Intelligent lock-control system for electric power safety
A safe and intelligent technology for electric power, applied in instruments, time registers, single input/output registers, etc., can solve the problems of potential safety hazards, easy accidents, easy to go to the wrong position, etc., to achieve convenient operation and The effect of carrying and managing comprehensively and avoiding wrong positions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
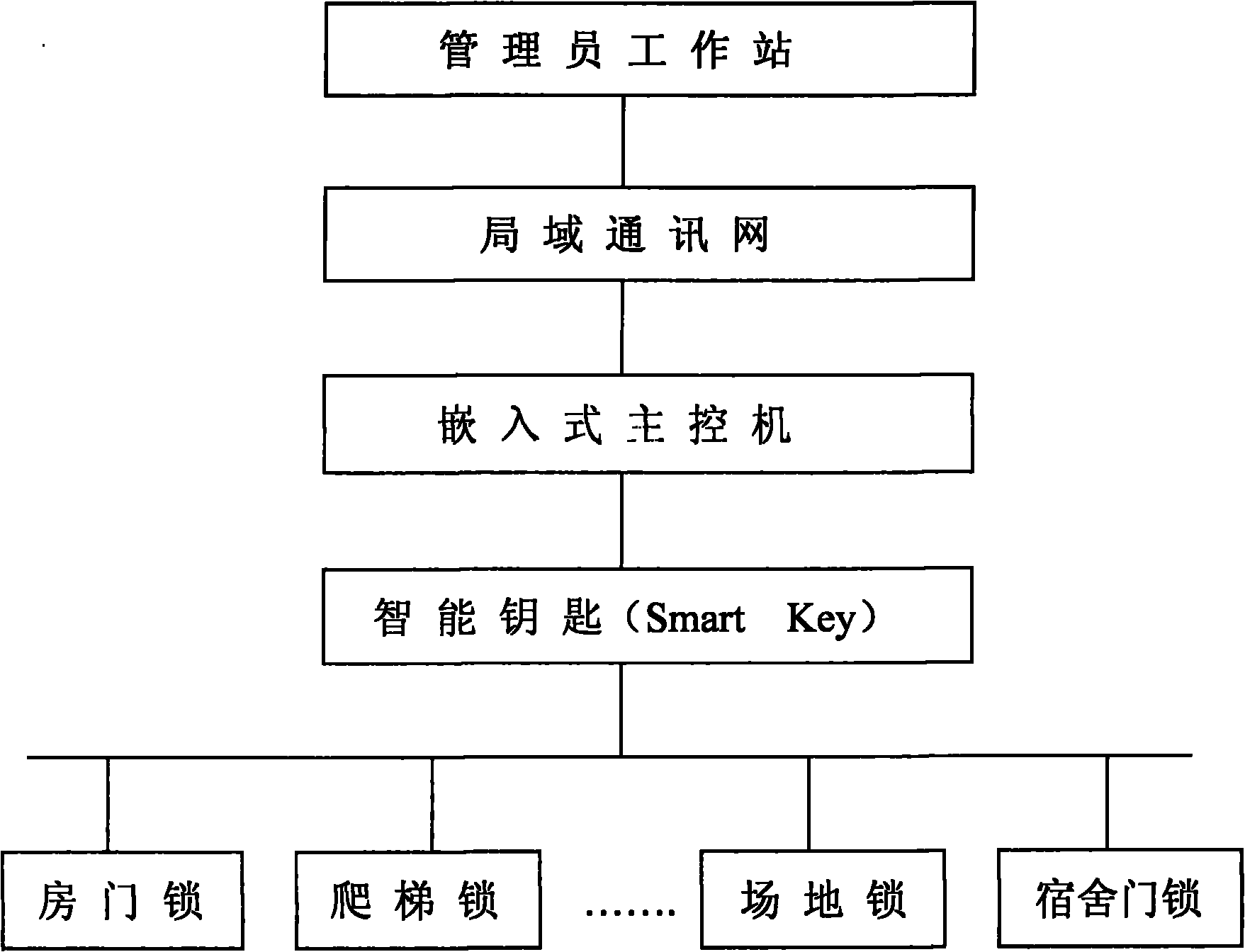
[0029] Such as figure 1 As shown, this solution is composed of administrator workstation, local area communication network, main control computer (embedded main control computer), smart key (Smart Key), locks and other components, and each lock is equipped with different RFID chips ; Among them, the administrator workstation is configured in the upper-level department with operation and safety management functions (such as: dispatching center, substation management station, substation work area, centralized control center, etc.), and the system administrator can set or change personnel permissions through the LAN. Safety supervisors can query and count unlocking records.
