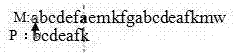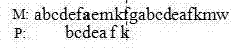Double-jump-based single mode matching method
A matching method and single-mode technology, applied in the field of single-mode matching based on double hopping, to achieve the effects of wide range of applications, improved detection speed, and improved real-time performance.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
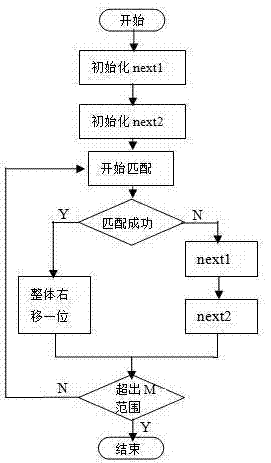
[0031] Such as figure 1 Shown can clearly understand the matching process of a kind of double-jump-based single pattern matching method of the present invention:
[0032] S21 initializes jump arrays next1 and next2;
[0033] S22 starts to match;
[0034] S23 If the matching is successful, the pattern string P[0...m-1] will be shifted one bit to the right as a whole, and if the matching fails, jump S to the right according to the jump array next1 1 characters, then press next2 to skip the second step, skipping S2 characters;
[0035] S24 judges whether the pattern string after the movement reaches or exceeds the end of the main string, if otherwise returns to S22, if then ends the matching, and outputs the positions of all character strings matched with the pattern string.
[0036] Further, the initialization rule of the jump array next1 is: when there is a character with the same bit as the main string M[pos+m] in the pattern string P[0,1...m-1], then the pattern string P[0...
Embodiment 2
[0044] Randomly select the following text as the main string: but in a larger sense, we can not dedicate, we cannot consecrate, we can not hallow this ground. the brave ten, living and dead, who struggled here, have consecrated it far above our power to add or detract. the world will little note nor long retetber what we say here, but it can never forget what they did here. it is for us, the living, rather to be dedicated to the great task retaining before us; dead, we take increased devotion to that cause for which they gave the last full teasure of devotion; that this nation, under god, shall have a new birth of freedot; and that governent of the people by the people and for the people shall not perish frot the earth. Select ground, the, here, cause, and earth as the pattern string (spaces and punctuation marks are not included in the actual experiment process). For each pattern string, record the number of comparisons and the number of successful matches using the matching ...
Embodiment 3
[0046] Factors such as the resource allocation mechanism of the hardware and operating system will make the time for each match different, and the time for matching will be within a time domain. This embodiment generates a random string of length 1,000,000 as the main string M, and generates lengths respectively A random character string with a length of 1, 10, 20, 30, 40, 50, 60, 70, 80, or 90 is used as the pattern string. Use the matching method of the present invention and the matching method based on the traditional Sunday algorithm to match the pattern strings in the main string, each pattern string matches 10,000 times, record the time domain of each pattern string under the two methods, and calculate the average value. The test environment is Intel(R) Core(TM) i3 CPU, the main frequency is 2.93GHz, the experimental data are as follows: Figure 8 Shown, wherein YC is the code name of the matching method of the present invention, and S is the code name of the matching m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com