Method for performing instruction optimization on column confusion process in advanced encryption standard (AES) encryption algorithm and instruction set processor
An encryption algorithm and process instruction technology, applied in concurrent instruction execution, electrical digital data processing, instruments, etc., can solve the problems of occupying a lot of hardware resources, difficult to combine, and limited acceleration effect.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0075] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
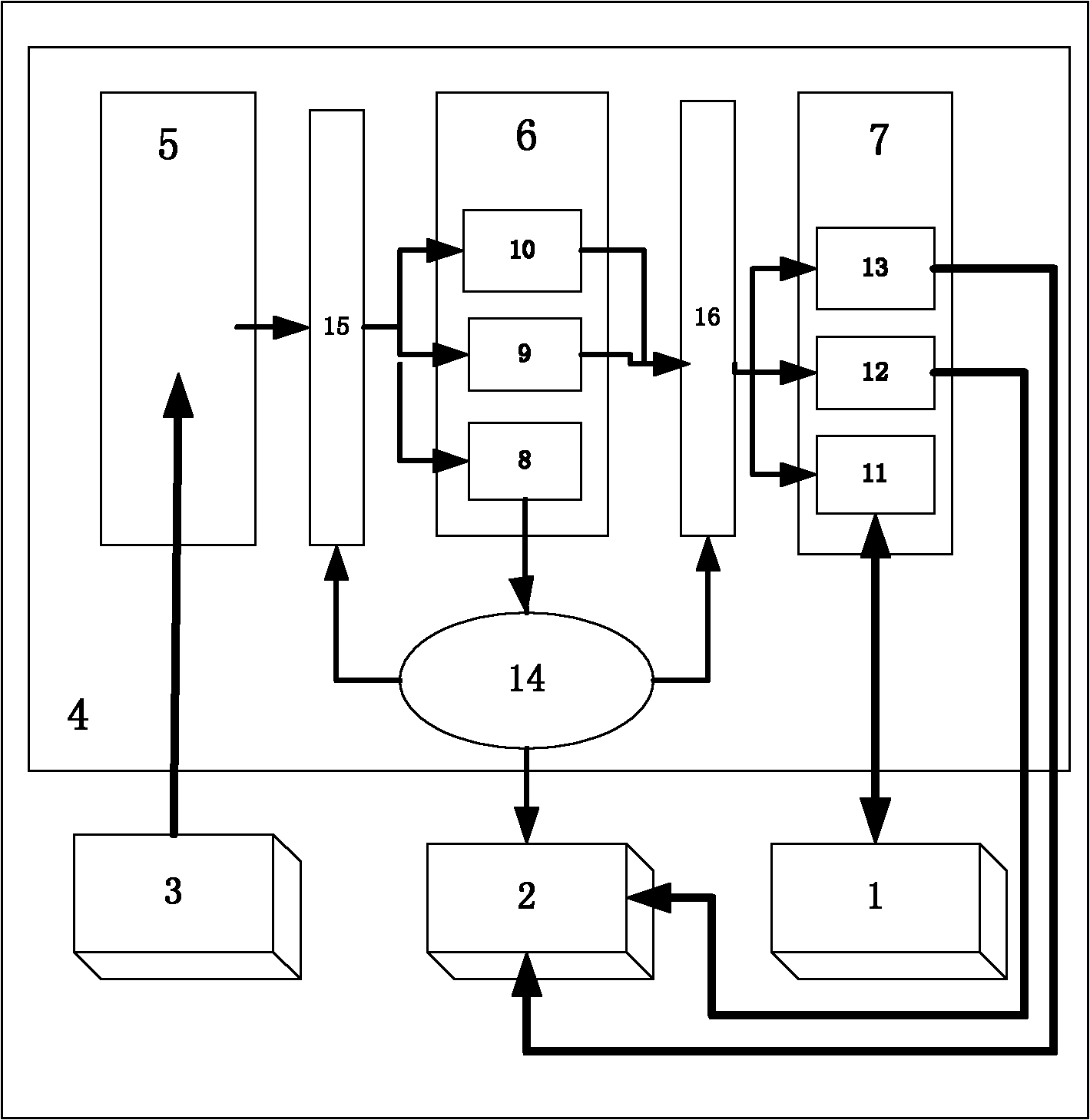
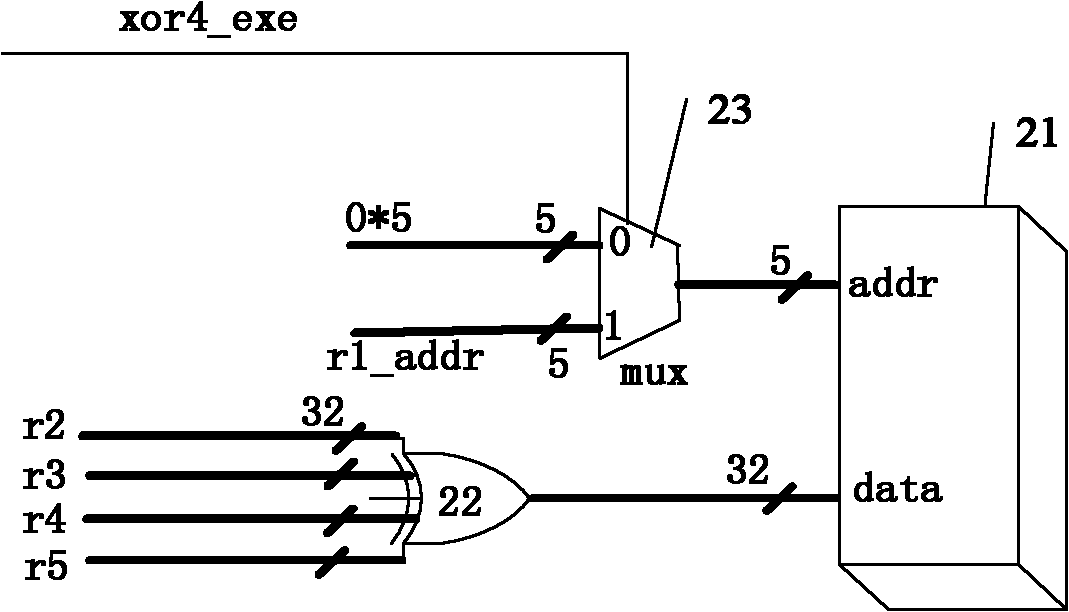
[0076] Figure 5 In , some steps of the column obfuscation process are accelerated under the premise of not changing the length of the instruction opcode, the number of instruction bits, and not affecting the running speed of the processor. The specific process is as follows:
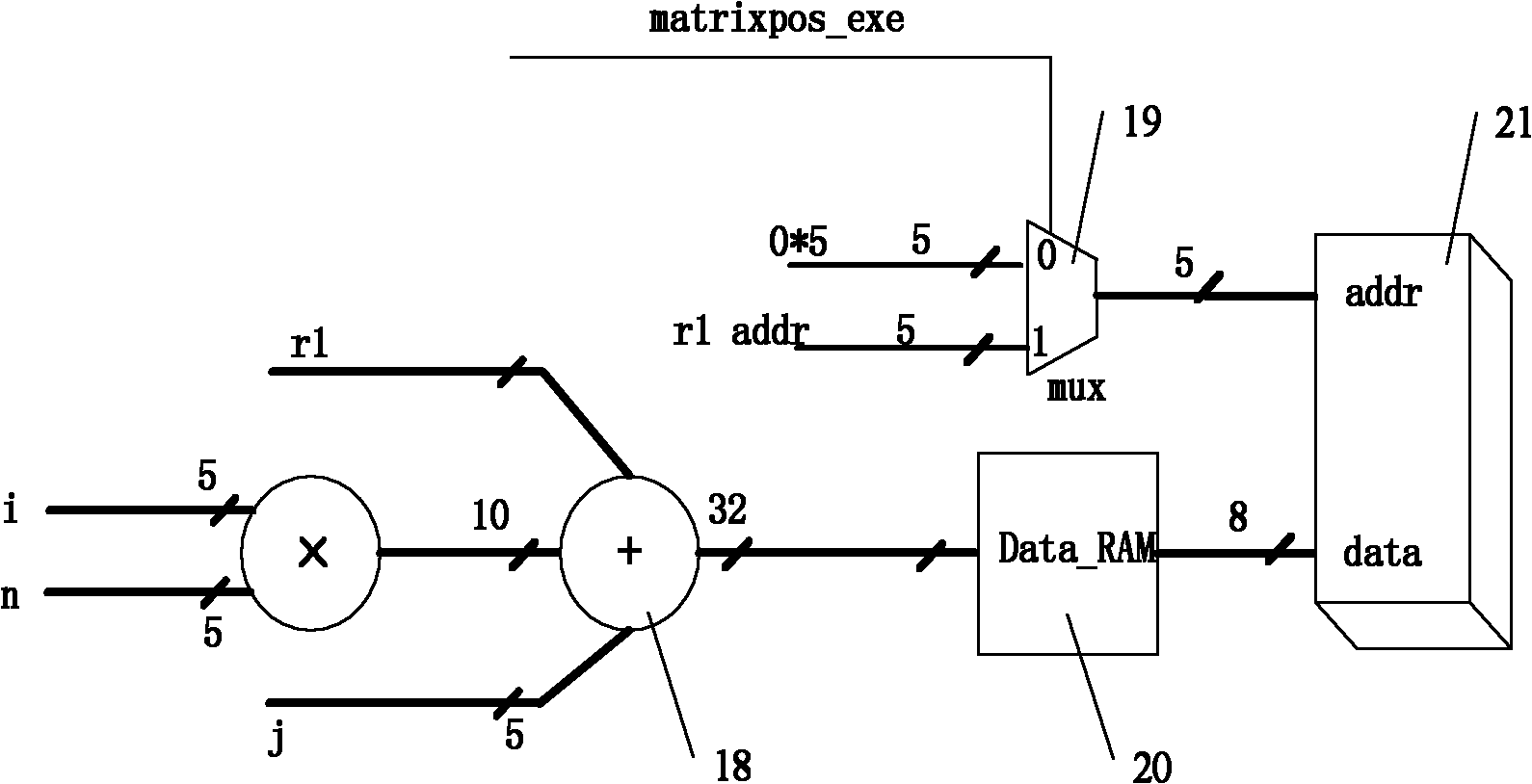
[0077] 1) When performing the AES encryption / decryption algorithm column obfuscation operation, the position of the data in the matrix needs to be positioned multiple times during the matrix multiplication operation, that is, the data at the position of matrix[i][j] is taken out. The data of the matrix in the actual memory is stored linearly, so in the traditional ARM processor, it is necessary to calculate the offset position of the data in the actual memory according to i and j, and search based on the offset position based on the base address matrix data, so 6 assembly...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com