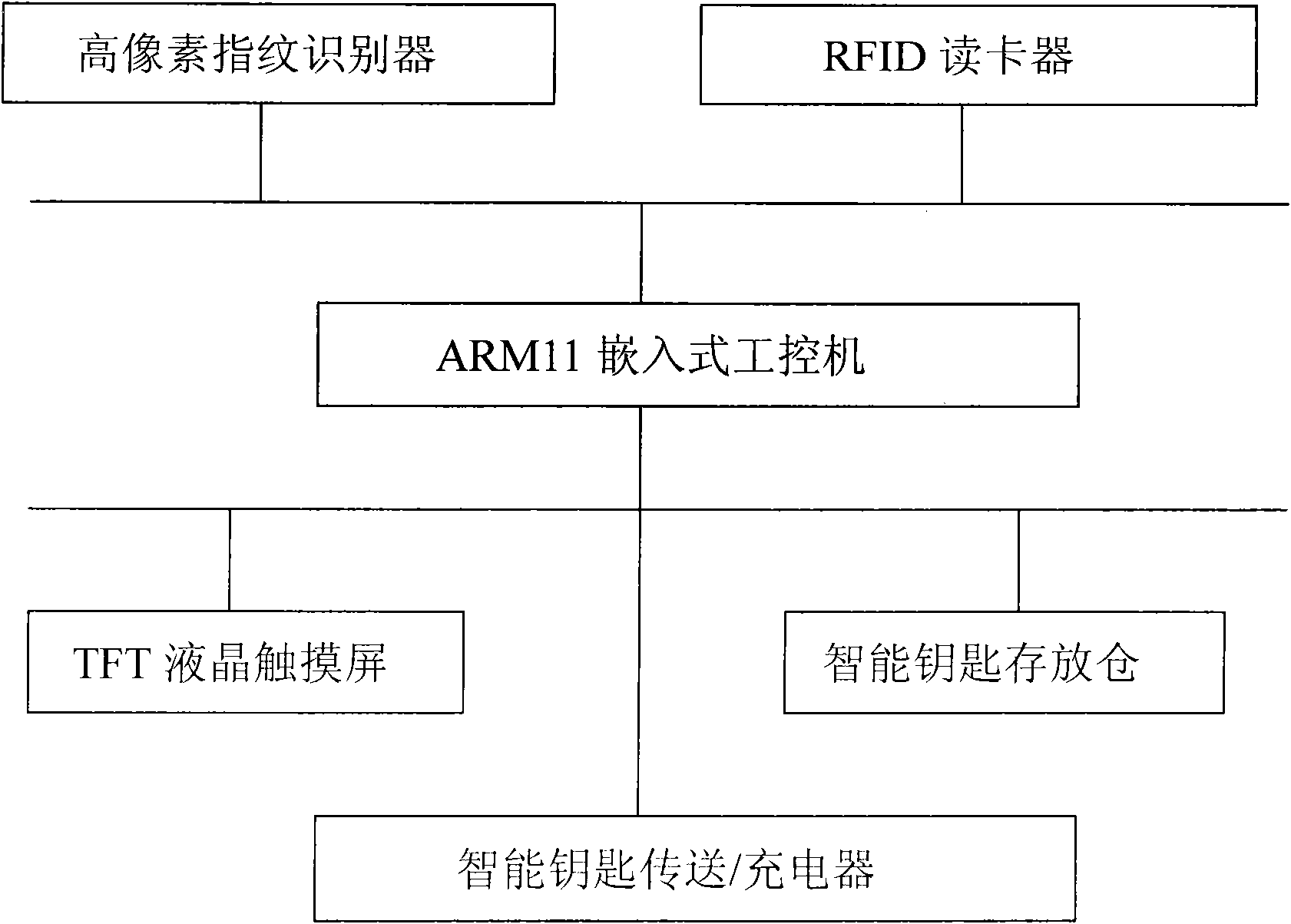
[0030] As the main control unit of the system, the main control computer is an embedded main control computer with lock control management software inside. It consists of ARM11 embedded industrial computer, 12-inch TFT color LCD touch screen, high-pixel fingerprint reader, RFID card reader, belt The door-co...
