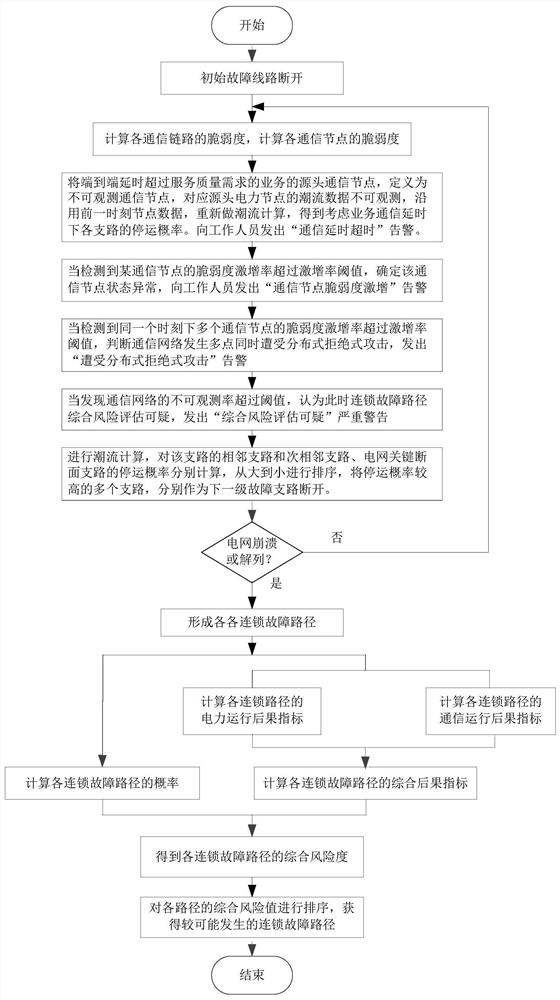
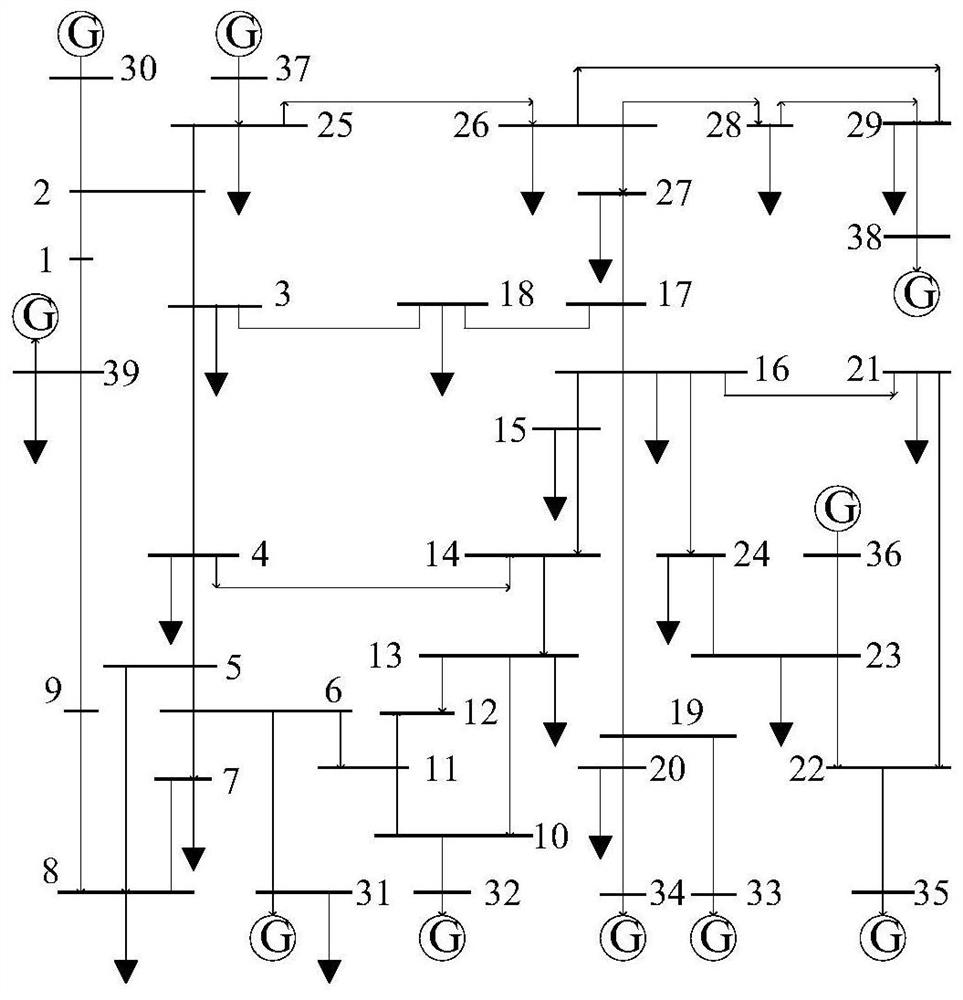
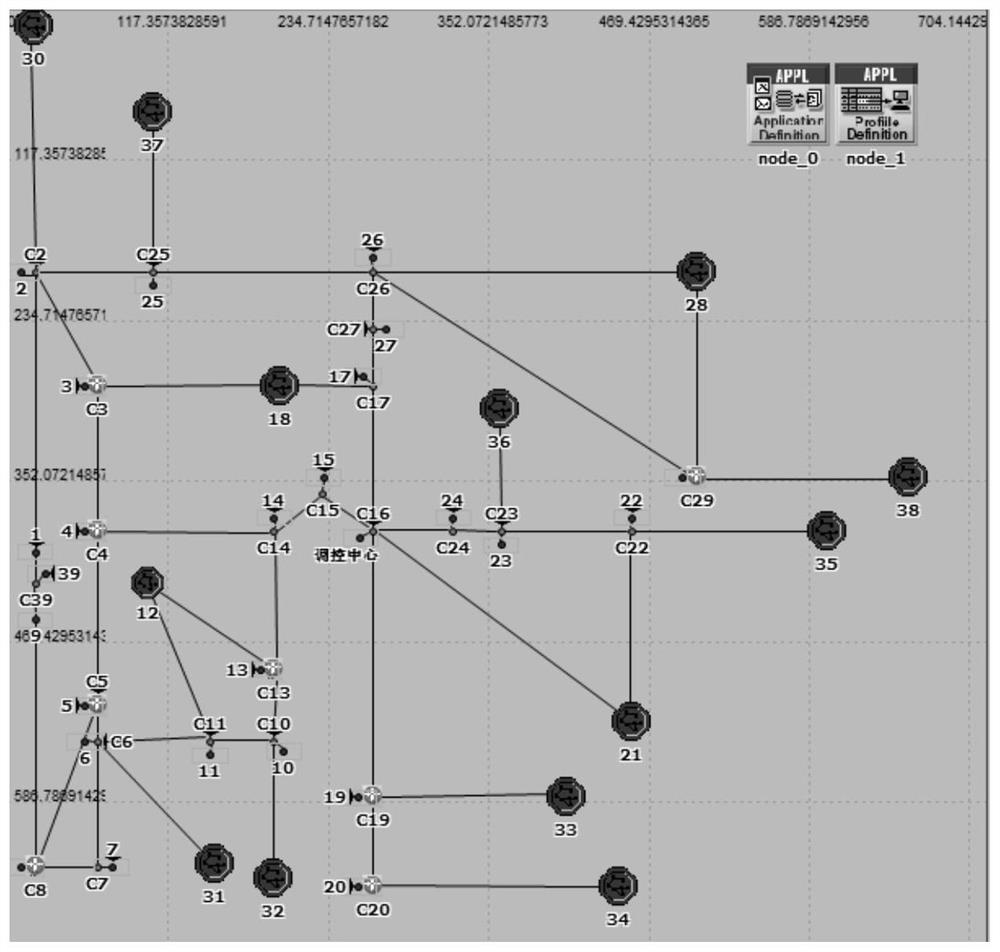
Risk assessment and warning method of cascading faults in interconnected power grid considering communication vulnerability
A technology for cascading failures and interconnecting power grids, applied in data processing applications, instruments, computing, etc., can solve the problem of undiscussed importance, lack of discussion of real-time performance indicators of communication links and communication nodes, and in-depth risk assessment methods for cascading failure paths, etc. question
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0209] Set up DDoS attack nodes in the OPNET communication simulation software, set two attack modes to simulate DDoS attacks on communication nodes in different locations, study the results of DDoS attacks in different locations on the comprehensive risk assessment of chain failure paths, and set up DDoS attack nodes , that is, set the source IP address as an unreachable fake address. After setting up a DDoS attack node, set up its internal business model. Connect multiple DDoS attack client nodes to the internal switch or core router of the communication node, so as to adjust the DDoS attack intensity of a communication node. The setting interface of multiple DDoS attack client nodes targeting internal switches or core routers in OPNET is as follows: Figure 4 shown.
[0210] The power branch 2-3 is set as the initial fault branch, and two attack modes are set for comparison, and the impact of the location of the attacked communication node on the risk assessment of power ...
Embodiment 2
[0229] Randomly select communication nodes in different locations to carry out DDoS attacks. For power nodes whose power flow data is unobservable, the data of the moment before the attack is used to carry out the risk assessment of cascading failures. The attack intensity takes the ratio of the number of attacked communication nodes to the total number of communication nodes, such as 5%, 10%, 15%, 20%, 25%, 30%, 35%, and 40%. The power branch 2-3 is set as the initial fault branch disconnected, and the more likely cascading failure paths under different DDoS attack intensities are studied.
[0230] Power risk P of each cascading failure path under different DDoS attack intensities L-ev , communication risk degree C L-ev , comprehensive risk R iskL-ev As shown in Table 6, Figure 5 shown.
[0231] Table 6 The highest comprehensive risk of cascading failure paths under different DDoS attack intensities
[0232] Attack Strength / % Highest risk cascading failure ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com