Realization method of protocol identification and control system based on P2P (peer-to-peer network)
A control system and protocol identification technology, applied in the network field, can solve problems such as many human factors, and achieve the effect of improving identification efficiency, reducing processing pressure, and operating in good condition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
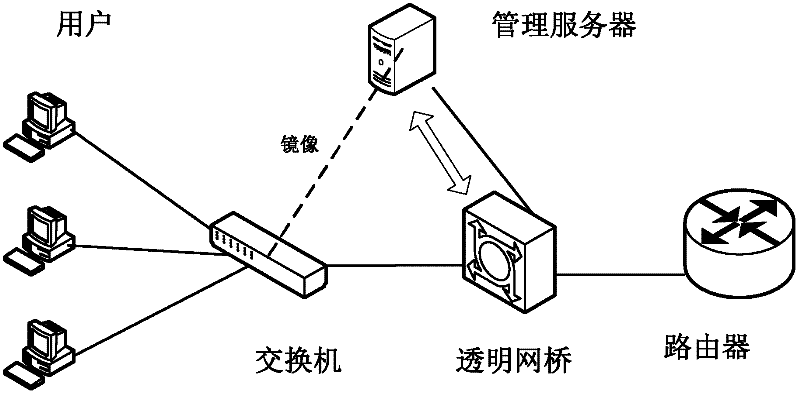
[0024] Architecture
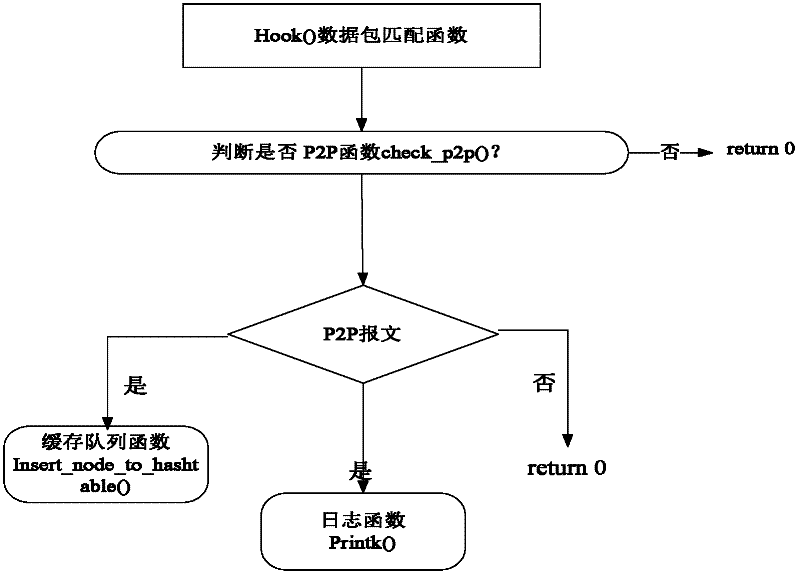
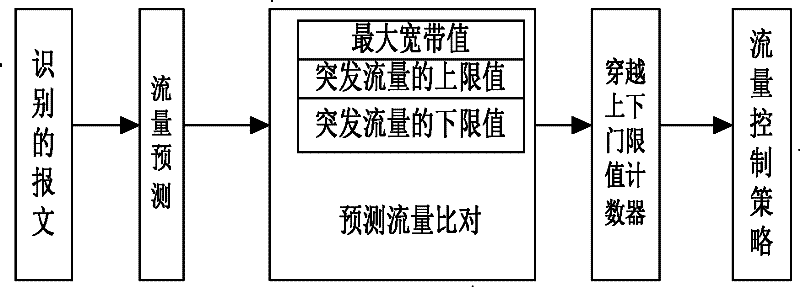
[0025] Non-encrypted message identification function: P2P traffic identification technology based on application layer data detection is to extract P2P application layer data (that is, P2P load) through protocol analysis and restoration technology, and judge whether it is It belongs to P2P application. Therefore, this type of method is also called Deep Packet Inspection (DPI). In the deep data packet detection technology, the feature library is established by extracting features from the specific P2P protocol and the load of the corresponding P2P system. For the real-time network flow passing through, the pattern matching algorithm is used to judge whether it contains the feature string in the feature library. If the feature matching is successful, the network flow is P2P data. The message identification part of the present invention uses DPI scanning technology to identify the hash search message and some related interactive messages in the specific n...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com