Proactive defense method for call interception in telecommunication network
An active defense and telecommunications network technology, applied in the field of communication, to achieve the effect of easy interception, increasing the difficulty of cracking, and achieving weak correlation or irrelevance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
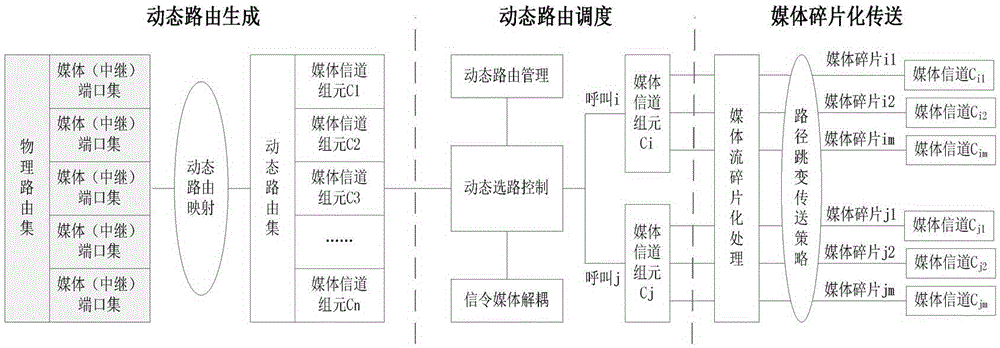
[0020] Example 1: Combining Figure 1-Figure 2 , a kind of active defense method against telecommunication network call wiretapping, this method comprises the following steps:
[0021] Step 1: Establish a dynamic routing set; in a telecommunication network, a physical routing refers to a set of channels with fixed source and destination addresses, fixed physical bandwidth, and static binding of channel identifiers and physical channels. Dynamic routing is based on physical routing. It is a logical routing generated by using the SS7 multi-point code technology, IP address pool technology and the dynamic address mapping method agreed between network elements. A set of channels with variable source and destination addresses, variable bandwidth capacity, and temporary pairing of channel identifiers and physical channels. Different from physical channels, such as 64kb / sTDM voice channel or RTP port, where the basic unit of service bearing in physical routing is, the basic unit of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com