Embodiment 2
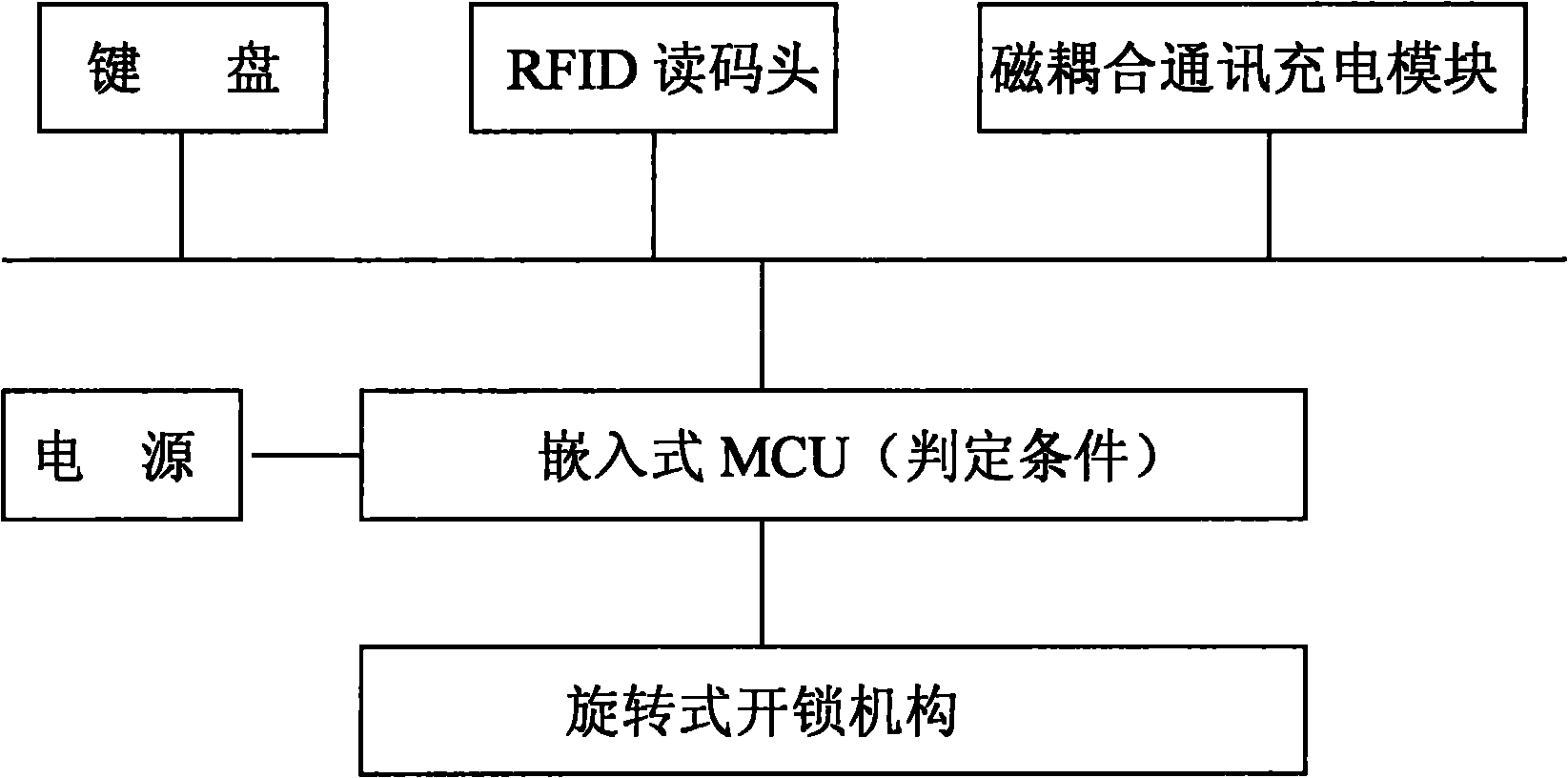
[0065] Such as Figure 5 As shown, the difference between this implementation and Embodiment 1 is that the main control machine in the system includes two parts, namely the PC and the smart key transmission / charger, and the smart key transmission / charger is an independent component and is connected with the The PC communicates. At this time, the PC has a user-defined display, and is also externally connected with an RFID card reader and a fingerprint identifier. When the staff needs to unlock, the identity verification is performed on the PC, and the unlocking range data of the person is delineated, and then communicates with the smart key transmission / charger to transmit the data to the smart key transmission / charger; at this time, the smart key transmission / charging The indicator light of the corresponding key in the device will be on, and at the same time, the smart key transmission / charger and the smart key will transmit data to the key through magnetic coupling communicat...
PUM
| Property | Measurement | Unit |
|---|---|---|
| Snr | aaaaa | aaaaa |
Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com