Method for implementing network five defending locking system of transforming plant without person on duty
A five-proof locking and substation technology, applied in the transmission system, information technology support system, circuit, etc., can solve the problems that information cannot be shared, data security cannot be guaranteed, and operation information and data cannot be shared.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
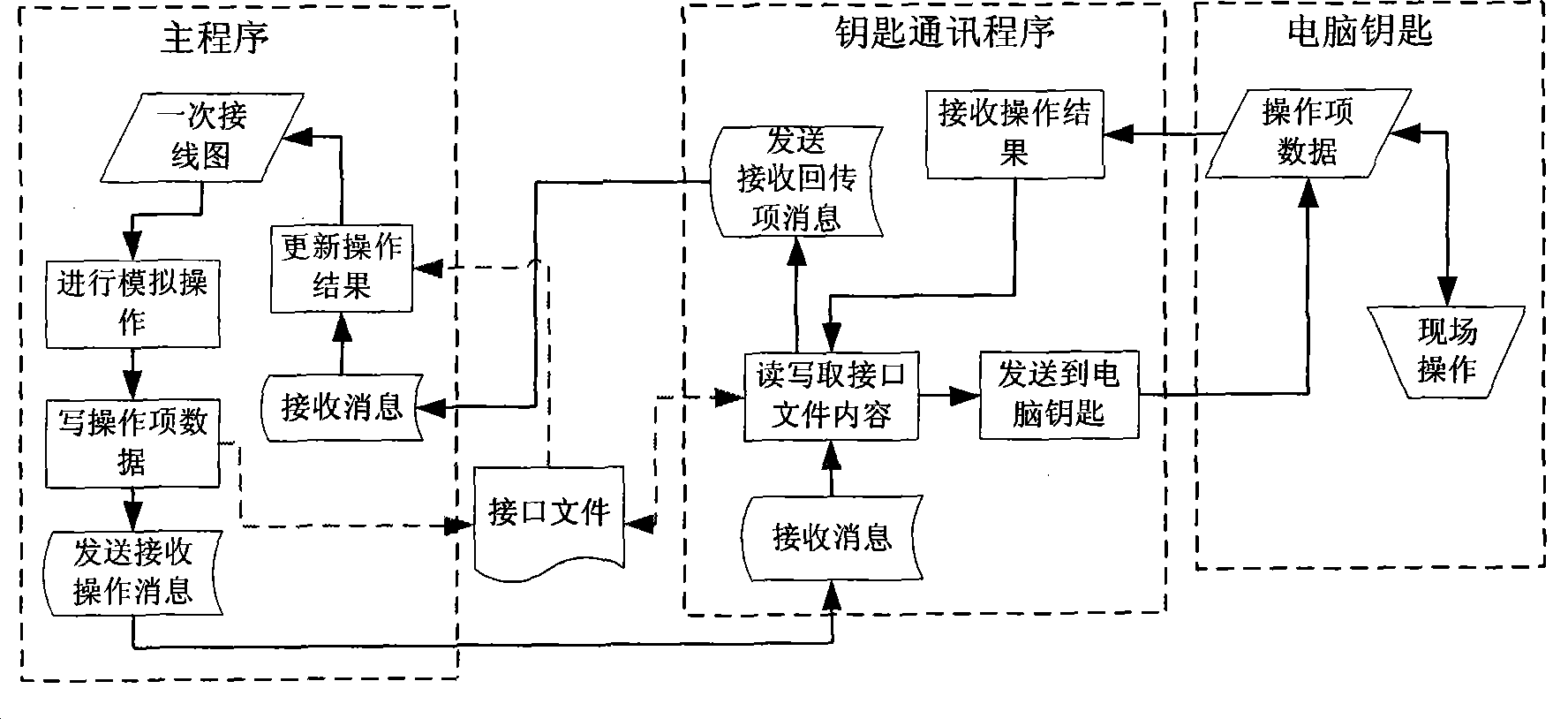
