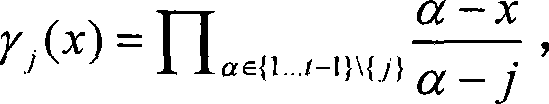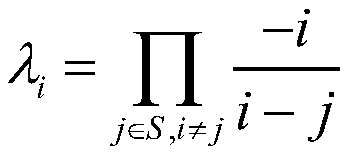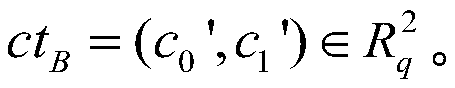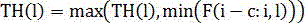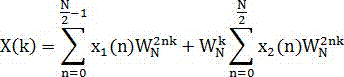Patents
Literature
124results about How to "Save communication bandwidth" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
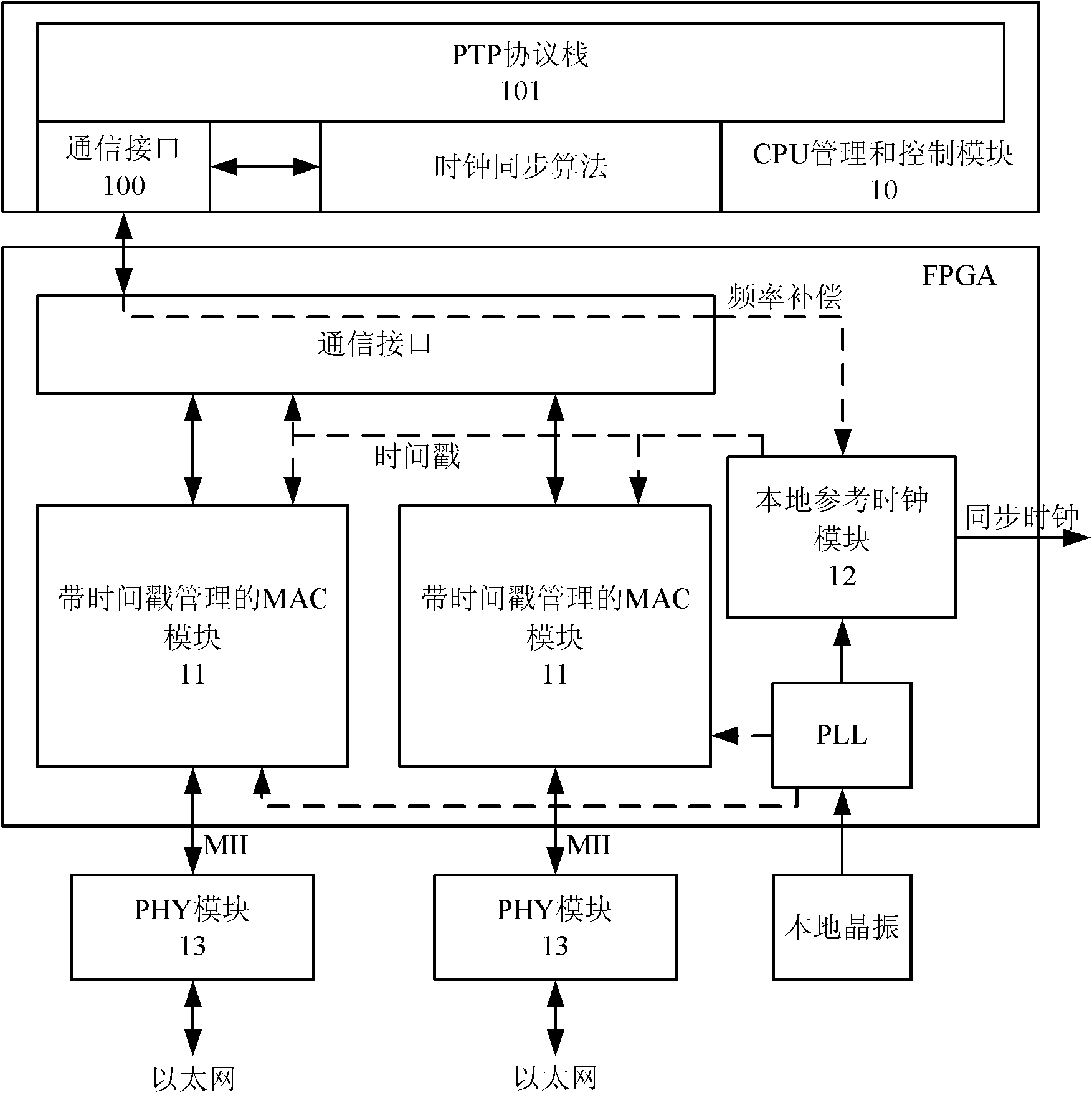
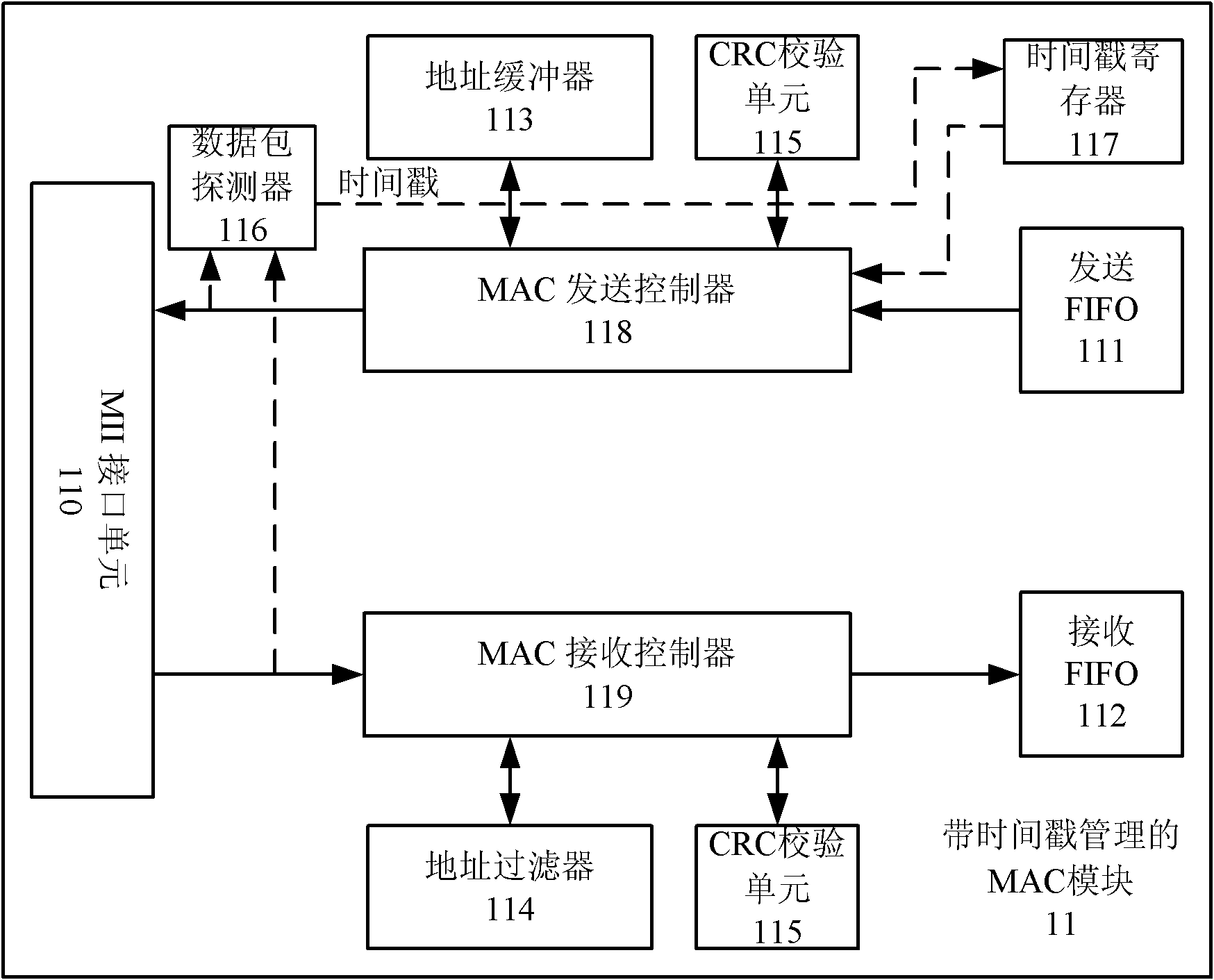
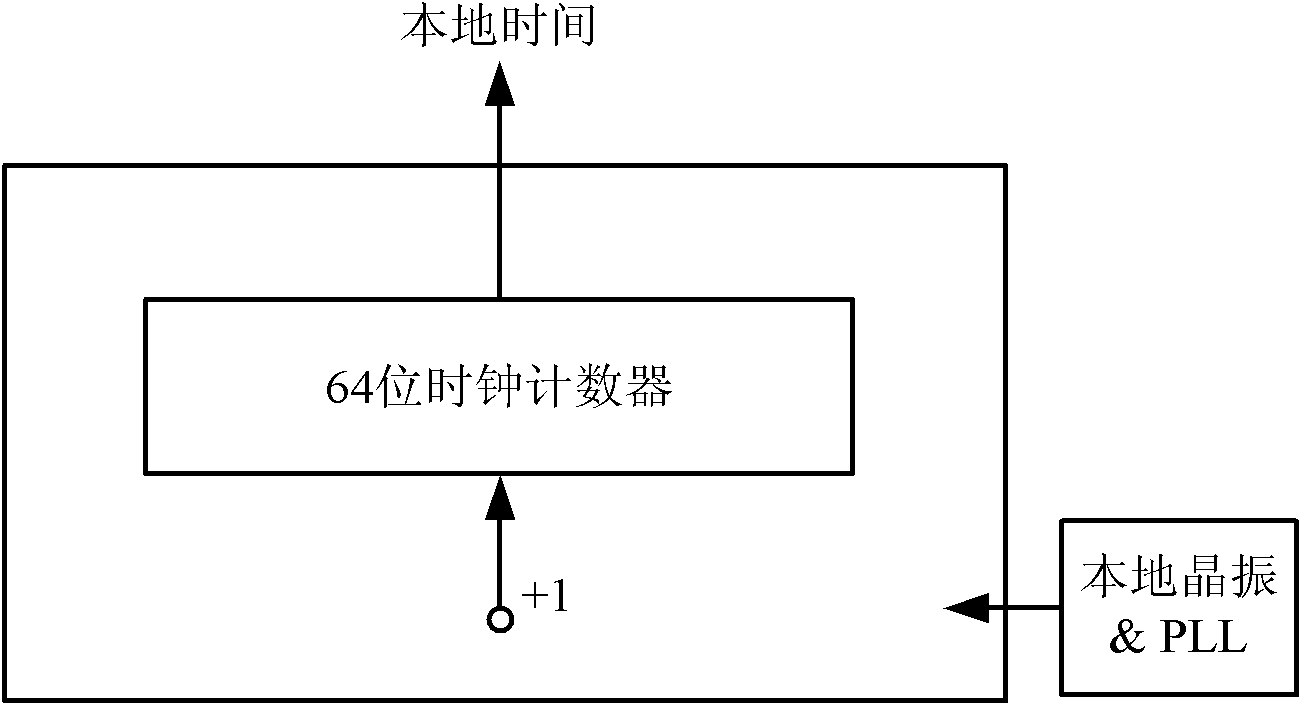
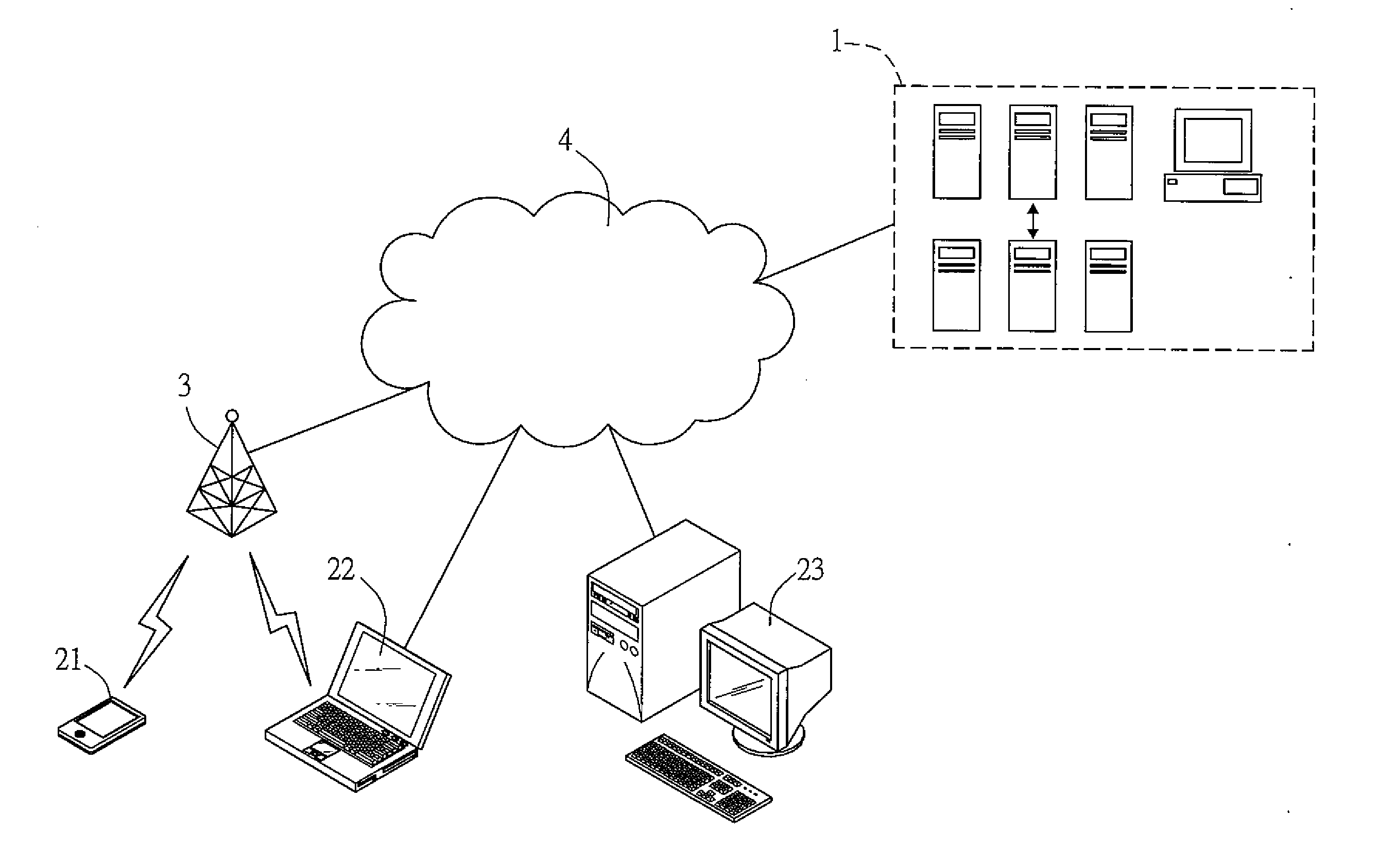
IEEE1588 based accurate clock synchronization protocol system and synchronization method thereof
ActiveCN101977104ASave communication bandwidthImprove real-time performanceSynchronising arrangementBus networksInformation transmissionTimestamp
The invention relates to an IEEE 1588 based accurate clock synchronization protocol system and a synchronization method thereof, belonging to the technical field of network information transmission. By adopting the invention, a main clock carries an accurate timestamp while sending a synchronization message, and a follow message is not required to be sent, thus greatly reducing communication bandwidth required for realizing clock synchronization. Meanwhile a frequency adjustable clock counter is constructed, and clock synchronization algorithm is combined, so as to realize frequency compensation function and achieve high accuracy clock synchronization requirement.
Owner:SHANGHAI JIAO TONG UNIV
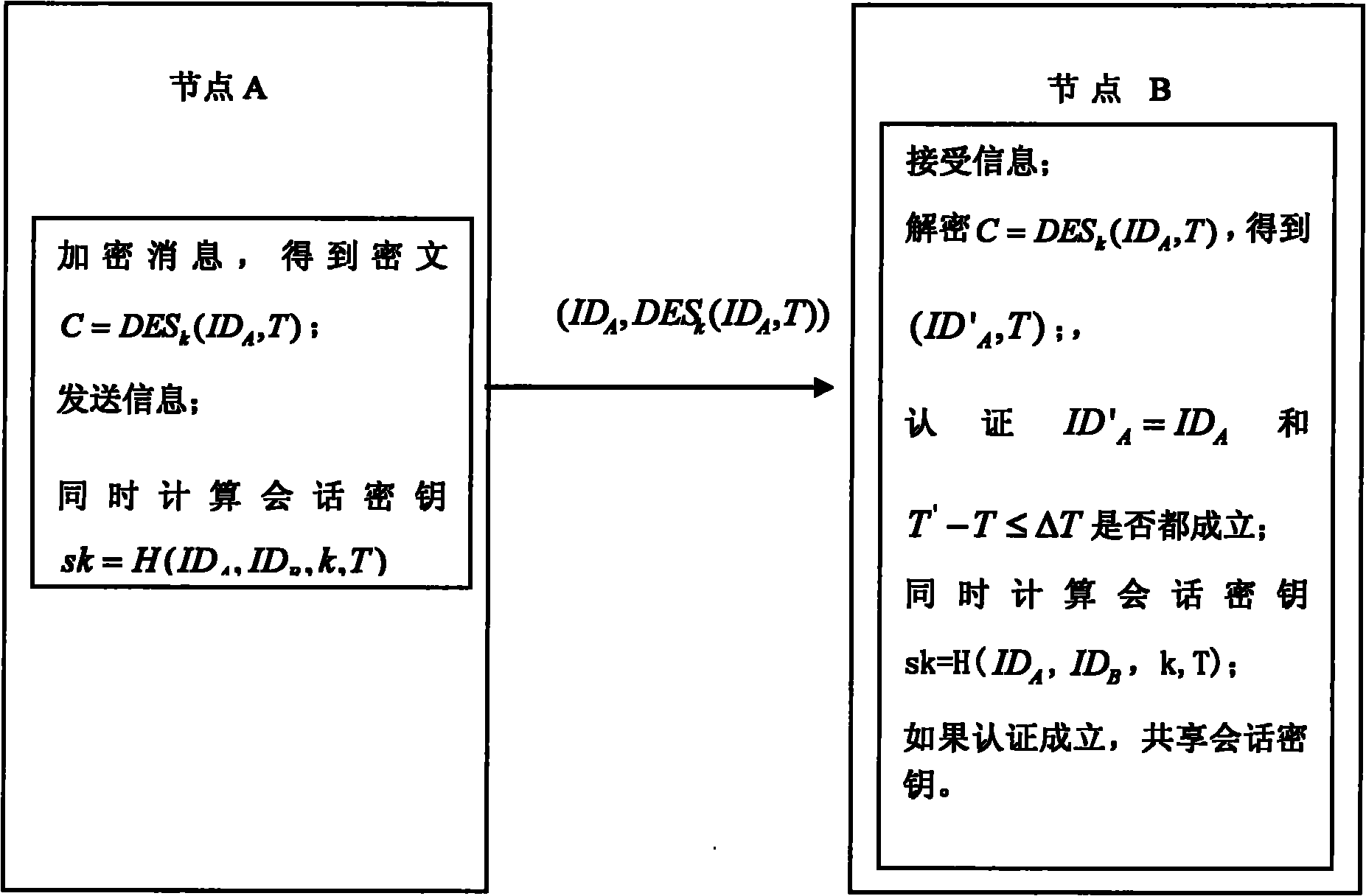
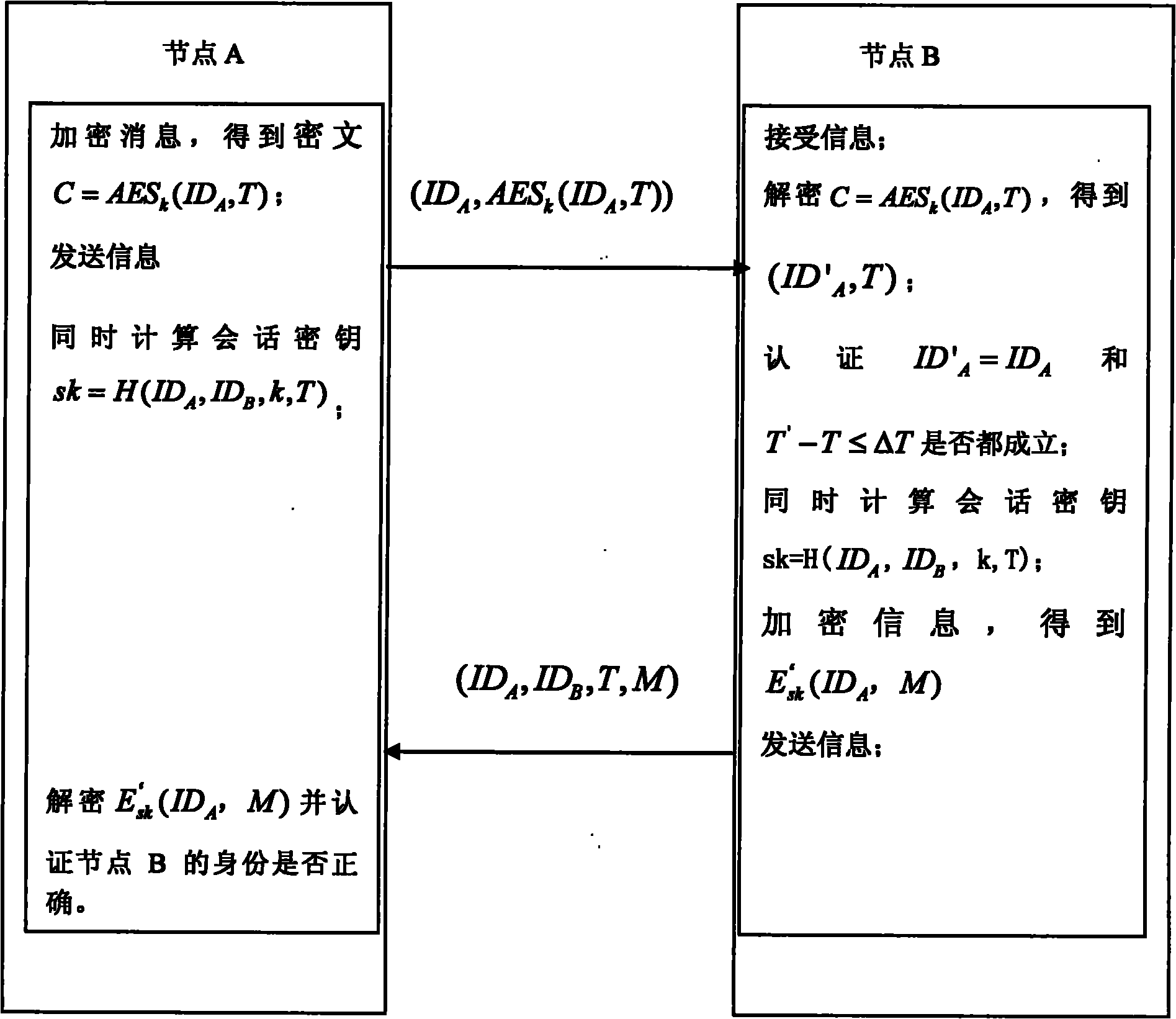
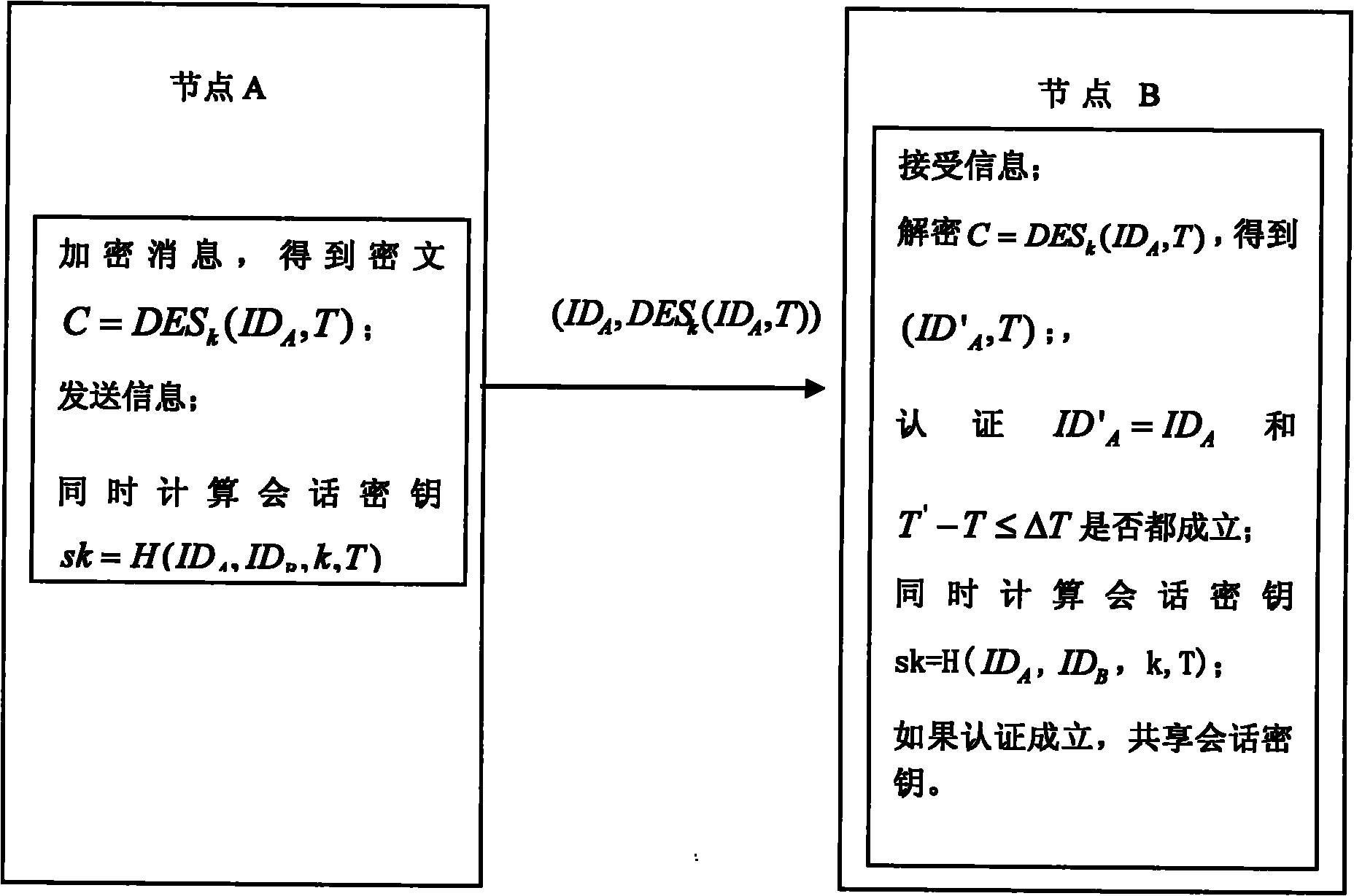
Weak authentication and key agreement method based on symmetrical password
ActiveCN101917270AHigh speedShorten the lengthKey distribution for secure communicationUser identity/authority verificationCiphertextPassword
The invention discloses a weak authentication and key agreement method based on a symmetrical password, comprising the following steps: 1) presetting a long-term shared secret key k between any two network node equipment A and B; 2) respectively arranging a clock on a node A and a node B, wherein, the error between each clock and standard time does not exceed T0 second; 3) internally installing an encryption algorithm E between the node A and the node B; and 4) building an authentication and session key between the node A and the node B by utilizing the encryption algorithm E and the long-term shared secret key k. The method of the invention has low energy-consumption computation and communication, rapid execution speed and high authentication efficiency, and is suitable for resource-restricted communication environments. As the invention uses a symmetric cryptographic algorithm DES or AES, the difficult degree that opponents capture authentication message to obtain the long-term shared key or a ciphertext is relative to the difficult degree of decoding the DES or AES algorithm, thus ensuring the safety of the ciphertext and the key.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
Cloud storage data security auditing method allowing group-user identity revocation
InactiveCN103501352AAudit validAvoid complex calculationsUser identity/authority verificationThird partyCloud storage security
The invention discloses a cloud storage data security auditing method allowing group-user identity revocation. The cloud storage data security auditing method comprises the following six steps: (1) generating keys (KeyGen); (2) calculating resign keys (ReKey); (3) generating signs (Sigh); (4) generating resigns (ReSign); (5) generating proofs (GenProof); (6) checking the proofs (CheckProof). Not only can shared data be effectively audited by a third party auditor after group-user identities are revoked, but also the security of the method is further enhanced compared with the existing method for solving a public auditing protocol allowing group-user identity revocation. As a result, the method disclosed by the invention can enhance the confidence of people in cloud storage security and further promote the health development of cloud storage environments.
