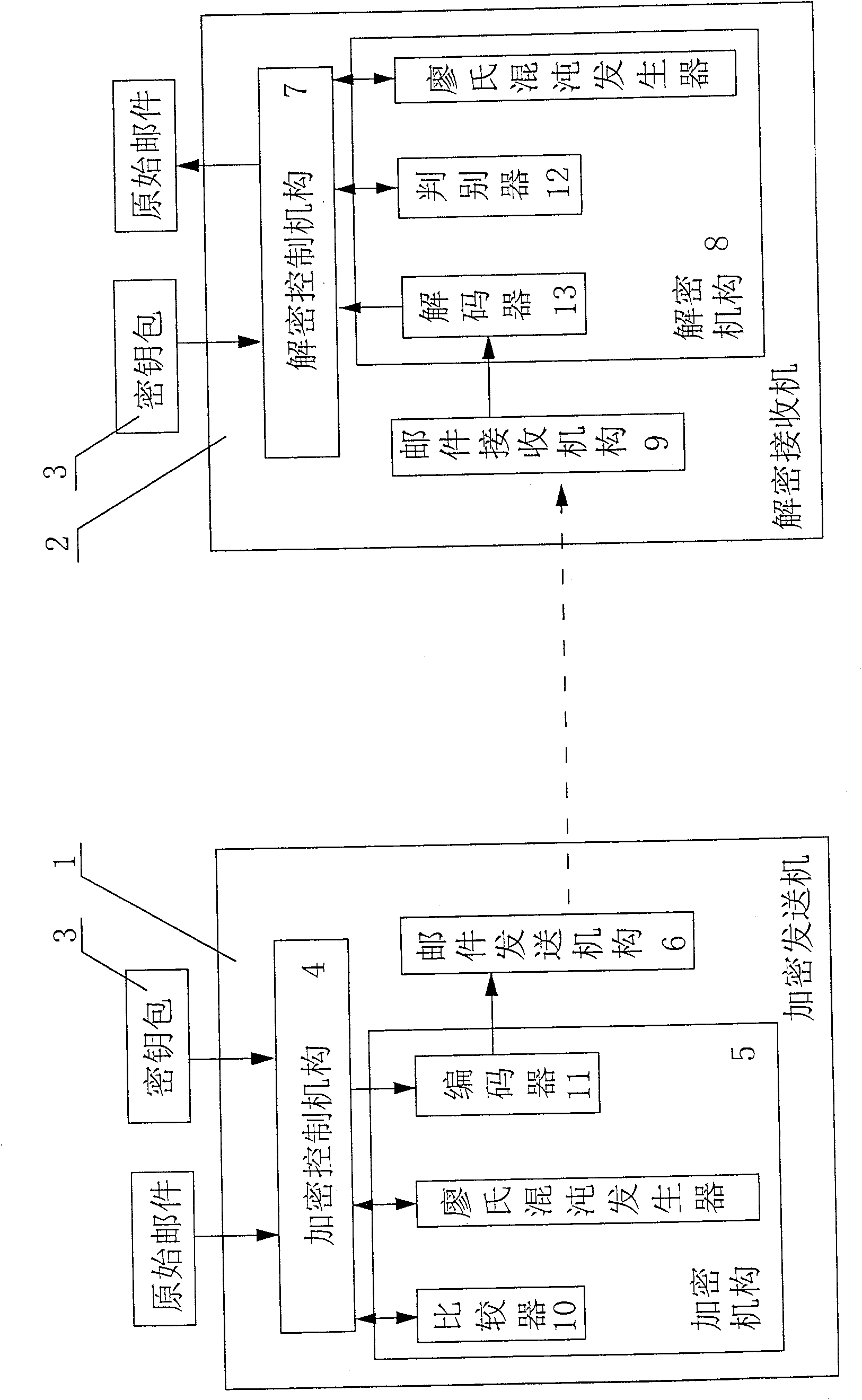
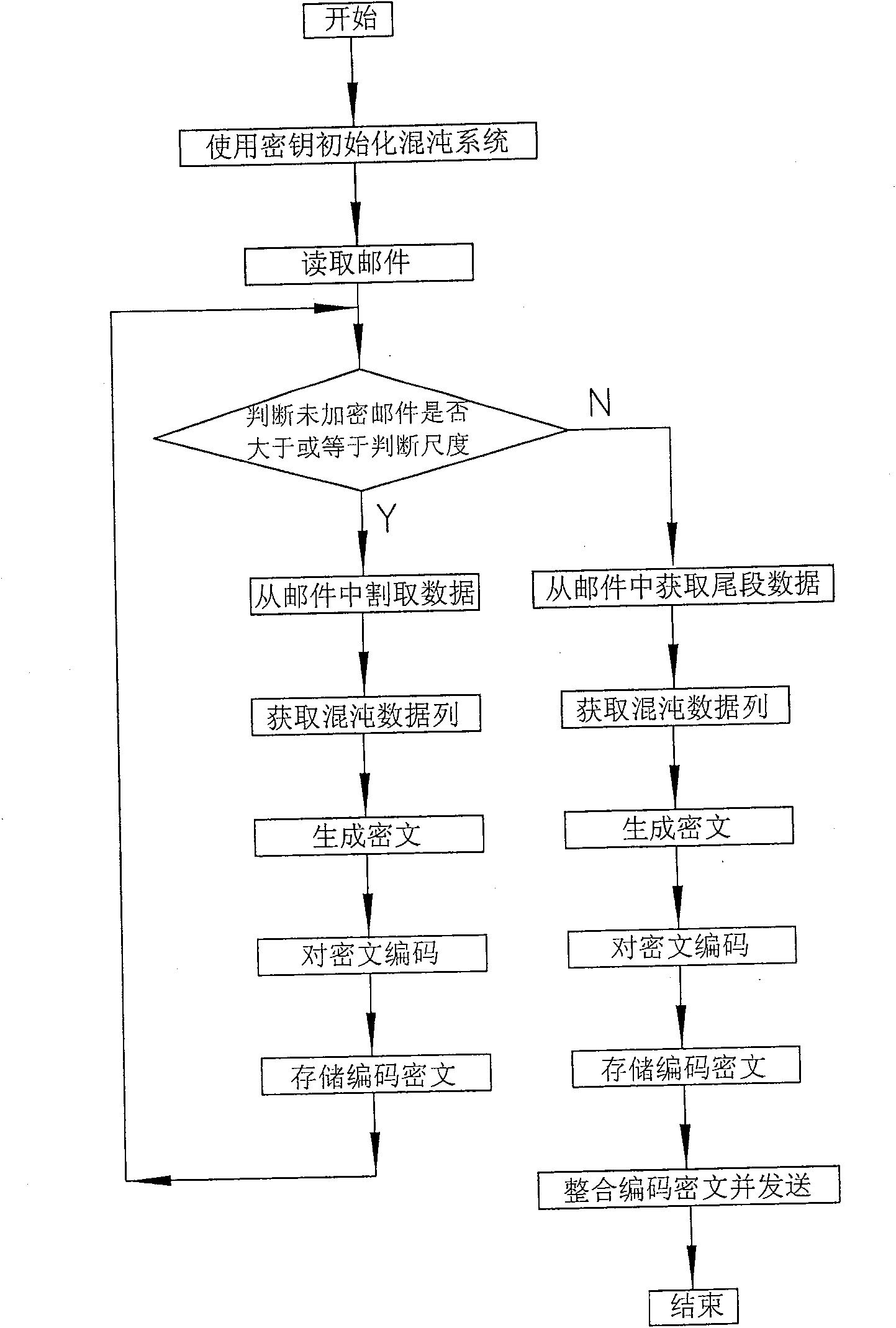
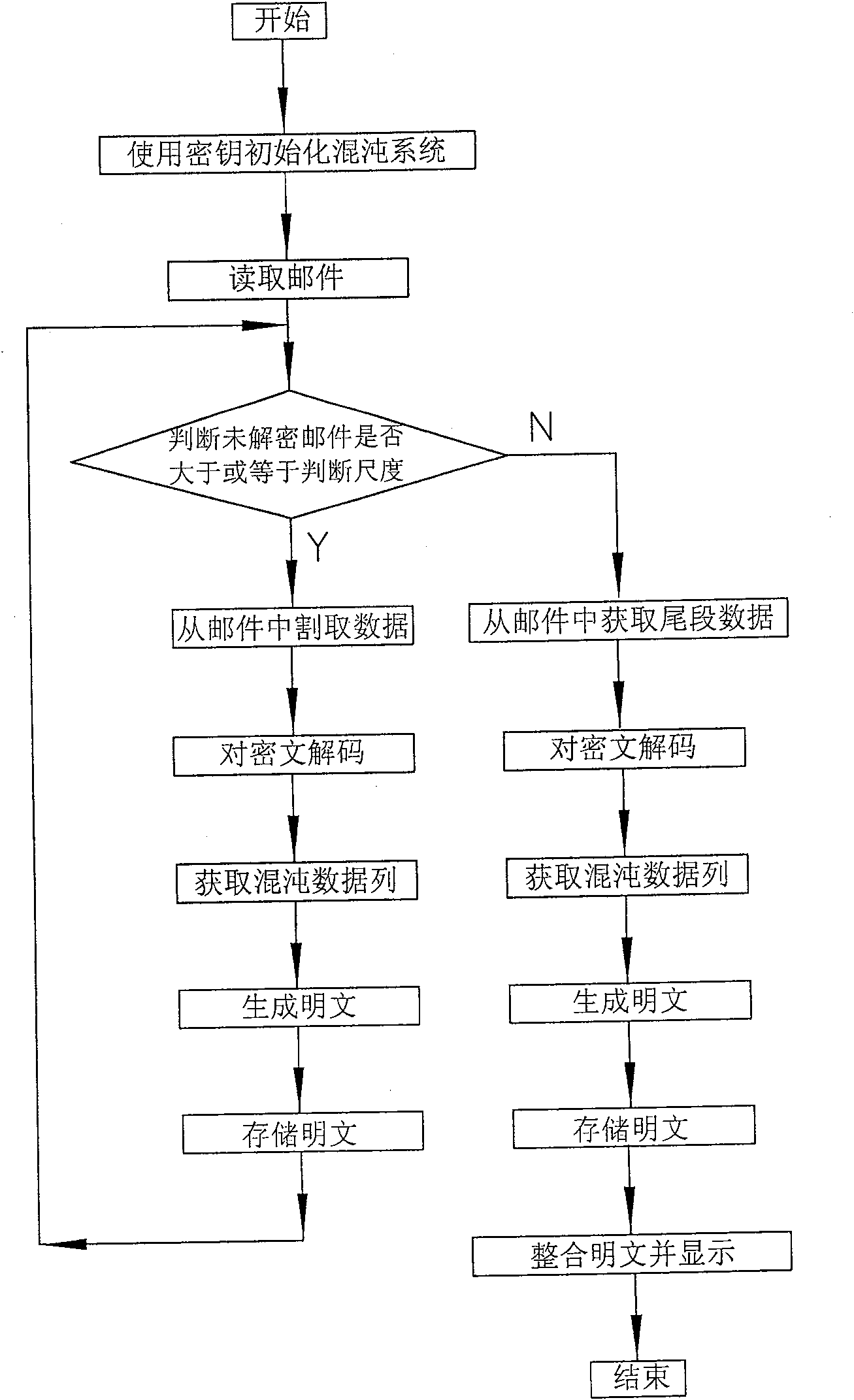
[0074] Such as figure 1 As shown, the present invention is a kind of electronic mail encryption sending and receiving system, is made up of encryption transmitter 1, decryption receiver 2 and key bag 3, and described encryption transmitter 1 is provided with encryption control mechanism 4, encryption mechanism 5 and mail The sending mechanism 6, wherein the encryption control mechanism 4 obtains the original mail, and reads the key in the key bag 3, and the output terminal of the encryption control mechanism 4 sends the key and the original mail to the encryption mechanism 5, and the encryption mechanism Liao's chaotic generator is installed in 5, and the Liao's chaotic generator generates the required chaotic sequence data. The encryption control mechanism 4 uses the chaotic sequence data to encrypt the mail information to obtain encrypted data, and then encodes the encrypted data and integrates them into encrypted data. package, the encryption control mechanism 4 sends the e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com