Electronic evidence consolidation method and system, and equipment
A technology of electronic evidence and solidification method, which is applied in transmission systems, electrical components, user identity/authority verification, etc., and can solve the problems of fragile electronic evidence, difficulty in reviewing authenticity, and beyond recognition
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
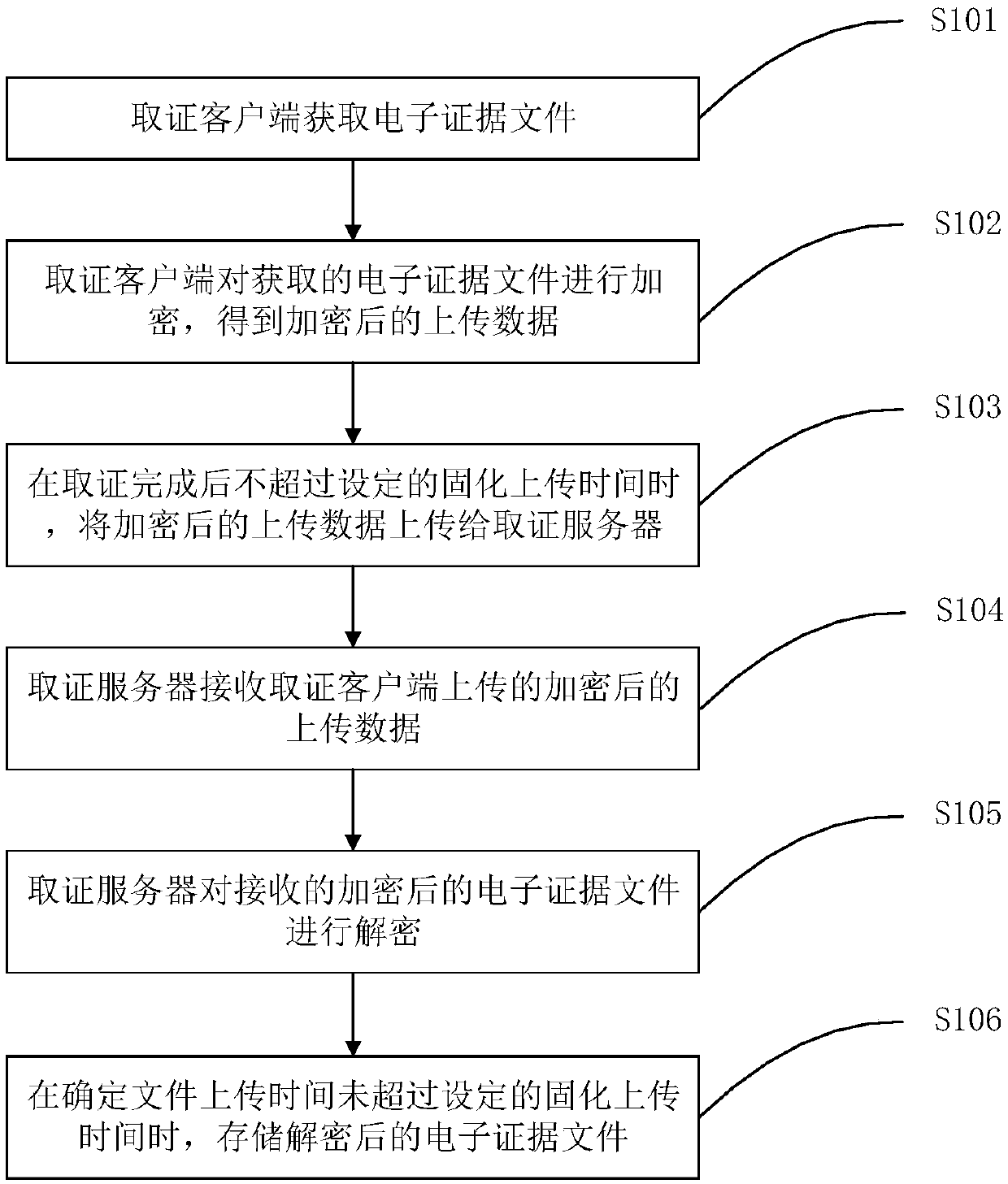
[0085] Embodiment 1 of the present invention provides a method for curing electronic evidence, the process of which is as follows figure 1 shown, including the following steps:
[0086] Step S101: the evidence collection client obtains electronic evidence files.
[0087] The evidence collection client starts the evidence collection process according to the user's evidence collection instructions; according to the evidence collection method selected by the user, it uses screen recording or screenshots to obtain the electronic evidence files requested by the user.