Owner:BEIHANG UNIV
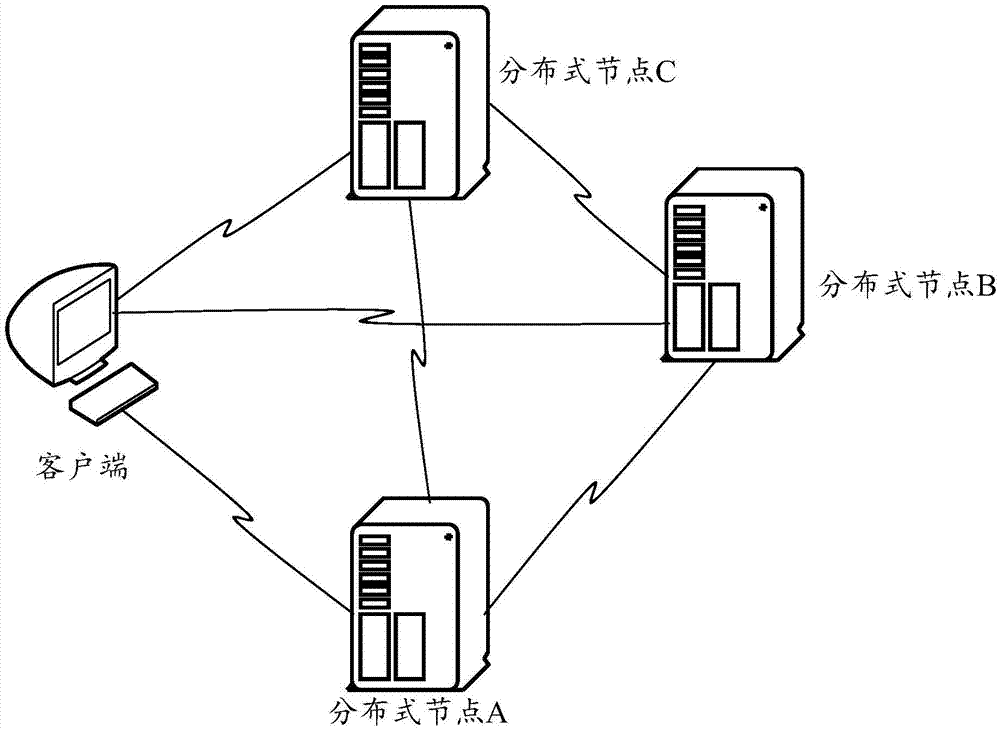
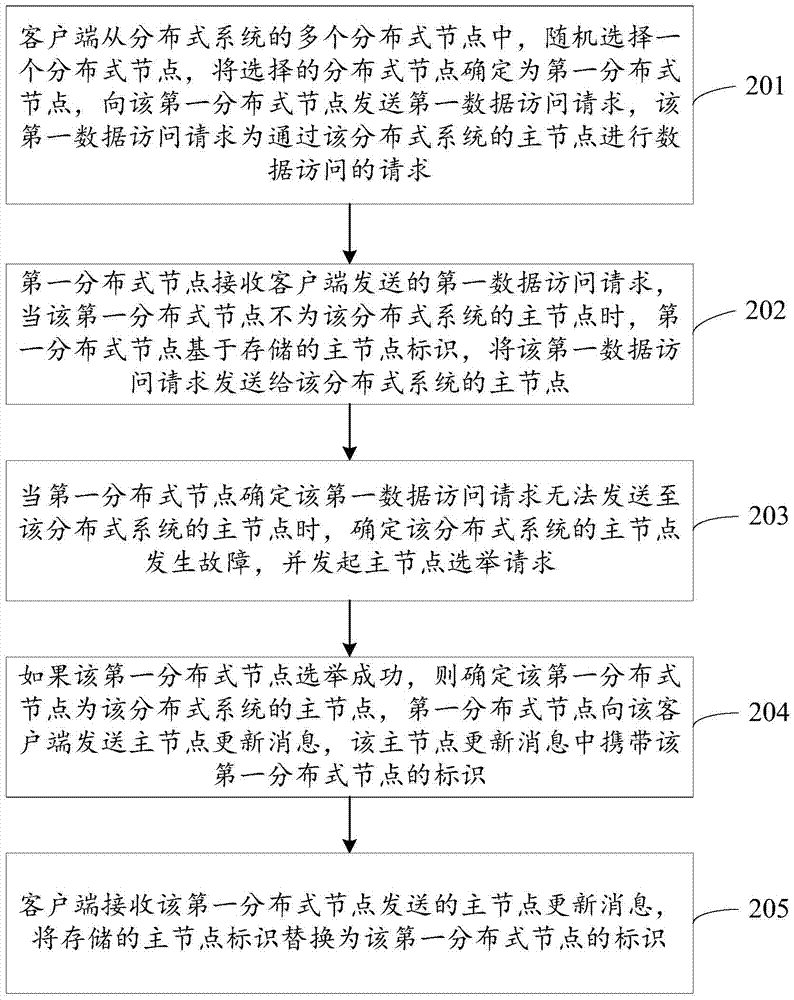
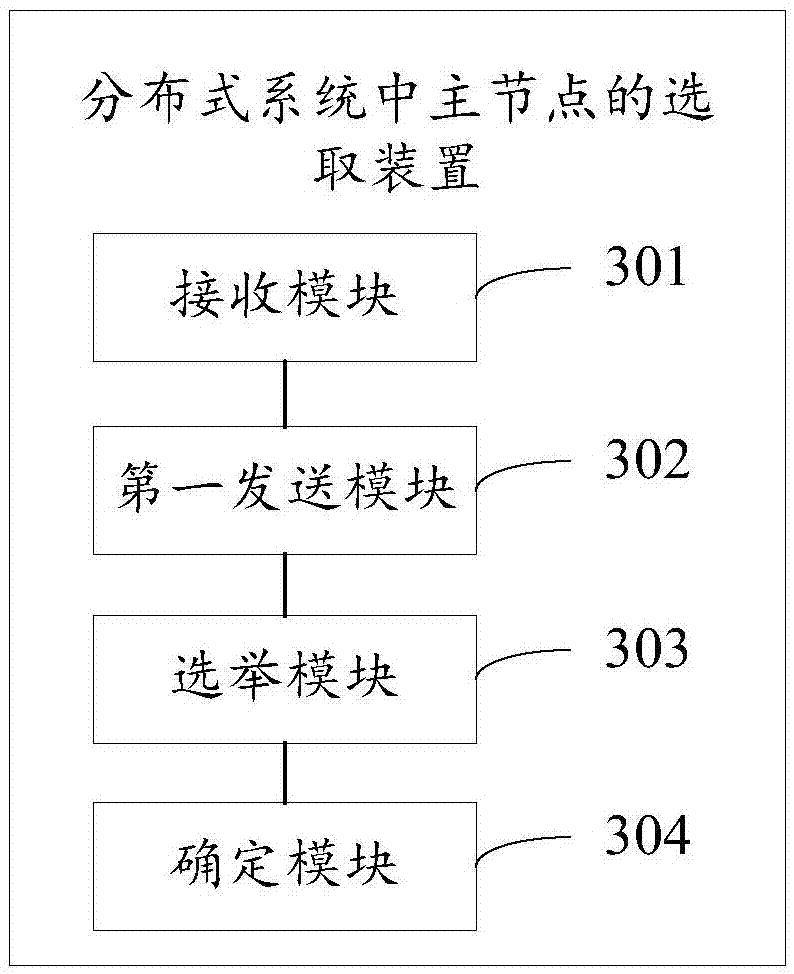
Method and device for selecting master node in distributed system
ActiveCN106911728AImprove work efficiencySave communication bandwidthData switching networksThe InternetData access
The invention discloses a method and device for selecting a master node in a distributed system, belonging to the field of Internet. The method comprises the following steps: a first distributed node receives a first data access request sent by a client, wherein the first data access request is a request for implementing data access through the master node of the distributed system, and the first distributed node is any of the distributed nodes in the distributed system; and when the first distributed node is not the master node of the distributed system, sending the first data access request to the master mode of the distributed system based on a stored master node identifier, when determining that the first data access request cannot be sent to the master node of the distributed system, determining that the master node of the distributed system has failure, and initiating a master node election request; and if the first distributed node is successfully elected, determining the first distributed node as the master node of the distributed system. According to the method and device disclosed by the invention, the communication bandwidths can be greatly saved, and the working efficiency of the distributed system can be increased.
Owner:HUAWEI TECH SERVICE
System And Method For Delivering Media Over Network
ActiveUS20160101356A1Reduce loadSave communication bandwidthProcessor architectures/configurationVideo gamesComputer graphics (images)Application software
A method for delivering media from a server to a client device over a network is disclosed. An Virtual-Reality (VR) scene application running on the server generates a virtual VR 3D environment containing 3D models. The server checks the status of each 3D model in a predetermined order, and then, only those 3D models which are not pre-stored in the client device will all be rendered by the server into a left eye frame and a right eye frame of 2D video stream. The server then sends to the client device the frames and meta data of the 3D models which are pre-stored in the client device via the network. The client device uses a combined VR frame of these frames as a background for rendering the 3D models which are pre-stored in the client device so as to generate a mixed VR frame of video stream for output.
Owner:KK UBITUS
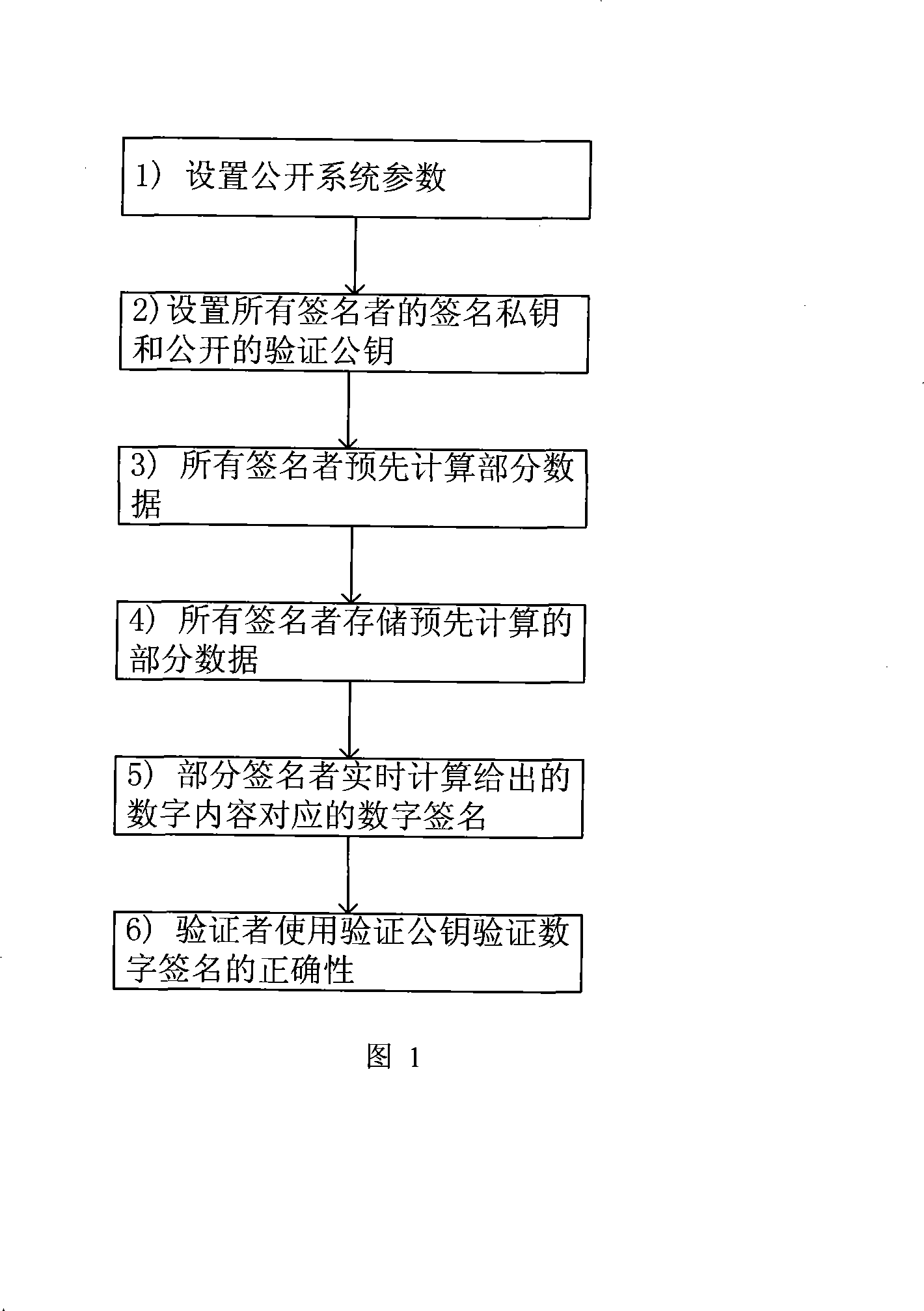
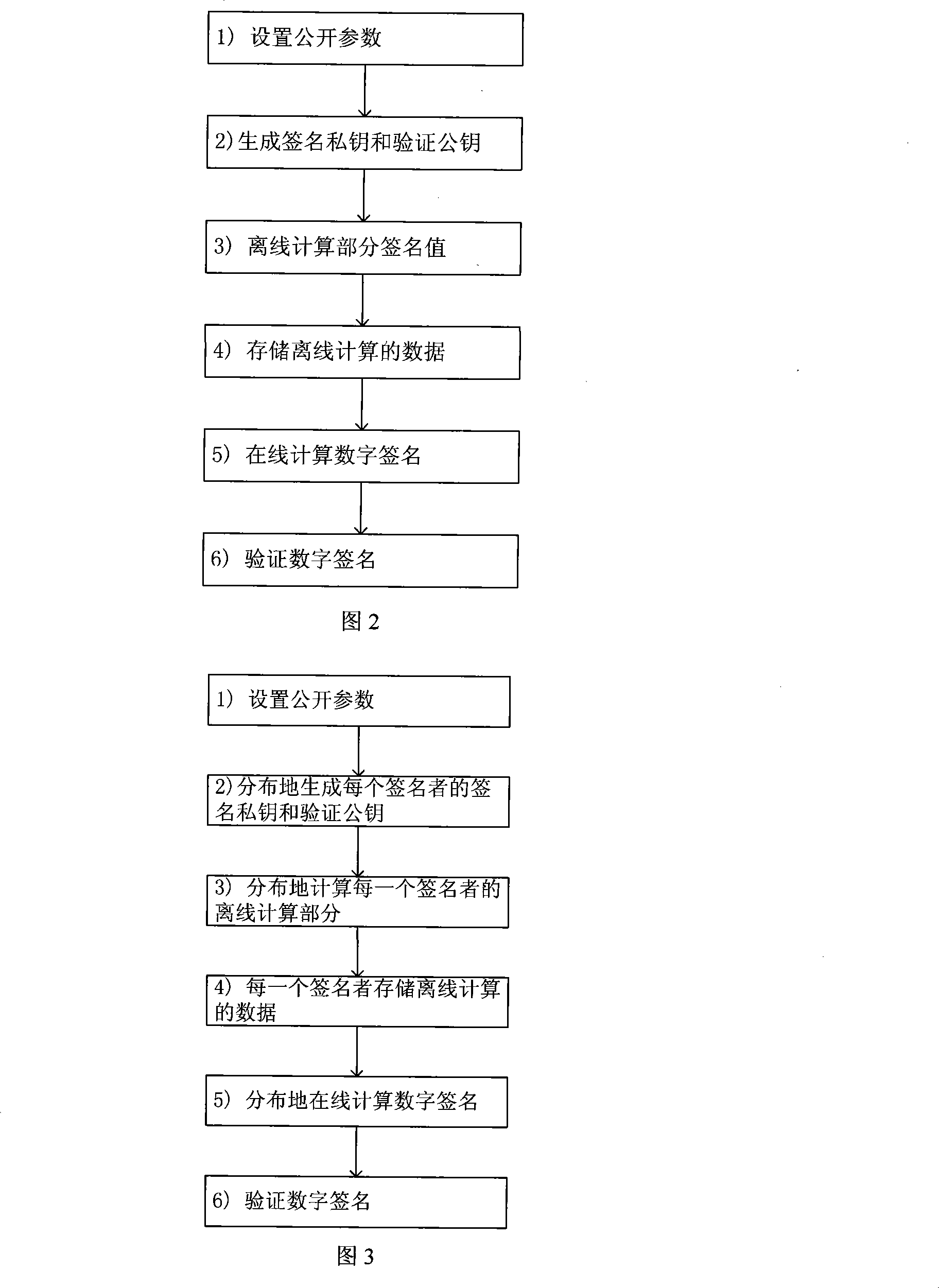
Realizing method of general-purpose digital signing scheme
ActiveCN101252431ASolve the problem of key disclosureReduce stepsUser identity/authority verificationGeneral purposeDigital signature
The invention relates to a method for realizing a universal digital signature scheme generating and verifying the digital content, comprising the following procedures: setting system parameters, generating a private key of the user signature and a public verifying key, and generating the digital signature in an off-line or on-line mode and verifying the digital signature. The invention creates a novel double-trapdoor chameleon function in a special way, so the limitation that the group inverse operation is needed when part of the data is calculated in advance in the background technique is solved, and the calculating amount is reduced; the limitation to the number of signers is removed; the problem of key leakage in the background technique of threshold digital signature scheme is solved; the calculating amount of the digital signature and verification is reduced; the signature length is shortened, and the memorizing requirement is reduced; therefore, the method has higher efficiency and better scalability.
