Information processing device and information processing method
An information processing device and processor technology, applied in secure communication devices, computer security devices, electronic digital data processing, etc., can solve the problems of passwords that cannot be returned, heavy burden, and user information cannot be synchronized.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0028] A first embodiment of the present invention will be described.
[0029] [system structure]
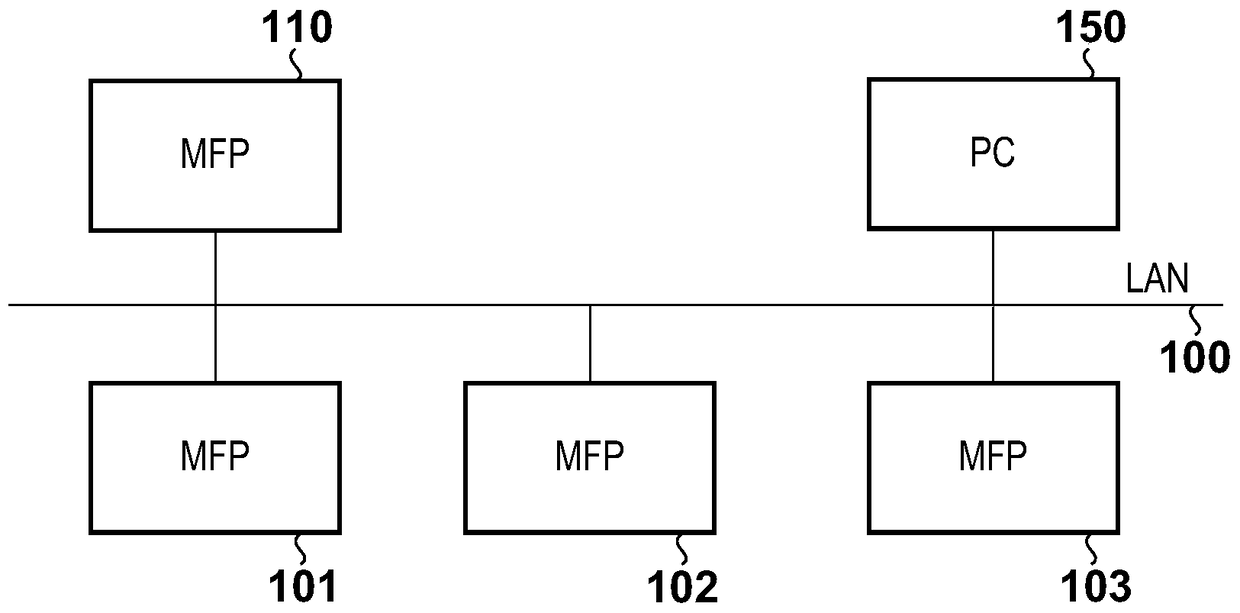
[0030] figure 1 is a block diagram showing an example of the structure of the entire system according to the present invention. Components to be described later are connected to the LAN 100 . The MFP 101 , the MFP 102 , the MFP 103 , and the MFP 110 are all multifunction peripherals (MFPs) and include an image reading device, a printing device, and a communication device. Each MFP has applications for copying, printing, scanning image transmission, and the like. Each MFP also has a function of performing user authentication prior to use of the MFP to enforce restrictions on use of these applications by each user, personalization by each user, and the like.
[0031] The PC 150 is a general PC (Personal Computer) installed with a web browser (not shown) and the like, and used to manage the respective MFPs.
