Method for protecting privacy of cloud computed big data
A big data and cloud protection technology, applied in the field of cloud computing, can solve problems such as reducing system performance, and achieve the effects of improving processing efficiency, availability, and effectiveness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
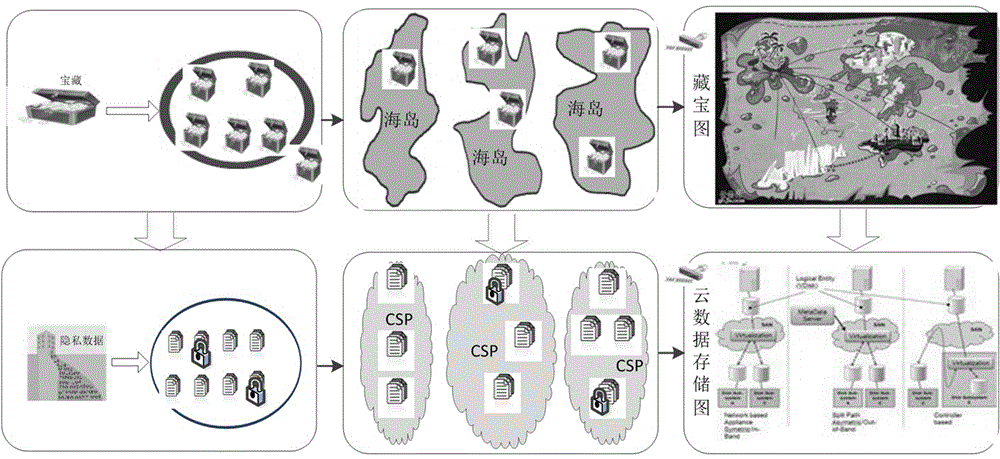
[0028] The present invention is a method for protecting the privacy of cloud computing big data, and its specific implementation plan will combine a certain medical big data containing patient private information Describe in detail, including the following specific steps:
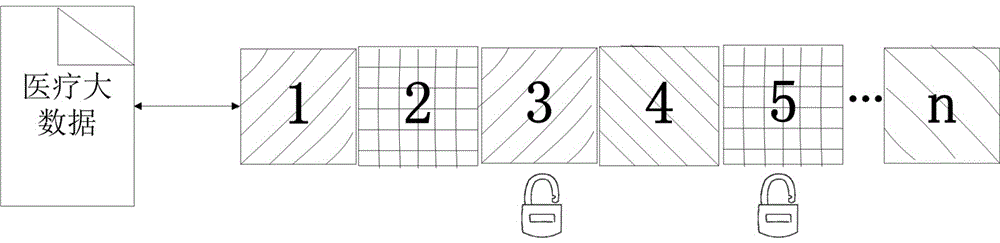
[0029] The first step is to learn from the idea of data packet division in the TCP / IP communication protocol in the Internet, and logically divide the big data of cloud tenants into logical blocks. Each logical block contains the relevant identifiers of big data tenant owners and cloud storage service providers, Identity or address information as well as serial numbers, unique marks, privacy-critical data block marks, shared marks, etc.
[0030] In this example, It is a combination of big data composed of different data types, then choose to divide the data into blocks according to the type of data, that is, divide the logical data blocks according to the extension of the data file, such as pdf, rar, d...
Embodiment 2
[0047] The difference between this embodiment and Embodiment 1 is that in Step 1, another logical block method is adopted, that is, the medical big data in this example It is a certain type of complete data. Use the data block software ArcGIS to block the large data according to the fixed data byte size, such as 4M size.
[0048] The data blocks divided by data size are also identified for each data block. According to actual needs, each data block additionally contains some necessary identification information, such as serial number, identification number ID, logical sequence number , privacy key identifier , encrypted identification Wait.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com