Owner:GUANGZHOU XINRUI NETWORK TECH
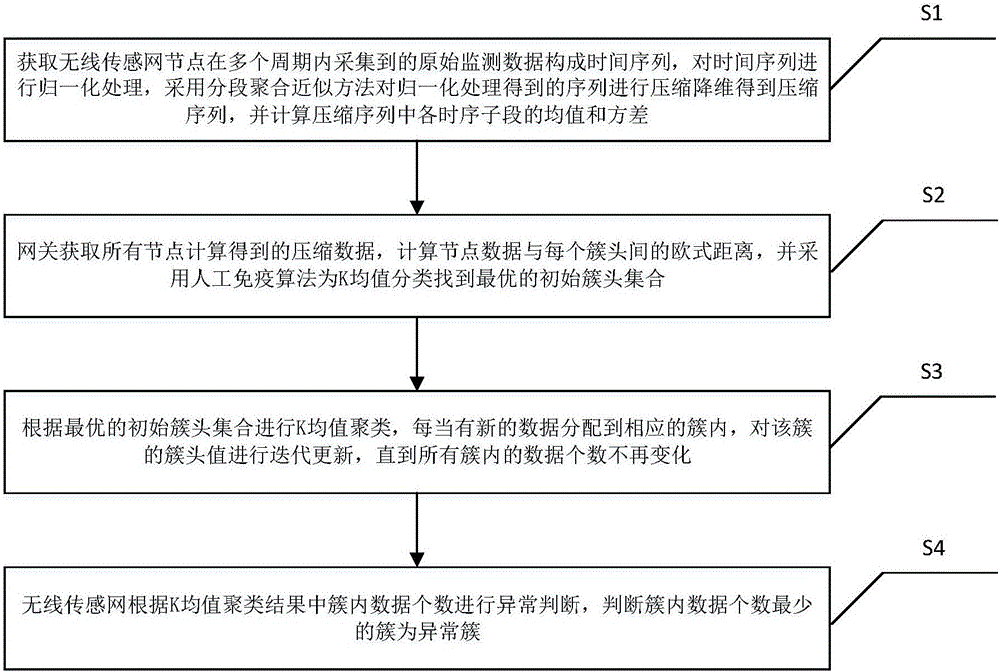
WSN (Wireless Sensor Network) abnormity detection method and system based on artificial immunization and k-means clustering
InactiveCN105791051AImprove search efficiencyPrecise positioningPower managementNetwork topologiesAnomaly detectionArtificial immune algorithm
The invention discloses a WSN abnormity detection method and system based on artificial immunization and k-means clustering. The method comprises that S1) original monitoring data collected by WSN nodes is obtained to form a time sequence, the time sequence is normalized, compression and dimension reduction are carried out on the normalized sequence, and the mean value and variance of each sequential segments in the compressed sequence are calculated; S2) the Euclidean distance between node data and each cluster head is calculated, and an artificial immunization algorithm is used to search an optimal initial cluster head set for K-means classification; S3) whenever new data is distributed into a corresponding cluster, iterative update is carried out on the cluster head value of the cluster till the amount of all data in the cluster does not change; and S4) the WSN determines abnormity according to the amount of data in the cluster in a K-means clustering result. According to the invention, abnormity information in monitoring data can be discovered accurately, the instantaneity and reliability of abnormity event detection of the WSN are improved, and energy and communication bandwidth of the WSN are greatly reduced.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Encoding and decoding device for low-code rate video super-resolution reconstruction
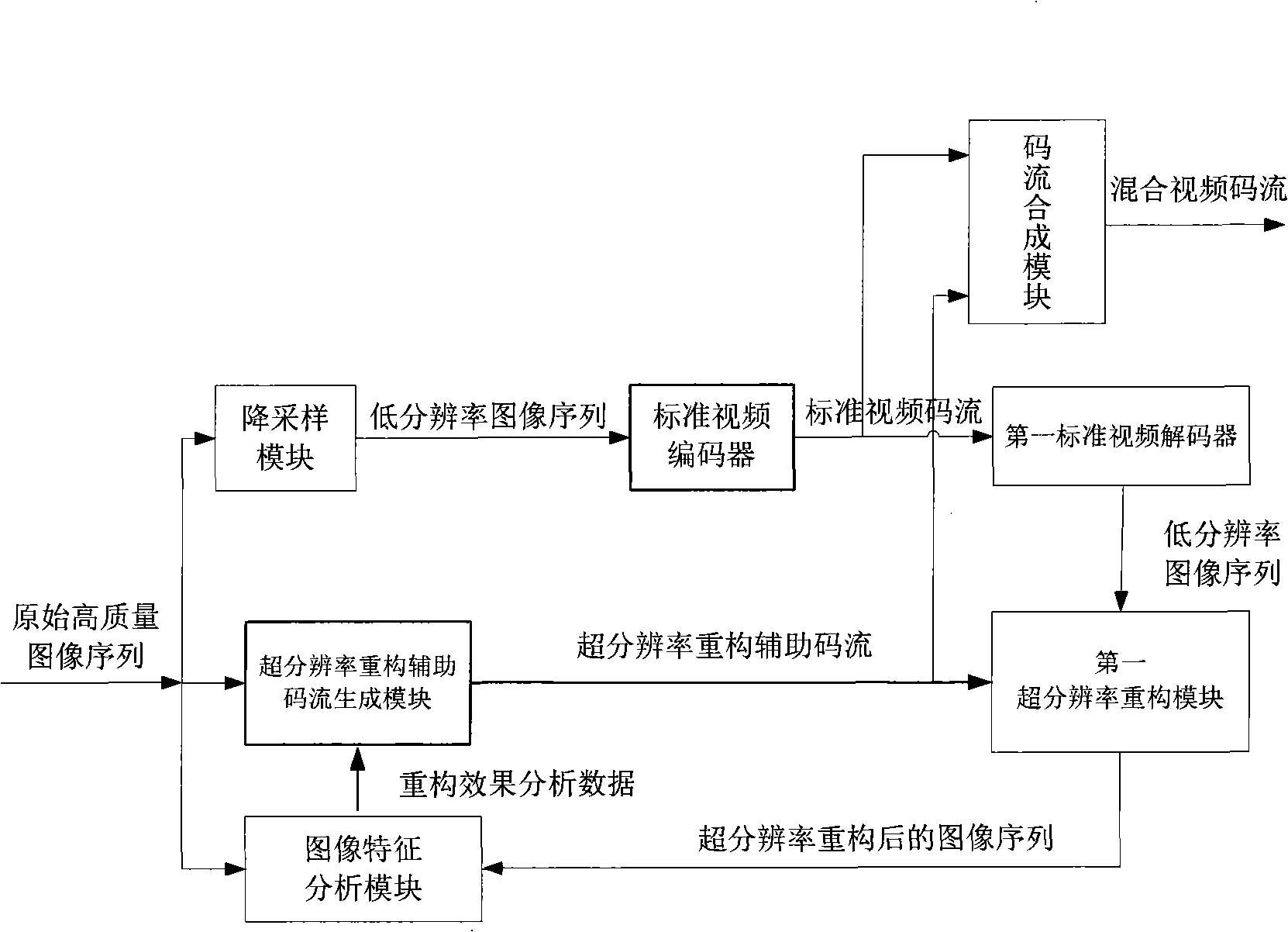
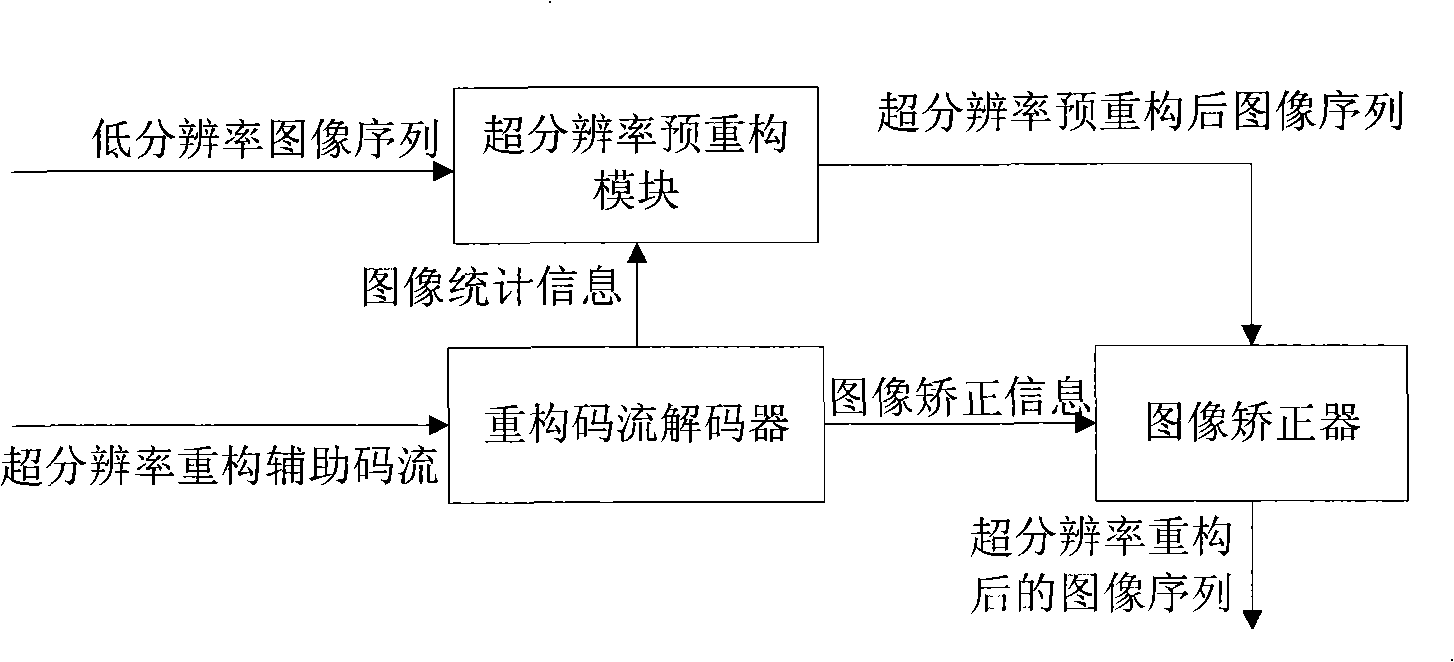
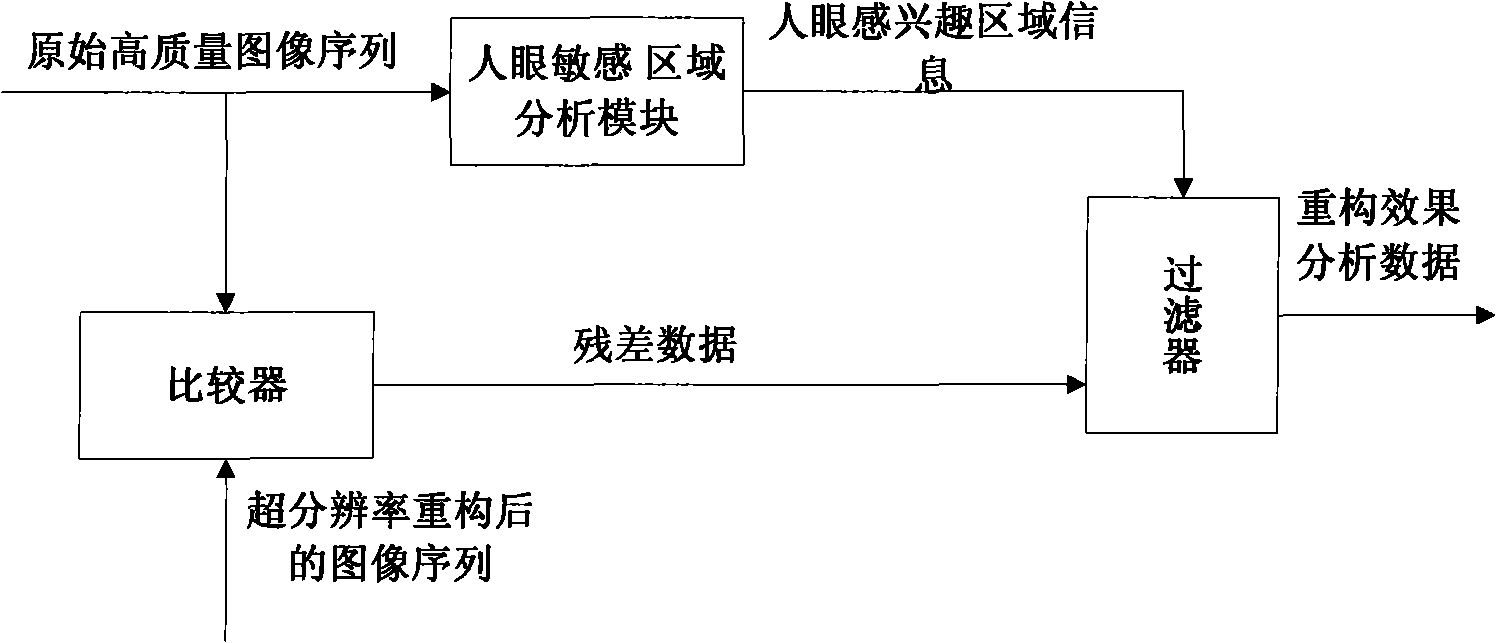
InactiveCN101345870AImprove efficiencyHigh precisionImage analysisTelevision systemsCode moduleClosed loop feedback
The invention discloses a coding device and a decoding device of low code rate video super-resolution reconstruction in the video processing field. In the invention, the coding device part provides auxiliary code stream to improve efficiency and precision of the low code rate video super-resolution reconstruction; the decoding device part uses the very little auxiliary code stream provided by the coding terminal to guide the super-resolution reconstruction of the decoding terminal; the coding device part uses the very little super-resolution constructed by pre-decoding closed loop feedback with super-resolution reconstruction to reconstruct the auxiliary code stream, and uses a human eye interested region analyzing module in the coding module to guide and correct with the emphasis on the super-resolution reconstruction of the human eye interested region, to further improve subjective quality input by video decoding. Compared with common video super-resolution ''blind'' reconstruction, the invention reduces complexity of the super-resolution reconstruction obviously, improves the reconstruction efficiency, meanwhile strengths the adaptive capacity of the super-resolution reconstruction to the high dynamic and diversified video image data, and improves the reconstruction precision.
Owner:SHANGHAI JIAO TONG UNIV
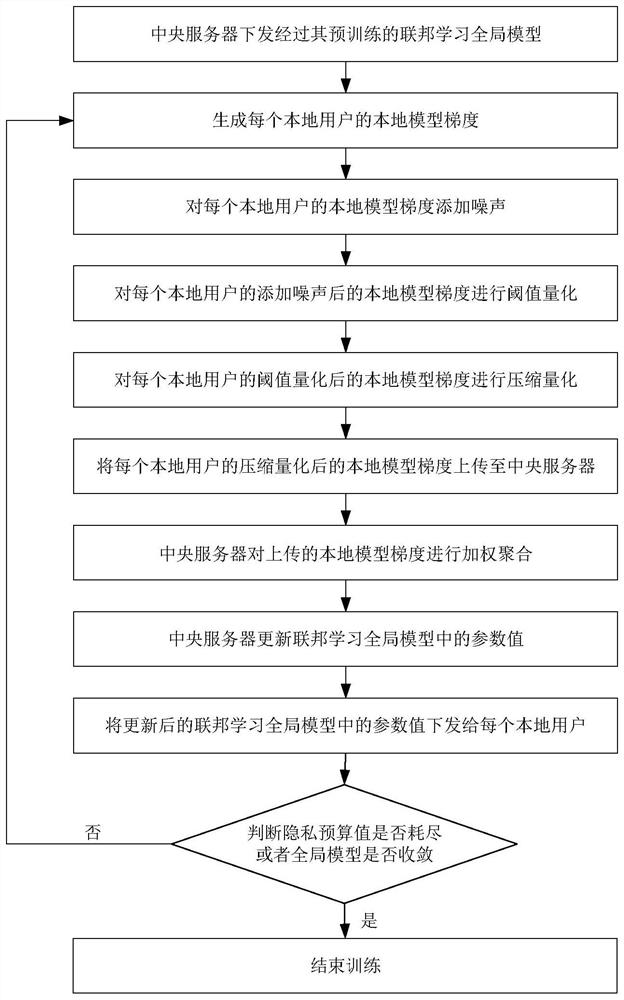
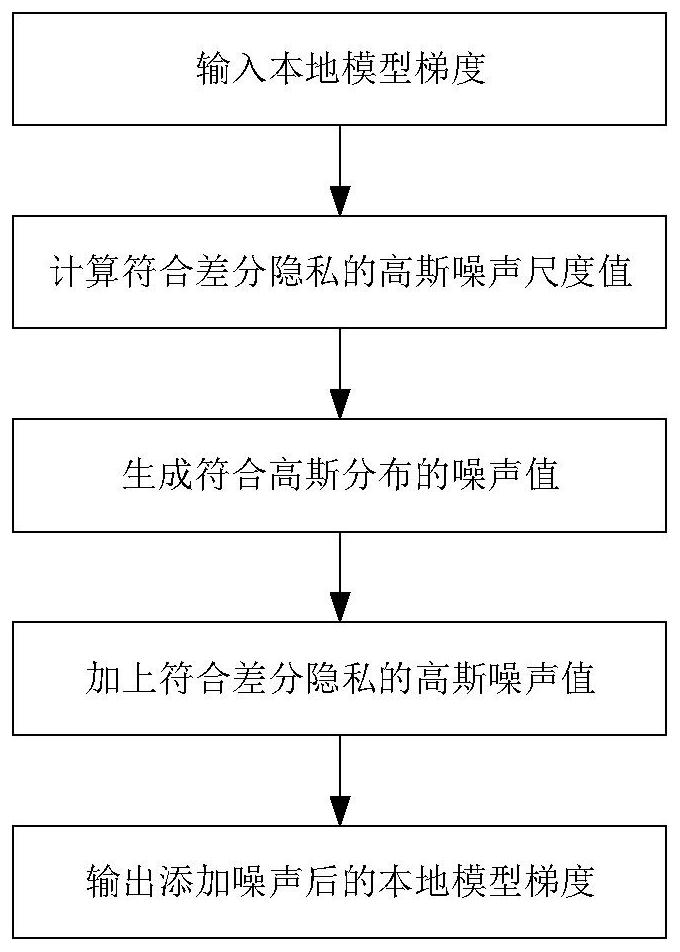
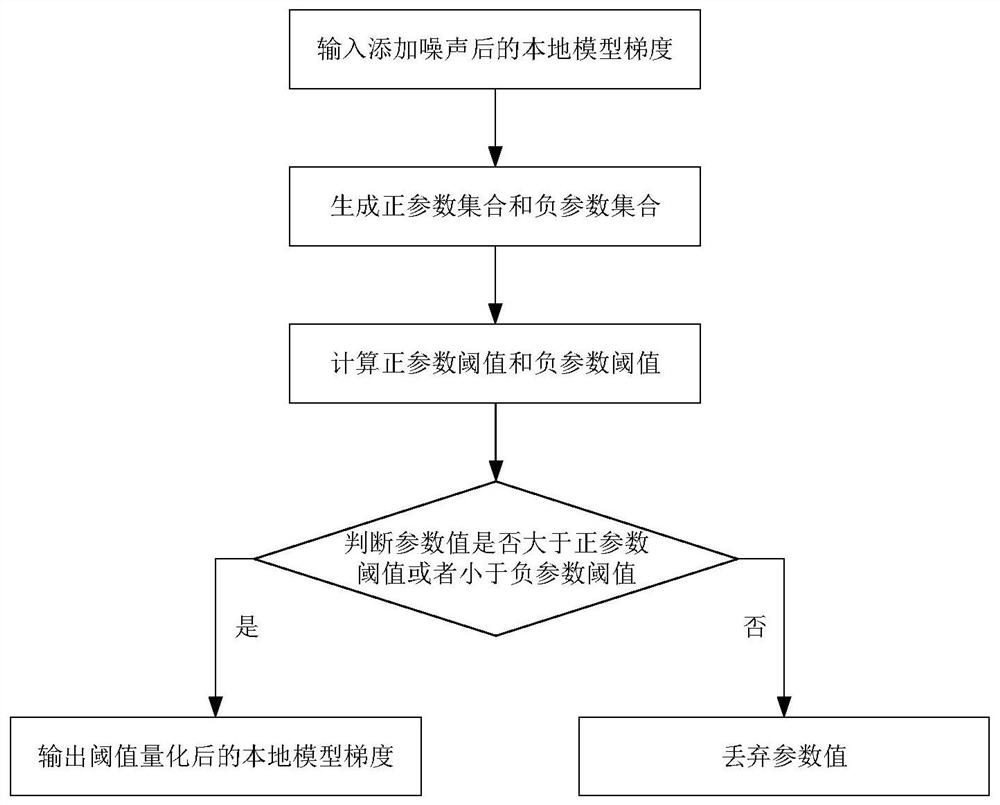
Federal learning global model training method based on differential privacy and quantification
PendingCN113591145APrivacy protectionGuaranteed accuracyDigital data protectionMachine learningDifferential privacyEngineering
A federated learning global model training method based on differential privacy and quantification comprises the following steps that a central server issues a pre-trained federated learning global model, a local model gradient of each local user is generated, and noise adding, threshold quantification and compression quantification is sequentially performed on the local model gradient of each local user, and the compressed and quantified local model gradient is uploaded to the central server, the central server performs weighted aggregation on the uploaded local model gradient by the central server, updates a global model, issues the global model to each local user, and training is ended when the privacy budget value of each local user is exhausted or the federal learning global model is converged. According to the method, on the premise that the precision of the federal learning global model is not lost, the privacy of local users is protected, the communication overhead in the transmission process is reduced, and the training efficiency of the federal learning global model is improved.
Owner:XIDIAN UNIV
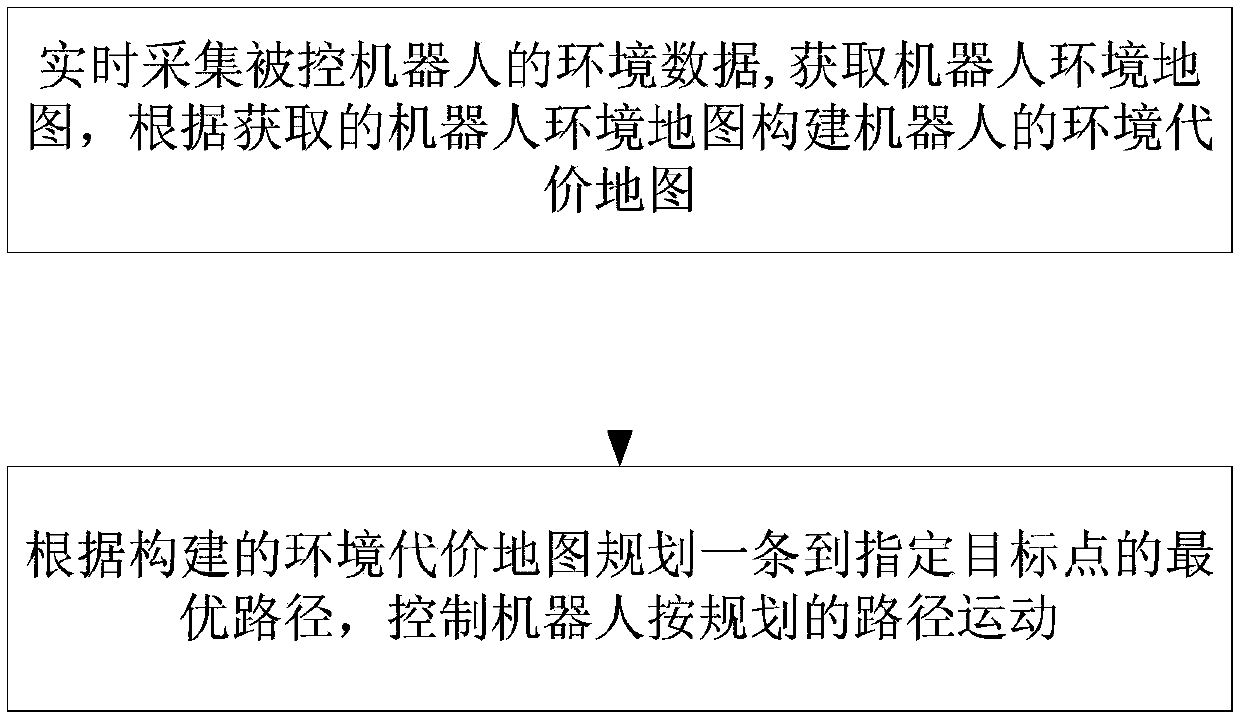
Robot behavior control method based on virtual reality
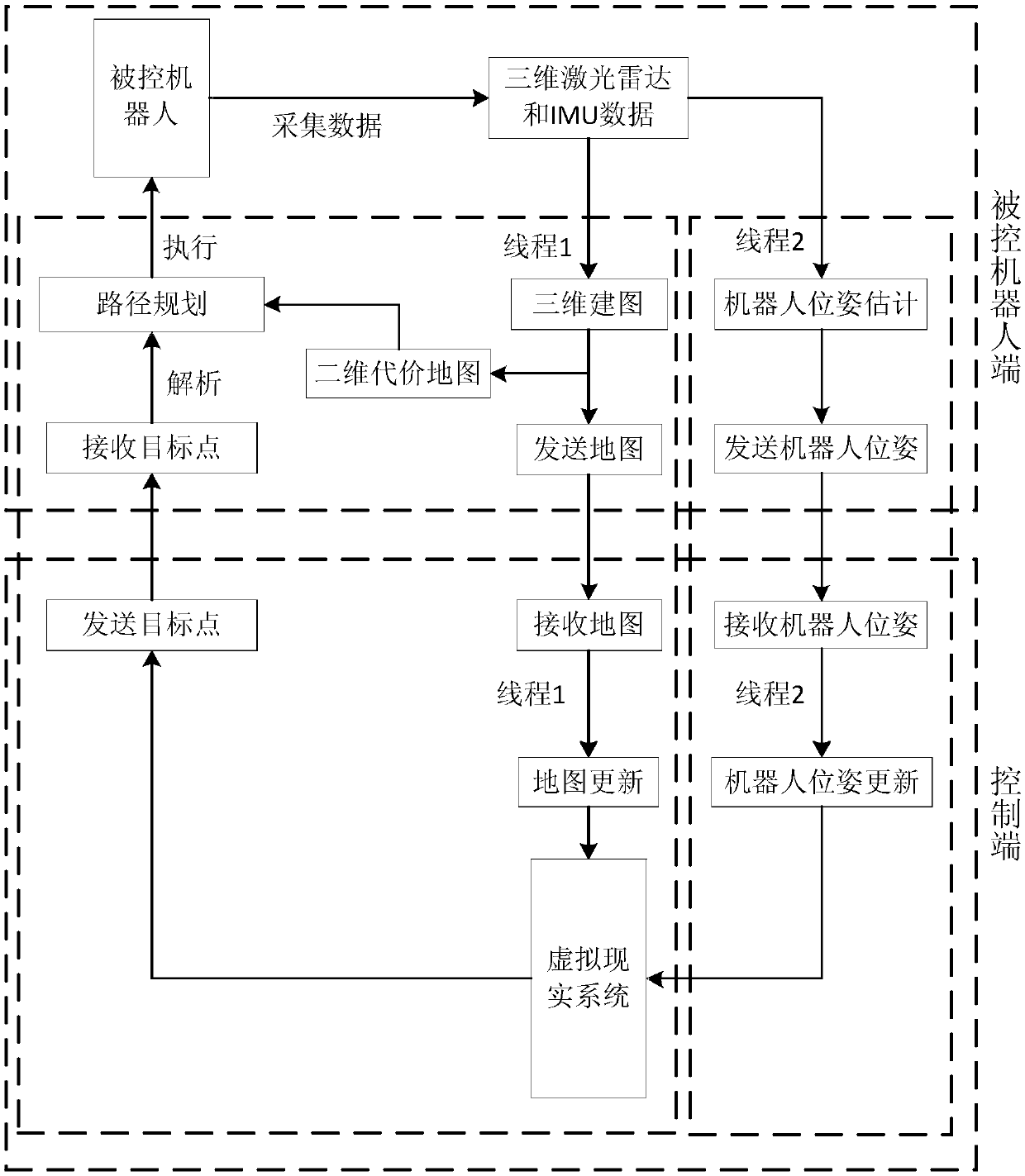
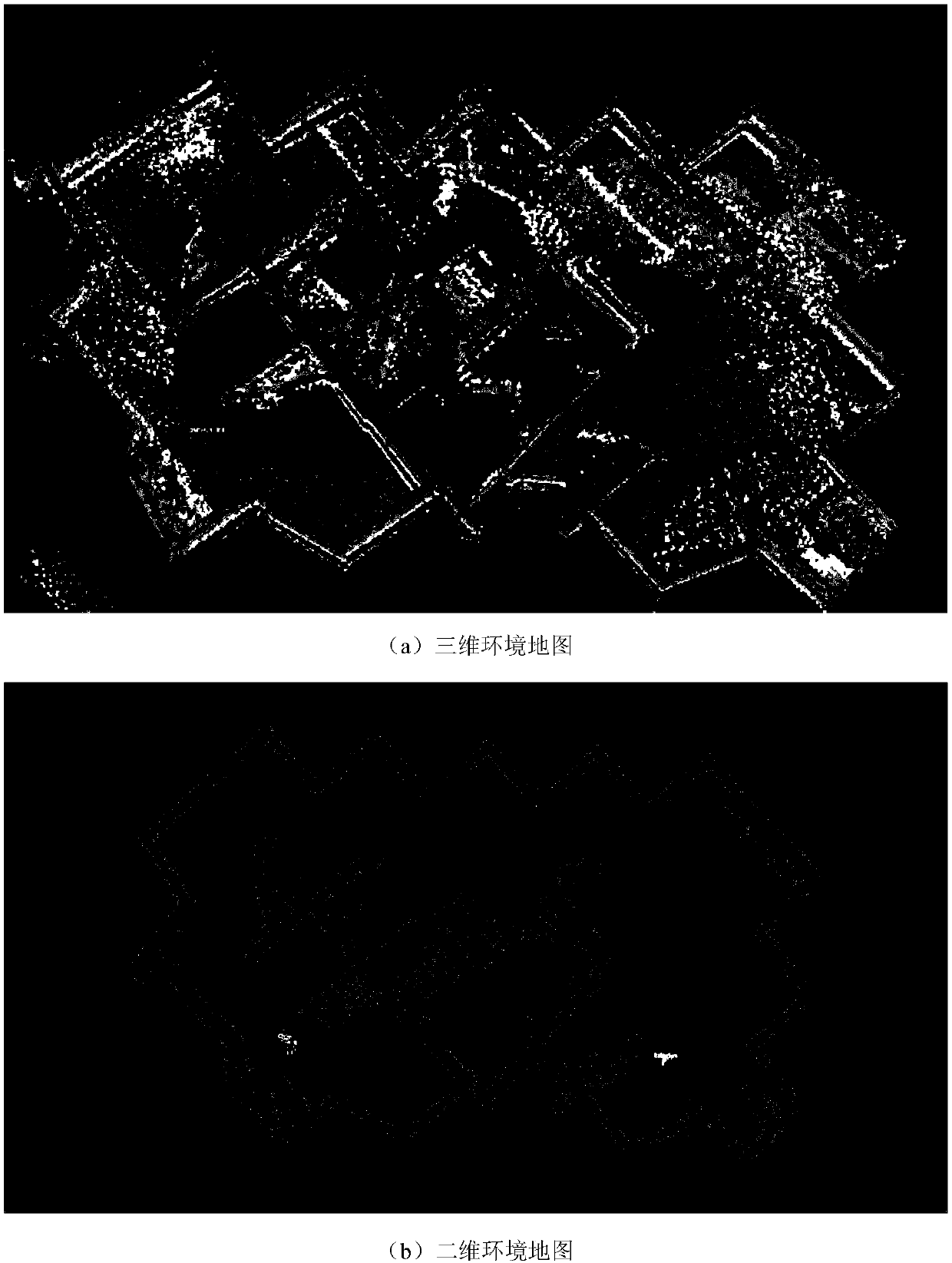
ActiveCN108908330AImprove real-time performanceImprove application flexibilityProgramme-controlled manipulatorRobot environmentSimulation
The invention discloses a robot behavior control method based on virtual reality. The control method includes the steps of S1, after environmental data of a controlled robot is collected in real timeto obtain a robot environment map, constructing an environmental cost map of the robot according to the obtained robot environment map; S2, according to the constructed environmental cost map, planning an optimal path to an assigned target point, controlling the robot to move according to the planned path. The method has the advantages of being easy to control, small in demanded communication bandwidth, high in timeliness, control precision and efficiency, flexible to use and the like.
