Software transaction internal memory implementing method based on delaying policy
An implementation method and technology of transactional memory, which is applied in the field of software transactional memory, can solve problems such as complex program design, deadlock, escort, etc., and achieve the effect of alleviating low efficiency, simple and efficient conflict arbitration strategy, and improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] When implementing the implementation method of the software transactional memory based on the delay strategy, the specific method is as follows:
[0034] 1) Transaction creation
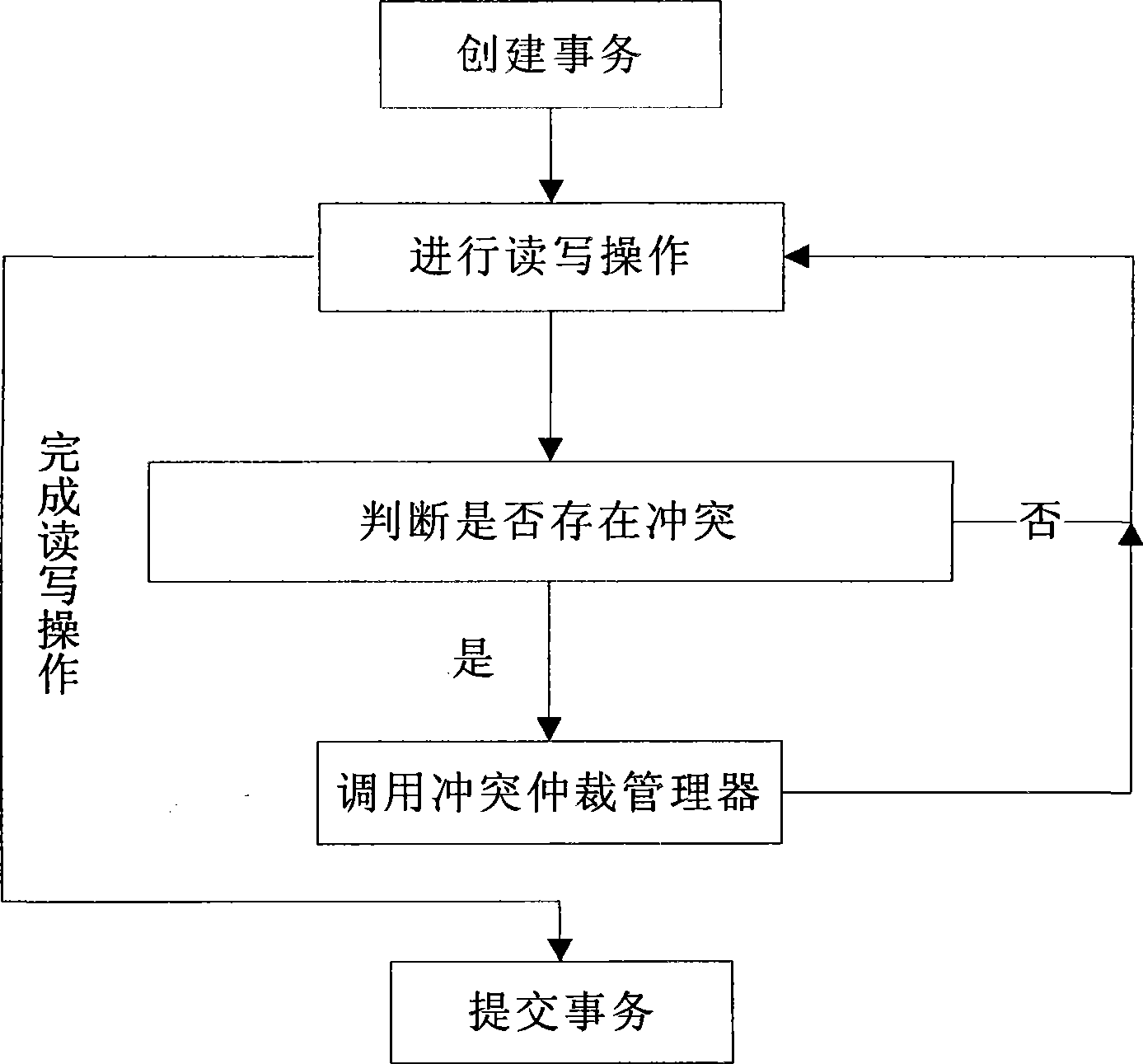
[0035] The execution process of software transactions includes: creating transactions, performing read and write operations, detecting conflicts, waiting for submission and submission, the whole process is as follows figure 1 shown;