[0088] Documents, pictures, audio and video, digital certificates, computer programs and other electronic files, information published on web platforms such as web pages, blogs, microblogs, circle of friends, post bars, and online disks, user registration information, identity authentication information, electronic transaction records, communications Records, login logs and other information, as well as communicatio...
Embodiment 2
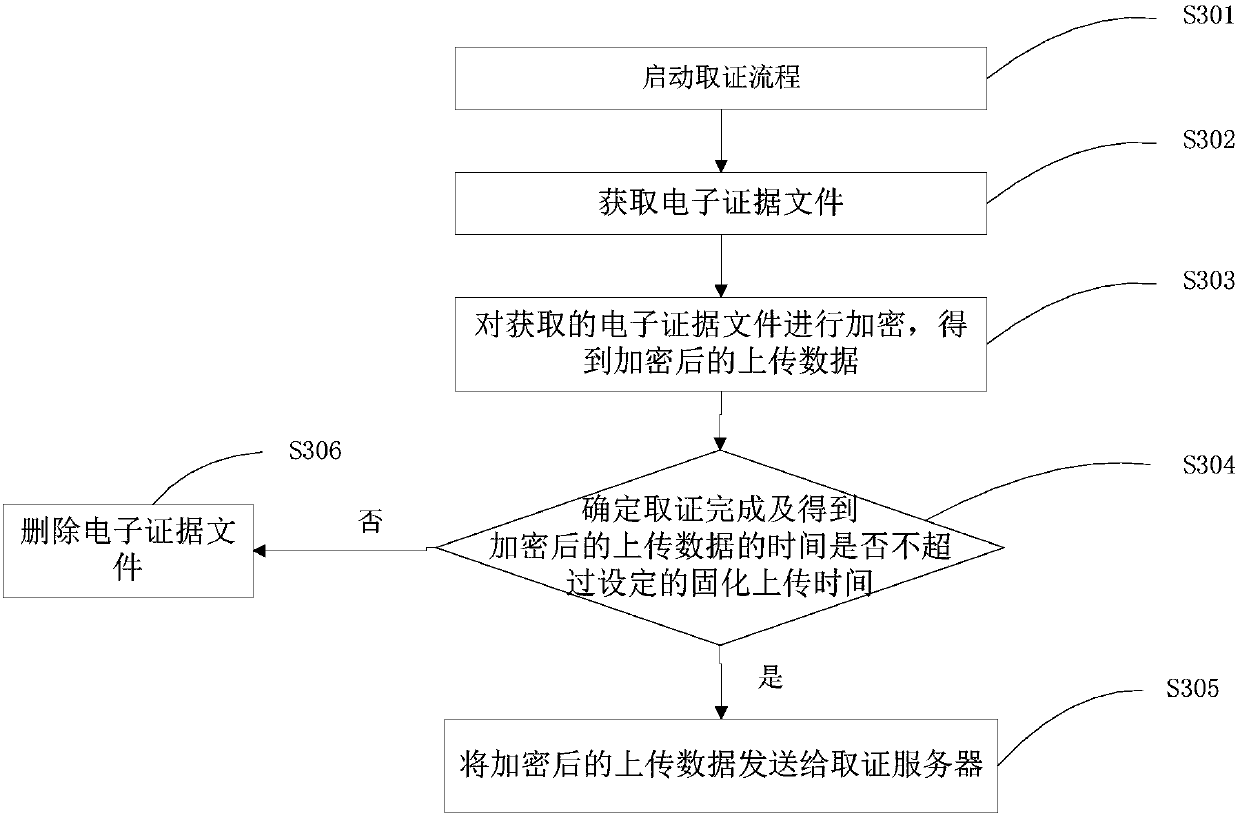
[0176] Embodiment 2 of the present invention provides a specific implementation process of the electronic evidence curing method, the flow of which is as follows Figure 5 shown, including the following steps:
[0177] Step S501: Start the evidence collection process.
[0178] The forensics client starts the forensics process after receiving the user's forensics instruction.
[0179] Optionally, the forensics client restarts the forensics process according to the instructions sent by the forensics server to resend the electronic evidence files after the electronic evidence files are deleted, until the number of times of re-acquisition exceeds the set threshold.
[0180] Step S502: Obtain electronic evidence files.
[0181] The forensics client collects electronic data according to the screen recording or screen capture method selected by the user, and at the same time collects the subject information, environmental information, process information, etc. that generate the ele...