Owner:NAT UNIV OF DEFENSE TECH
Multi-identity selection landing device and service system
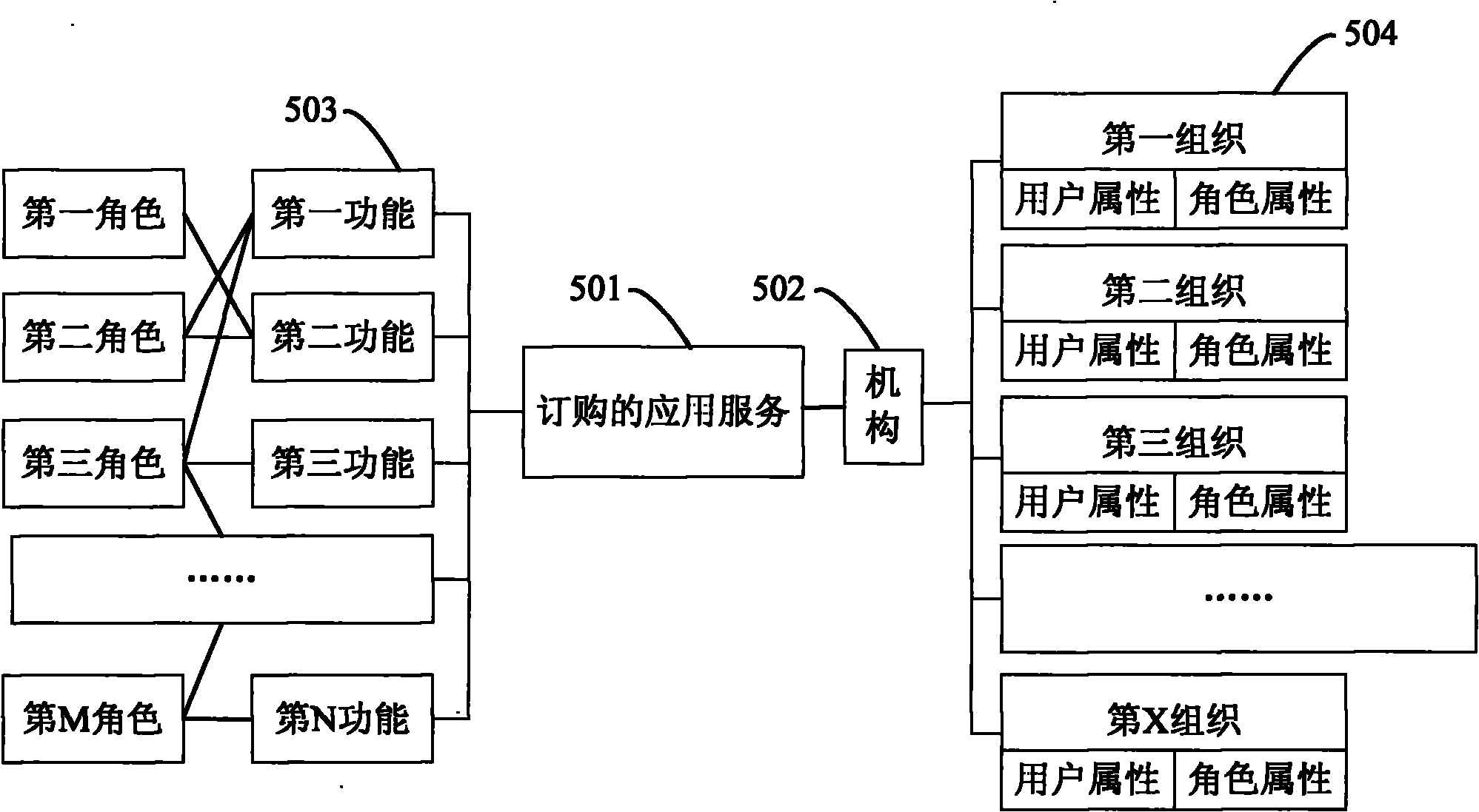
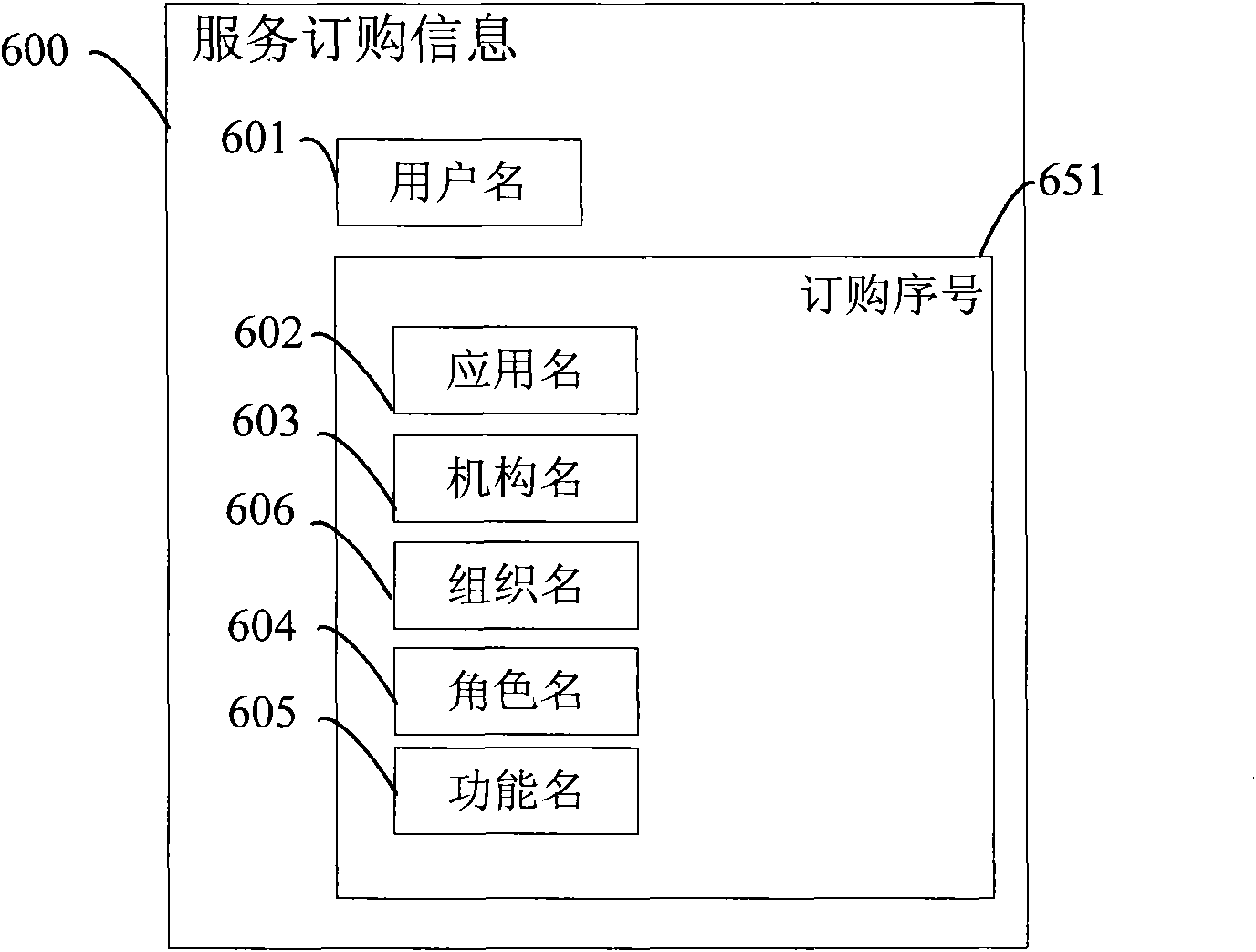
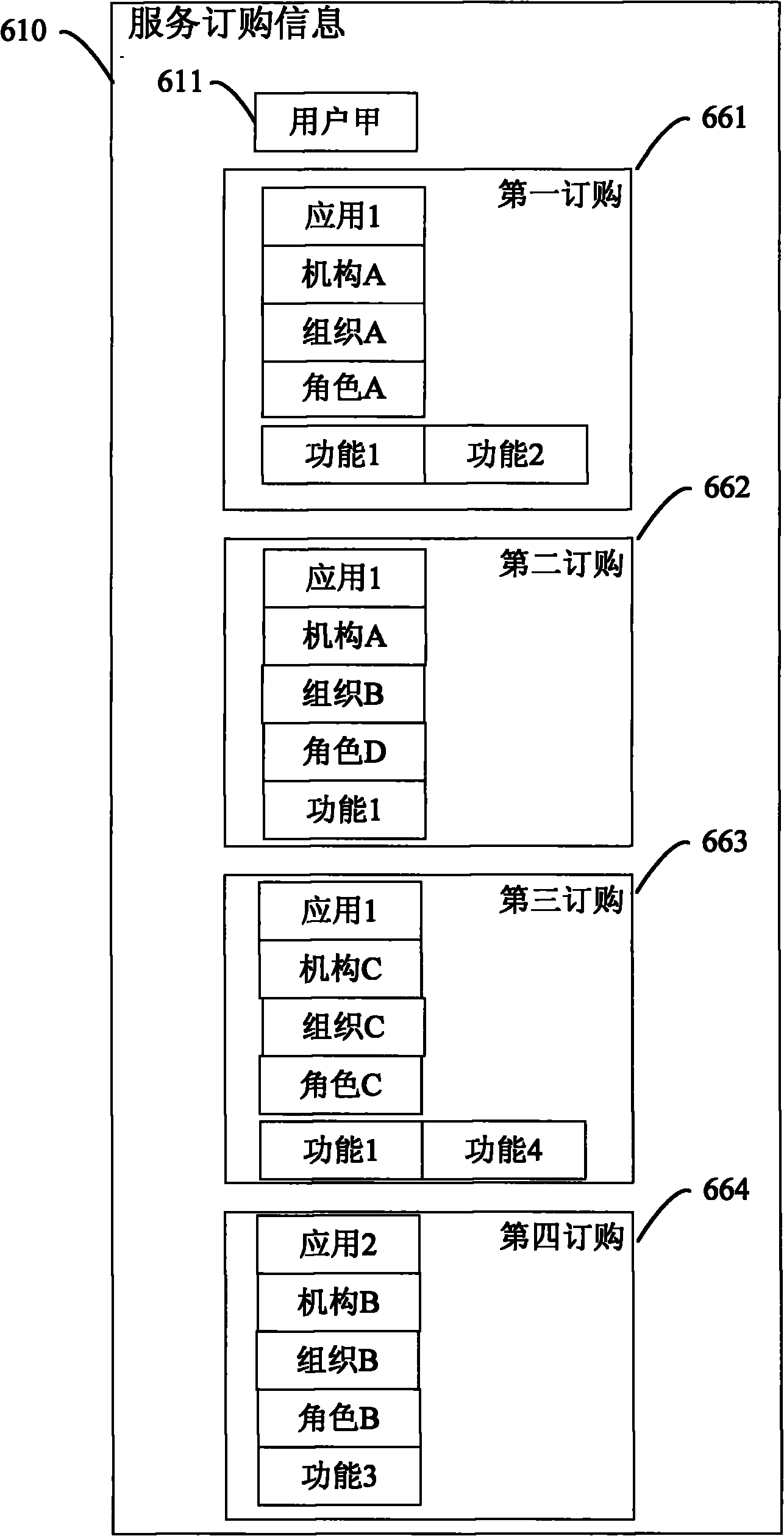
InactiveCN101977184AReduce access requestsSave communication bandwidthTransmissionCommerceTerminal equipmentEngineering
The invention provides a multi-identity selection landing device and a service system. The multi-identity selection landing device is suitable for being coupled with a terminal device and comprises a landing request processing unit, a service order information acquisition unit and a service calling token acquisition unit, wherein the landing request processing unit is suitable for receiving and verifying a landing request from the terminal device; the service order information acquisition unit is coupled to the landing request processing unit, is suitable for being activated by active data generated by the landing request processing unit after passing verification and is used for acquiring user-matched service order information corresponding to the landing request and feeding the user-matched service order information back to the terminal device; and the service calling token acquisition unit is suitable for receiving a service order selection request based on the service order information from the terminal device and is used for acquiring a service calling token and feeding the service calling token back to the terminal device.
Owner:江苏西商钢铁贸易有限公司
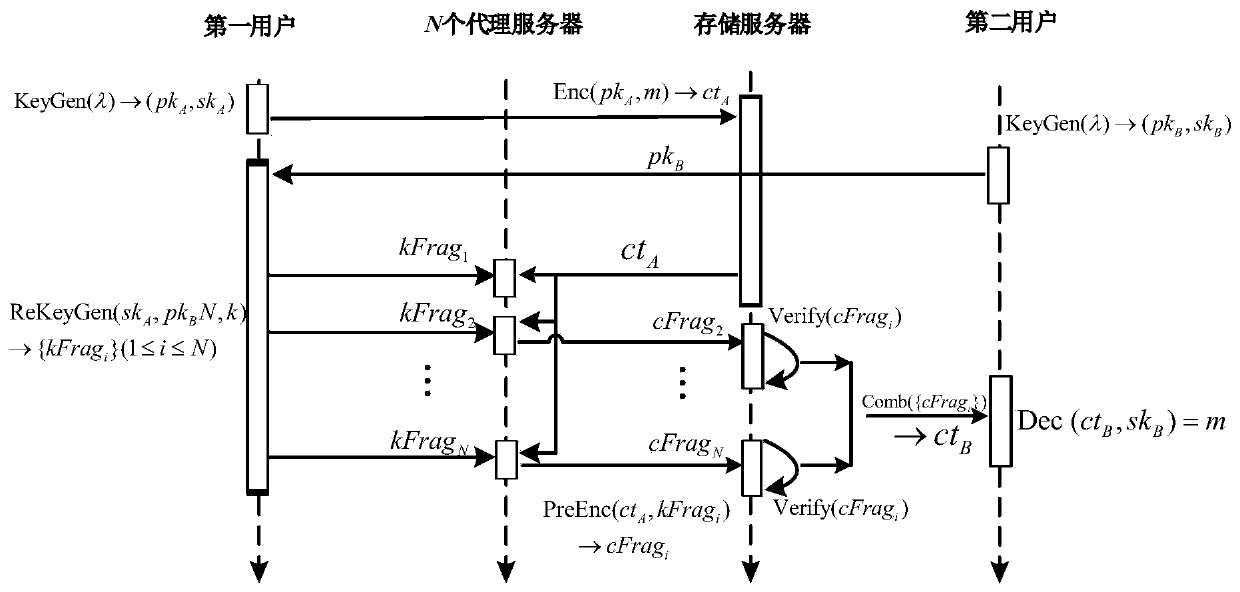
Verifiable ideal on-grid threshold proxy re-encryption method and verifiable ideal on-grid threshold proxy re-encryption system
ActiveCN111342976ADetect dishonesty in timeTimely detection of malicious conversion behaviorKey distribution for secure communicationUser identity/authority verificationHomomorphic signatureAlgorithm
The invention belongs to the technical field of data encryption and privacy protection, and discloses a verifiable ideal on-grid threshold proxy re-encryption method and system, and the method comprises the following steps: generating a first public and private key and a second public and private key through a KeyGen algorithm; encrypting the original message according to the first public key to generate a ciphertext; generating an agent key through a ReKeyGen algorithm according to the first private key and the second public key, dividing the agent key into a plurality of key shares, and signing each key share through a homomorphic signature technology to obtain a plurality of key share signatures; converting the ciphertext into a plurality of ciphertext shares according to the pluralityof key shares, and converting the plurality of key share signatures into a plurality of ciphertext share signatures; verifying the legality of the corresponding ciphertext share according to each ciphertext share signature; combining the legal ciphertext shares into a re-encrypted ciphertext; decrypting the re-encrypted ciphertext according to the second private key to get the original message. According to the invention, the method and system have the advantages of high availability, low trust and strong security, can effectively resist quantum attacks, and is high in encryption efficiency.
Owner:ENG UNIV OF THE CHINESE PEOPLES ARMED POLICE FORCE
FPGA-based micro-illumination control method for programmable LED array
ActiveCN108200687ASimplify communicationIncrease frame rateElectrical apparatusElectroluminescent light sourcesDriving currentGraphics
The invention discloses an FPGA-based micro-illumination control method for a programmable LED array. The method comprises the steps of firstly carrying out FPGA-based serial port receiving and decoding circuit design; calculating basic data of graphics for programmable LED array display on site according to a control instruction and carrying out circle area determining, in-circle brightness standard normal distribution and color area division and then classifying and storing the data into on-chip dual-port RAMs of an FPGA; reading out display data in the on-chip dual-port RAMs of the FPGA according to a scanning position of the programmable LED array; and finally quickly driving the programmable LED array, of using multi-row scanning, with separate three RGB channels in parallel by usingthe FPGA and displaying output data. According to the FPGA-based micro-illumination control method for the programmable LED array, a large number of external storage devices are saved, the programmable LED array is driven by using the FPGA, and graphic display and PWM modulation of drive current are achieved.
Owner:NANJING UNIV OF SCI & TECH
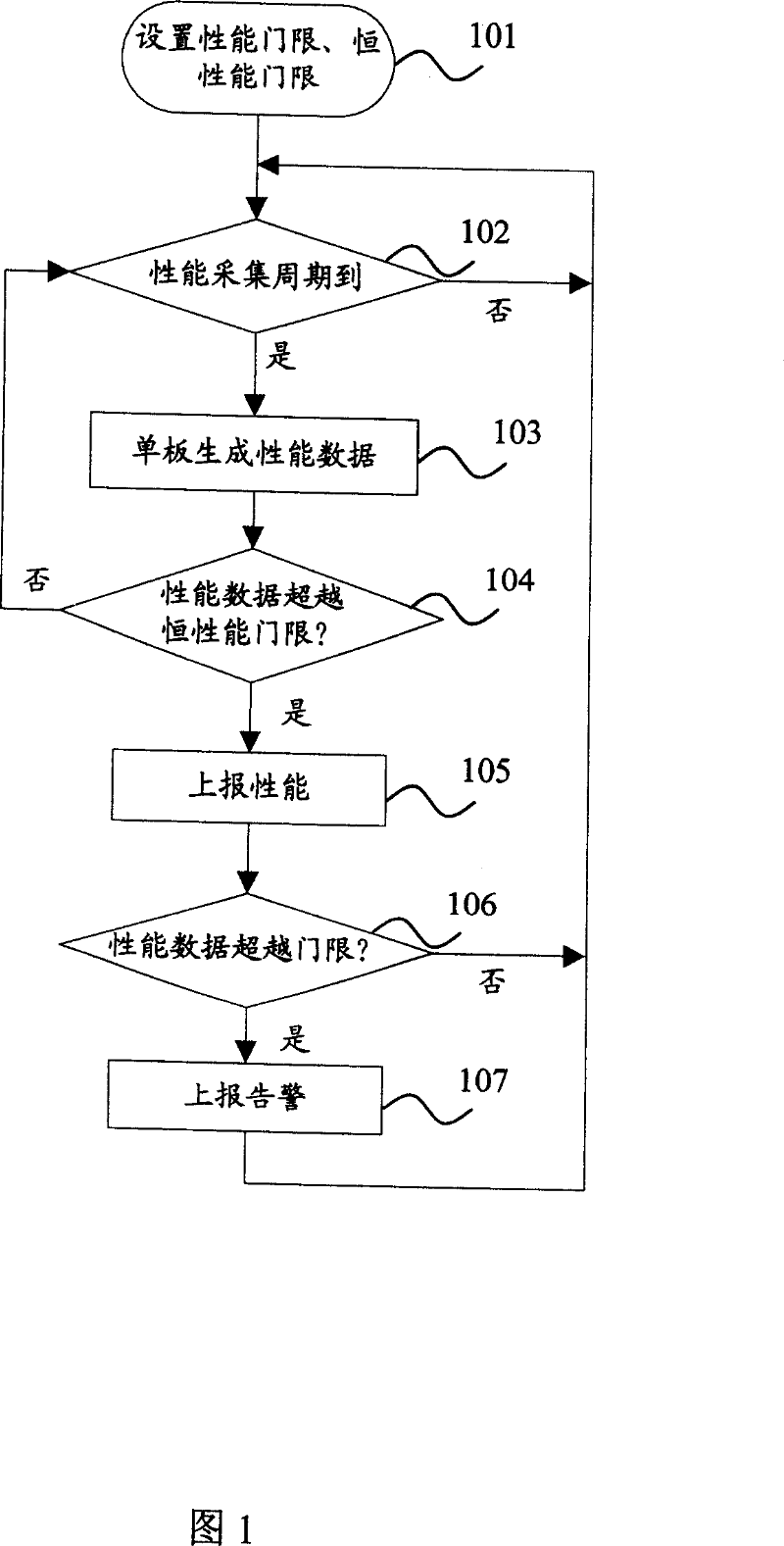
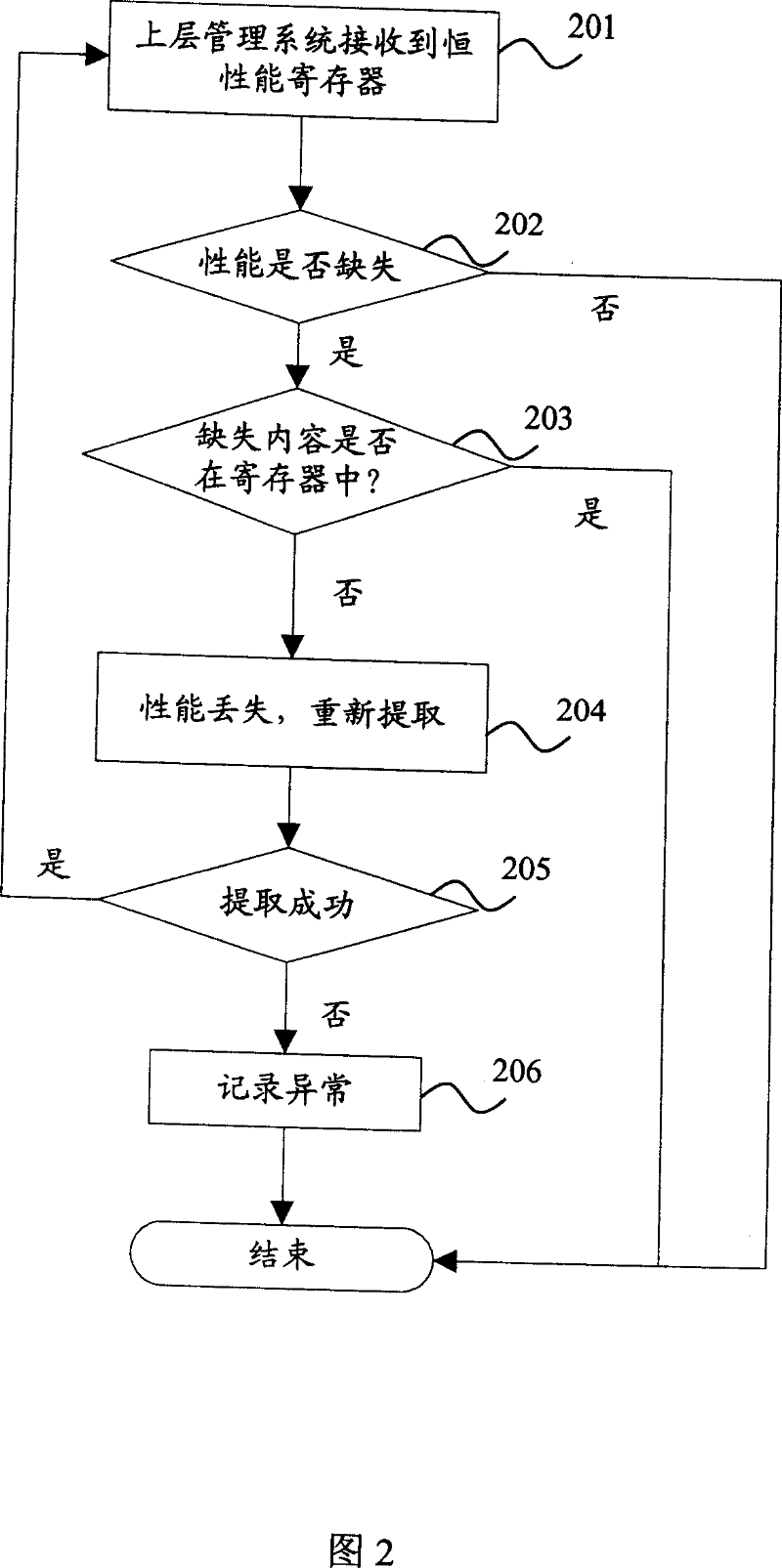
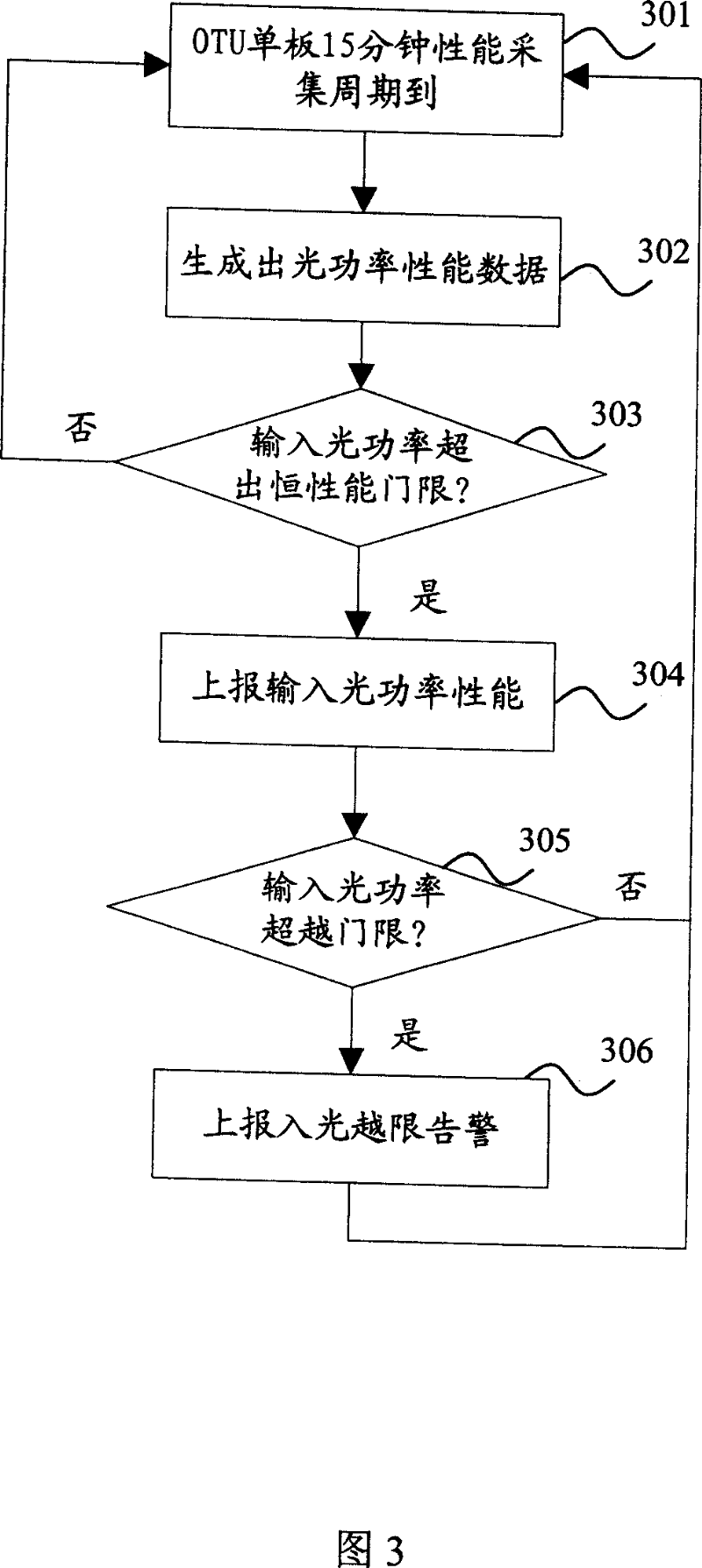
Method for reporting board performance data of equipment
InactiveCN101043371ASend lessConvenience to followPulse modulation television signal transmissionTelevision system scanning detailsSystem maintenancePerformance index
The provided performance data report method for device single board comprises: (1) according to the normal fluctuation range of every performance index of board, setting a 'constant performance threshold' for every performance data; (2) collecting performance data; (3) comparing current monitored data with former threshold; and (4) if current data over the threshold, reporting the current data; or else, inhibiting the report. This invention reduces data quantity and CPU load, as well as the requirements of network element controller for data processing and storage room.
