Safe protection system and method
A security protection and subsystem technology, applied in transmission systems, electrical components, etc., can solve the problems of insufficient controllability, inflexible deployment, poor scalability, etc., to reduce packet copying, flexible deployment, and easy operation and maintenance. management effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments. The following examples are used to illustrate the present invention, but are not intended to limit the scope of the present invention.
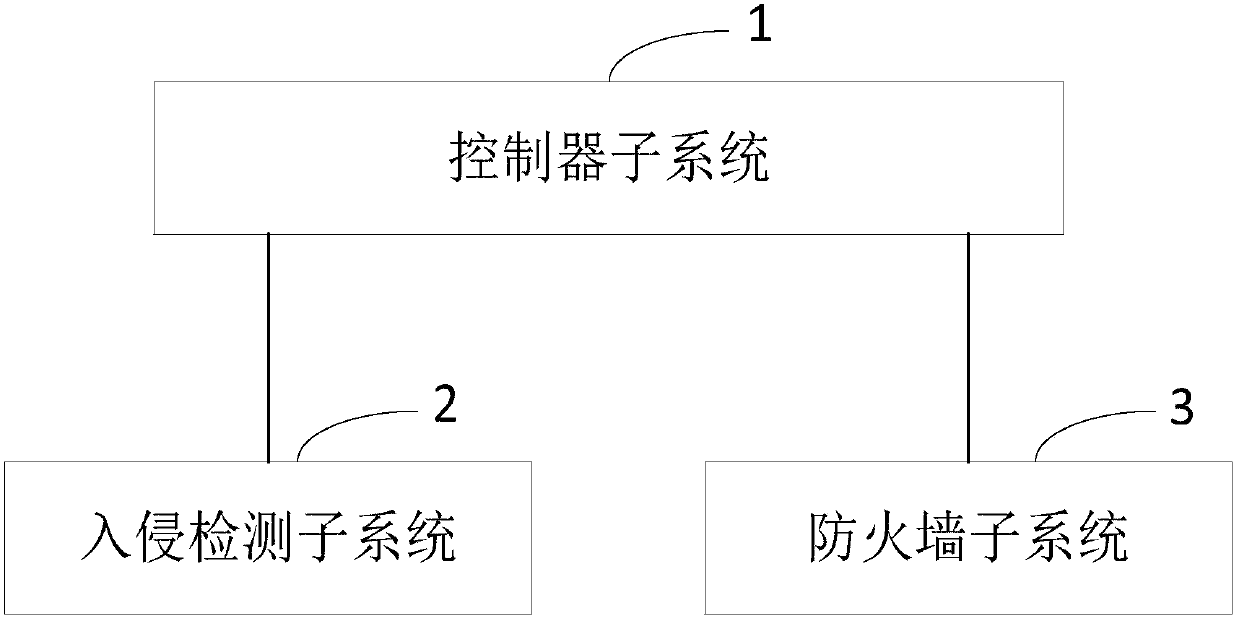
[0054] figure 1 It is a schematic diagram of the overall structure of a safety protection system according to an embodiment of the present invention, such as figure 1 As shown, the embodiment of the present invention provides a security protection system, which is characterized in that it includes a controller subsystem 1, an intrusion detection subsystem 2 and a firewall subsystem 3, wherein:
[0055] The controller subsystem 1 is configured to update the rules of the intrusion detection subsystem and the rules of the firewall subsystem according to the illegal data in the detection results reported by the intrusion detection subsystem 2, and update the rules of the intr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com