Safety automatic login management system
An automatic login and management system technology, which is applied in the field of safe automatic login management system, can solve the problems of account security leakage, account number memory is cumbersome, etc., and achieve the effect of improving security and preventing leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
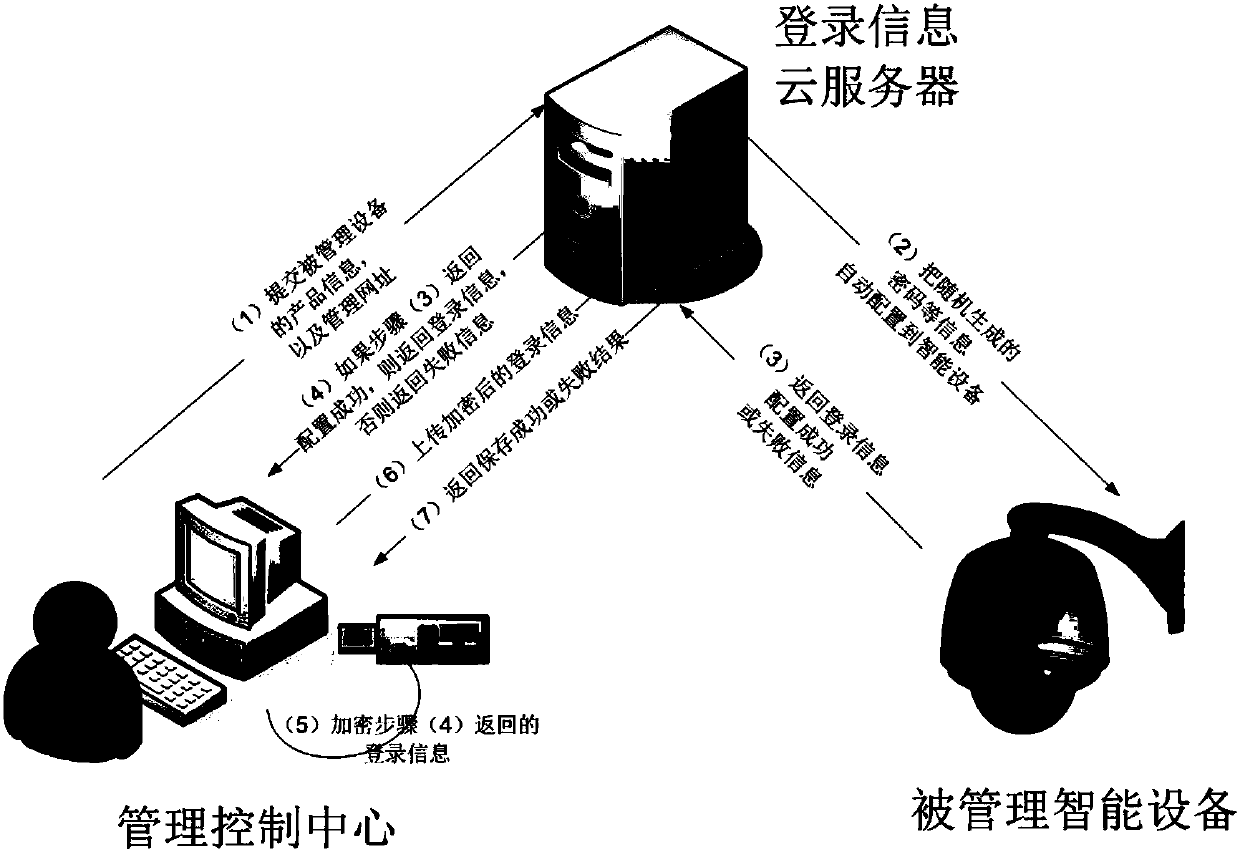
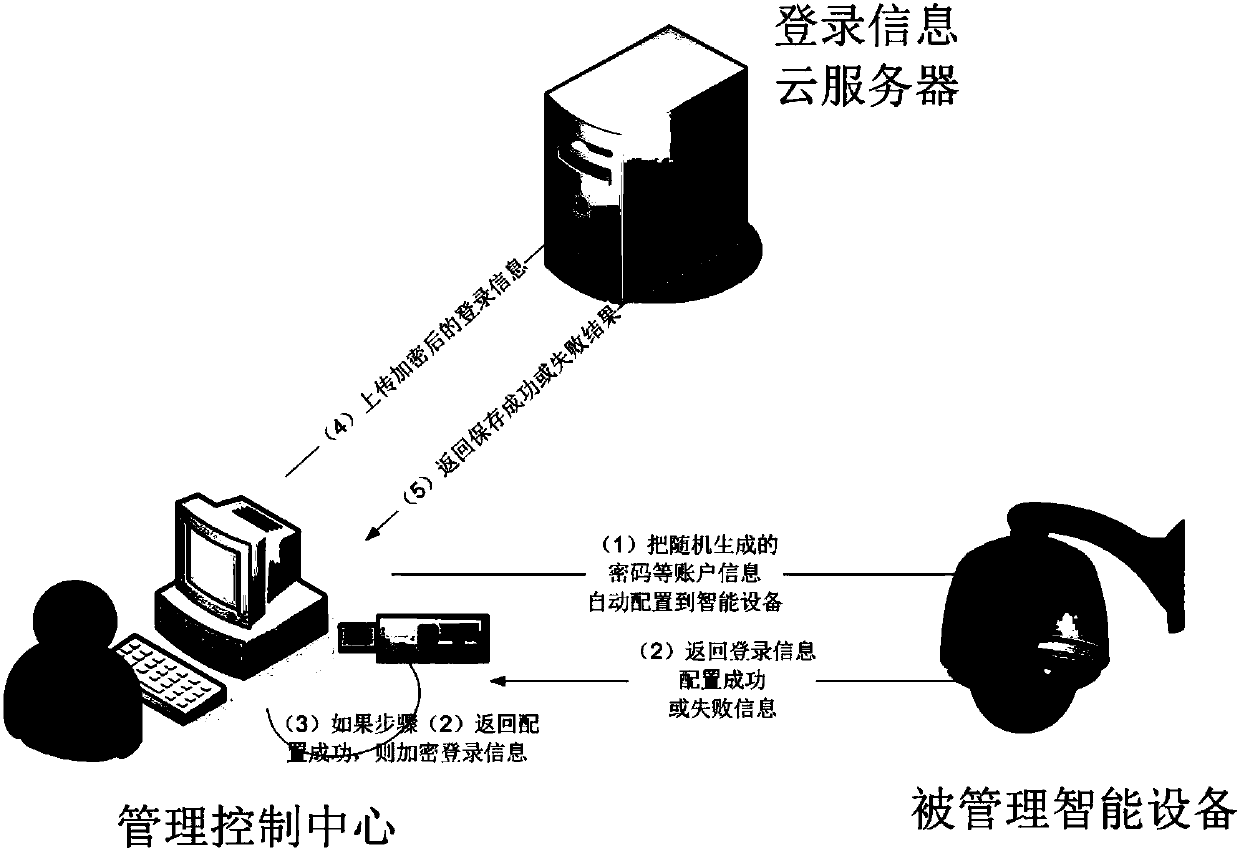
[0041] This embodiment takes Figure 1 to Figure 3 The application scenario shown (the computer inserted into the dedicated USB-Key is the management control center, and the smart camera is the managed smart device) is a specific example for further elaboration.
[0042] The specific implementation is as follows:
[0043] Step 1: Run the automatic login management system client on the computer (management control center) that inserts the exclusive USB-Key to generate a pair of public key and private key for the user, and save the private key in the USB-Key;
[0044] Step 2: The management control center is connected to the smart camera, and the current login password is changed to a randomly generated complex password;
[0045] Step 3: If step 2 fails, retry step 2, otherwise, encrypt the password and other login information randomly generated in step 2 with the public key generated in step 1, and upload the encrypted login information to the login information server;
[004...
Embodiment 2
[0049] By adopting the technical scheme of the present invention, secure and complex login information can be randomly generated for accounts or smart devices, and automatic login can be realized. In order to make the technical scheme of the present invention easier to understand, the following Figure 4 application scenarios (the mobile phone is the management control center, and the router is the managed smart device).
[0050] The specific implementation is as follows:
[0051] Step 1: Run the mobile phone to automatically log in to the management system APP, generate the public key and private key exclusive to the mobile phone, and save them in a password-protected local file;
[0052] Step 2: Scan the mobile phone to the router with the initial password through WIFI, log in to the router with the initial password, and change the current login password of the router to a randomly generated complex password;
[0053] Step 3. If step 2 fails, retry step 2. Otherwise, encry...
