Industrial wireless network security communication implementation method based on cipher key
An industrial wireless network and secure communication technology, applied in the field of industrial wireless network security communication implementation, can solve problems such as not being an industrial wireless network security management solution, and achieve the effects of authentication and authorization, rational utilization, and network performance improvement.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] Hereinafter, preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings.
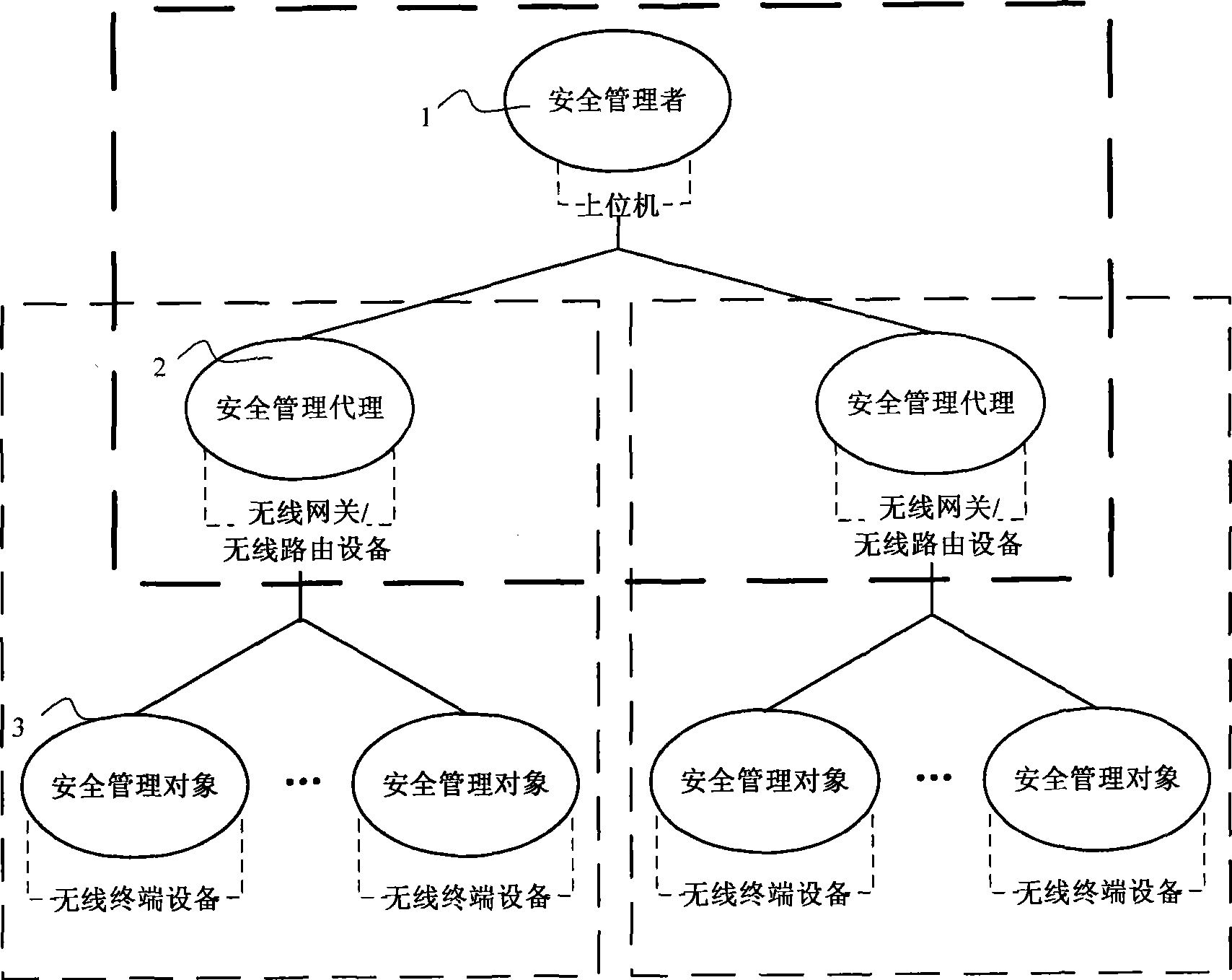
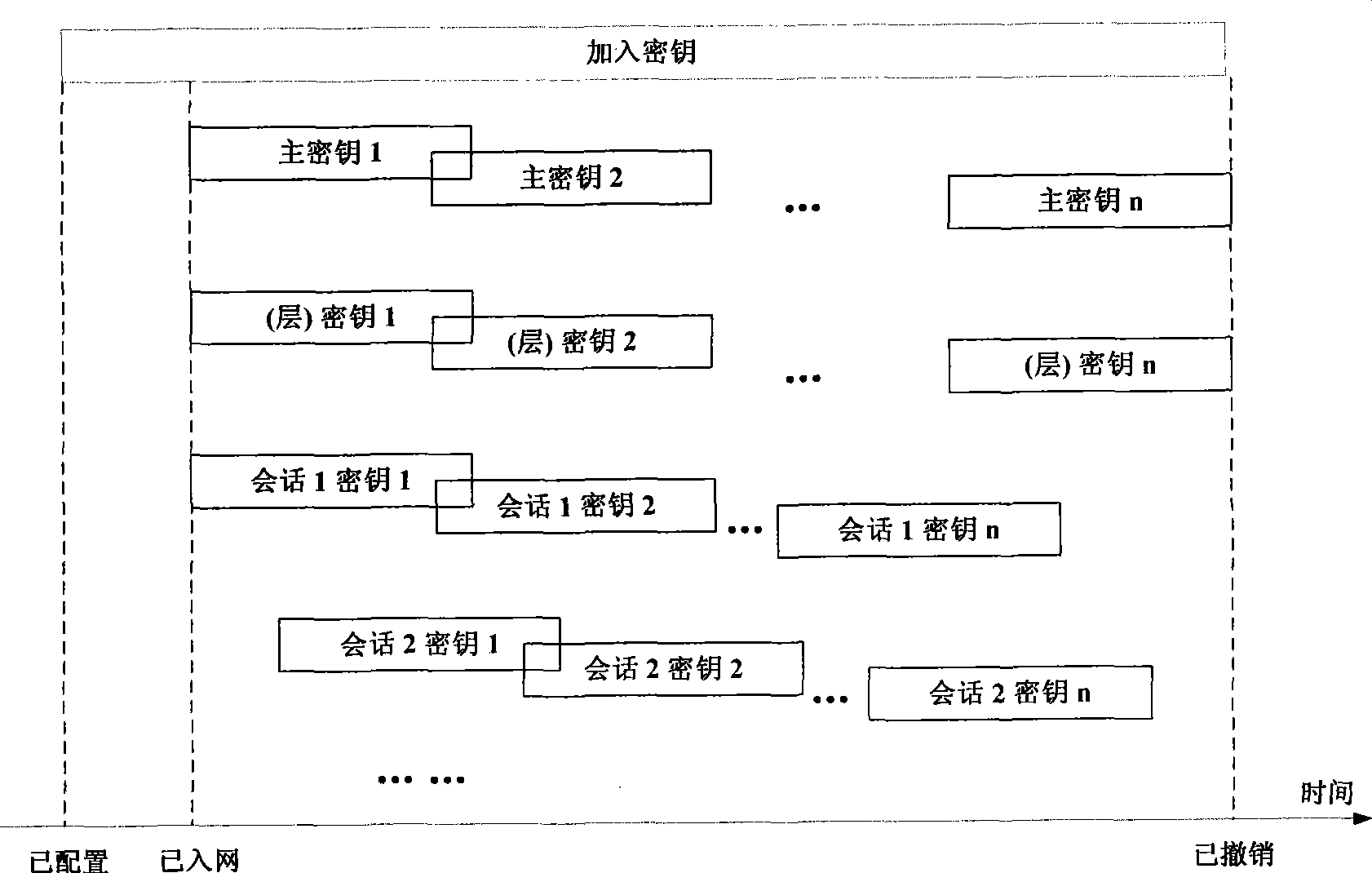
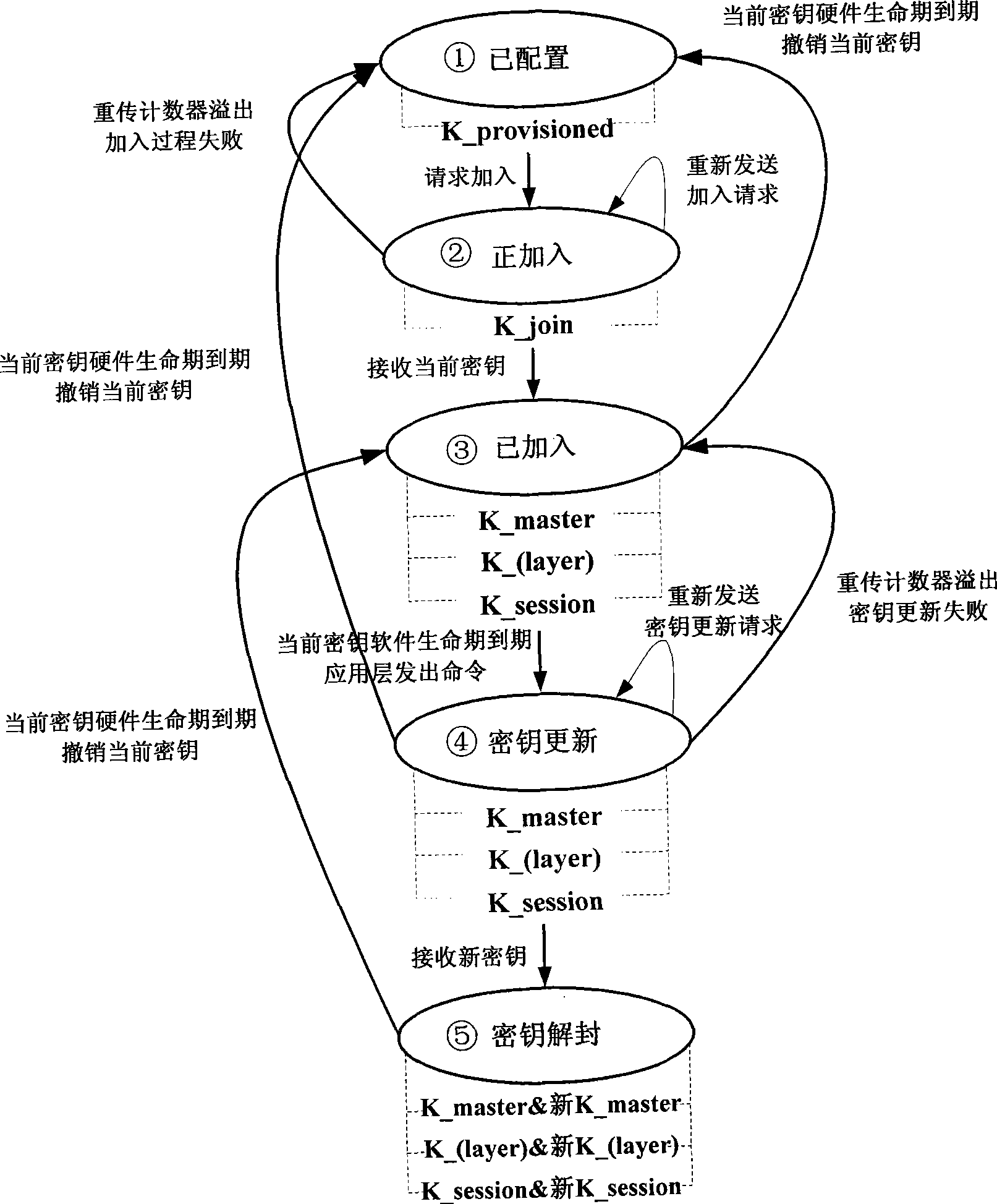
[0034] Such as figure 1 As shown, in this embodiment, the industrial wireless network security architecture is composed of a security manager 1 (host computer), a security management agent 2 (subnet routing device), and a security management object 3 (terminal device). Manage secure communications across the network in a distributed coexistence manner. In centralized network security management, the network security manager 1 is responsible for configuring the security policy of the entire network, key management and network access device authentication. Distributed network security management is that wireless gateways and wireless routing devices with security management agents are responsible for subnet boundary protection, and realize message filtering (including network address, flow control, industrial communication message identif...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com