Visible light-activated access control method with hidden channel
An optical control access control and hidden channel technology, which is applied in the field of optical communication, can solve problems such as the security impact of access control devices, and achieve the effects of avoiding information interception, improving privacy, and avoiding information forgery and identity forgery.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
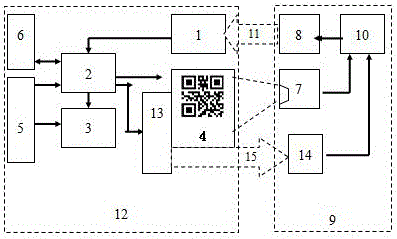
[0039] An embodiment of the visible light control access control method with hidden channel of the present invention is as follows:
[0040] (1) Establish a visible light-controlled access control device with a hidden channel, including: a mobile unlocking terminal 9 and a light-controlled access control lock 12 .
[0041]The mobile unlocking terminal 9 includes: a light emitting module 8 , a display scanning module 7 , a control module 10 , and an optical key receiving module 14 .
[0042] The light emitting module 8 is used to send the light signal 11 of the identity information of the mobile unlocking terminal 9 and the authentication information of unlocking, and the function of this module is realized by LED.
[0043] The display scanning module 7 is used for scanning and receiving the two-dimensional code displayed by the display module 4 of the light-controlled access control lock 12, and the function of this module is realized by a two-dimensional code scanning head. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com