Safe, reliable and low-cost RFID mutual authentication method
A two-way authentication and RFID tag technology, which is applied in the field of wireless network communication and identity authentication, can solve problems that affect system security, are vulnerable to asynchronous attacks, and do not implement RFID tag authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The present invention will be described in detail below with reference to the accompanying drawings and examples.
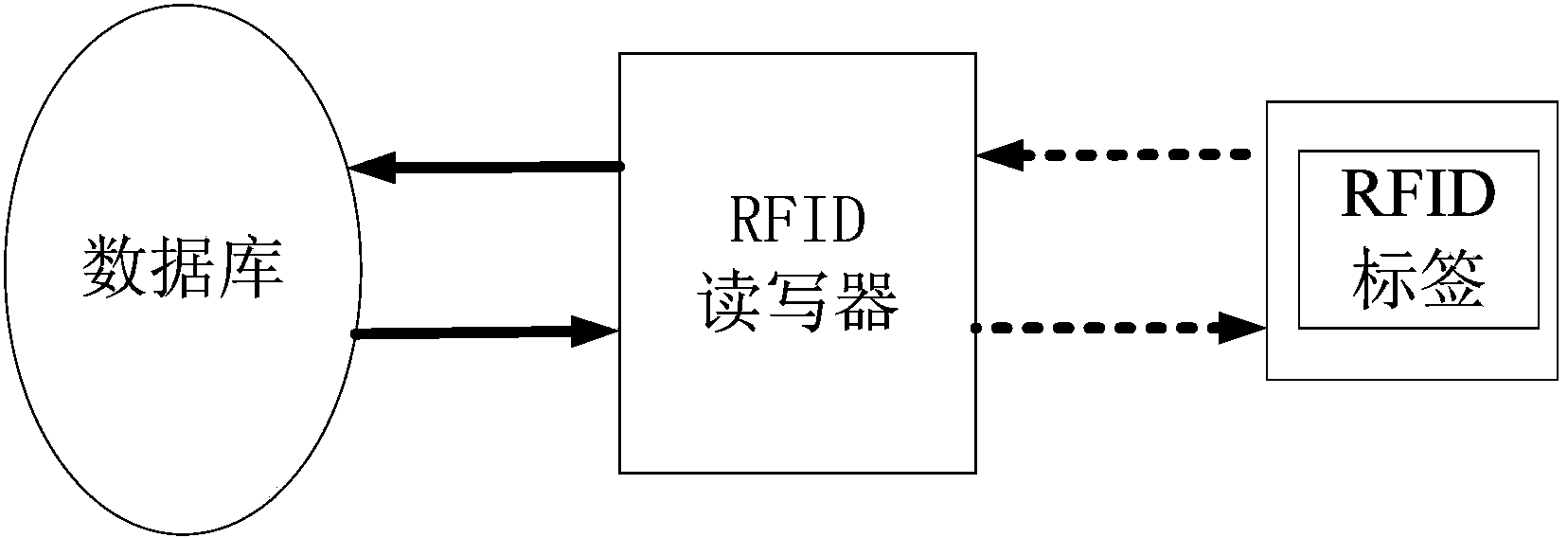
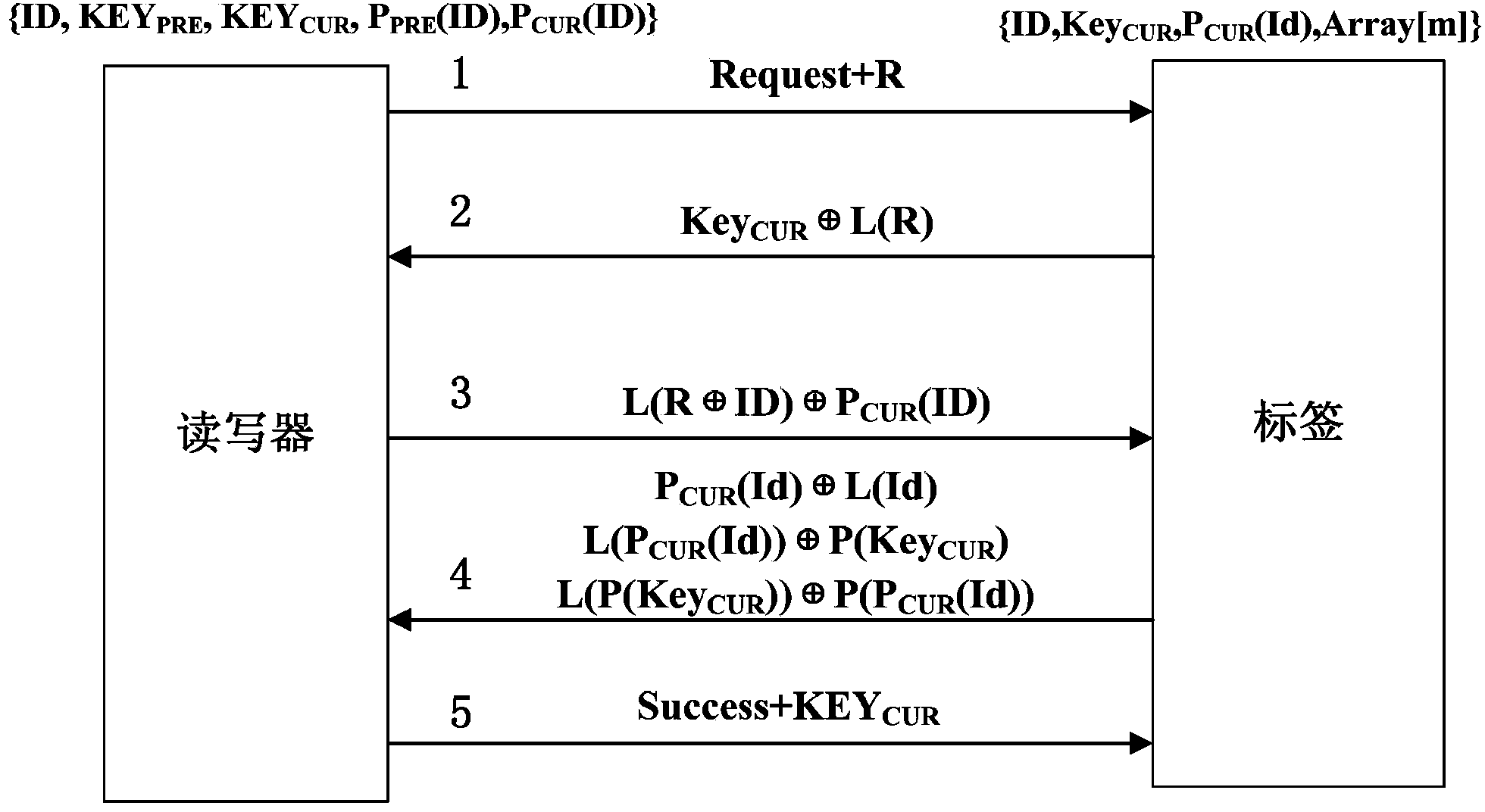
[0049] A safe, reliable, and low-cost RFID bidirectional authentication method, used for security authentication during wireless communication between an RFID tag and an RFID reader-writer in an RFID automatic identification system, the RFID automatic identification system including an RFID tag, an RFID reader-writer and backend database, which includes:
[0050] (1) Embed a linear feedback shift register and a physical unclonable function (Physical Unclonable Function, PUF) in the RFID tag; among them, the function of the linear feedback shift register is to generate pseudo-random numbers; the function of the physical unclonable function is to generate and The Id of the RFID tag corresponds to the spoofed Id, avoiding the plain text transmission of the RFID tag Id and key. Embed a random number generator and the same linear feedback shift register as the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com