Owner:ZTE CORP
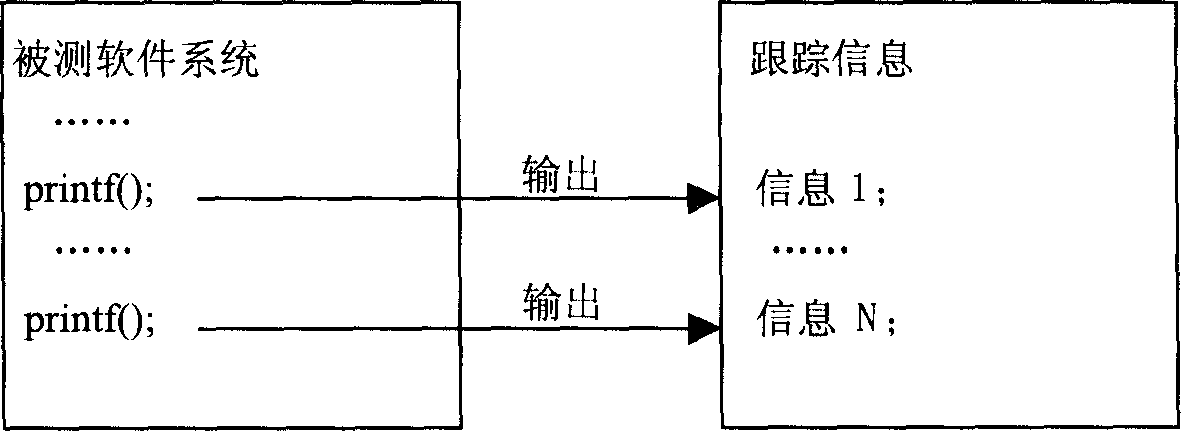
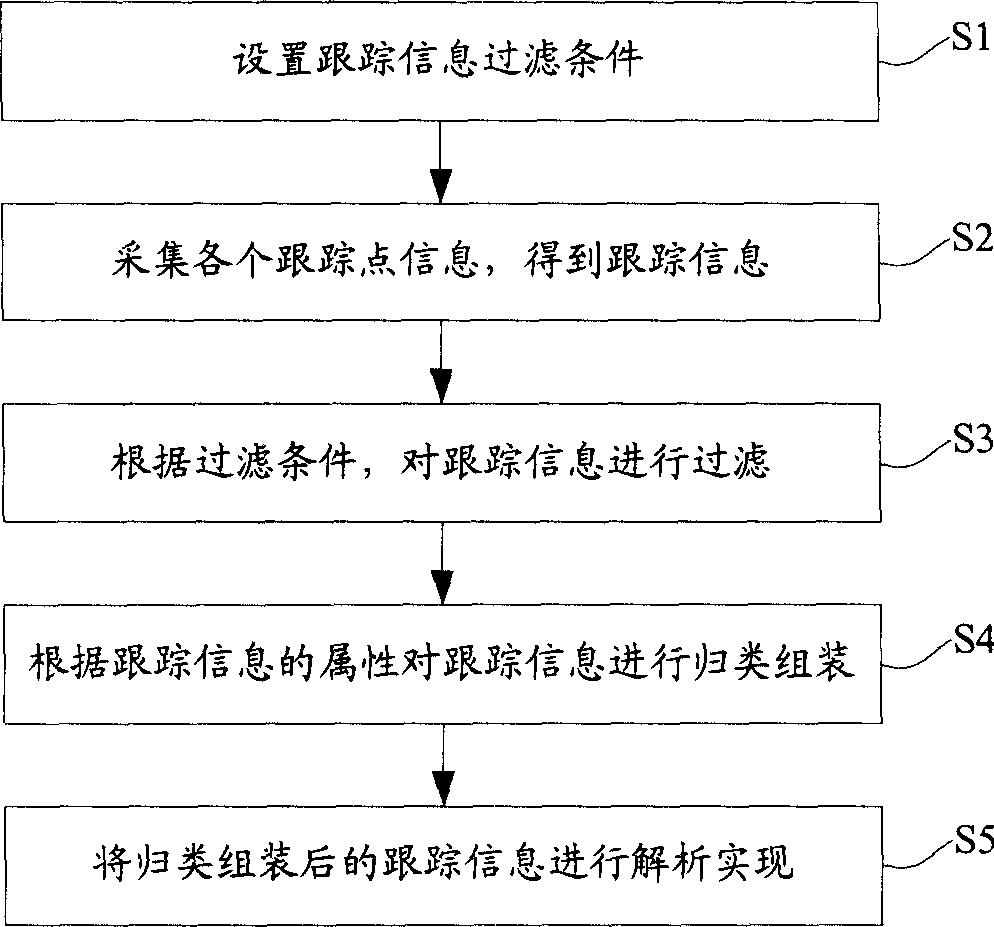
Method of software trace and system therefor
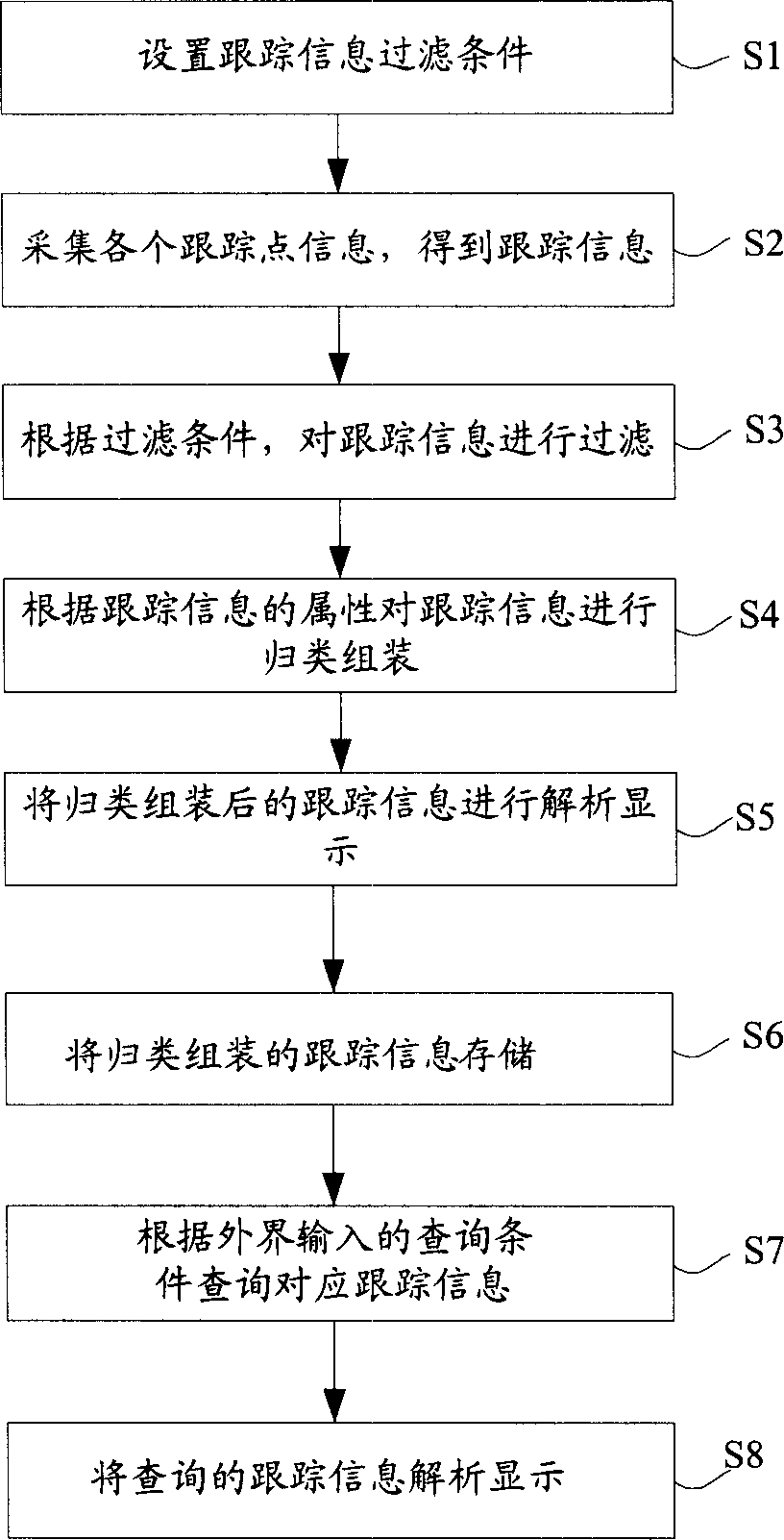
InactiveCN1731366ASave communication bandwidthReduce occupancySoftware testing/debuggingSizingSoftware engineering
The invention provides a software tracing method, which comprises the following steps: arranging tracing information filter condition; collecting the information of each tracing point in the tested software system to obtain the tracing information; filtering the tracing information by the filter condition; sizing and composing the tracing information by the attribute; doing analysis display to the sized and composed information. The invention also provides a software tracing system.
Owner:HUAWEI TECH CO LTD
Safety communication method suitable for remote control with limited capability at controlled end
InactiveCN101931623AImprove confidentialityLimited number of solutionsError prevention/detection by using return channelSecure communicationTelecommunications link
The invention discloses a safety communication method suitable for remote control with a limited capability at a controlled end. The method comprises the following steps of: setting password sets at a control end and the controlled end and generating a password set according to an input initialization password by an irreversible method, wherein the password set comprises an index number and the password per se and encryption and decryption are performed by using the password corresponding to the recorded index number in a normal communication process; when the password is asynchronous, transmitting the index number by encrypting to perform password synchronization; and when a password set updating condition is met, negotiating about the update of the password set by transmitting a selected index number. A password set generating device for calculating the password set and communicating with the controlled end only when the password set is needed to be generated is arranged at the controlled end. Various attacks are resisted effectively by using a dynamic password and operation of real-time password calculation needed by the transmission of each data packet is avoided. Simultaneously, the password per se does not need to be transmitted on a communication link in password synchronizing and password set updating processes, so that simpleness and safety are realized.
Owner:SOUTH CHINA UNIV OF TECH
Low-energy-consumption remote storage system and design method thereof
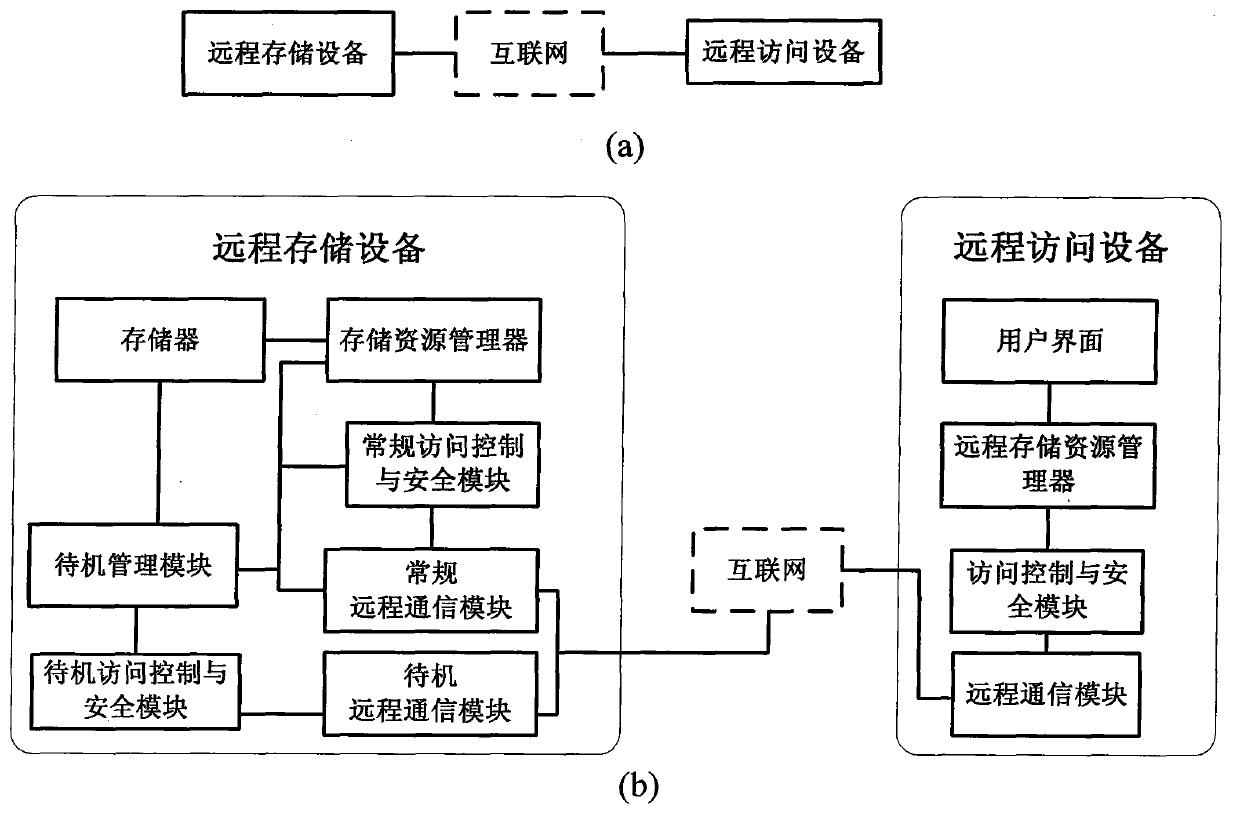
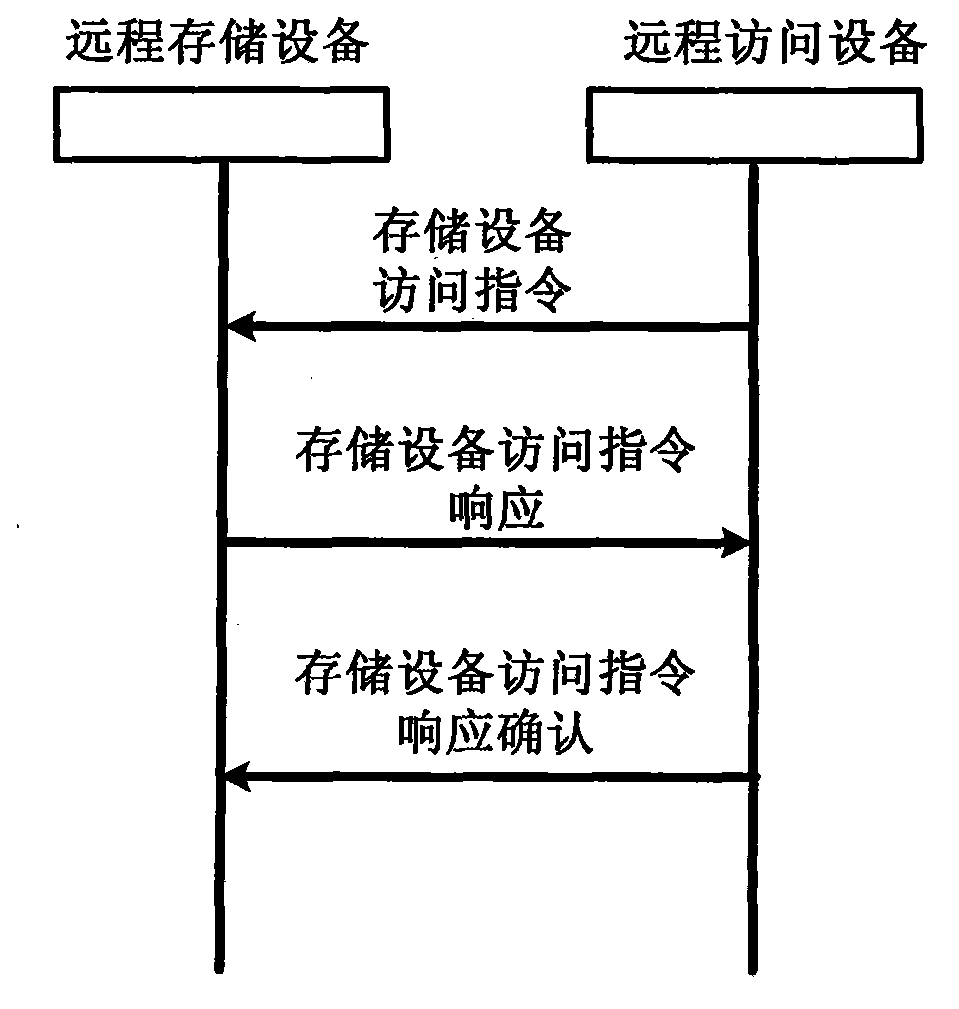
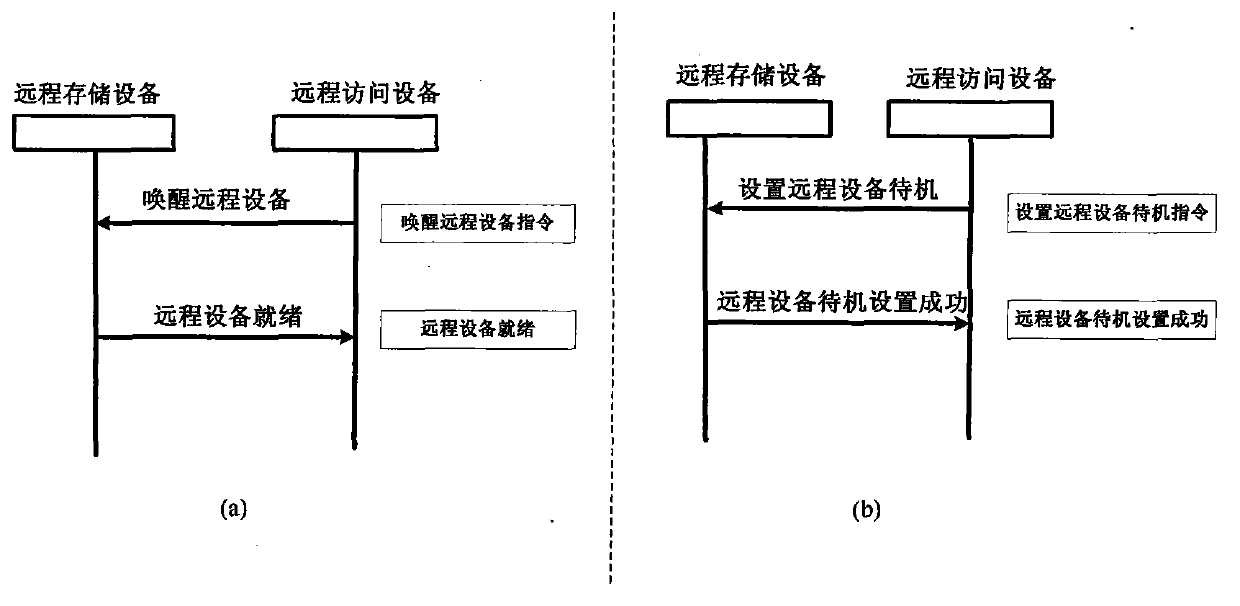
InactiveCN103873540AIncrease capacityReduce lossUnauthorized memory use protectionPower supply for data processingEnd-to-end encryptionNetwork communication
The invention relates to a low-energy-consumption remote storage system and a design method thereof, in particular to a method of remote data storage by utilizing network communication, and a storage system, and belongs to the technical field of network communication and data storage. The remote storage system comprises a remote storage device and a remote access device, and has normal and standby work modes. The remote storage device comprises a storer, a storage resource manager, a normal access control and security management module, a standby access control and security management module, a normal remote communication module, a standby remote communication module and a standby management module, and the remote access device comprises a user interface, a remote storage resource manager, an access control and security module, and a remote communication module. In the period that the storer does not carry out an access operation, the storage device is in a low-power-consumption or power-off state, the energy consumption is effectively reduced; the end-to-end encryption can be performed, and the basic guarantee of the security of data resources of the user is provided.
Owner:李祥明 +2
Wireless sensor network abnormal event detection method and system based on secondary mixed compression
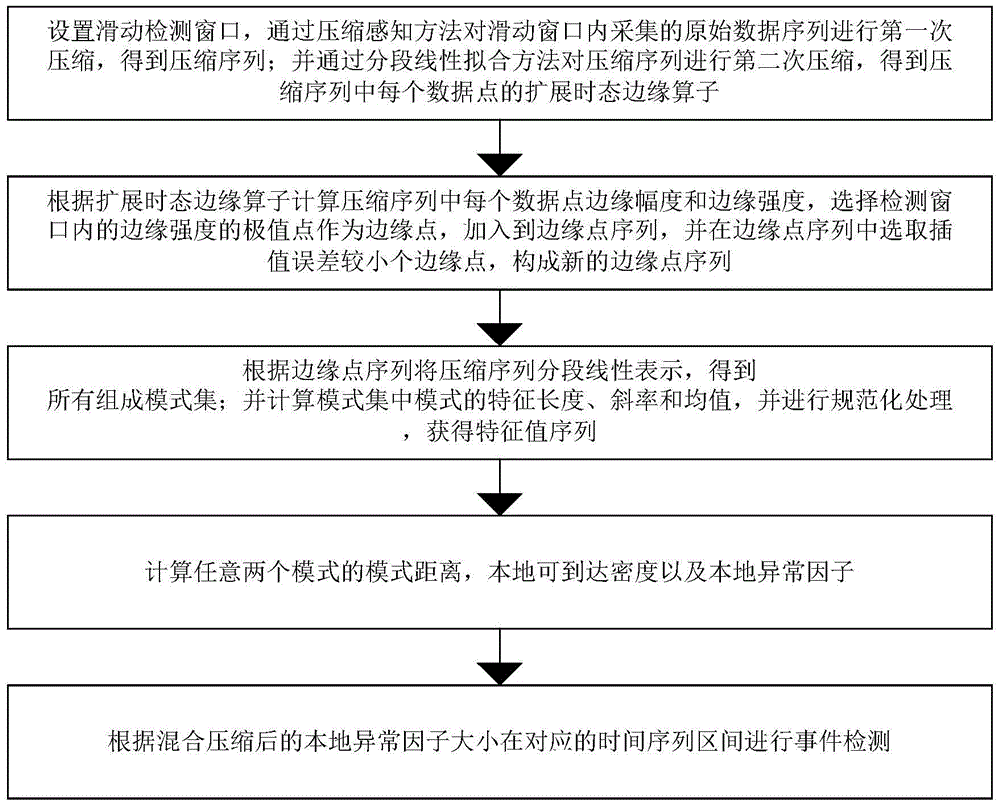
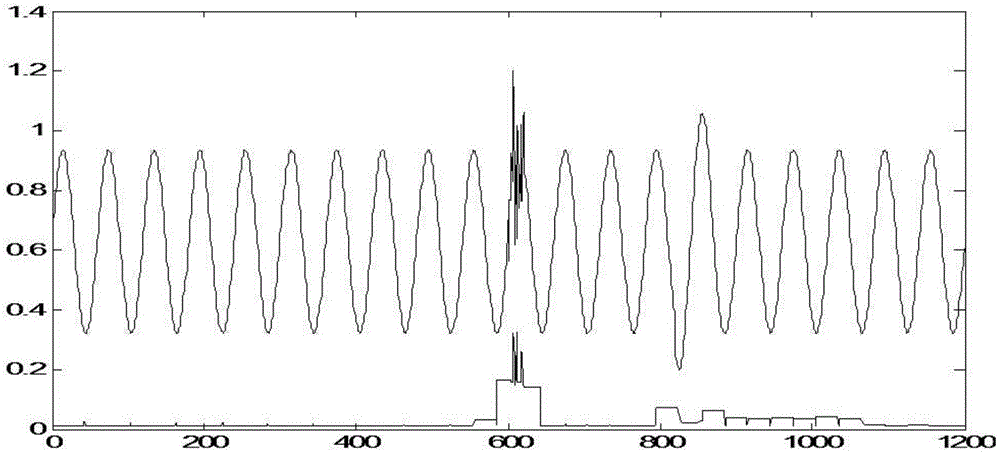
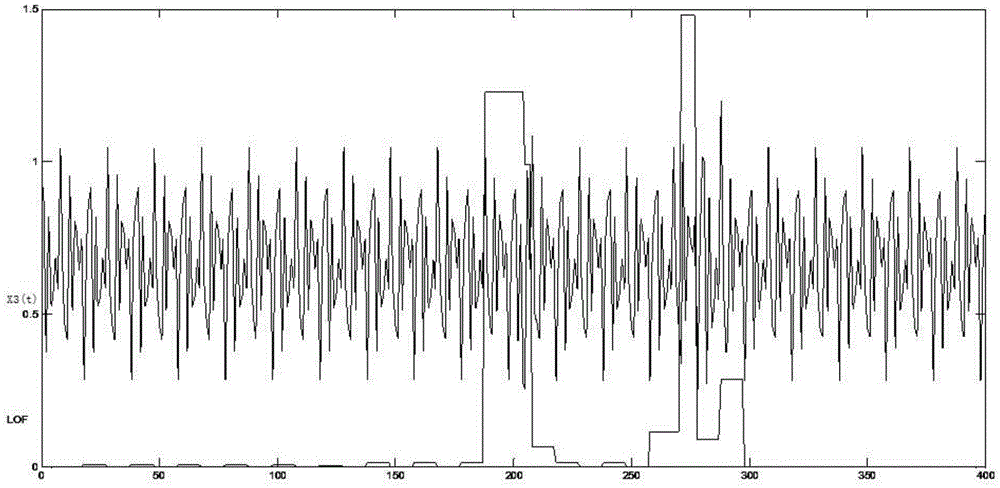
InactiveCN105491614ASmall amount of calculationEfficient discoveryNetwork topologiesHigh level techniquesOriginal dataPoint sequence
The invention discloses a wireless sensor network abnormal event detection method and system based on secondary mixed compression. The method comprises the steps that S1. primary compression is performed on original data sequences by a compression sensing method; and secondary compression is performed on the compressed sequences by a piecewise linear fitting method so that state edge operators are obtained; S2. edge amplitude and edge intensity of each data point in the compressed sequences are calculated, and new edge point sequences are formed by selecting edge points of low interpolation error from edge point sequences; S3. characteristic value sequences are obtained according to edge point sequences; S4. local accessible density and local abnormal factors are calculated; and S5. event detection is performed in corresponding time sequence intervals according to the size of the local abnormal factors after mixed compression. Search efficiency and abnormal data accurate positioning capacity of wireless sensor network nodes can be enhanced so that abnormal events can be more efficiently and rapidly found; and timeliness of abnormity detection can be enhanced so that energy and communication bandwidth can be greatly saved.
