Weak authentication and key agreement method based on symmetrical password
A symmetric cryptography and key negotiation technology, applied in key distribution, can solve problems such as unaffordable special networks, large computing and communication resources, and limited capabilities, and achieve fast encryption and decryption, low energy consumption for computing and communication, and high efficiency Improved effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
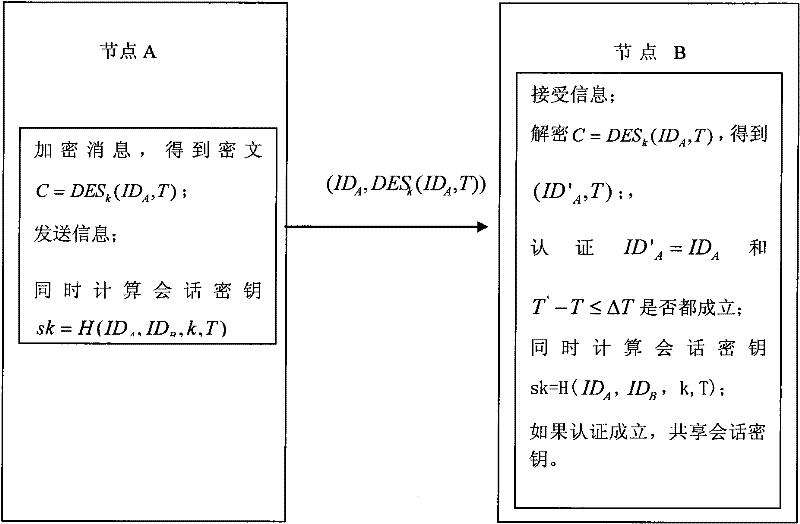
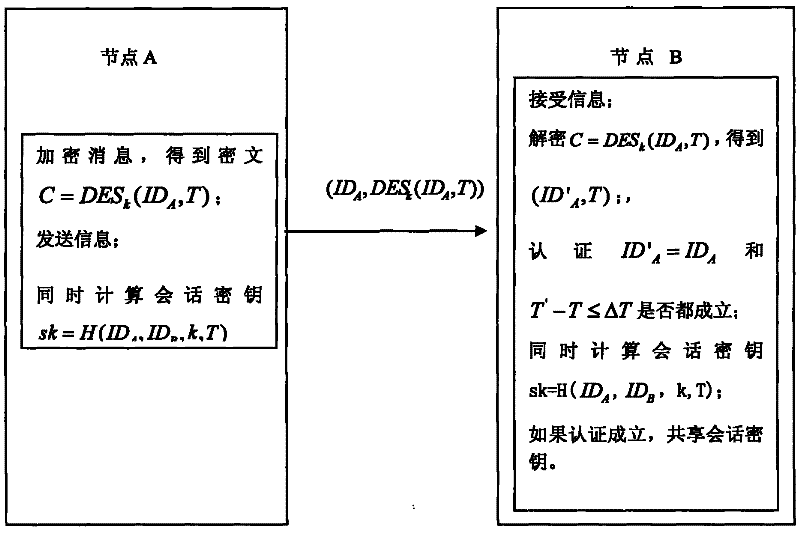
[0036] Embodiment 1: One-way authentication using the symmetric key encryption algorithm DES
[0037] As mentioned above, the present invention is based on symmetric cryptography, a shared key has been established between any two nodes, and the identity authentication and session key are established under the premise that the clocks are almost synchronized. The specific steps are as follows:
[0038] 1) Preset a long-term shared key k between any two network node devices A and B.
[0039] In the key pre-distribution stage, first generate a large key pool G and key identification; then randomly extract several keys that are not repeated to form a key chain; finally load different key chains to different sensor nodes. Each node has to discover the surrounding nodes with which it has a shared key, and only nodes with a shared key are considered to be connected. In the case where any two nodes have a shared key, if user A wants to initiate authentication to user B and establish ...
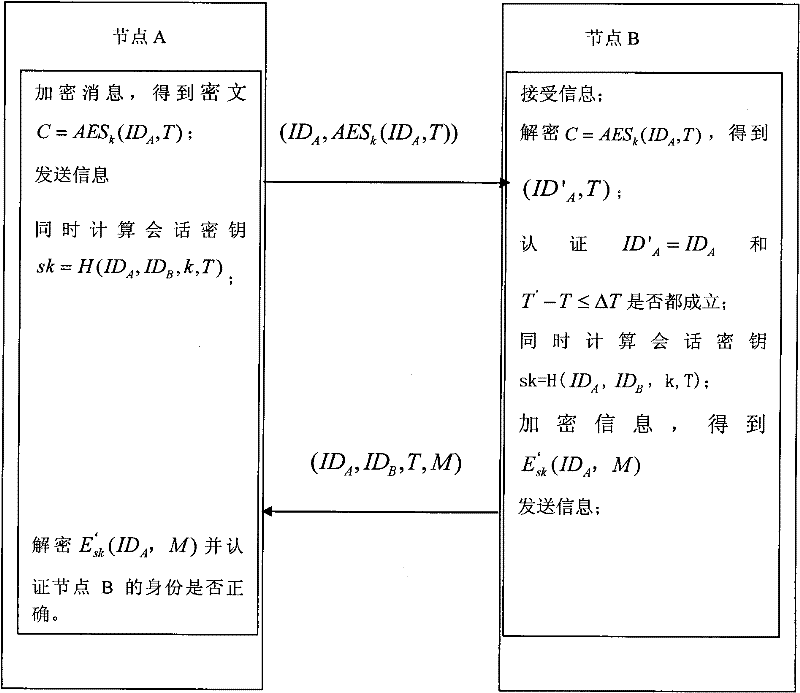
Embodiment 2
[0047] Example 2: Two-way authentication using the symmetric key encryption algorithm AES
[0048] 1) Preset a long-term shared key k between any two network node devices A and B. The long-term shared key k is generated by a server, and the key length is 128 bits.
[0049] With the development of symmetric cryptography, the DES data encryption standard algorithm has been unable to meet the requirements of today's distributed open network for data encryption security due to the small key length (56 bits). Therefore, in 1997, NIST publicly solicited new data encryption standards. , namely AES. AES is a block key, the algorithm inputs 128 bits of data, and the key length is also 128 bits. Each round requires the participation of an Expandedkey of the same length as the input packet. Since the length of the externally input encryption key K is limited, a key expansion program (Keyexpansion) is used in the algorithm to expand the external key K into a longer bit string to genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com