Wireless sensor network key management method based on key table
A wireless sensor and network key technology, applied in the field of wireless sensor networks, can solve the problems such as the inability to guarantee the balance between the calculation overhead and the communication overhead, the lack of a pair key and a group key key management system scheme, etc., so as to reduce the communication overhead. , the effect of alleviating resource constraints and resisting network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Hereinafter, the preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings.
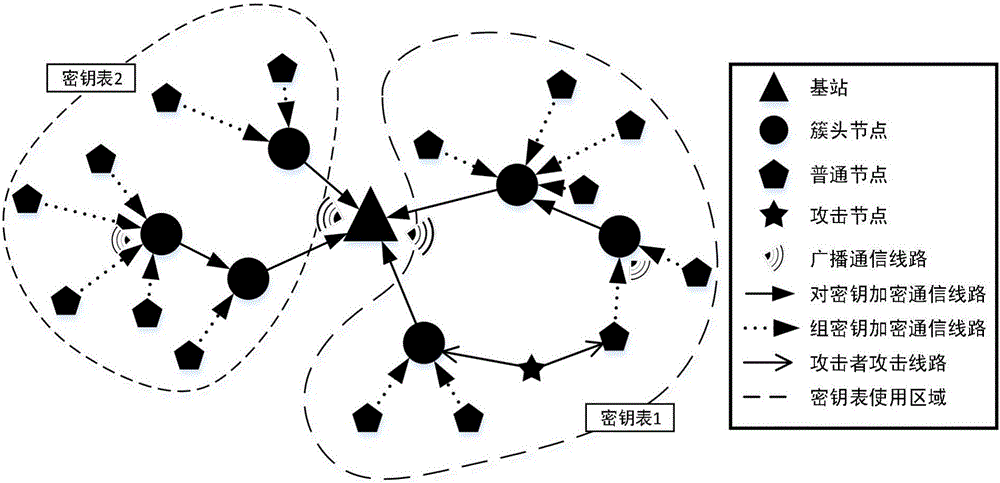
[0042] In this embodiment, the network adopts a clustered topology, such as figure 1 As shown, the nodes can be safely clustered in the initial stage of network establishment (the number of nodes in each cluster is about 5-20), in which the sensor nodes are responsible for data collection, and send to the cluster head node by encrypting the key, and the cluster head node sends the data After being aggregated, it is encrypted and forwarded to the base station in the form of single-hop or multi-hop. That is, the nodes in the cluster only communicate with the corresponding cluster head node, and the cluster head node communicates with neighbor nodes or base stations, and the message is sent in a broadcast mode. The base station is unbreakable, has unlimited energy and storage capabilities, and the base station can obtain the status of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com