Owner:CHINA UNIV OF GEOSCIENCES (WUHAN)
Intelligent security and protection video monitoring method and system, and monitoring terminal
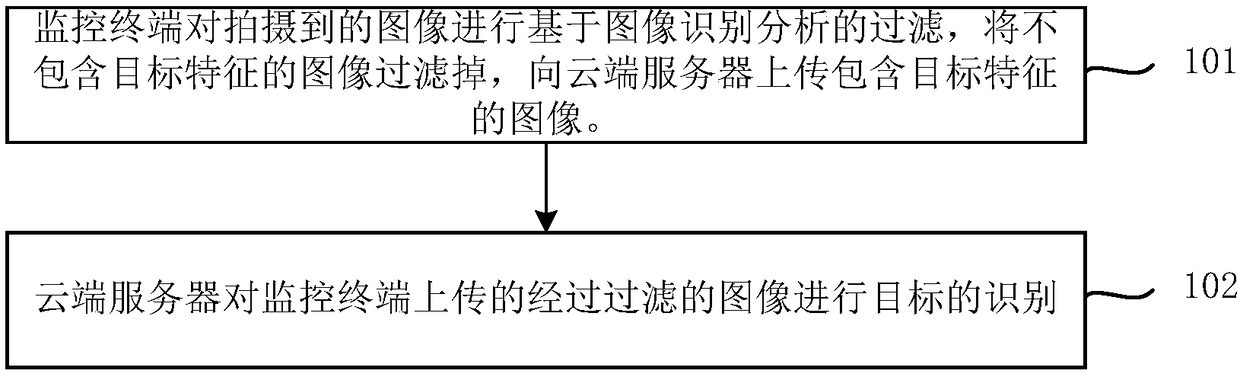
InactiveCN108920995AReduce video imageSave communication bandwidthCharacter and pattern recognitionClosed circuit television systemsVideo monitoringPattern recognition
The application relates to the field of intelligent monitoring, and discloses an intelligent security and protection video monitoring method and system, and a monitoring terminal. The flow of monitoring image uploading and the calculation amount of a cloud server can be greatly reduced without lowering the target recognition accuracy. In the present invention, the monitoring terminal performs filtering based on image recognition analysis on the captured image, filters images which do not include a target feature, and uploads an image containing the target feature to a cloud server; and the cloud server performs target recognition on the filtered image uploaded by the monitoring terminal.
Owner:HUAZHONG UNIV OF SCI & TECH
Computerized method of organizing and distributing electronic healthcare record data
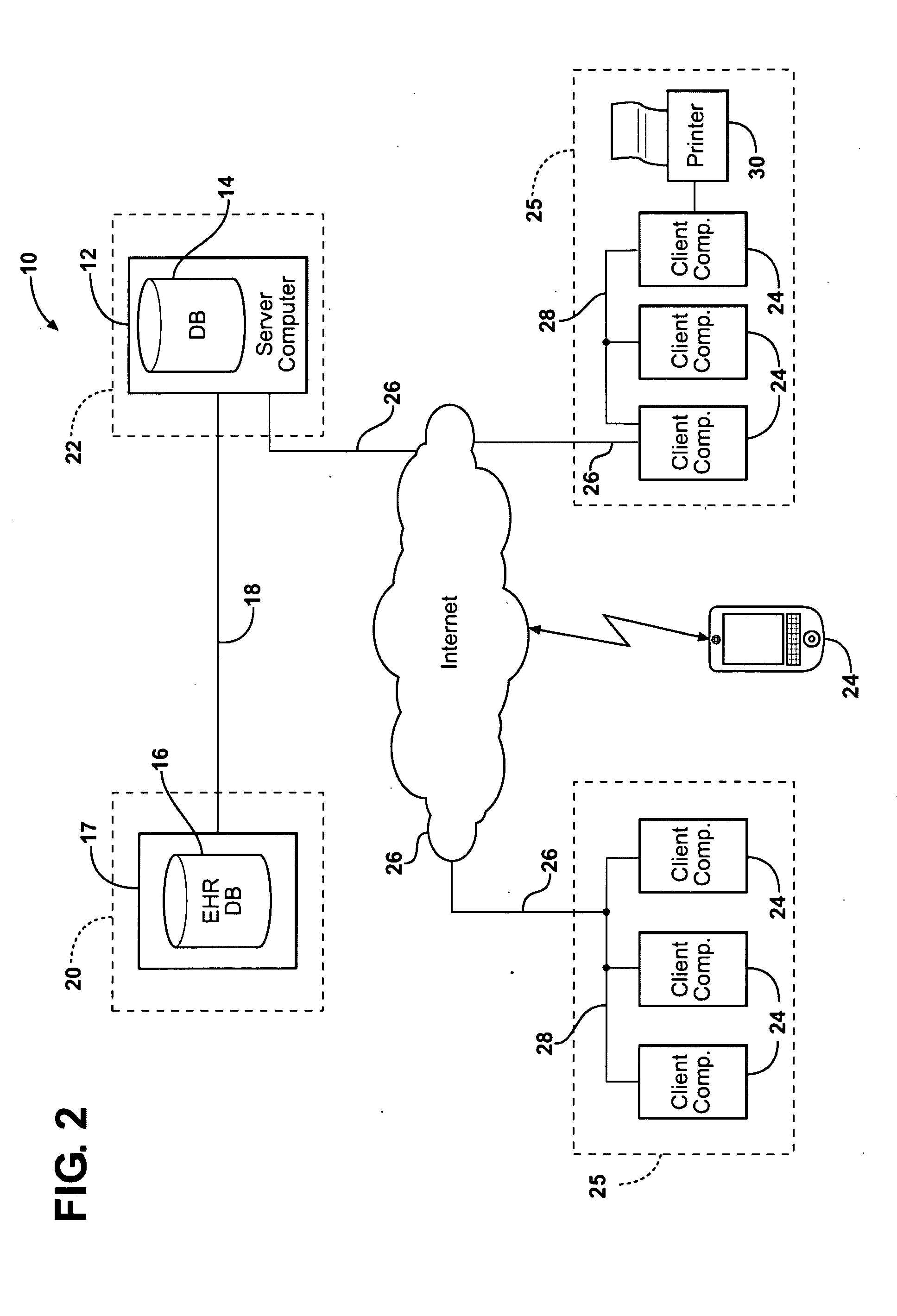
InactiveUS20110029592A1Quickly and efficiently analyzeSave communication bandwidthMultiple digital computer combinationsOffice automationClient-sideElectronic document
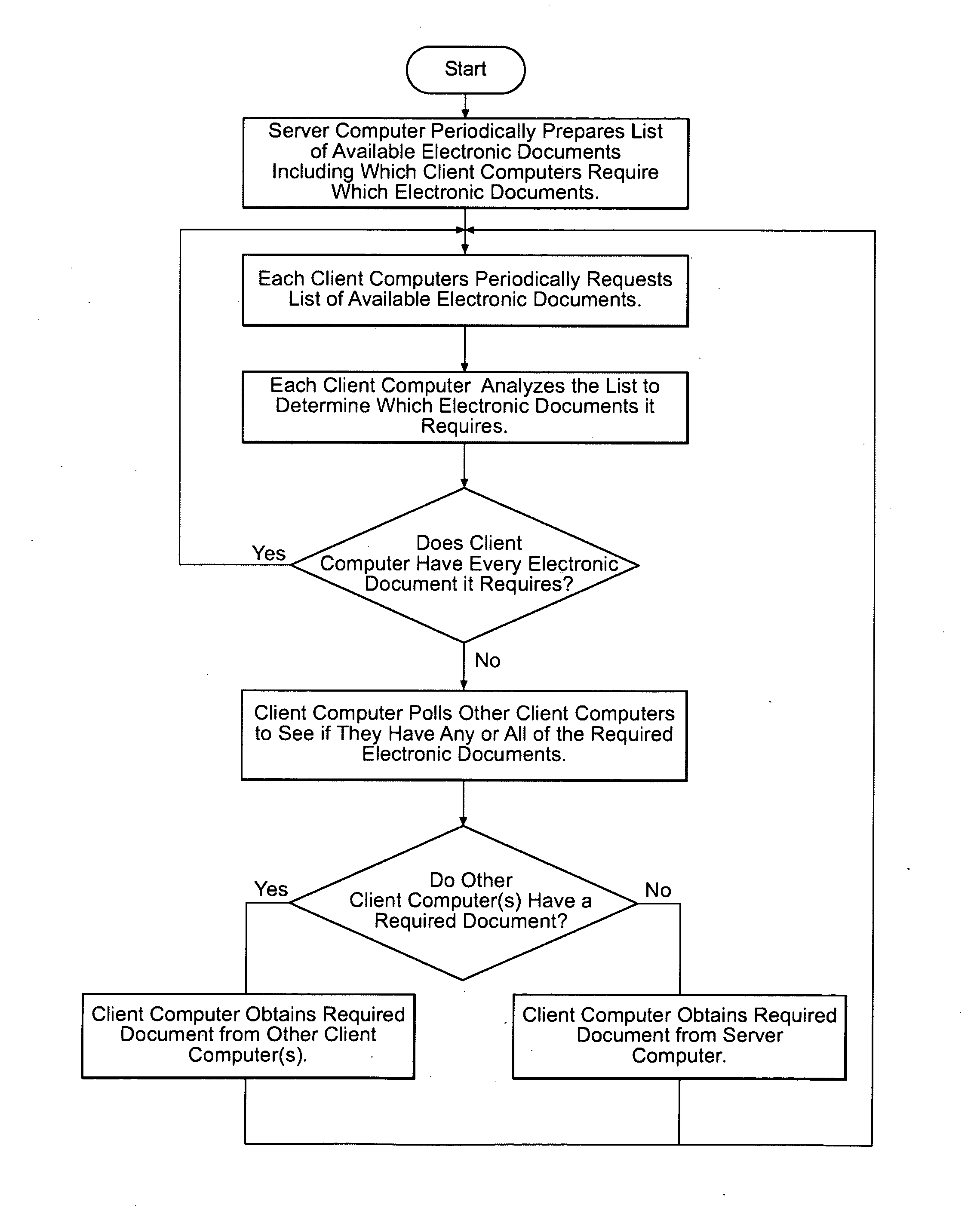
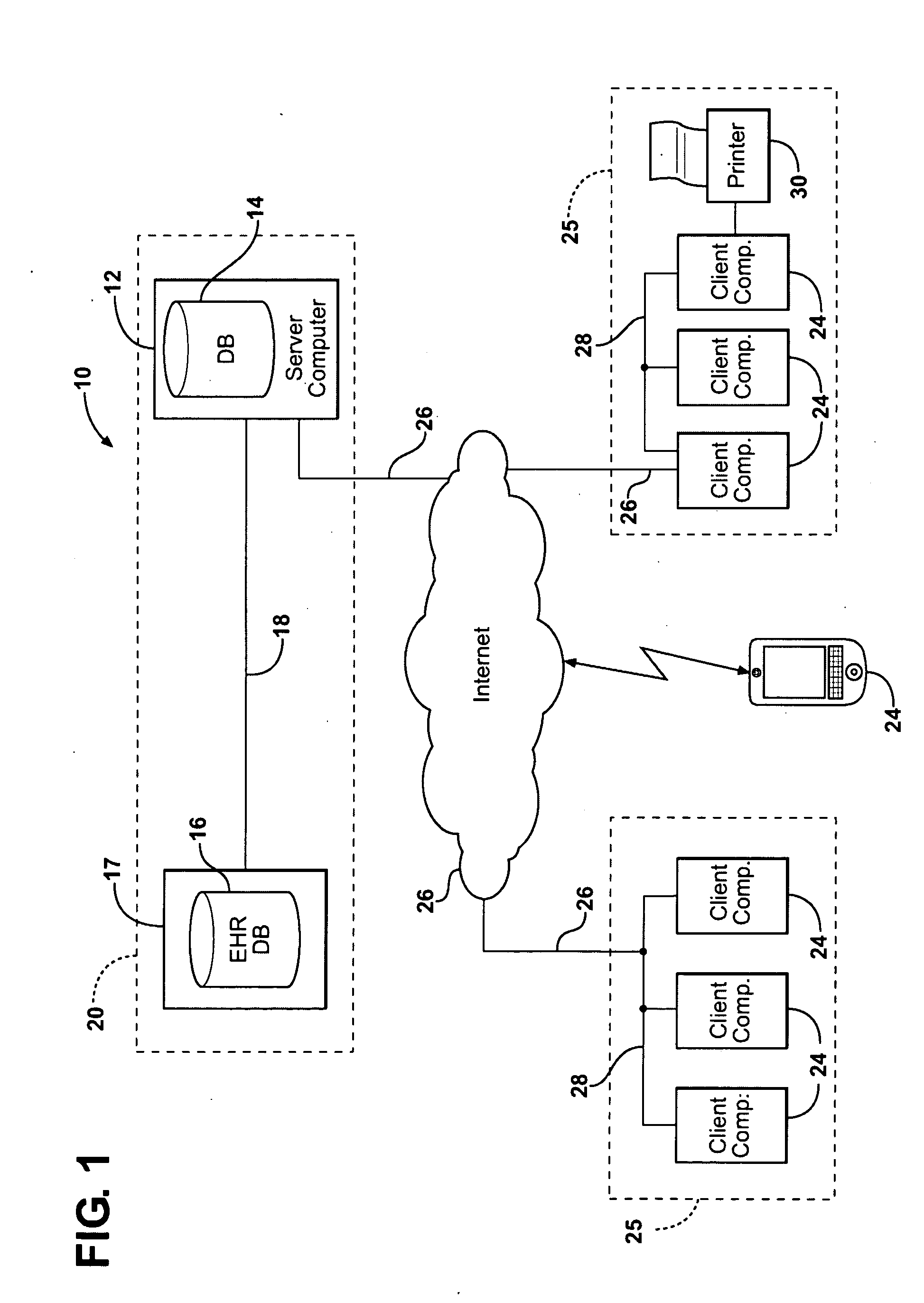
A system and method for organizing and distributing electronic healthcare records (EHRs) copies the EHRs from an EHR database to a separate, remote server computer. The remote server generates viewable and printable electronic documents from the EHRs while omitting information that is not needed by the healthcare professional viewing the electronic documents. Electronic documents for patient appointments in a predetermined window are transferred from the remote server to client computers located in a health care facility. The electronic documents may also be transferred between the client computers to save on network bandwidth from the server computer. The server computer routinely updates the electronic documents based on new EHRs received form the EHR database. Stale electronic documents with out-of-date information are tagged as such.
Owner:GALEN HEALTHCARE SOLUTIONS
Decoding method and decoding device
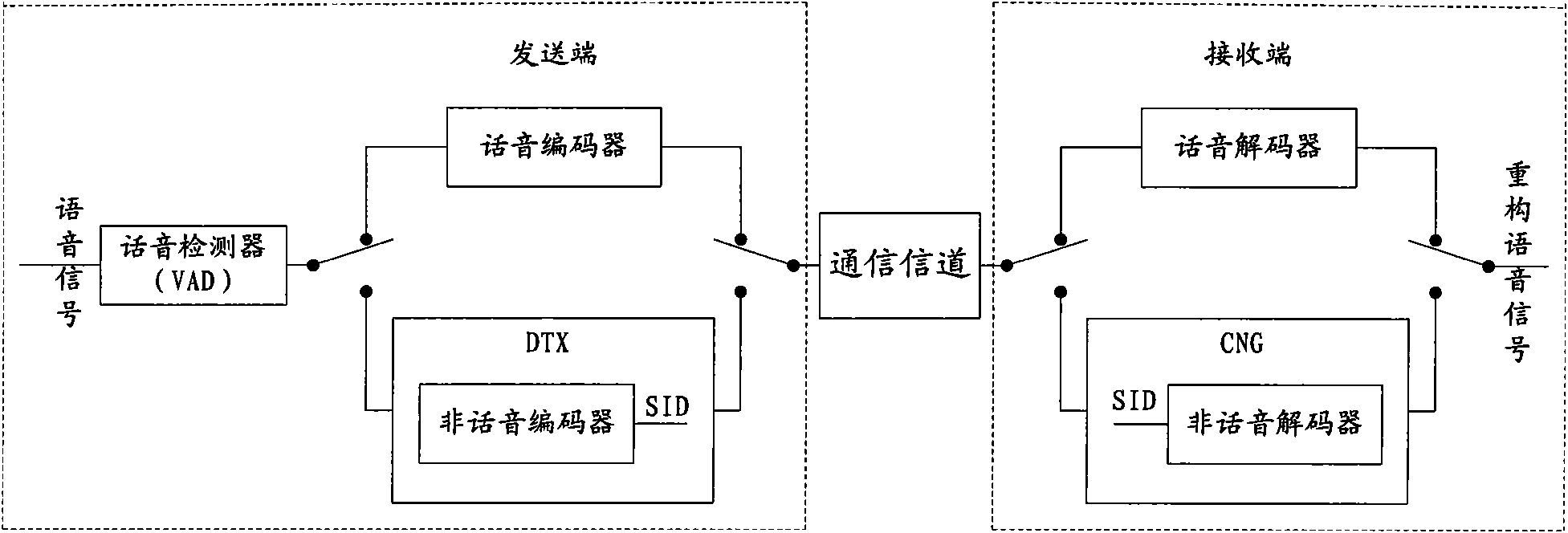
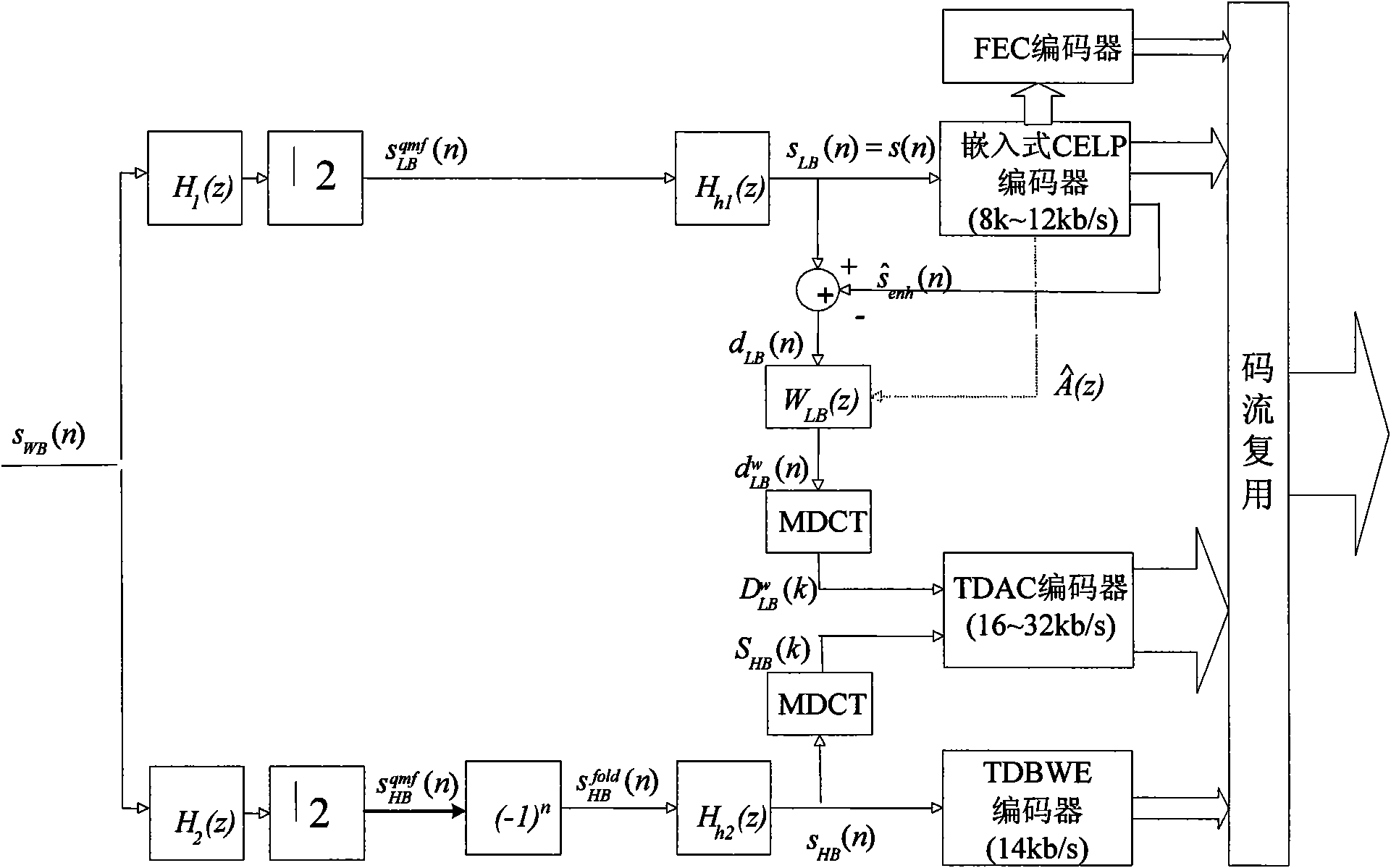
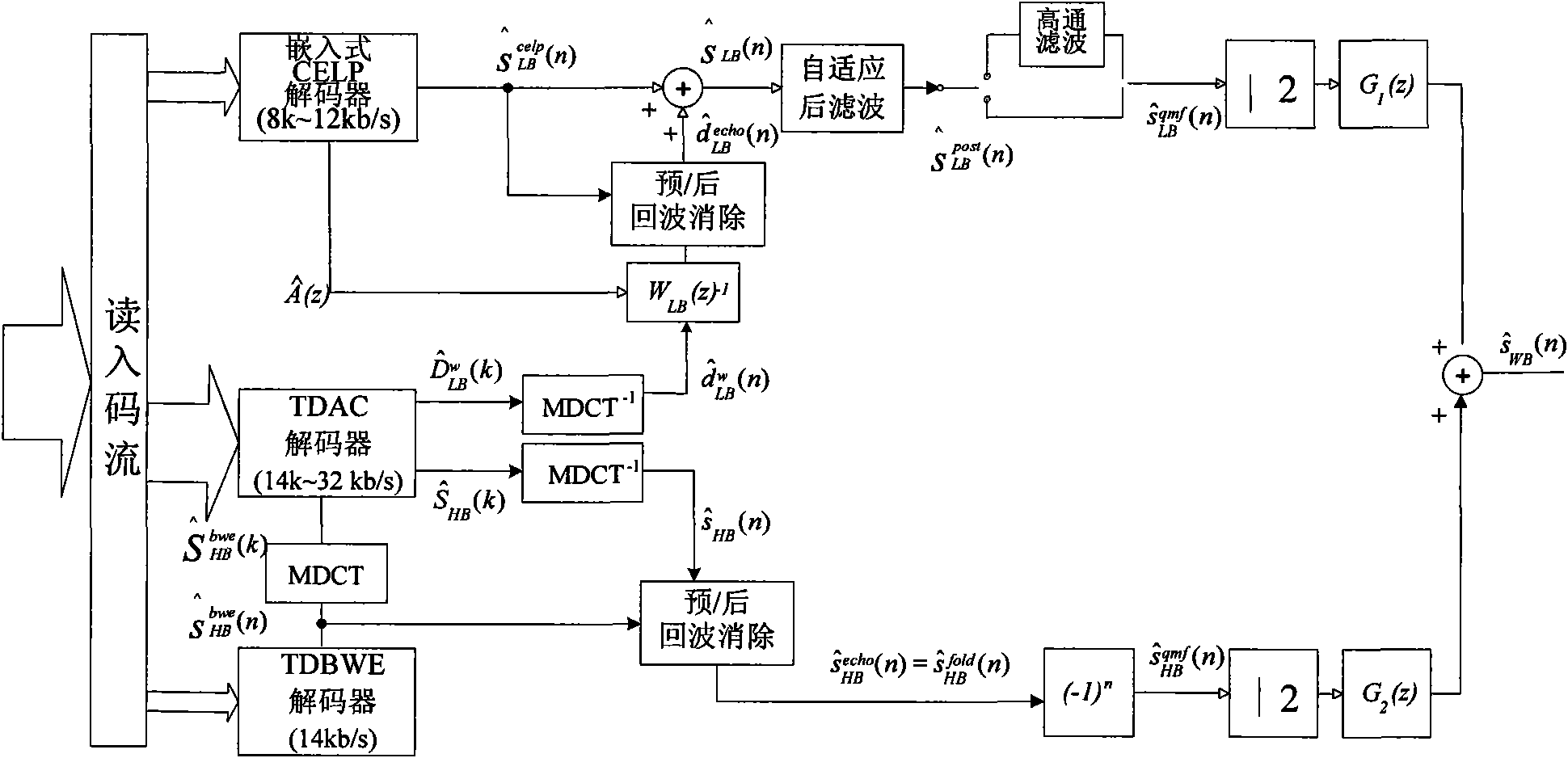
ActiveCN101651752ASave communication bandwidthGuaranteed coding qualitySubstations coupling interface circuitsSpeech analysisDecoding methodsSignal quality
The embodiment of the invention discloses a decoding method which comprises the following steps: acquiring CNG parameters of a first frame of a first superframe from a speech coding frame at the frontof the first frame of the first superframe; carrying out background noise decoding to the first frame of the first superframe according to the CNG parameters, wherein the CNG parameters comprise target excitation gains and LPC filter coefficients, wherein the target excitation gains are determined by fixed codebook gains quantized by the long-term and smooth speech coding frame, and the LPC filter coefficients are defined by LPC filter coefficients quantized by the long-term and smooth speech coding frame. The invention also discloses a decoding device. By utilizing the embodiment, the occupied bandwidth can be remarkably reduced under the condition of ensuring the signal quality.
