Business process execution language (BPEL)-based secure access service integration modeling method
A technology for secure access and business integration, applied in the field of computer technology and information security, it can solve the problems of complex configuration, unfavorable use, and large development volume, and achieve the effect of strong flexibility and easy modification.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be further described below through specific embodiments and accompanying drawings.
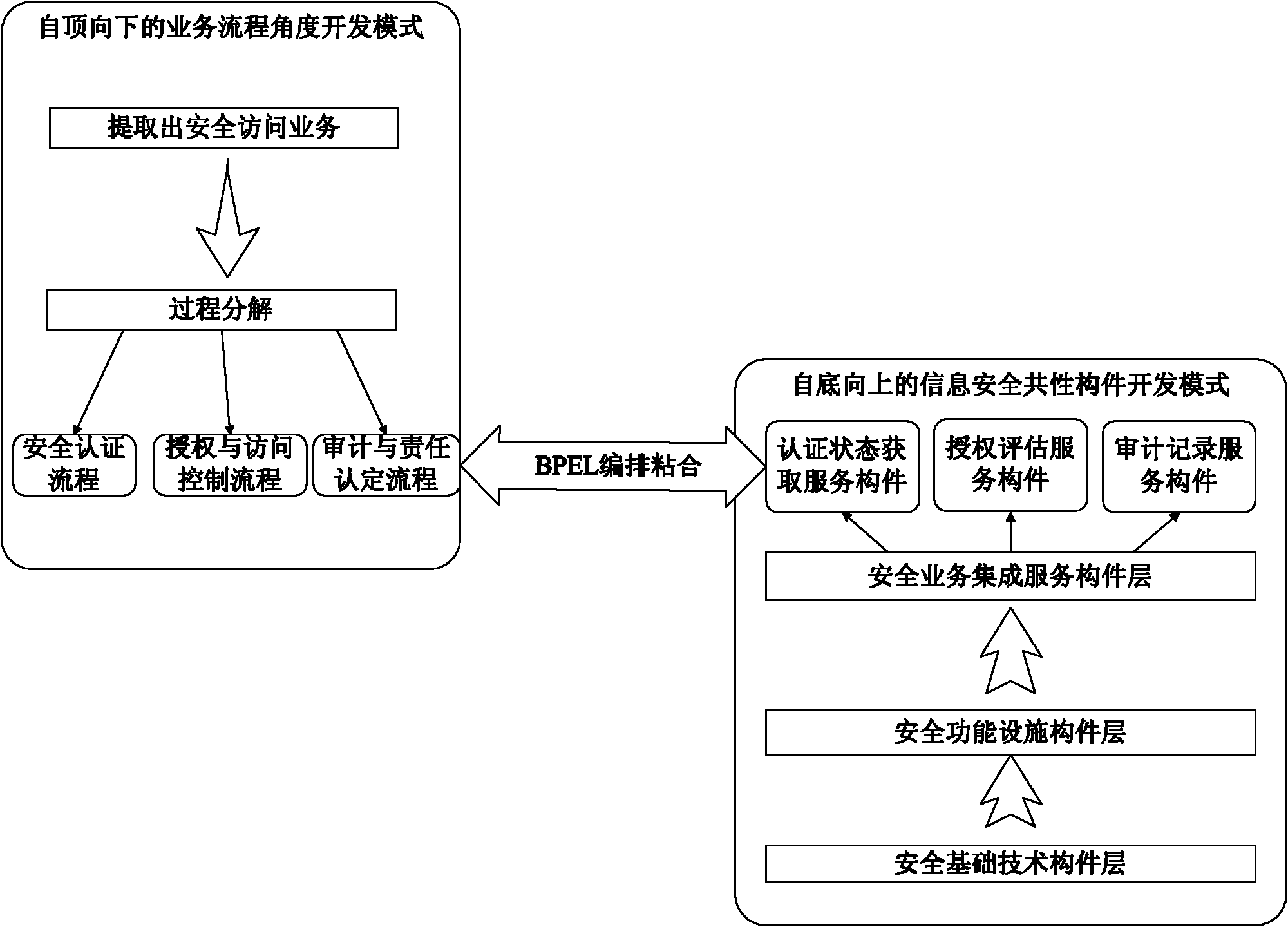
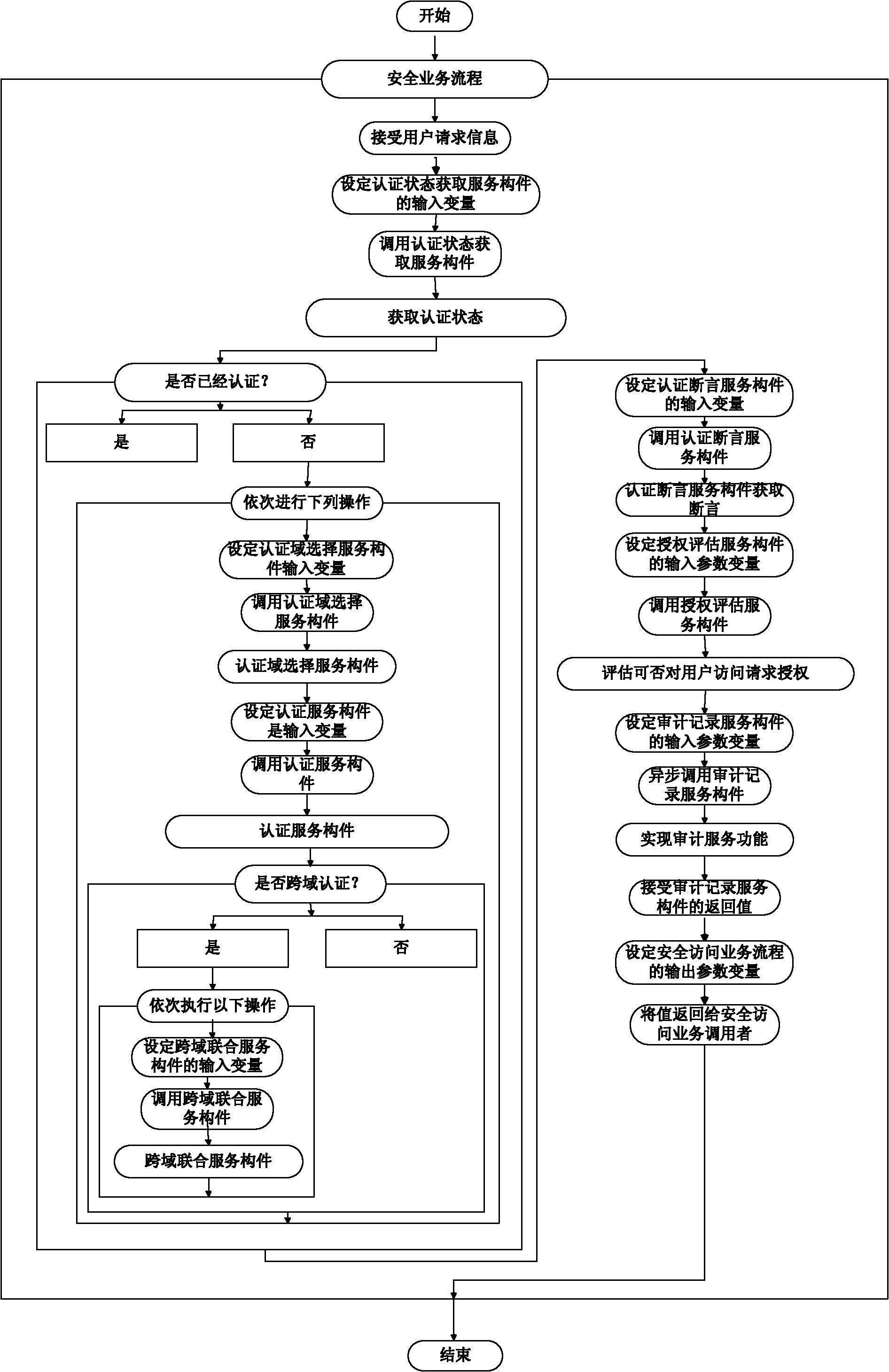
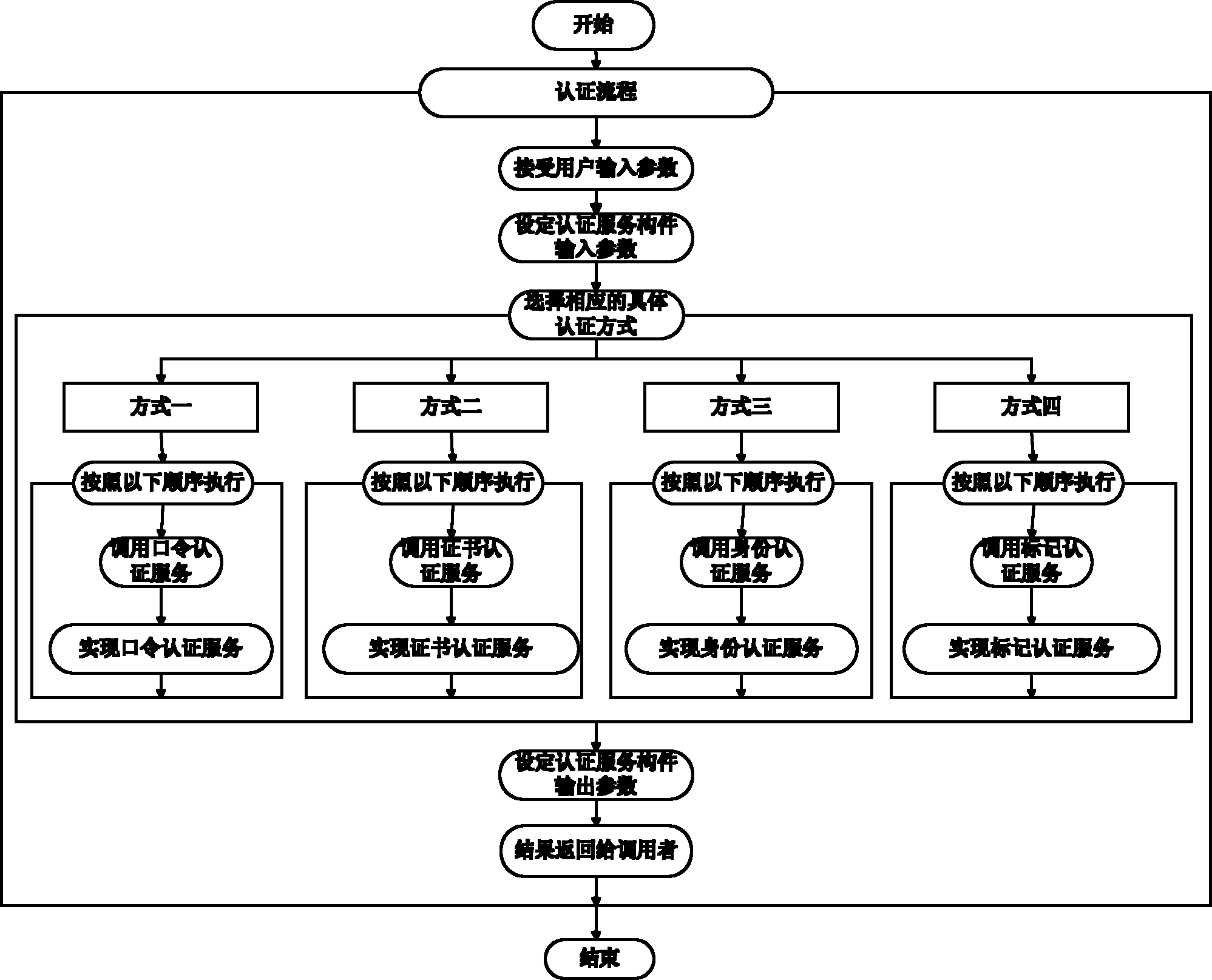
[0028] The development of information security common components is from the underlying infrastructure components to the middle functional facility components and then to the upper integrated service components, while the development of business processes is from the upper layer business modeling to the middle layer process analysis and then to the bottom layer service integration. These are developments in two different directions. The present invention uses BPEL arrangement to seamlessly combine component development and business process development to form a complete security business integration modeling model, such as figure 1 shown. The information security common component set is divided into three levels, from bottom to top: security infrastructure component technology layer, security function facility component layer and security integration service c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com