Data processing method and system
A data processing and data technology, applied in the field of data security, can solve the problems of lack of ability, no stream processing design, lack of configuration expansion ability, etc., to achieve the effect of high configurability, advanced architecture and stable technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
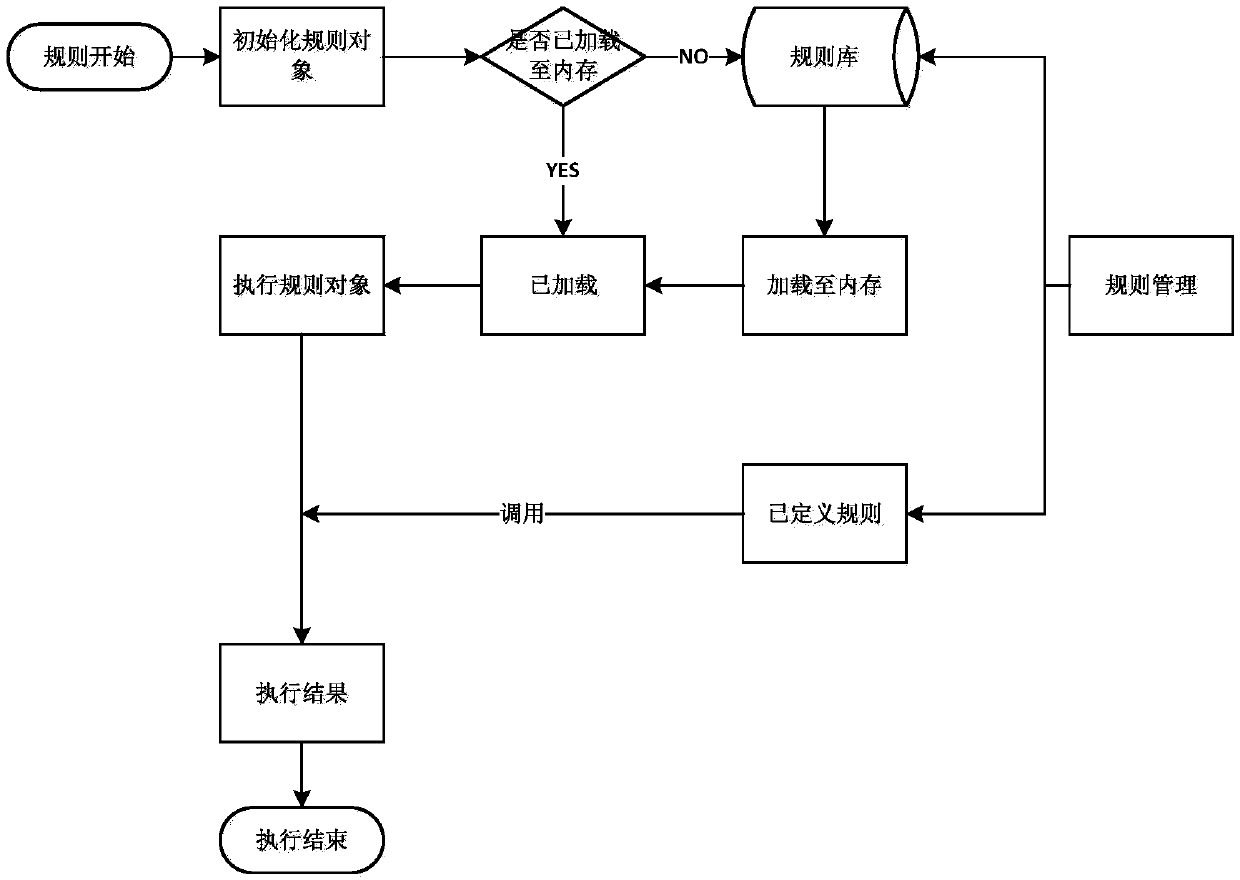
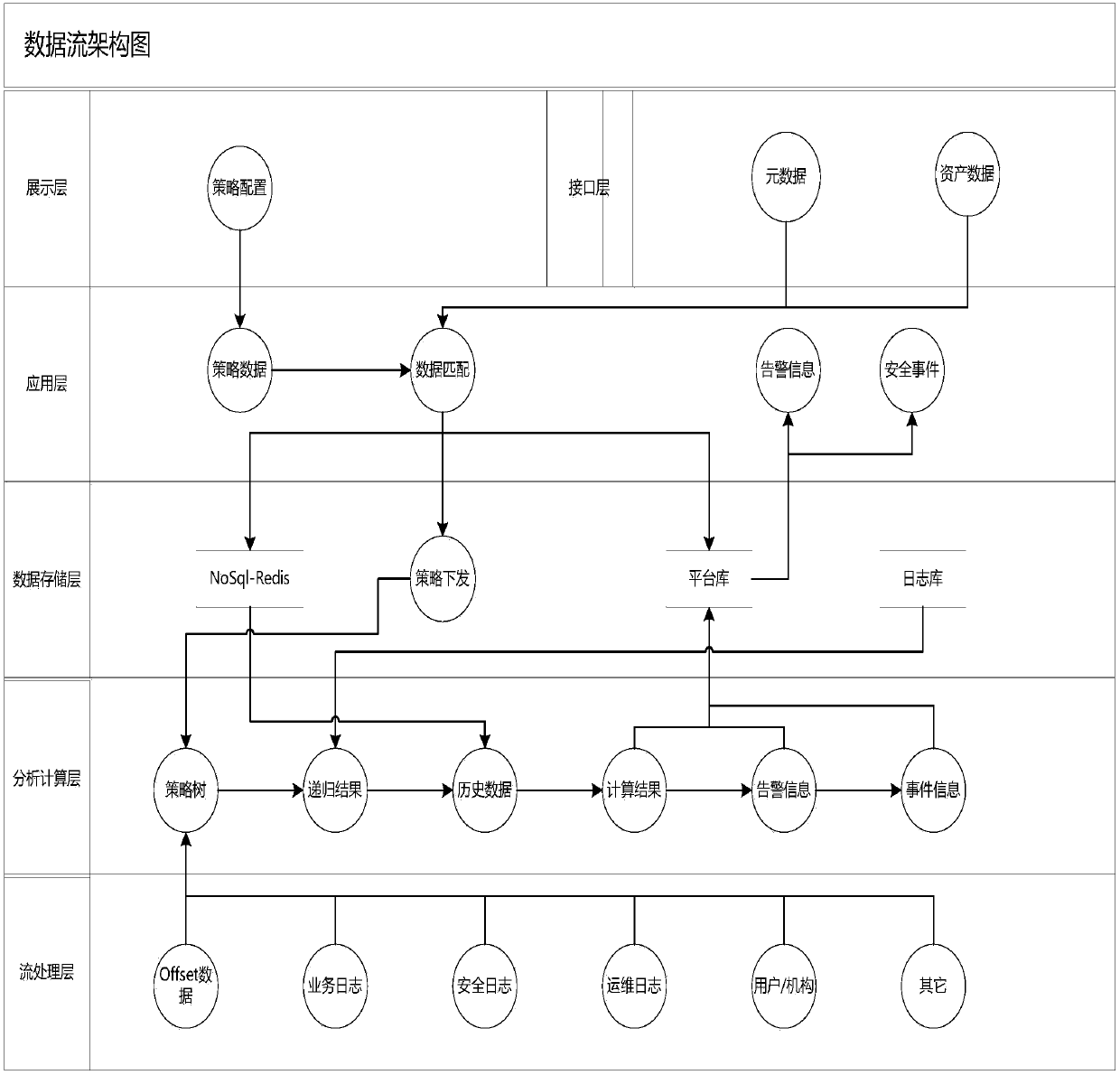
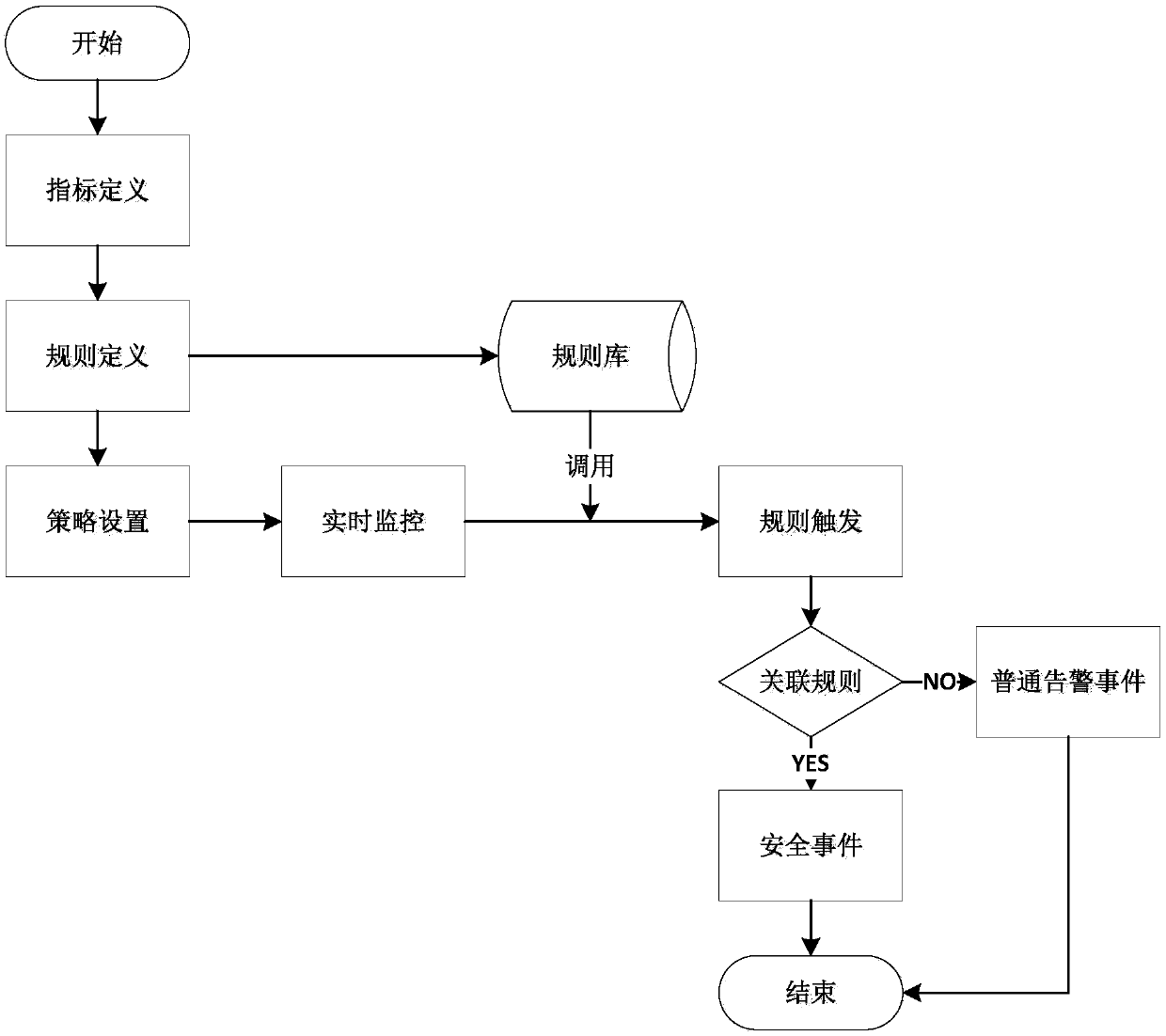
Image
Examples
Embodiment Construction
[0049] Kafka is a high-throughput distributed publish-subscribe messaging system that can handle all action streaming data in consumer-scale websites. Such actions (web browsing, searching and other user actions) are a key factor in many social functions on the modern web. These data are usually addressed by processing logs and log aggregation due to throughput requirements. This is a viable solution for systems like Hadoop that log data and analyze offline, but require real-time processing constraints. The purpose of Kafka is to unify online and offline message processing through Hadoop's parallel loading mechanism, and to provide real-time consumption through clusters.
[0050] Redis is an open-source, log-type, Key-Value database written in ANSI C language, supports network, can be memory-based or persistent, and provides APIs in multiple languages. Redis is a key-value storage system. Similar to Memcached, it supports relatively more value types for storage, including s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com