[0032] [Hardware structure]
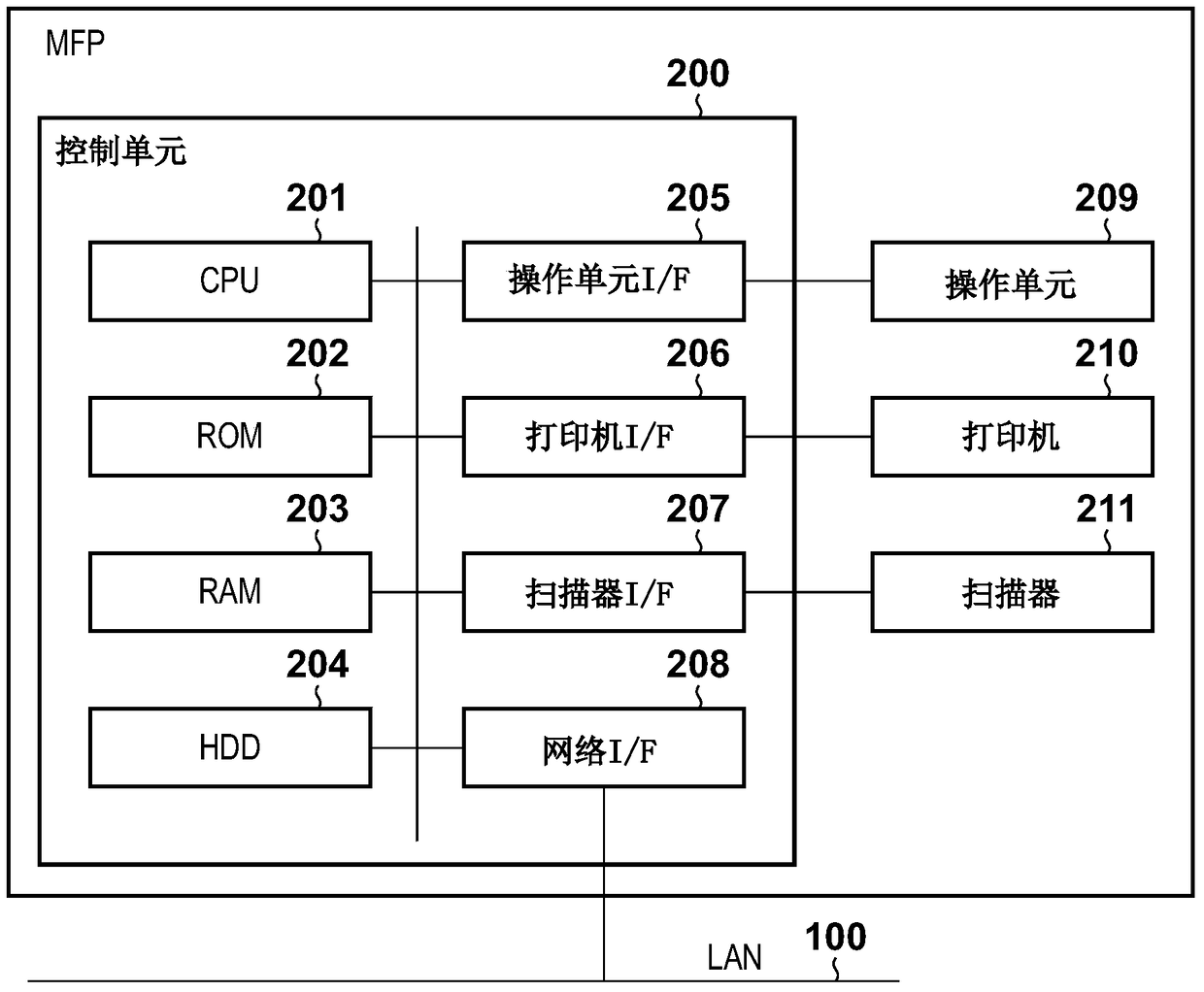
[0033] figure 2 It is a hardware bl...
no. 2 example
[0056] A second embodiment of the present invention will be described. In the second embodiment, the processing of the imported user information is performed using user authentication when accessing the web application of the MFP from the web browser of the PC connected to the network is used as a trigger.
[0057] Figure 11 The procedure performed to the web browser (not shown) of the PC 150 and the MFP 101 according to the present embodiment is exemplified. This processing procedure is implemented by causing each of the CPUs of the PC and the MFP to read the program stored in the storage unit and execute the program.