Owner:HUAWEI TECH CO LTD
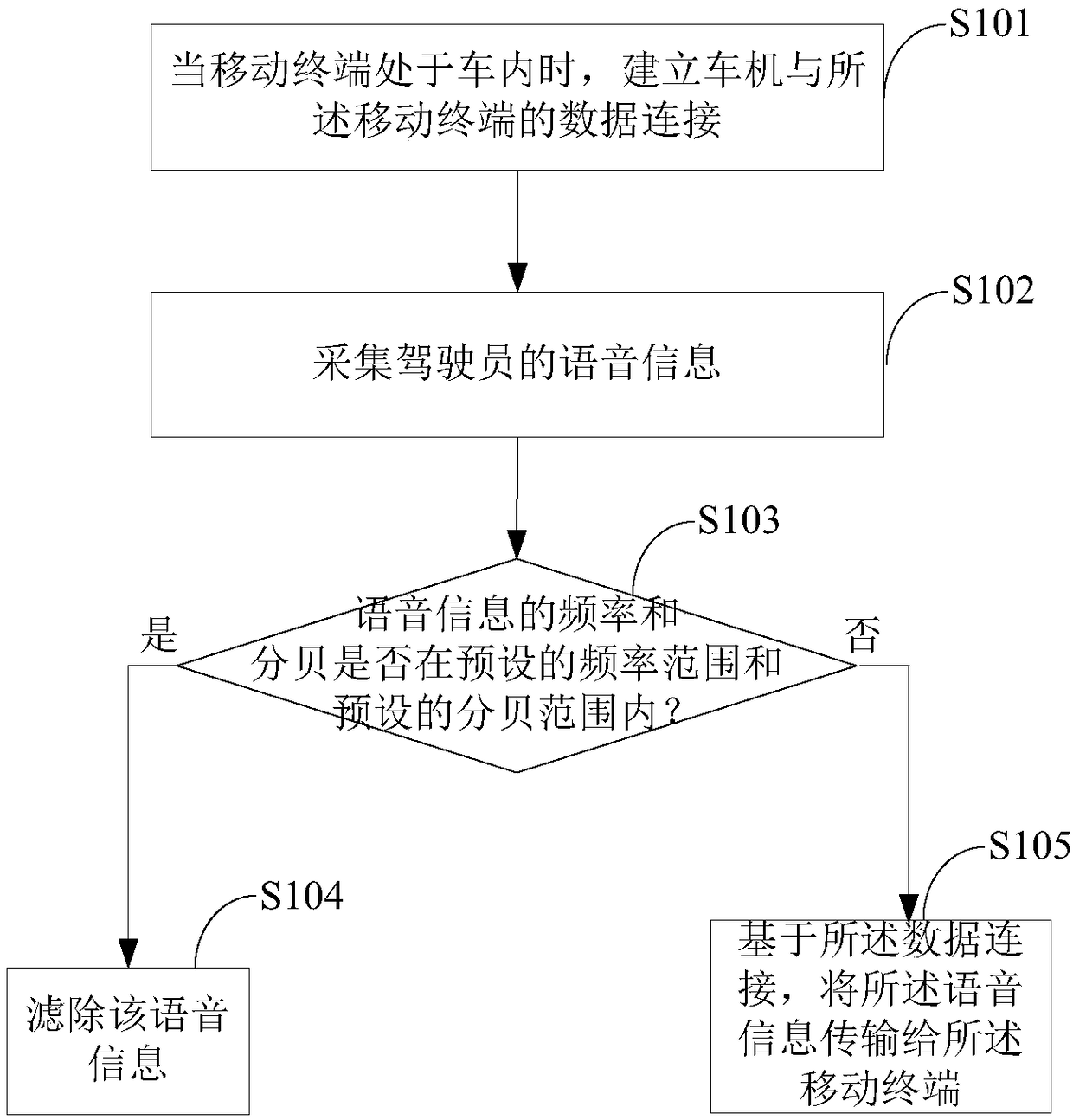
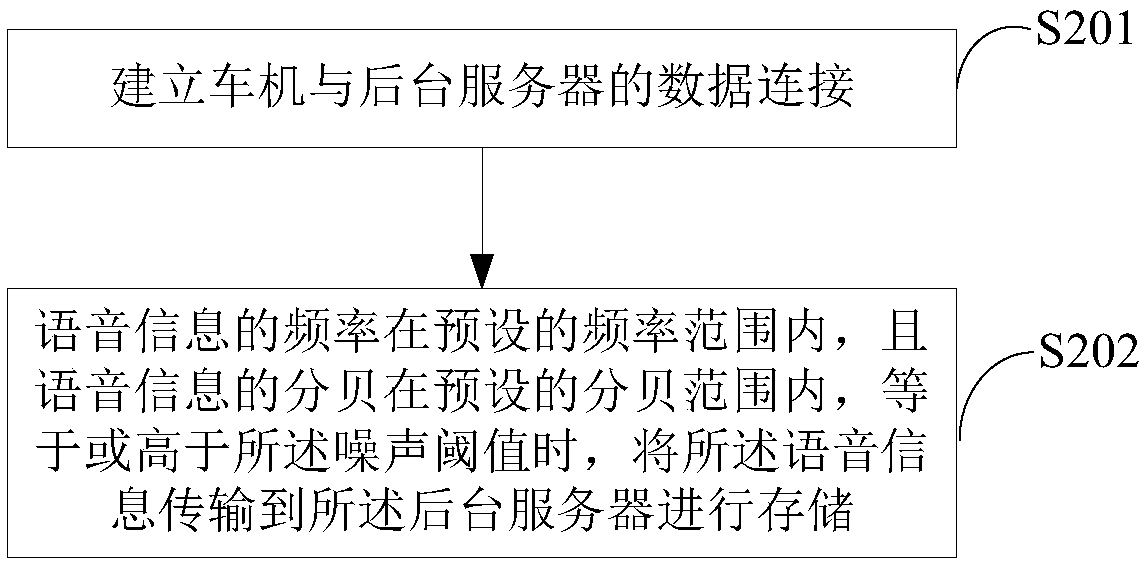
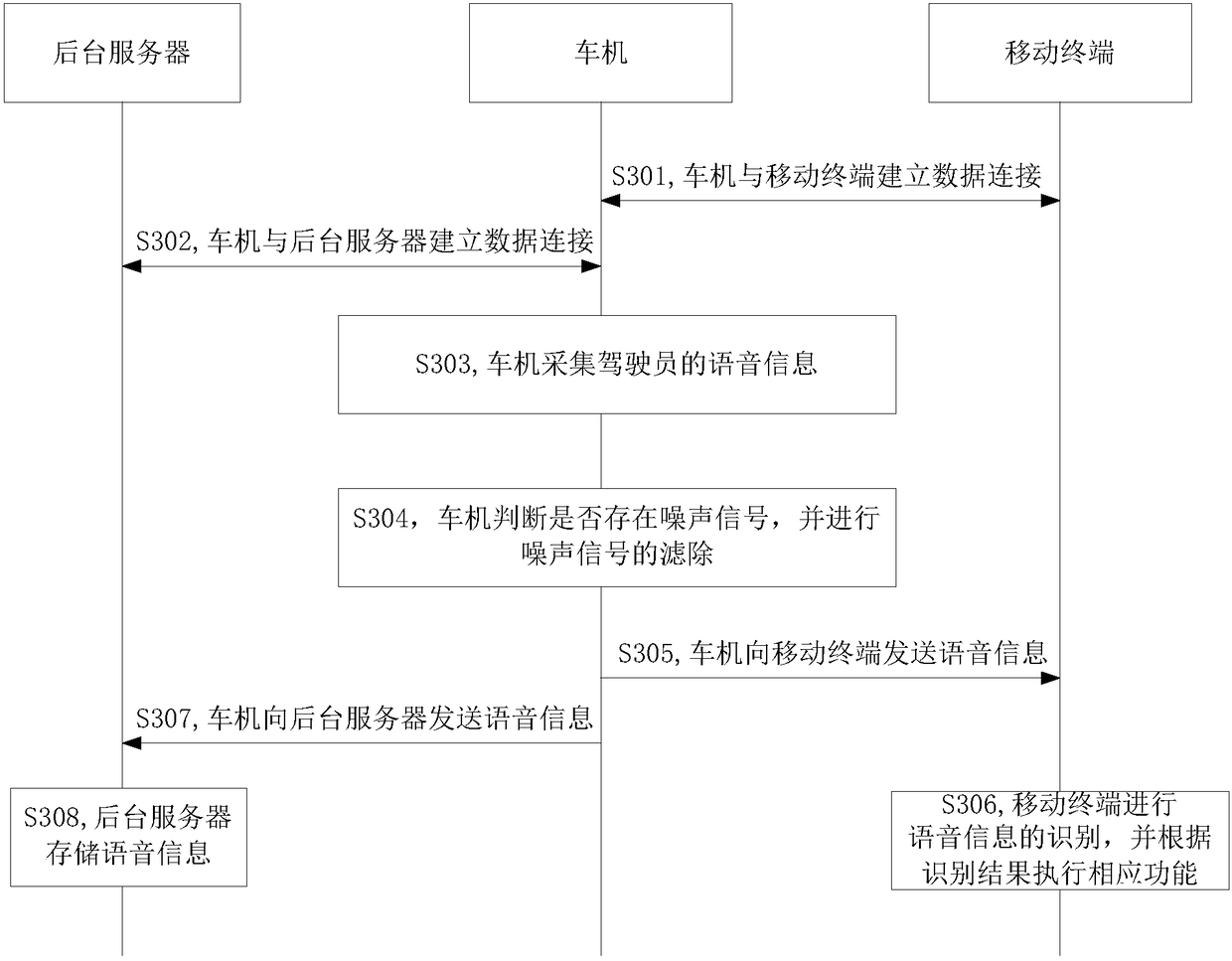
In-vehicle entertainment product and corresponding voice transmission method and system
InactiveCN108257610ASave communication bandwidthOptimize resource allocationSpeech analysisShort range communication serviceData connectionIn vehicle
The embodiment of the invention provides an in-vehicle entertainment product and a corresponding voice transmission method and system, and belongs to the technical field of vehicles. The voice transmission method for the in-vehicle entertainment product comprises the steps: building a data connection between the in-vehicle entertainment product and a mobile terminal when the mobile terminal is located in a vehicle; collecting voice information of a driver; judging whether the frequency and decibel of voice information are respectively within a preset frequency range and a preset decibel rangeor not: filtering the voice information if the frequency and decibel of voice information are not respectively within the preset frequency range and the preset decibel range, or else transmitting thevoice information to the mobile terminal based on the data connection. According to the embodiment of the invention, the method can achieve the filtering of a noise signal collected by the in-vehicleentertainment product, enables the noise signal not to be transmitted to the mobile terminal, thereby saving the communication bandwidth between the in-vehicle entertainment product and the mobile terminal, enabling the in-vehicle entertainment product and the mobile terminal not to carry out the processing of the noise signal, and facilitating the resource allocation of the in-vehicle entertainment product and the mobile terminal.
Owner:FAFA AUTOMOBILE (CHINA) CO LTD
Improved method and system for operating a cyclic production machine in coordination with a loader or unloader machine
ActiveCN101454733AReduced production cycle timeImprove controllabilityPress ramTotal factory controlEngineeringImproved method
A method for synchronising a first machine of a manufacturing process section arranged to carry out a production cycle comprising a working part and a non-working part, which said first machine is operated in conjunction with at least one second machine. The first machine carries out a process during the working part of the cycle on a workpiece which is loaded into and / or unloaded out of said first machine by said at least one second machine during the non-working part of each process cycle. The first machine is preferably a mechanical press and the second machine is preferably an industrial robot arranged to carry out a loader and / or unloader function. A system for carrying out the method and a computer program are also described.
Owner:ABB (SCHWEIZ) AG
Data transmission method and system in instant communication
ActiveCN1842064AImprove the efficiency of instant messagingEnsure safetyData switching by path configurationSecuring communicationTransport systemData transmission
The invention provides a data transmitting method and system of an instantaneous communication. The transfer transmitting switches in the date between the client end and the object client end. The method comprises: a) choosing the client end with data transfer ability as node; b) choosing the node for providing the data transfer server to the client end and the object client end and then allocating a node key to the node; c) establishing the node transfer communicating channel; d) using the node transfer communicating channel to switch the data of between the client end and the object client end.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Multi-terminal data synchronization method based on ACK synchronization
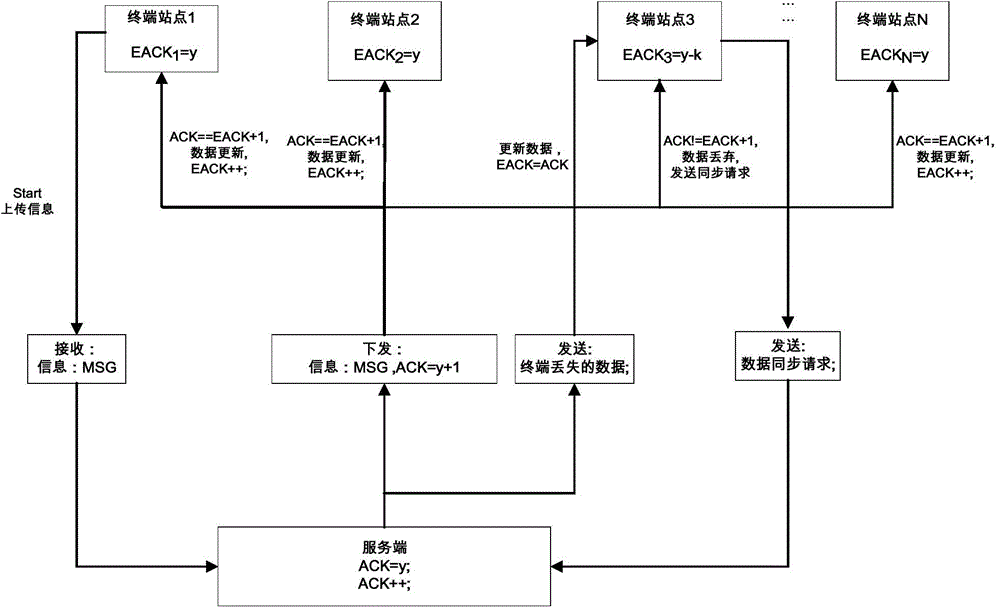
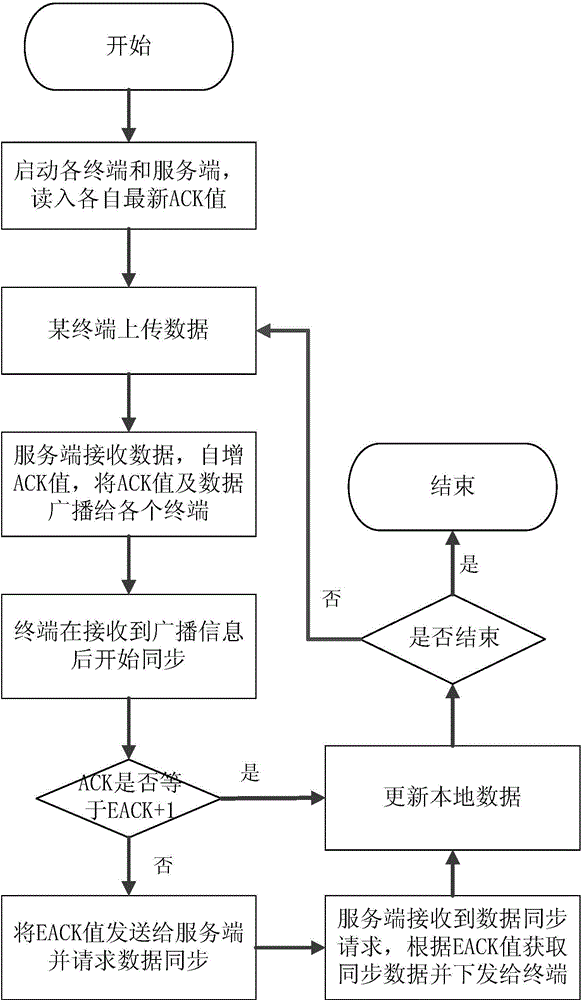
ActiveCN104954101AAchieve synchronizationGuaranteed reliability and efficiencyError prevention/detection by using return channelBroadcast dataDistributed computing
The invention provides a multi-terminal data synchronization method based on ACK synchronization. According to the method, a server and all terminals keep respective latest transmission control character sequence numbers; the server is firstly started to read in the latest value of the own transmission control character sequence number, and then all the terminals are started to read in the latest values of the respective transmission control character sequence numbers; when data is newly added to one terminal, the terminal sends the data to the server; the server saves the data, updates the own transmission control character sequence number, and broadcasts the data to all the terminals; after receiving the data broadcasted by the server, any one terminal parses the transmission control character sequence number of the broadcasted data, and judges whether the transmission control character sequence number of the broadcasted data is equal to the value of the local transmission control character sequence number plus one or not; if yes, the terminal updates the broadcasted data to the local end, and updates the value of the local transmission control character sequence number; if no, the terminal discards the broadcasted data, and uploads a synchronization request containing the value of the local transmission control character sequence number to the server; after obtaining the corresponding data, the terminal updates both the local data and the value of the local transmission control character sequence number.
Owner:HUBEI UNIV OF ARTS & SCI
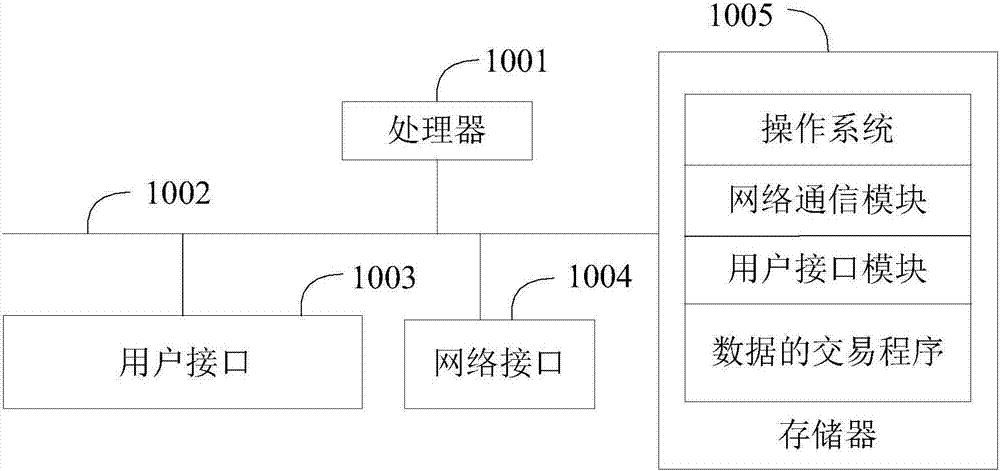
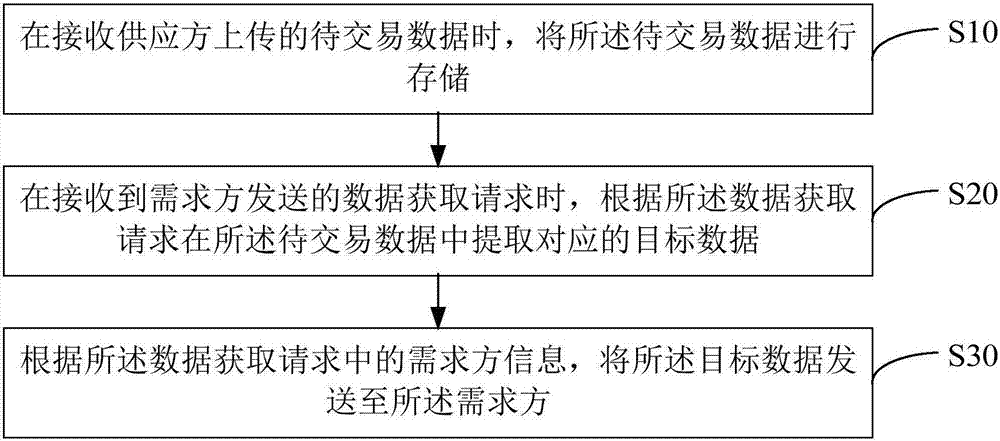
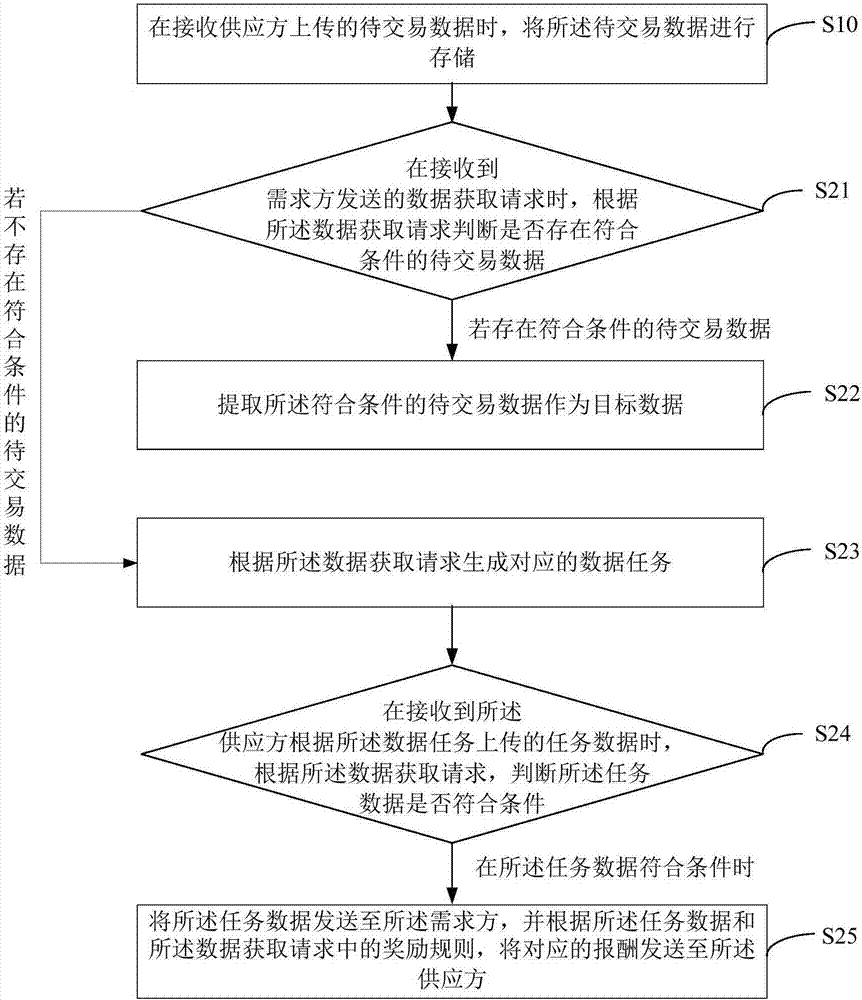
Data transaction method and device and computer readable storage medium
InactiveCN107508858AImprove efficiencySolve technical problems with low effectivenessTransmissionTransaction dataData acquisition
The invention provides a data transaction method and device and a computer readable storage medium. According to the data transaction method, when to-be-transacted data uploaded by a supplier is received, the to-be-transacted data is stored; when a data acquisition request sent by a demand side is received, according to the data acquisition request, corresponding target data is extracted from the to-be-transacted data; and according to the data, demand side information in the request is acquired, and the target data is sent to the demand side. In the mode, according to the invention, the target data which meets the requirements of the data demand side is extracted from the to-be-transacted data uploaded by the data supplier. Therefore, by screening out the target data which accords with conditions of the data demand side, an effective rate of the data acquired by the demand side is improved, a communication bandwidth is saved, user experience of crowd-sourcing data acquisition is promoted, and the technical problem of low effectiveness of data acquired by the data demand side is solved.
