Transmission control protocol blocking module and soft switch method
A transmission control protocol and soft switching technology, applied in the field of security attack prevention technology TCP interception, can solve the problems of not being able to truly protect the server, running out of resources during the service period, and single working mode, saving memory and improving utilization. , the effect of flexible working mode
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Below in conjunction with accompanying drawing and specific embodiment, the present invention is described in further detail:
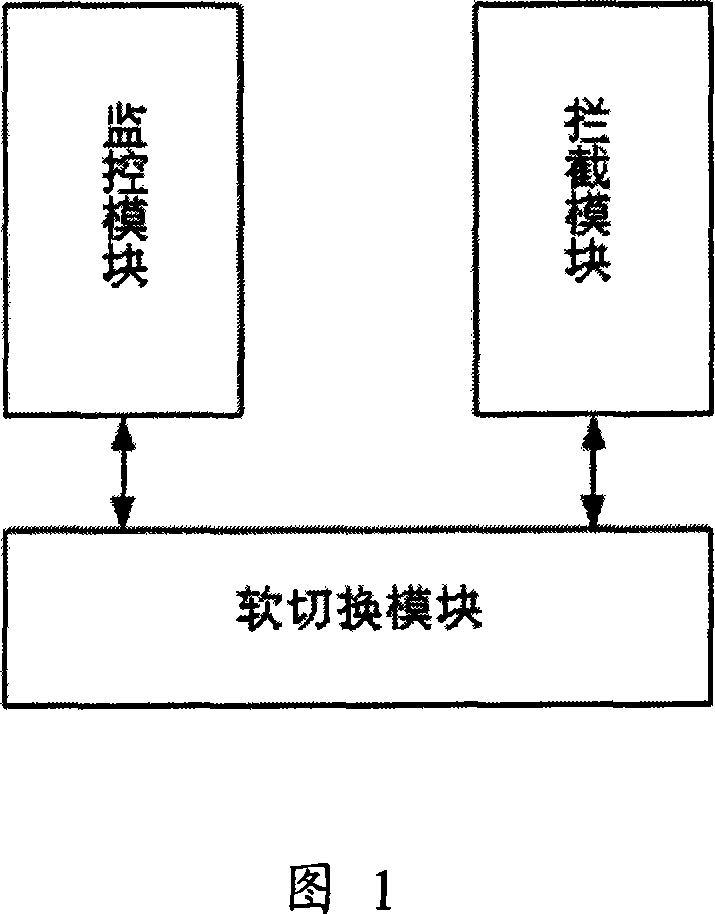
[0028] In the present invention, the router can freely switch the working mode of the TCP interception module according to the situation that it is attacked:
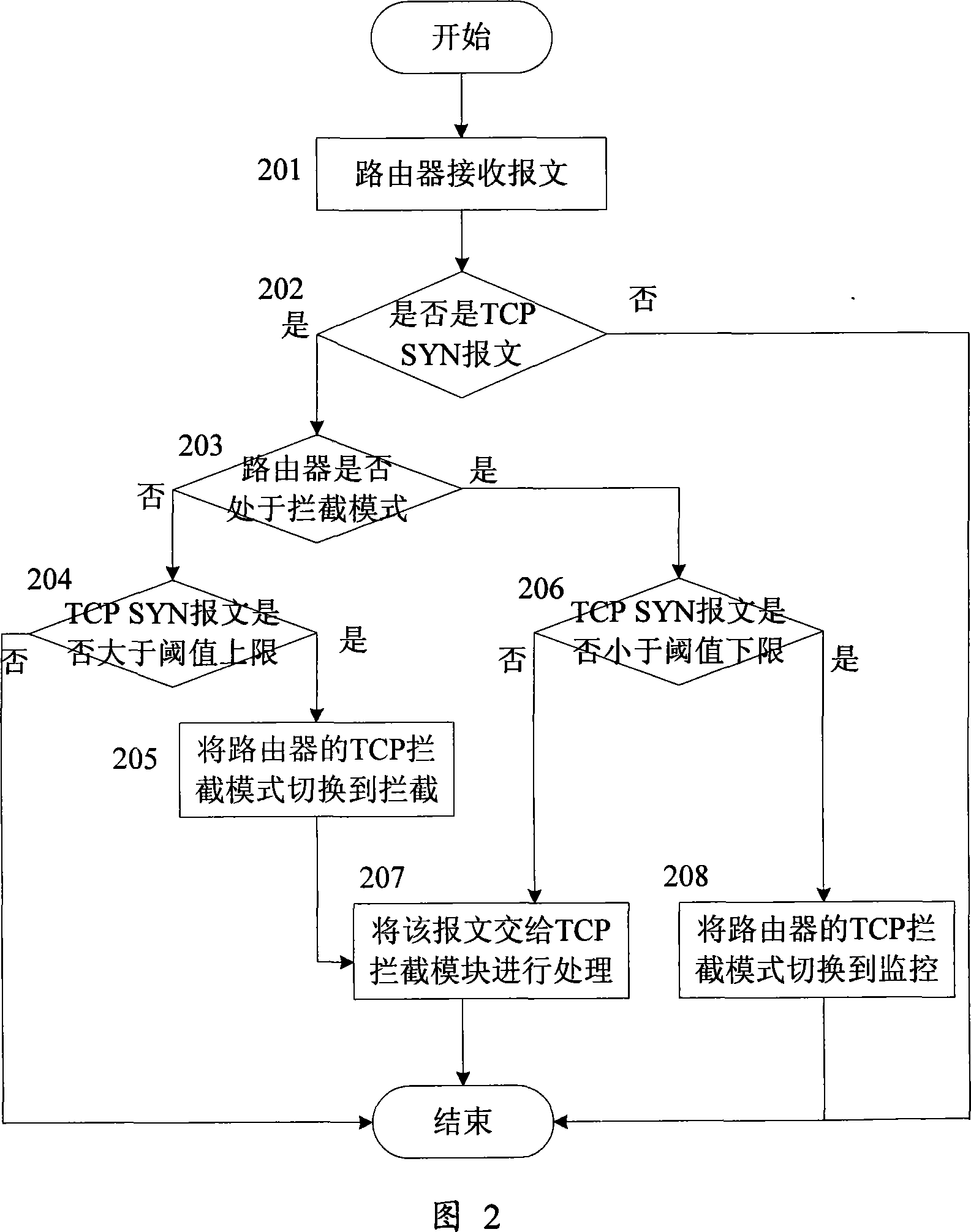
[0029] Monitoring mode: indicates that the router is in a non-attack state. The monitoring module monitors the TCP connection requests initiated by the external host to the internal server, and judges whether the router suffers a Attacks to external networks.
[0030] Interception mode: Indicates that the router has been attacked. The interception module will intercept the TCP connection request initiated by the external host to the internal server, and connect the longest (or random) semi-connection from the system, and then send a response message instead of the internal server. , reduce the initial timeout retransmission time to 0.5s, so that the overall timeout time saved by the sys...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com