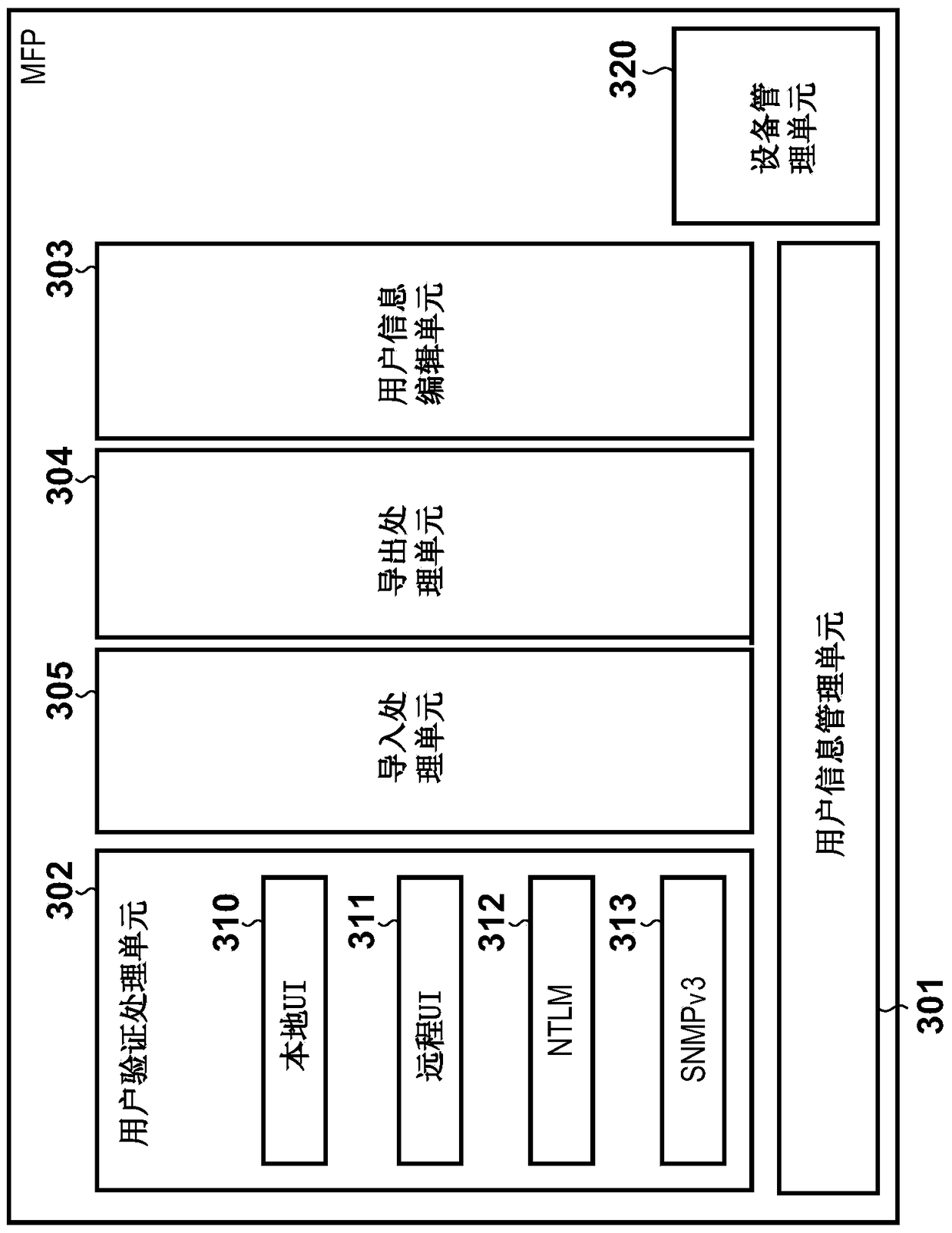
[0058] In step S1101 , the remote UI 311 of the user authentication processing unit 302 of the MFP 101 transmits a web page for user authentication to the PC 150 . The content of the user authentication information page used here is the same as the screen displayed on the operation unit 209 in the first embodiment ( Figure 4 ) have the same content. In s...
no. 3 example
[0067] A third embodiment of the present invention will be described. In the third embodiment, the trigger to update user information managed as a hashed password after import is not the MFP where the user information exists but another MFP connected to the network.
[0068] Figure 12 is a flowchart of updating the user information management unit 301 of the MFP 102 immediately after the process of updating the user information management unit 301 using authentication on the operation unit 209 of the MFP 101 as a trigger. ie, this is in Figure 10 Processing performed between the processing of step S1007 and the processing of step S1008 in .
[0069]In step S1007, the user information management unit 301 of the MFP 101 updates the password of a certain user's record. After that, in step S1201 , the user information management unit 301 of the MFP 101 acquires from the device management unit 320 an MFP whose password should also be updated. MFPs whose passwords should be up...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com