Method for carrying out RSA encryption storage on data dictionary information
A data dictionary and encrypted storage technology, applied in the field of cloud computing, can solve problems such as data information leakage, and achieve the effect of protecting sensitive data, difficult to crack, and high execution efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0039] The process of initializing management node A in step b) is:
[0040] b-1) start management node A;
[0041]b-2) After the management node A starts successfully, it initializes the local embedded database engine and opens the database file, and then enters the waiting state, waiting for the data storage node D, service provider node S and log node L to register.
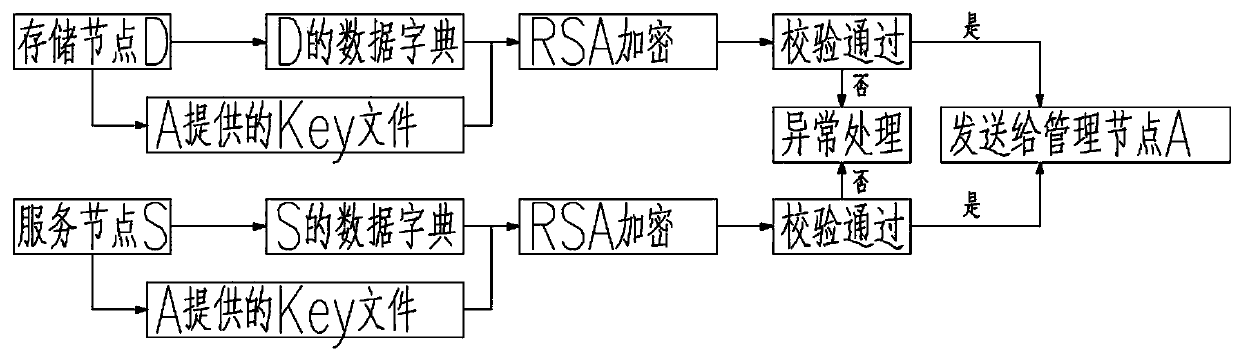
[0042] The so-called RSA encryption algorithm is currently the most influential public key encryption algorithm, and is generally considered to be one of the best public key schemes at present. RSA is the first algorithm that can be used for encryption and digital signature at the same time. It can resist all cryptographic attacks known so far and has been recommended by ISO as a public key data encryption standard. The RSA encryption algorithm is based on a very simple number theory fact: it is very easy to multiply two large prime numbers, but then it is extremely difficult to factorize their products, so t...
Embodiment 2
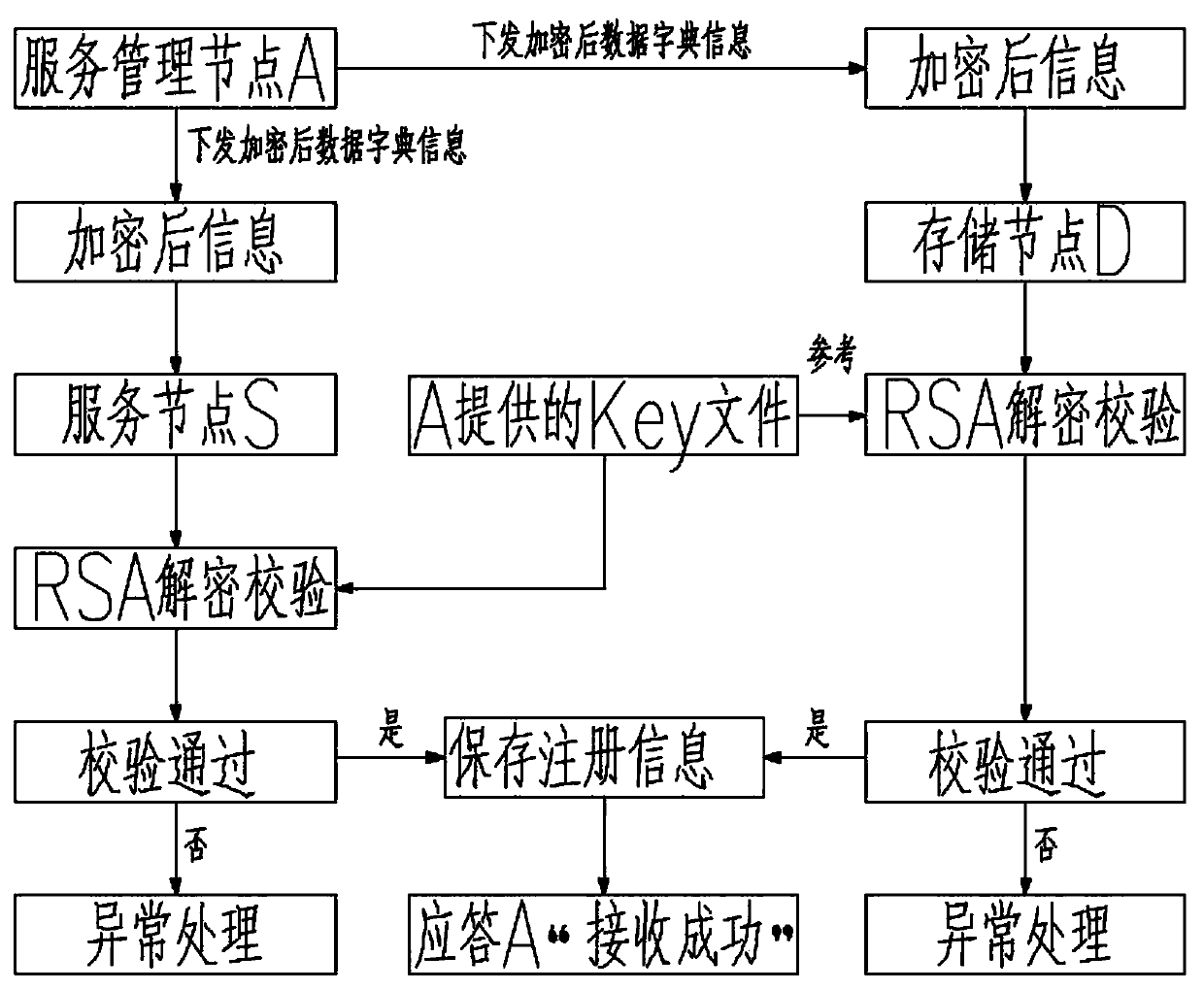
[0044] The service nodes registered with the management node A in step c) are the data storage node D, the service providing node S and the log node L. What each type of service node reports is the data dictionary information that needs to be released when the node itself provides services. The information is encrypted using the Key file information provided by management node A according to the RSA algorithm. Encrypted and uploaded to management node A.
