Process memory protecting method based on auxiliary virtualization technology for hardware
A hardware-assisted and virtualized technology, applied in the direction of preventing unauthorized use of memory, can solve problems such as system performance impact, and achieve the effect of protecting memory space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The advantages of the above and / or other aspects of the present invention will become more apparent as the present invention will be further described in conjunction with the accompanying drawings.
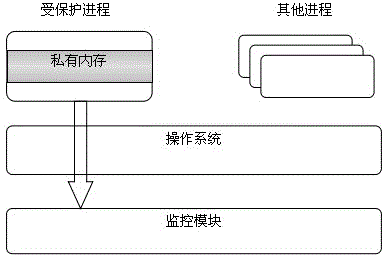
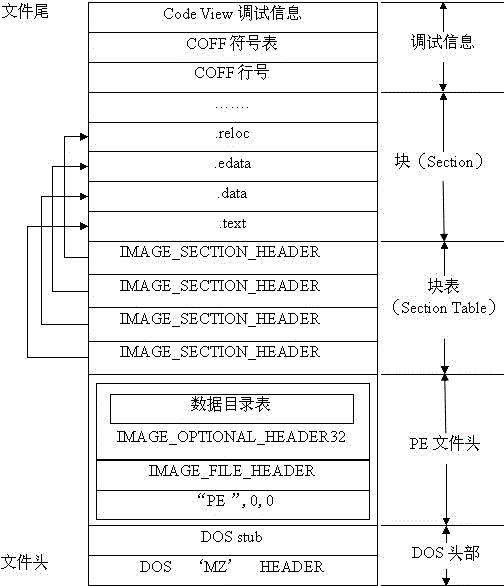
[0020] like figure 1 As shown, the process memory protection method based on hardware-assisted virtualization technology, using Intel VT (Virtualization Technology) technology to support virtualization hardware, realizes the security isolation of the process memory monitoring module and the operating system, and protects the protected process in the system The memory space is effectively protected. The invention prevents address modification attack by monitoring the modification of CR3 register and page table, and uses shadow page table mechanism and data execution protection technology to defend against code injection attack.
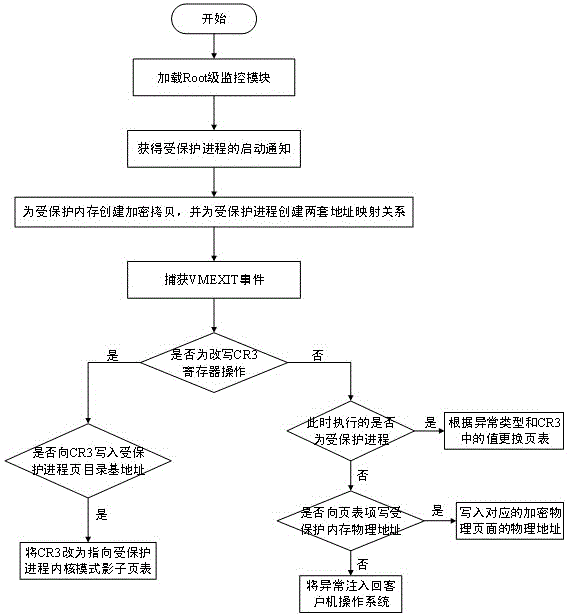
[0021] like figure 2 As shown, the flow of the process memory protection method based on hardware-assisted virtualization technology includes th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com