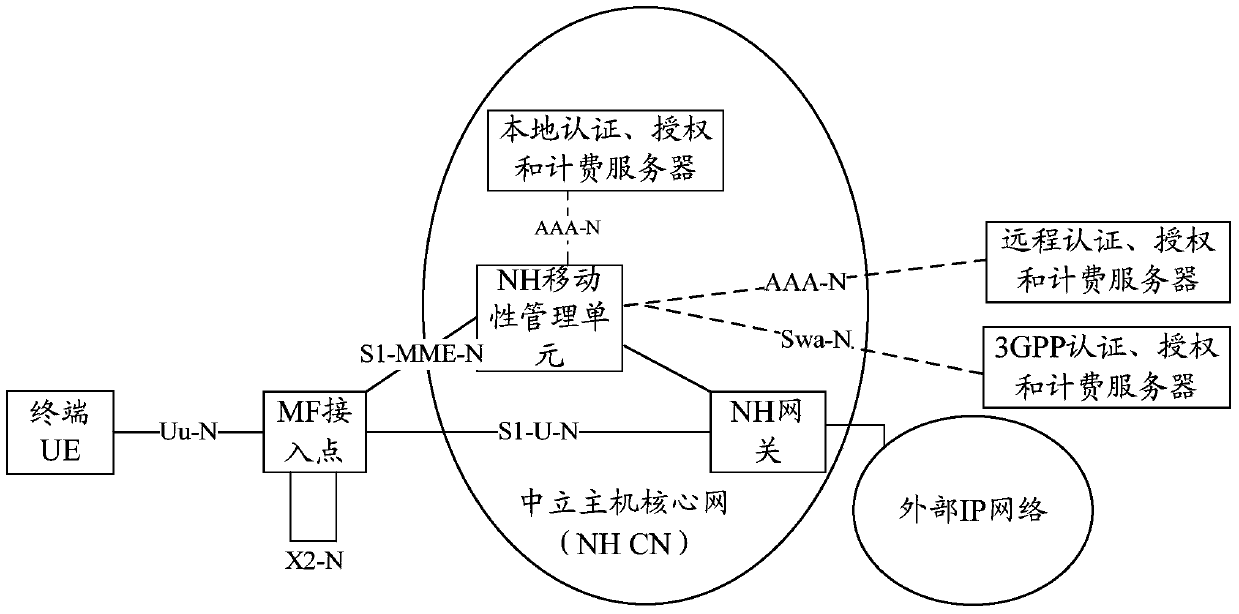
Method, device and terminal for terminal access network
A terminal access and network technology, applied in the field of communication, can solve problems such as affecting network performance and heavy network signaling burden, and achieve the effects of improving network performance, reducing network signaling burden, avoiding authentication and bearer establishment/release
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
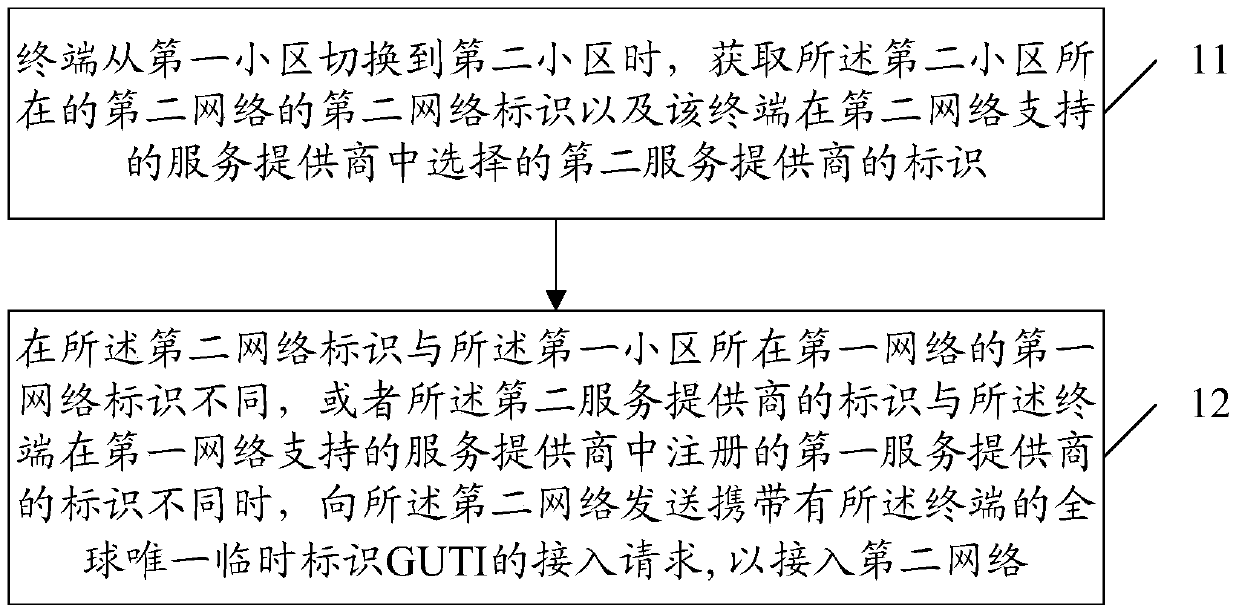
[0042] Such as figure 2 As shown, the first embodiment of the present invention provides a method for a terminal to access a network, including:
[0043] Step 11, when the terminal switches from the first cell to the second cell, obtain the second network identifier of the second network where the second cell is located and the second service provided by the terminal selected from the service providers supported by the second network Merchant's logo.