Owner:SHENZHEN ECHIEV AUTONOMOUS DRIVING TECH CO LTD
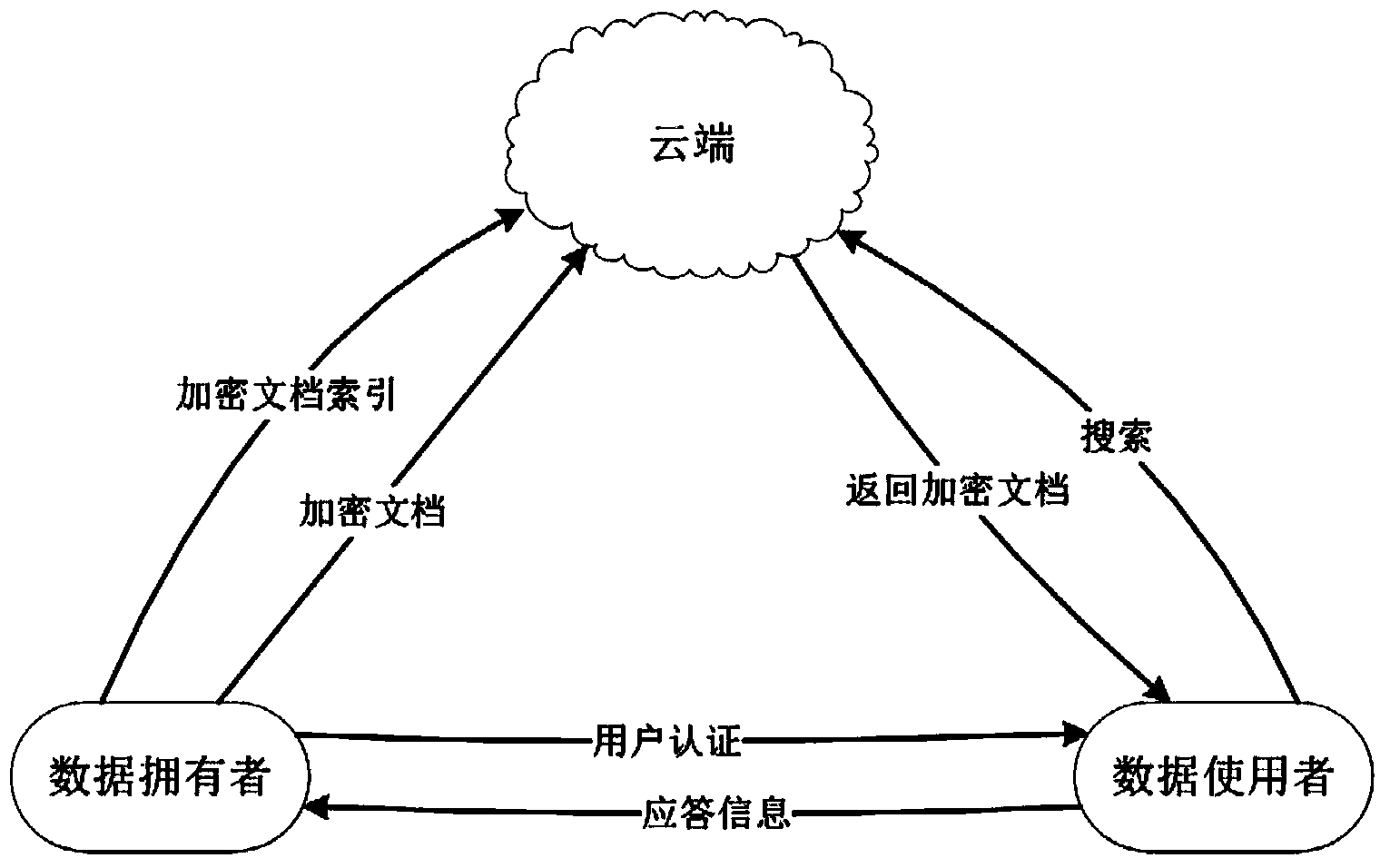
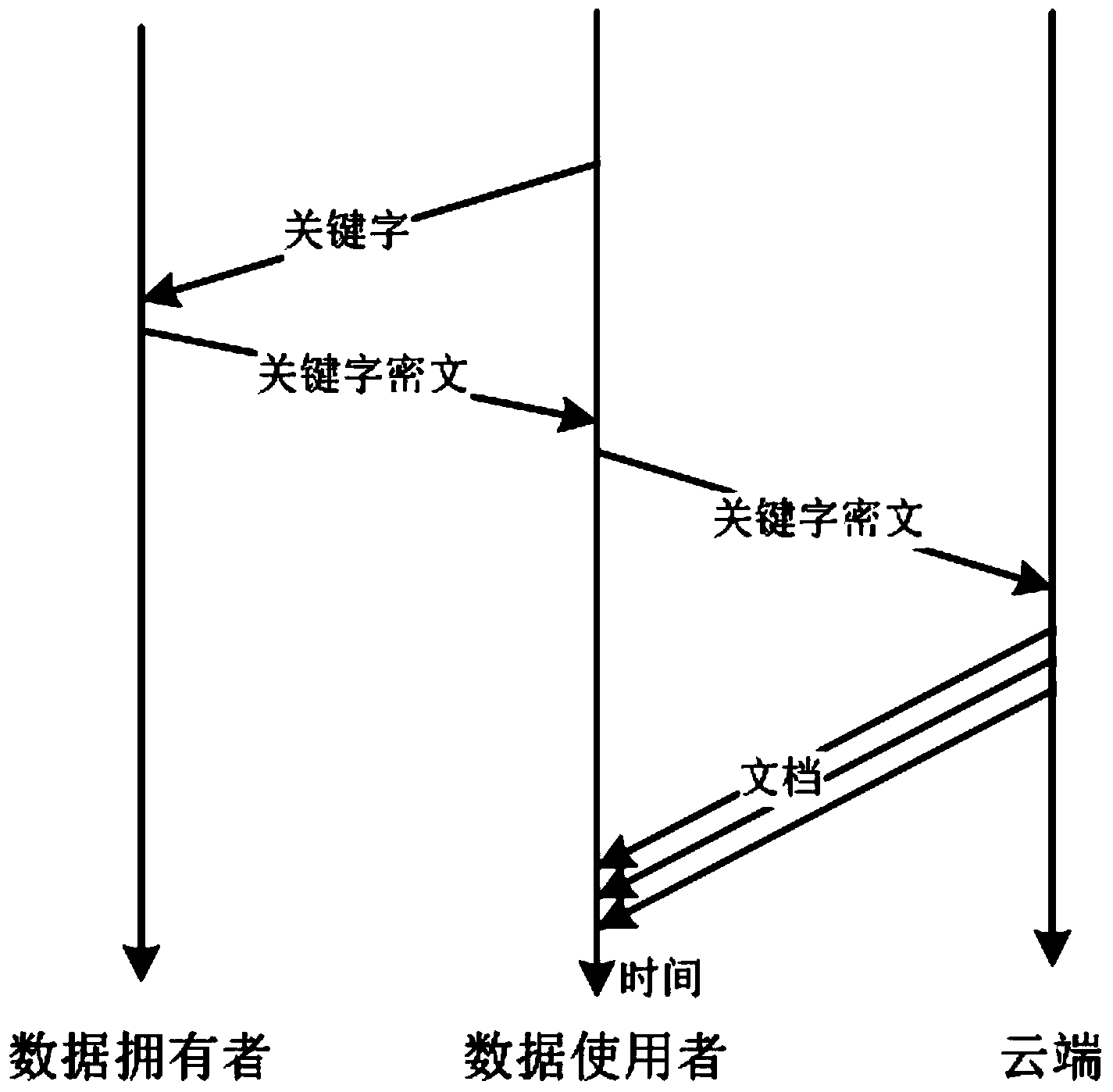
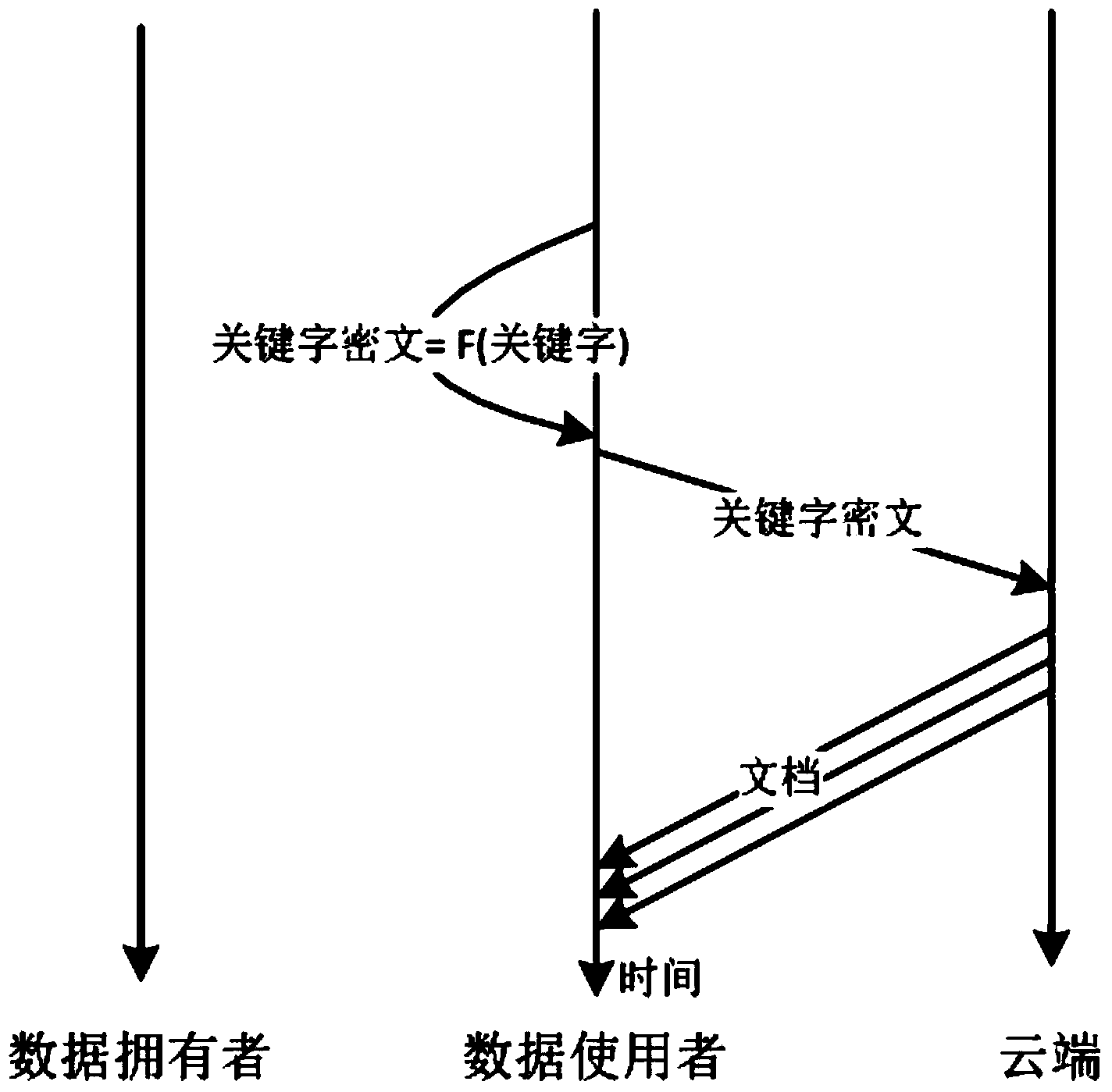
Efficient and safe multi-keyword-supporting searching method in mobile cloud
InactiveCN103544301AEnsure safetySimplify the search processSpecial data processing applicationsDocument management systemsUser inputMobile cloud
The invention discloses an efficient and safe multi-keyword-supporting searching method in a mobile cloud. The method is based on a TF-IDF (Term Frequency-Inverse Document Frequency) search model; a data owner stores an encrypted document and an encrypted document index in a cloud end, and a data user inputs a keyword which is encrypted by Fast Accumulated Hashing to search the encrypted document stored in the cloud end, so that search safety is realized. The isolation of search is realized through the addition of noise. The search control is realized through user registration and verification. The high efficiency of search is realized through one-time communication, keyword compression, establishment of search cache and binary set. The efficient and safe multi-keyword-supporting searching method in the mobile cloud guarantees security of document collection, keywords and indexes involved in the search process in the aspect of security, simplifies the search process, increases the search efficiency, compresses total communication amount and reduces communication bandwidth in the aspect of efficiency, and solves the bandwidth bottleneck problem of the encrypted search on a cloud platform.
Owner:SHANGHAI JIAO TONG UNIV +1
Adaptive voice activity detection method
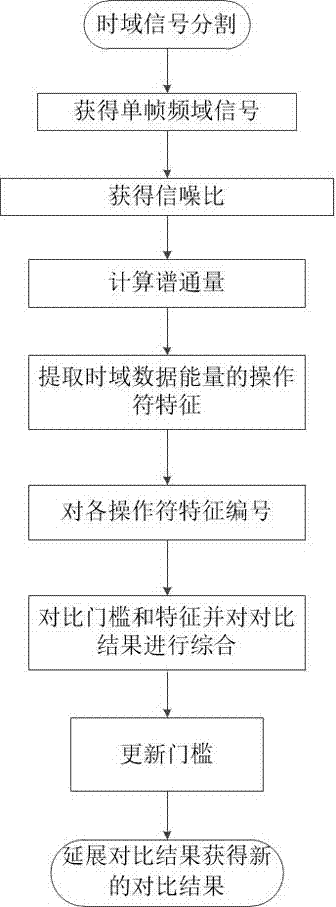
ActiveCN107331393ASave communication bandwidthLower requirementSpeech recognitionTime domainVoice communication
The invention relates to the voice signal processing field, and especially relates to an adaptive voice activity detection method mixing three thresholds and based on time domain and frequency domain characteristic extractions; the method can control the equipment work states by detecting whether a voice system has active voices or not; when no active voice is detected, the equipment can be in a low power state or a suspended state, thus reducing equipment operation requirements and power consumption, and reducing the communication bandwidth for the voice communication equipment.
Owner:成都启英泰伦科技有限公司
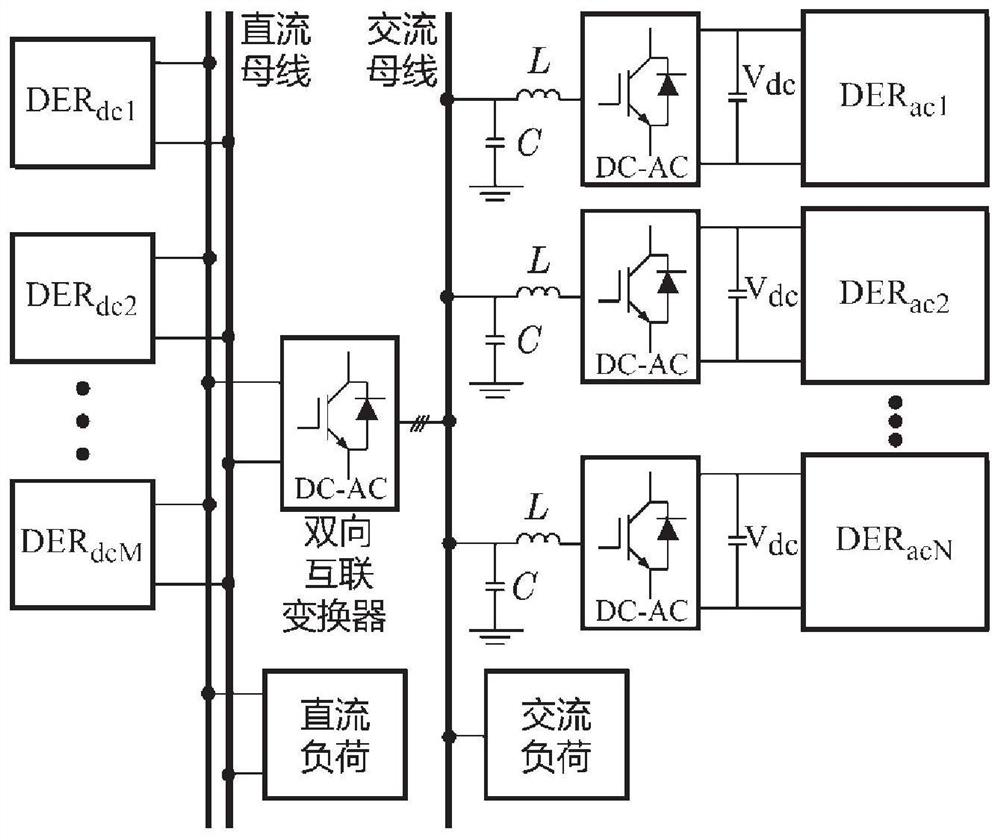
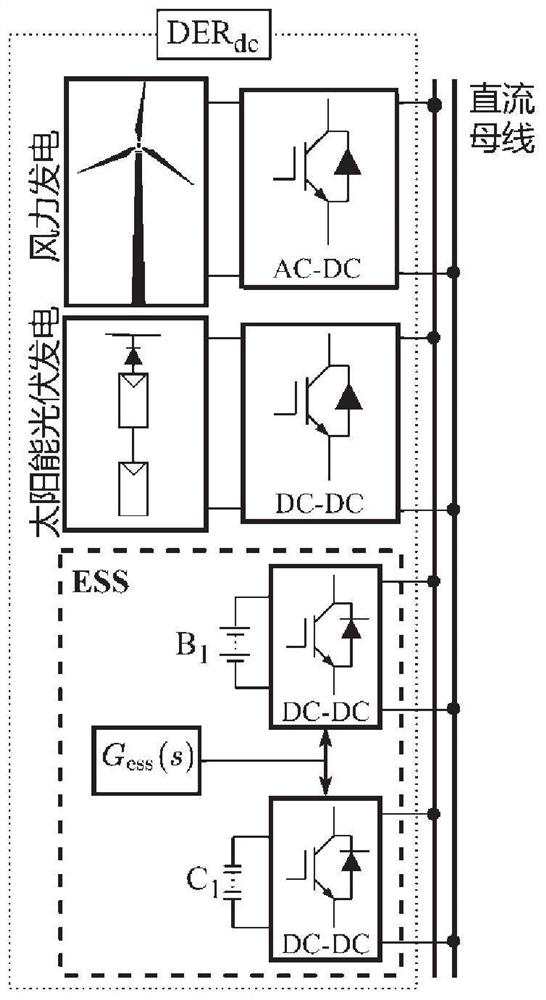
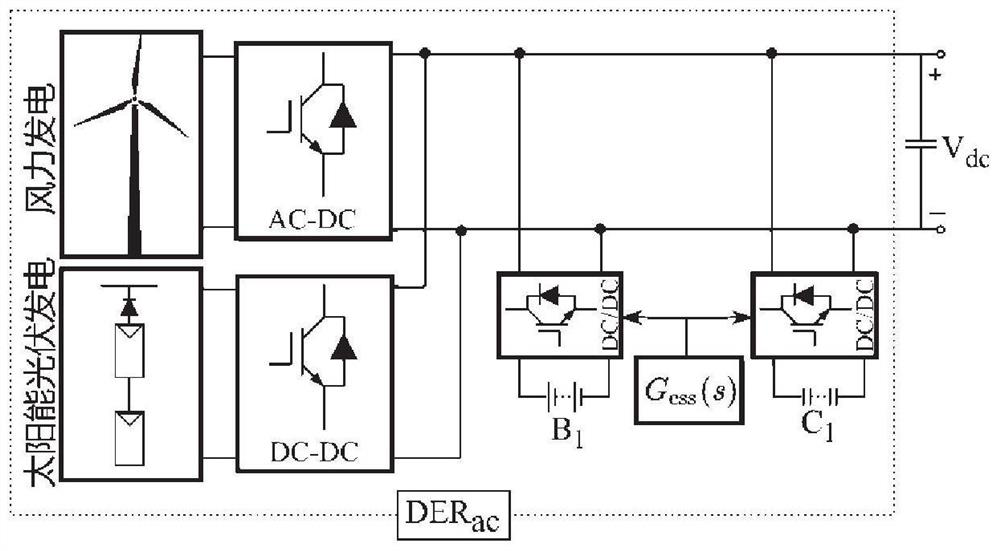
Distributed voltage source converter cooperative control method and AC-DC hybrid microgrid
ActiveCN112803505AIncrease inertiaReduce frequencyBatteries circuit arrangementsDc source parallel operationPower flowControl engineering
The invention discloses a distributed voltage source converter cooperative control method and an AC-DC hybrid microgrid. The distributed voltage source converter cooperative control method comprises the following steps of: adjusting a power flow between an AC sub-grid and a DC sub-grid through a bidirectional interconnection converter; when the load of the AC sub-grid suddenly changes, calculating the total optimal power input of the AC sub-grid, and judging whether the DER total power in the current AC sub-grid reaches the total optimal power input of the AC sub-grid or not; if so, calculating the input power contribution of each DER in the AC sub-grid through using a virtual inertia algorithm; and if not, indicating that the DER in the DC sub-grid has redundant power, the DC sub-grid participates in cooperative control. According to the distributed voltage source converter cooperative control method, the inertia of the micro-grid is remarkably improved, the communication bandwidth is reduced, the service life of storage equipment is prolonged, and the method has the characteristic of quick and stable control.
Owner:SHANDONG UNIV
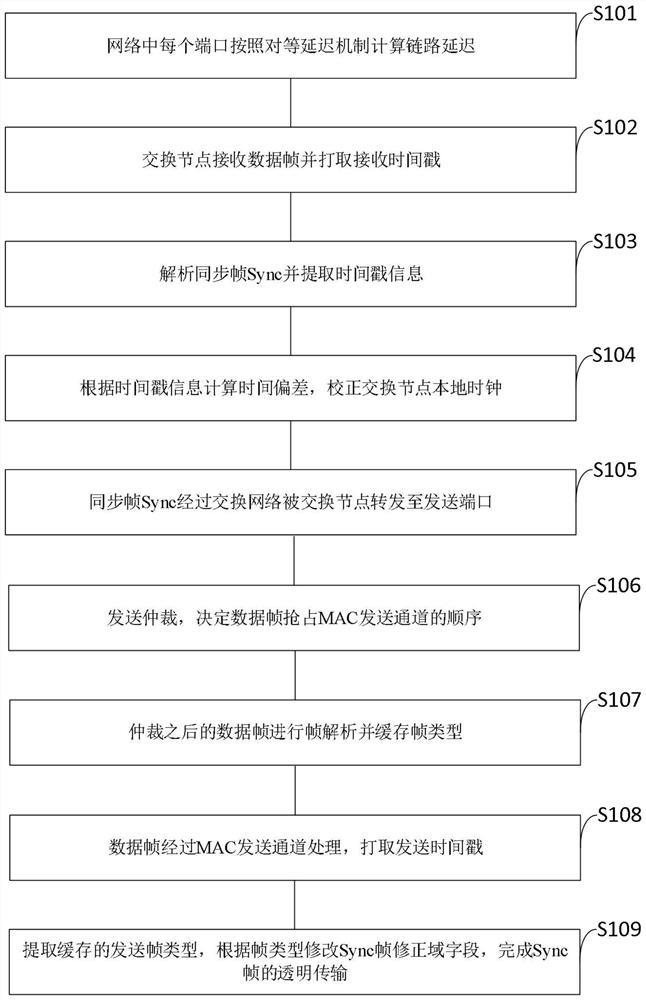
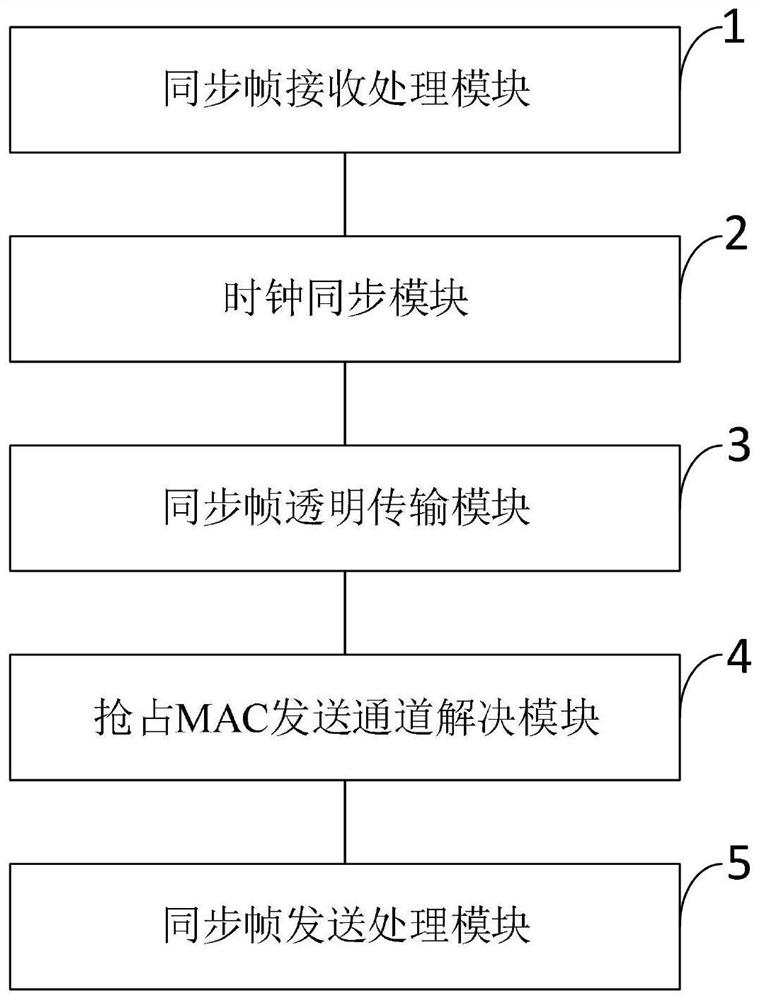
1588 synchronization method, system and device for high-speed TTE cascade network
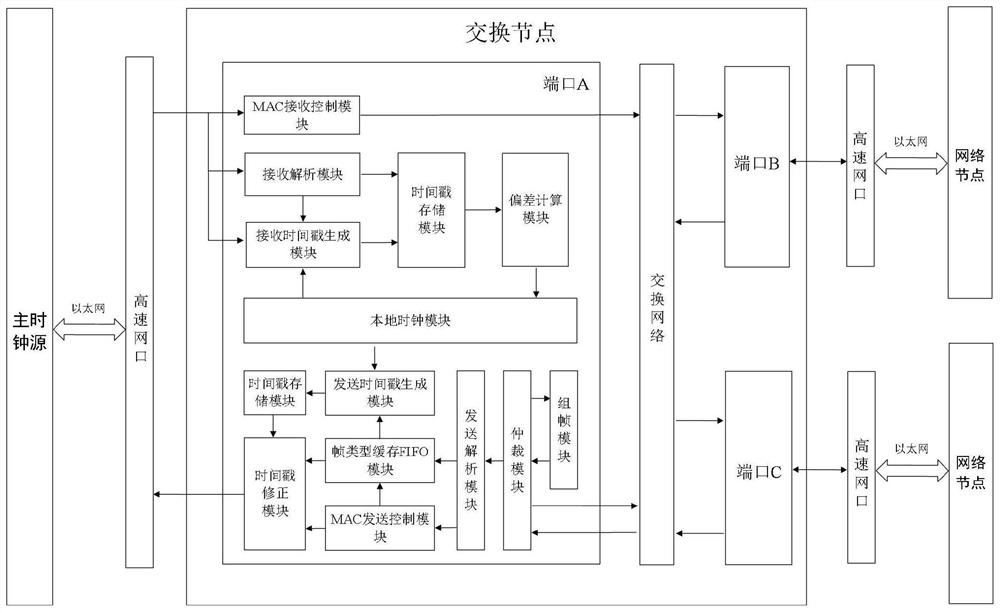
ActiveCN111800213ASolve the conflict problem of preempting the MAC sending channelImprove applicabilityTime-division multiplexComputer hardwareEngineering
The invention belongs to the technical field of network communication. The invention discloses a 1588 synchronization method, a 1588 synchronization system and a 1588 synchronization device for a high-speed TTE cascade network. The 1588 synchronization method comprises steps of enabling a port to calculate link delay; enabling a switching node to receive data frames, stamping receiving timestamps,analyzing the synchronous frame Sync and extracting the frame content; caching timestamp information, calculating time deviation, correcting a local clock, forwarding a synchronization frame Sync toa sending port, sending arbitration, sending analysis and caching a frame type, performing MAC sending processing, taking a sending timestamp, extracting the cached sending frame type, modifying a Sync frame correction domain, and finishing transparent transmission. According to the invention, the data frame type is analyzed at the data link layer and then MAC sending processing is carried out, sothat timestamp correction can be carried out rapidly when a synchronization frame is about to be transmitted to a high-speed network port; and meanwhile, the switching node is designed to adopt a transparent clock and common slave clock working mode, so that the universality and functional diversity of a synchronization scheme are improved.
Owner:XIDIAN UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com