Multi-KMC key recovery method
A key recovery and key technology, applied in the field of information security, can solve the problems of KMC breach and key leakage, and achieve the effect of ensuring security, simplifying complexity, and ensuring transmission security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
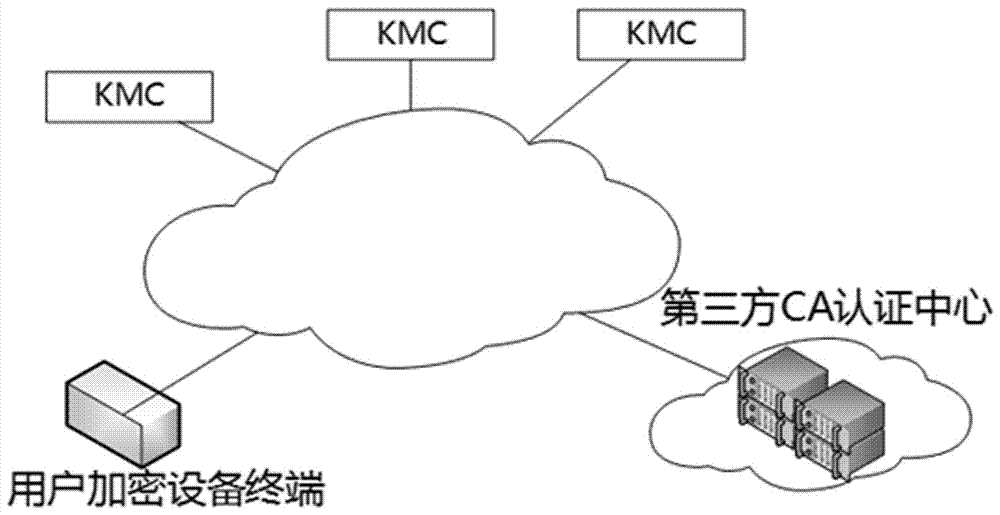
[0042] A multi-KMC key recovery system, which includes a user encryption terminal, KMC and a third-party CA center;
[0043] The user encryption terminal is responsible for the generation of random numbers and keys, key division, and data packet signature verification, encryption and decryption operations;
[0044] The KMC is responsible for the preservation and restoration of the split key;
[0045] The third-party CA center is responsible for issuing digital certificates for each participant.
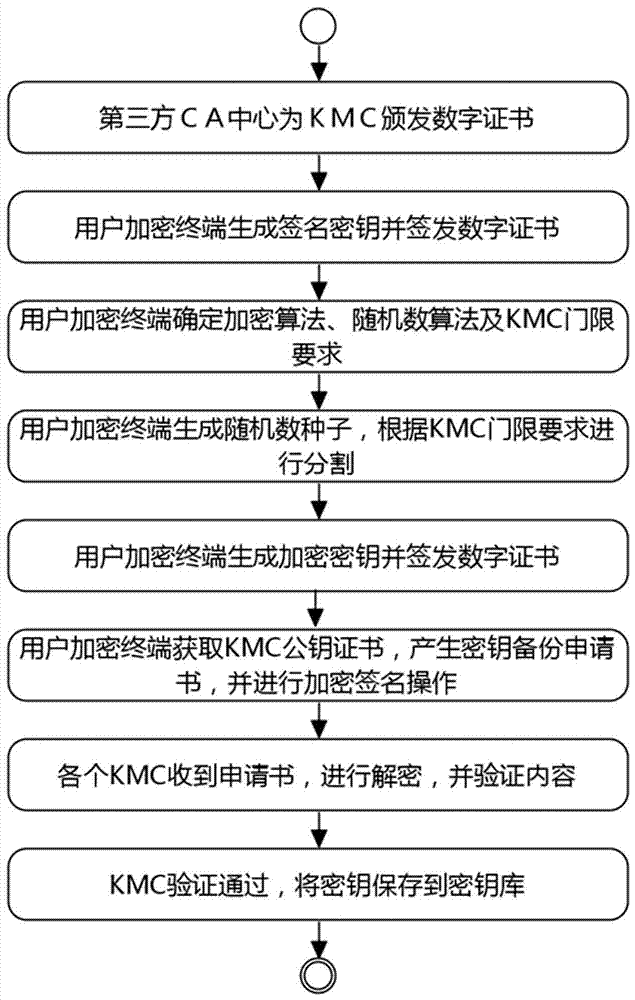
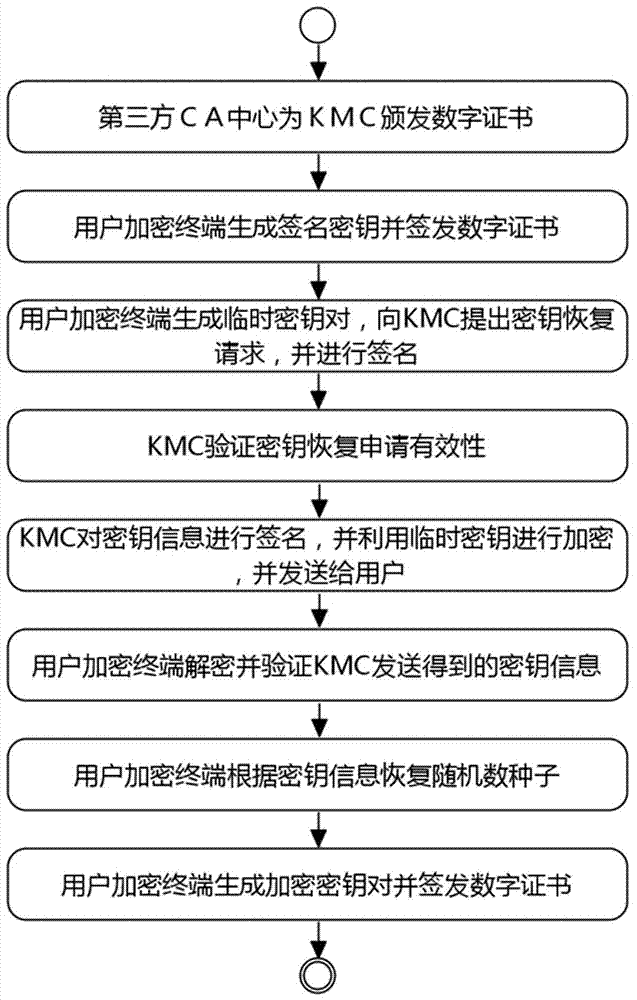
[0046] The multiple KMC key recovery method is realized through two parts: key backup and key recovery;
[0047] Key backup: The third-party CA center first issues a digital certificate to each participant, and then uses a user encryption terminal to generate a random number. According to the threshold number of the set KMC, a threshold algorithm is used to split the key, and the split random number Sign it, encrypt it with the public key of each KMC, and upload it to KMC for key backup;
[004...
Embodiment 2
[0068] A multi-KMC key recovery system, which includes a user encryption terminal, KMC and a third-party CA center;
[0069] The user encryption terminal is responsible for the generation of random numbers and keys, key division, and data packet signature verification, encryption and decryption operations;
[0070] The KMC is responsible for the preservation and restoration of the split key;
[0071] The third-party CA center is responsible for issuing digital certificates for each participant.
[0072] For clarity of description, assume that in this embodiment, the encryption key algorithm is the SM2 national secret algorithm, the SM3 national secret algorithm is used as the digest algorithm, the SM3 SM2 national secret algorithm is used as the signature algorithm, and the digital certificate is in the X509 format. In addition, the KMC threshold mofn involved in key backup and recovery is (2,3), which means that there are 3 KMCs used to back up the key, and any 2 of them can restore ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com