[0025] The method of realizing the networked five-proof locking system of unattended substation is as follows:
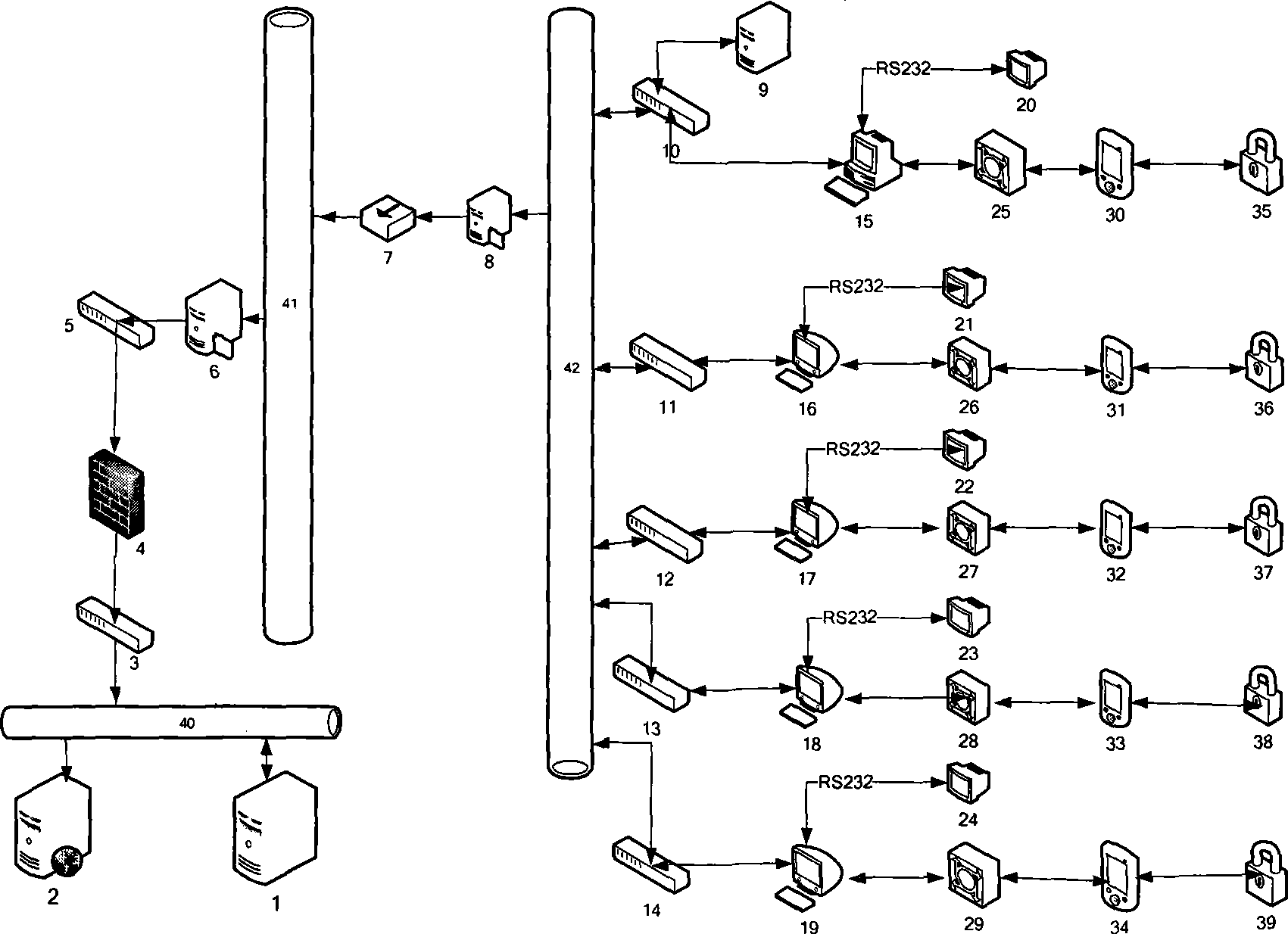
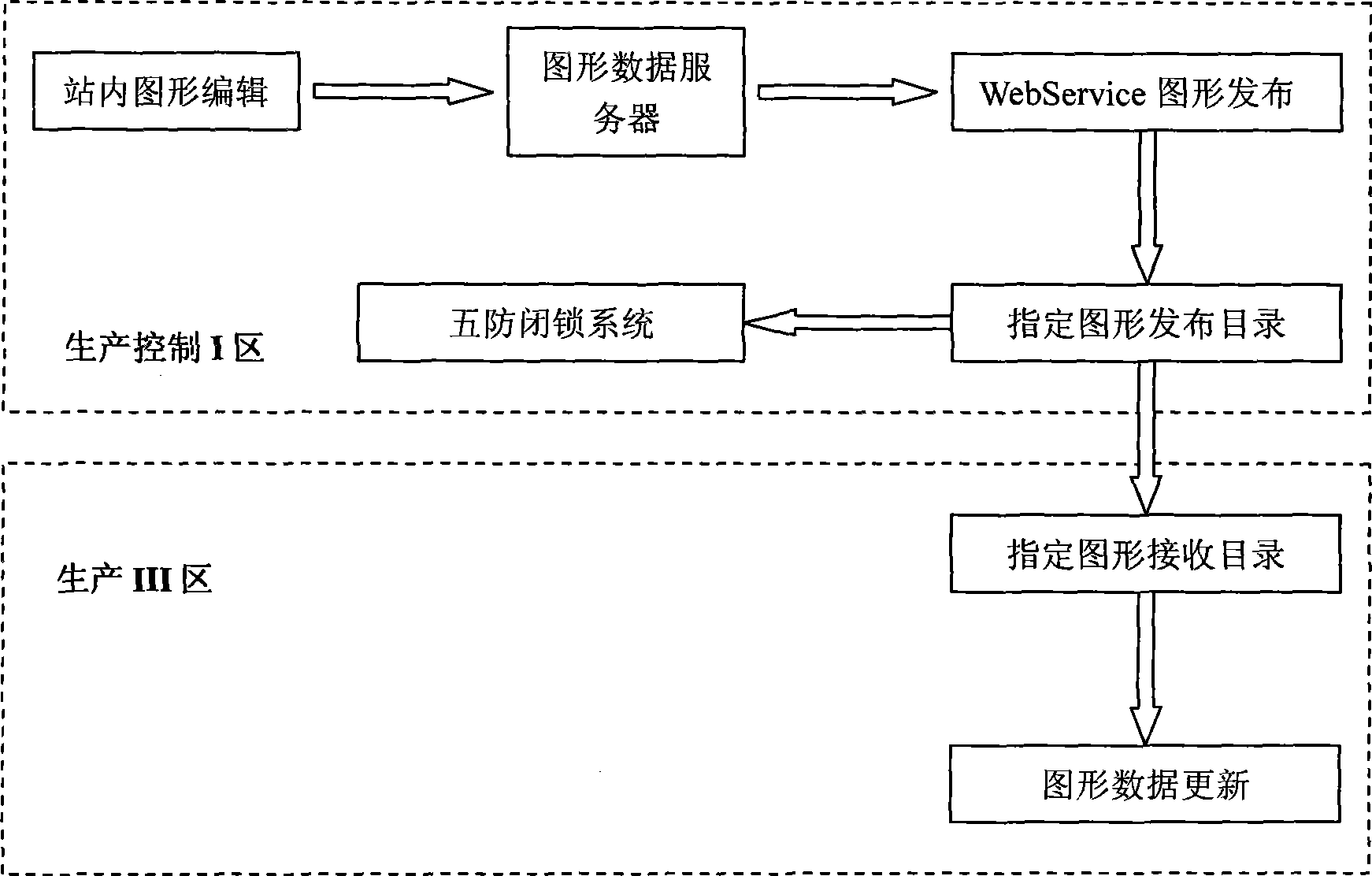
[0026] (1) Establishing a system network (see figure 1 ):
[0027] The system network is composed of production control zone I dedicated network, production zone III network, and management information zone network; the production control zone I zone dedicated network and production zone III network are unidirectionally connected through the forward physical isolator 7; the production zone III network and The management information area network is unidirectionally connected through a firewall 4; the special network in the production control I area is composed of a master station, a sub-station, a production control I area network 42, and a file sending server 8, and the master station and each sub-station pass through the production control I area. Network 42 two-way connection; described production III area network is made up of production III area network 41, fil...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com