Embodiment 3
[0046] The process of registering with management node A in step c) is:
[0047] c-1) Start the pre-registered service node. After the service node is successfully started, query the local database to obtain the configuration information of the service node and put it into the memory;
[0048] c-2) After the configuration information is obtained successfully, register with management node A. At this time, provide the service registration code and service access password provided by management node A, and send a registration request to management node A;
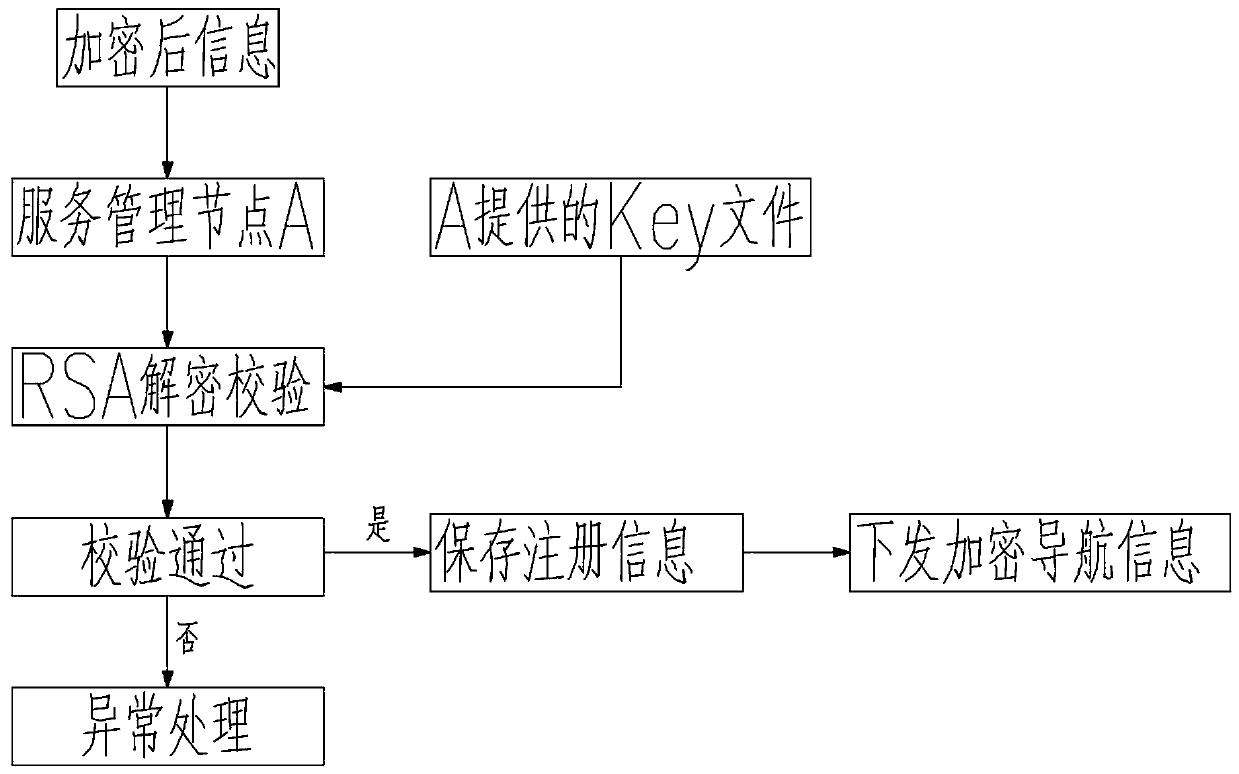
[0049] c-3) Management node A verifies after receiving the registration request, saves the information of the pre-registered service node in its own resource library after the verification is passed, and adds a registered service node on the management control platform of management node A.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com