Role access control method based on dynamic description logic
A role access control, dynamic description logic technology, applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve the problem that it is difficult to determine the corresponding relationship between roles and permissions, and it is difficult to meet the requirements without good inheritance of RBAC static authorization. Information security needs and other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
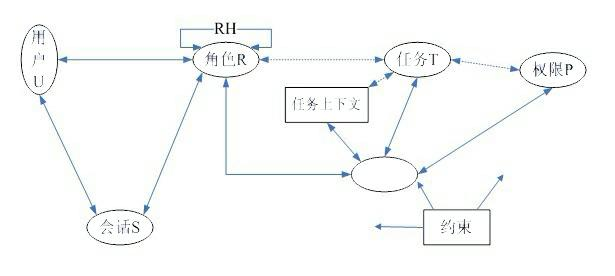
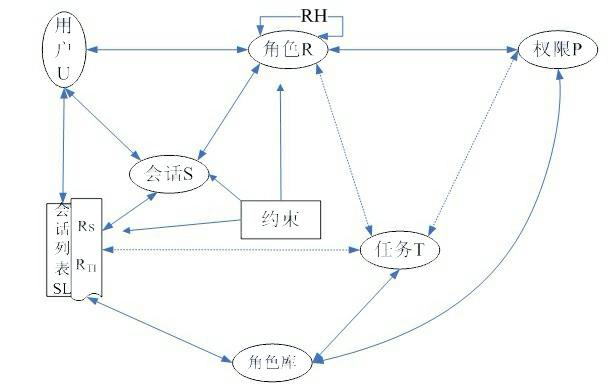
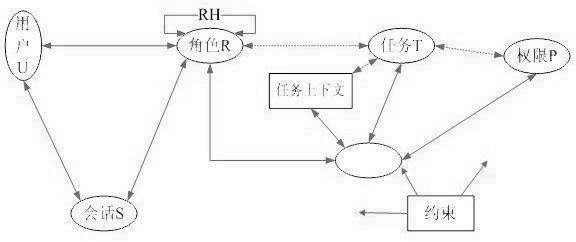
[0071] Attached below figure 2 The models and methods provided by the present invention are described in detail.
[0072] figure 2 Based on the role-based access control model, tasks, role libraries, and session lists are added, and roles are divided into static roles and dynamic roles. First, we first use dynamic description logic SHOIQ -DL formally describes the entire model, establishing SHOIQ -DL ERBAC The purpose of the knowledge base is to automatically handle the role constraint mechanism in access control. Secondly, based on this model, the system administrator statically assigns permissions to roles to form various forms of the above-mentioned roles, and saves these roles in the role library. In order to make the assignment of roles and permissions within a reasonable range of granularity, this requires the system administrator to have certain experience.
[0073] The administrator also needs to statically add some basic roles, such as the roles correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com