Information safety attack and defense system structure of cloud platform
A technology of information security and system architecture, applied in the field of information security, can solve problems such as different, lack of network attack and defense systems, difficulty in adapting to the needs of new technologies and new security threats, etc., to reduce and difficulty, reduce security risks, and easy to deploy and the effect of using
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
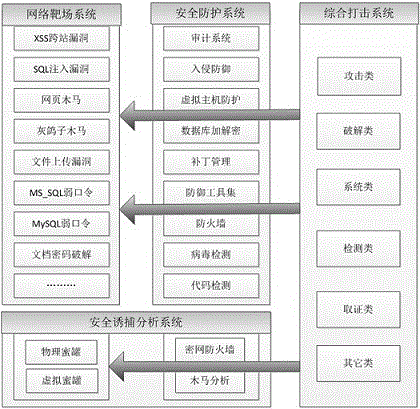
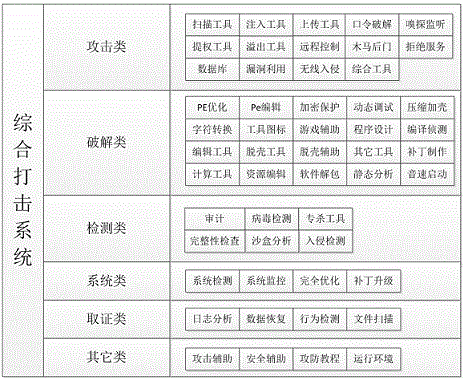
[0052] see figure 1 , The present invention provides a cloud platform information security attack and defense architecture, the architecture includes a network shooting range system, a security protection system, a comprehensive attack system and a security trap analysis system.
[0053] The network shooting range system is an important foundation of the offensive and defensive system. The system can be designed in a virtualized environment and has a variety of vulnerability images, which can simulate operating system-level, application-level, and network-level vulnerabilities, and can quickly and dynamically deploy attacked objects as needed. In this way, an opportunity for attack drills is provided for the attacking network, and at the same time, the effect of the attack can be detected.
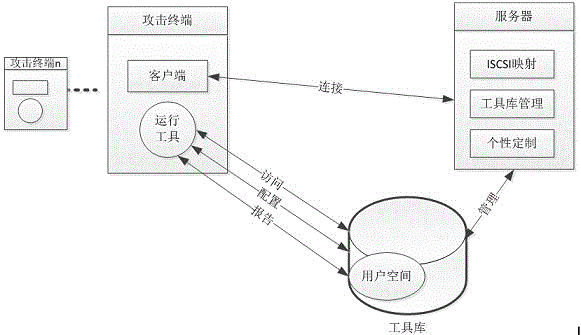
[0054] The network shooting range system can use a single or multiple servers to run a virtualized environment to realize the shooting range network. Each of the virtual servers is desig...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com