A Hyperchaotic Image Encryption Method
An encryption method and hyper-chaotic technology, applied in image data processing, image data processing, instruments, etc., can solve the problems of time-consuming, low encryption efficiency, transmission and distribution difficulties, etc., achieve wide application prospects, resist classic attacks, improve Effects of bad traits
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
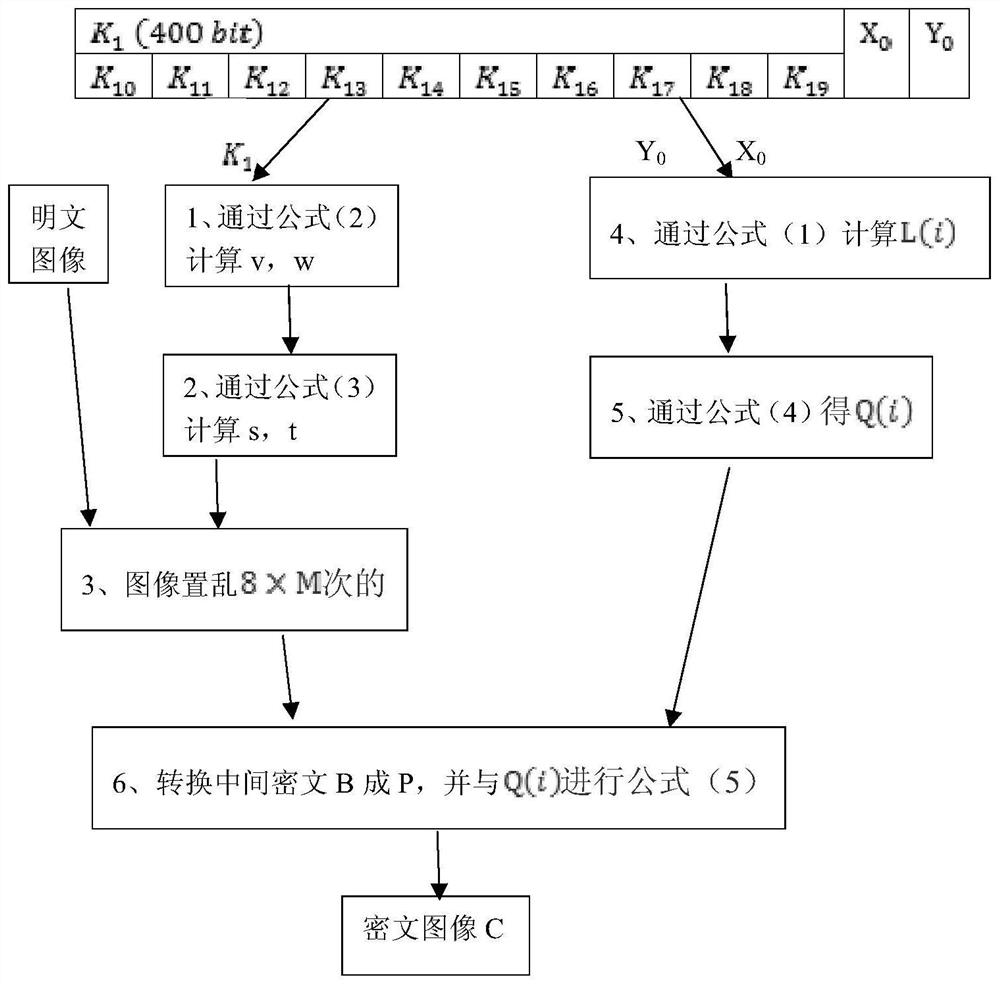
[0044] The specific implementation steps are as figure 1 The encryption flow chart is shown.
[0045] The present invention will realize image encryption, first will realize the initialization process of key, as figure 2 shown.
[0046] The encryption key K is mainly composed of a 400-bit binary auxiliary key K 1 , enter key X 0 , Y 0 It consists of three parts.
[0047] Step 1: First, the length of 400-bit binary auxiliary key K 1 Divide into ten binary units with a length of 40 bits, K 10 , K 11 ,...,K 19 .
[0048] Step 2: Enter key X 0 , Y 0 As the initial key of Hyperhenon mapping, as shown in formula (1), where c=1.76, d=0.1, and X 0 , Y 0 Take a value between (0,1) to generate a set of hyperchaotic sequences for diffusion operations.
[0049]
[0050] k=0, 1, 2, ... (1)
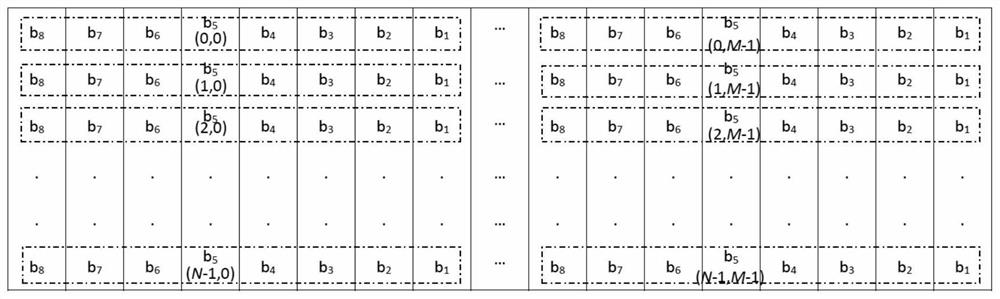
[0051] in completion figure 2 After the key initialization process, proceed to figure 1 During the image encryption process, an intermediate bit ciphertext matrix is also genera...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com