[0044] In this step, the terminal may perform cell reselection during the moving process. The terminal first performs cell reselection in a cell that is the same as the first network ID of the first network where the first cell is located. For example, the signal of the cell does not meet the requirements or the system broadcasts an indication that the cell is a prohibited access cell or a blocked cell; then the terminal can only select a cell that is different from the first network ID. When the terminal selects a suitable I...
no. 2 example
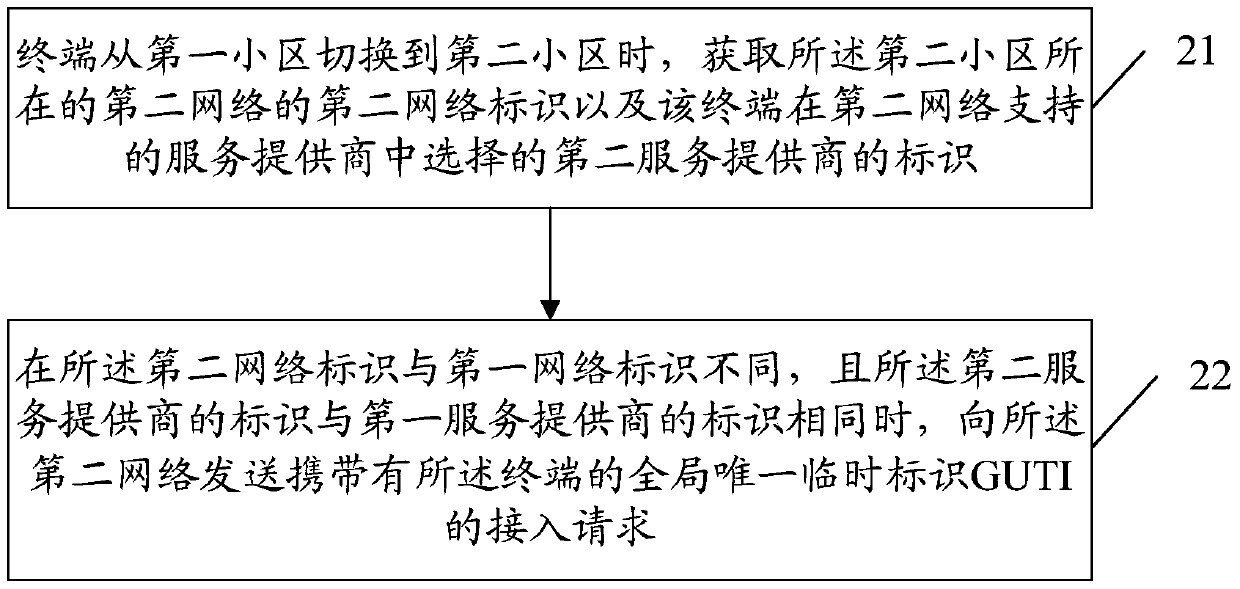
[0050] Such as image 3 , Figure 4 As shown, the second embodiment of the present invention provides a method for a terminal to access a network, including:
[0051] Step 21 is the same as Step 11 above.
[0052] Step 22, when the second network identifier is different from the first network identifier, and the second service provider's identifier is the same as the first service provider's identifier, send a message carrying the terminal to the second network The access request of the globally unique temporary identifier GUTI; or,
[0053] Step 23, when the second network ID is different from the first network ID, and the second network ID is in the set of network IDs of the network equivalent to the first network ID, and the ID of the second service provider is the same as the first network ID When the identifiers of the service providers are different, and the identifier of the second service provider is in the identifier set of the equivalent service provider of the fi...
no. 3 example
[0059] Such as Figure 5 As shown, the third embodiment of the present invention provides a method for a terminal to access a network, including:
[0060] Step 31 is the same as Step 11 above.
[0061] Step 32: When the second network identifier is different from the first network identifier, and the second service provider's identifier is the same as the first service provider's identifier, determine whether the terminal is currently located in the terminal saved Within the location area in the tracking area list (TA list).
[0062] Step 33, if the terminal is located in the location area in the tracking area list, send a service request carrying the globally unique temporary identifier GUTI of the terminal to the second network;
[0063] Step 34: If the terminal is located in a location area outside the tracking area list, send a location area update request or an attach request carrying the terminal's globally unique temporary identifier GUTI to the second network.
[00...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com