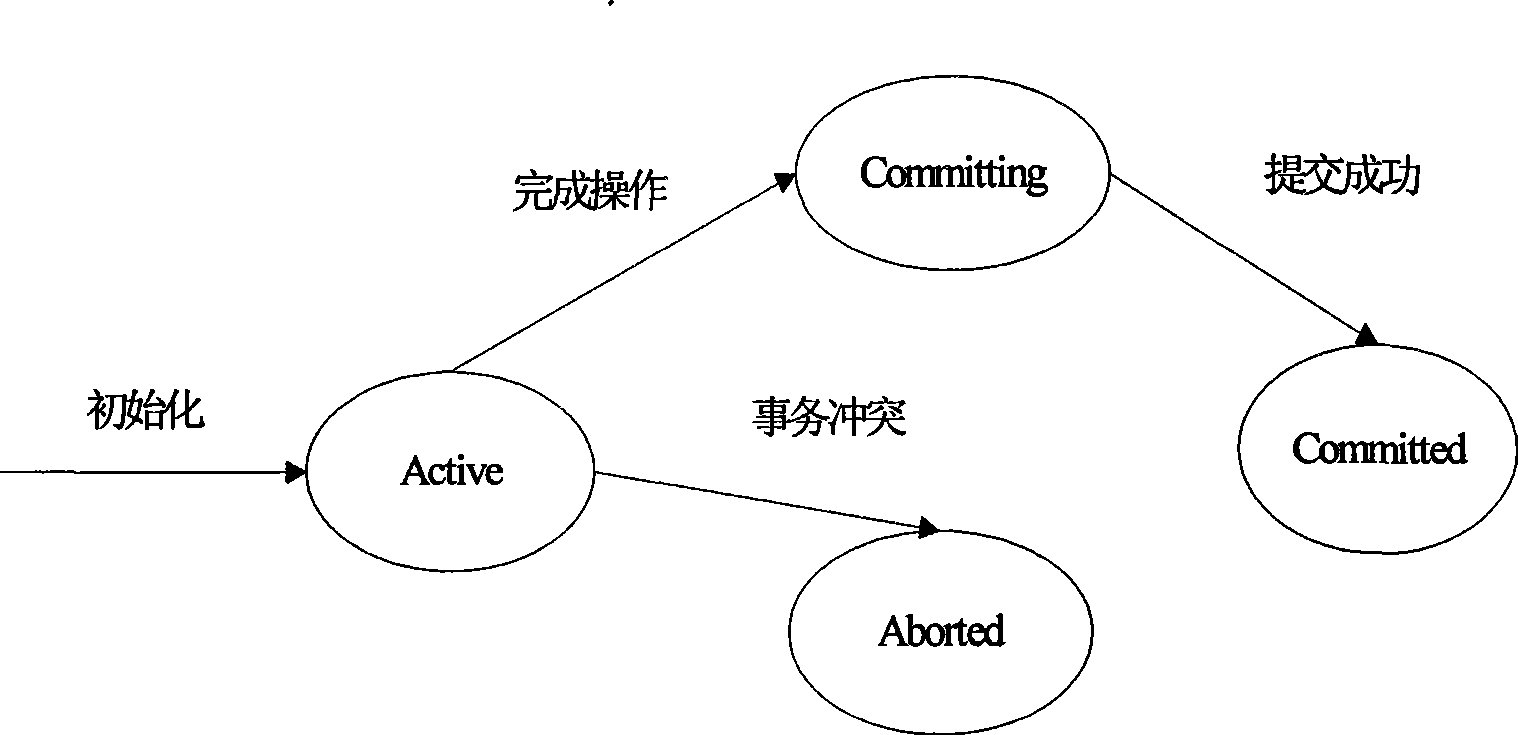
[0036] This method provides four states for software transactions: Active, Aborted, Committed, and Committed, respectively indicating that the transaction is running, the transaction has terminated, the software transaction has completed the operation on the object and is waiting to be submitted, and the transaction has been committed successfully, such as figure 2 shown;
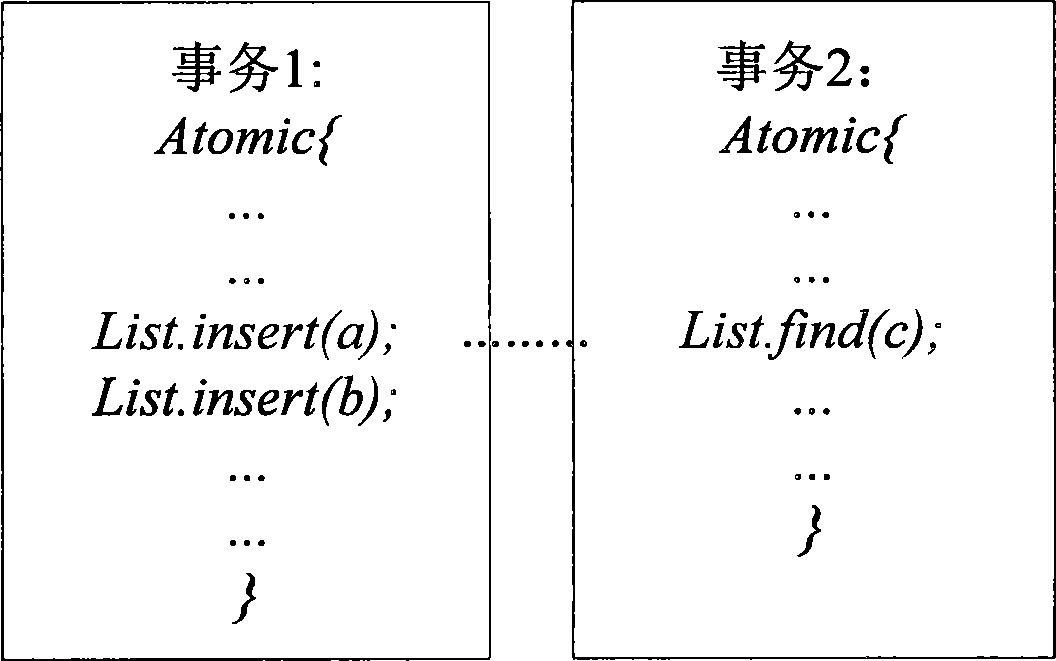
[0037] A transaction is created when an object needs to be read and written during program execution, and a transaction is a series of continuous instruction sets that operate on the same o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com