Method and device for protecting storage system
A storage system and algorithm technology, applied in transmission systems, computer security devices, internal/peripheral computer component protection, etc., can solve the problems affecting the life of the storage system and the performance of the storage system that is easy to wear, and achieve the effect of prolonging the life and protecting the performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
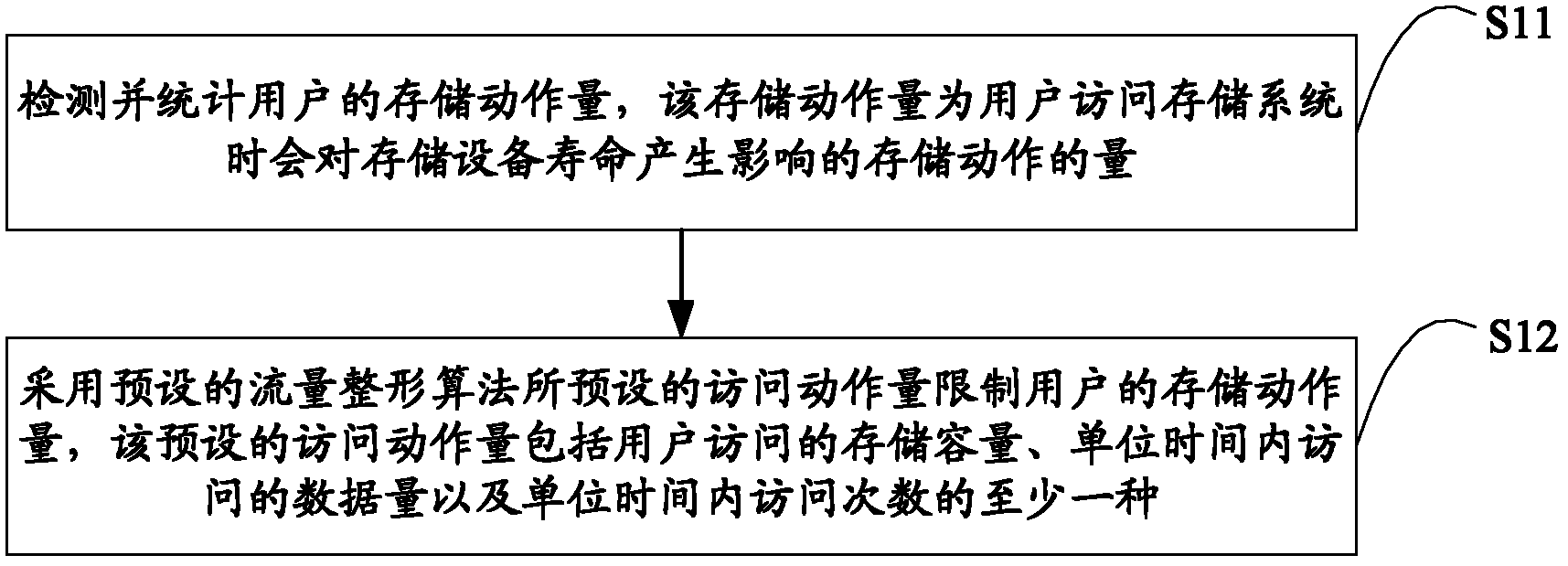
[0025] figure 1 It shows a flow chart provided by Embodiment 1 of a storage system protection method of the present invention. In this embodiment, the purpose of protecting the storage system is achieved by limiting the user's storage actions. The details are as follows:
[0026] Step S11 , detecting and counting the amount of storage operations of the user, which is the amount of storage operations that will affect the life of the storage device when the user accesses the storage system.
[0027] In this embodiment, the user's storage action amount is the amount of storage action that will affect the life of the storage device when the user accesses the storage system. In the trusted and controllable infrastructure of the public cloud, real-time statistics and detection of cloud computing user storage access behavior are performed, and the amount of user storage actions is counted and detected. For example, a user's storage action is detected in a converged network adapter (...
Embodiment 2
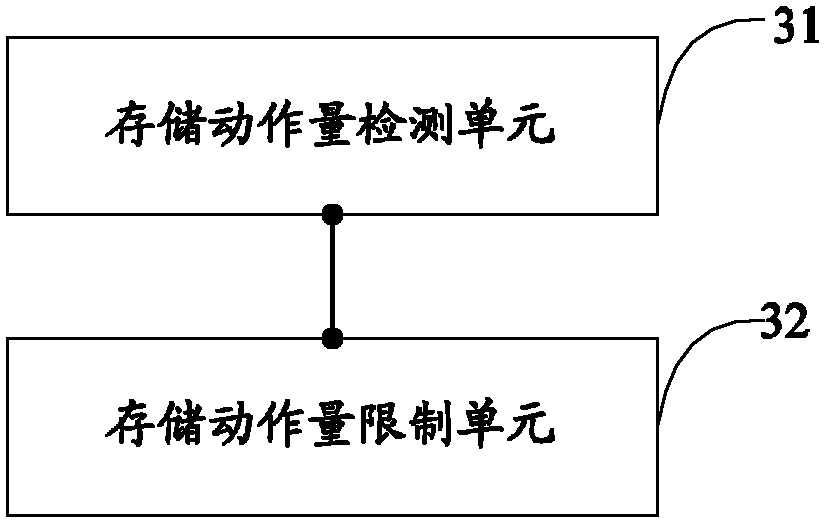
[0058] image 3 The structure diagram provided by Embodiment 2 of the storage system protection device of the present invention is shown, and for the convenience of description, only the parts related to the embodiment of the present invention are shown.
[0059] The storage system protection device can be used for various information processing terminals connected to servers through wired or wireless networks, such as palmtop computers, computers, notebook computers, personal digital assistants (Personal Digital Assistant, PDA), etc., and can be run in these terminals The software unit, hardware unit or a combination of software and hardware can also be integrated into these terminals as an independent pendant or run in the application system of these terminals, wherein:
[0060] The storage system protection device in this embodiment includes a storage operation amount detection unit 31 and a storage operation amount limiting unit 32, wherein:
[0061] The storage operation...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com