Embodiment 3
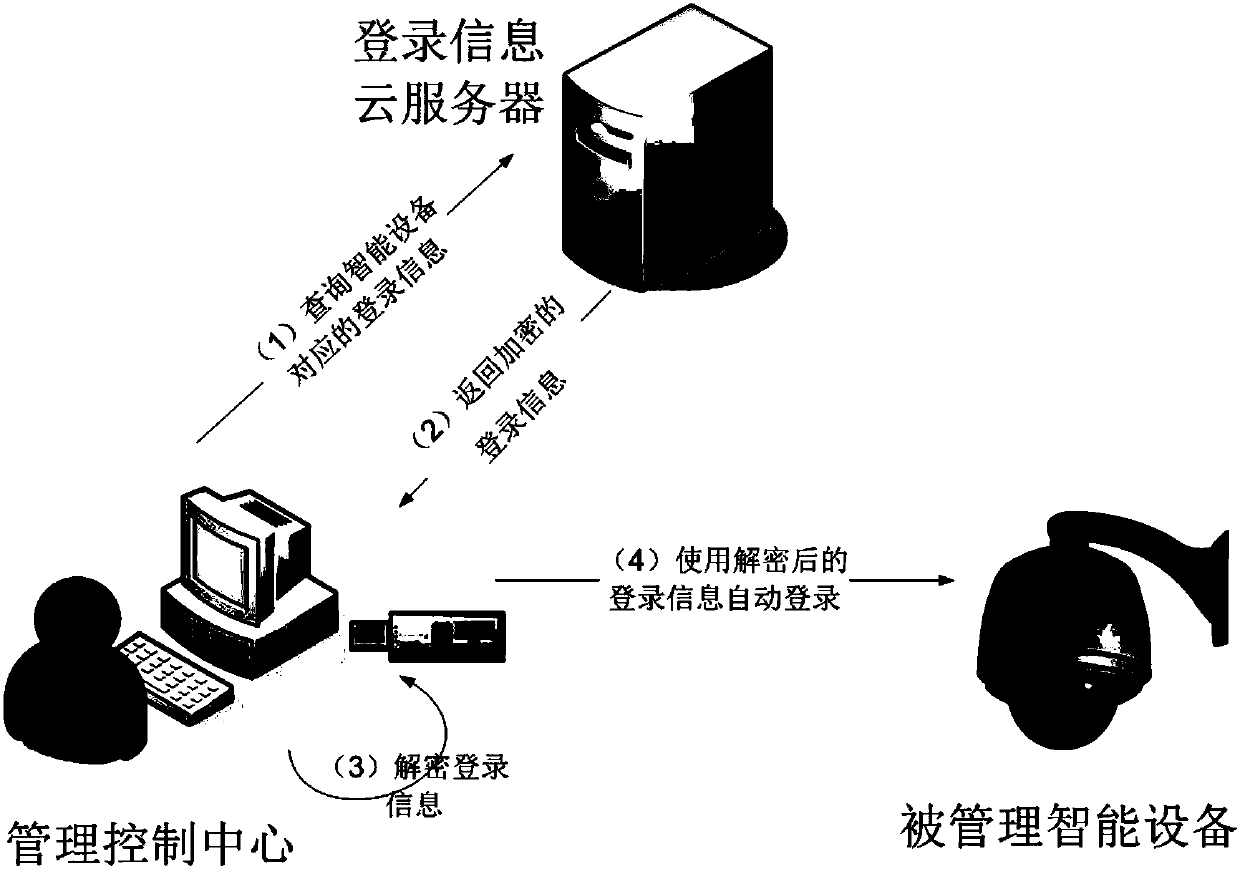
[0056] Below to Figure 5 to Figure 6 The application scenarios are further elaborated with specific examples.
[0057] Step 1: The user sends a request to the automatic login system to log in to a third-party application;
[0058] Step 2: The automatic login system decrypts the account information of the third-party application stored locally or in the cloud;
[0059] Step 3: The automatic login system evokes the third-party application, and transmits the decrypted account information to the third-party application. If the account information (such as password, etc.) needs to be updated, the current account information and the new account information can be transmitted to the third-party application at the same time. account information. In order to ensure the security of account information transmission, the information can be encrypted;
[0060] Step 4: After the third-party application is awakened, verify the current account information received. If the verification is ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com