Embodiment 3
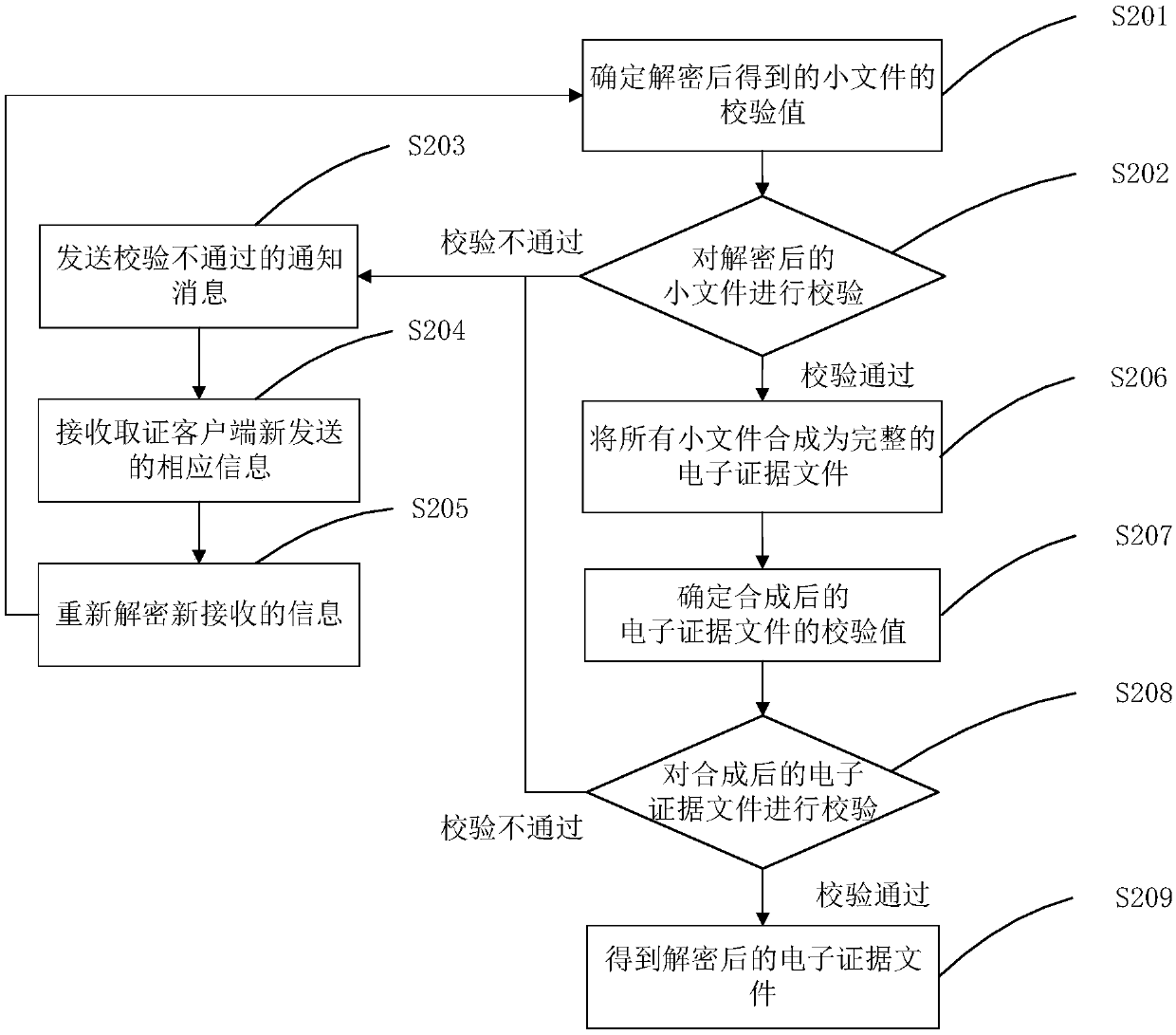
[0199] Embodiment 3 of the present invention provides another specific implementation process of the electronic evidence curing method, the flow of which is as follows Figure 6 shown, including the following steps:
[0200] Step S601: the forensics client starts the forensics process.
[0201] Step S602: the evidence collection client obtains electronic evidence files.
[0202] Step S603: Divide the electronic evidence file into several small files.
[0203] The forensics client divides the obtained electronic evidence files into several small files according to the selected rules.
[0204] Step S604: Determine the hash value corresponding to each small file.
[0205] The forensics client uses the selected hash calculation method to calculate the hash value of each small file as the verification value of the corresponding small file. Wherein, the calculation method of the hash value may select the Secure Hash Algorithm (Secure Hash Algorithm, SHA1) algorithm, may select t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com