Method for detecting differential fault attack resisting capability of AES-OTR algorithm
A differential fault attack and algorithm technology, applied in the field of information security, can solve the problems of evaluating the ability of the AES-OTR algorithm to resist differential fault attacks, hidden dangers of product safety, etc., and achieve the effect of accurate, simple and easy-to-implement methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
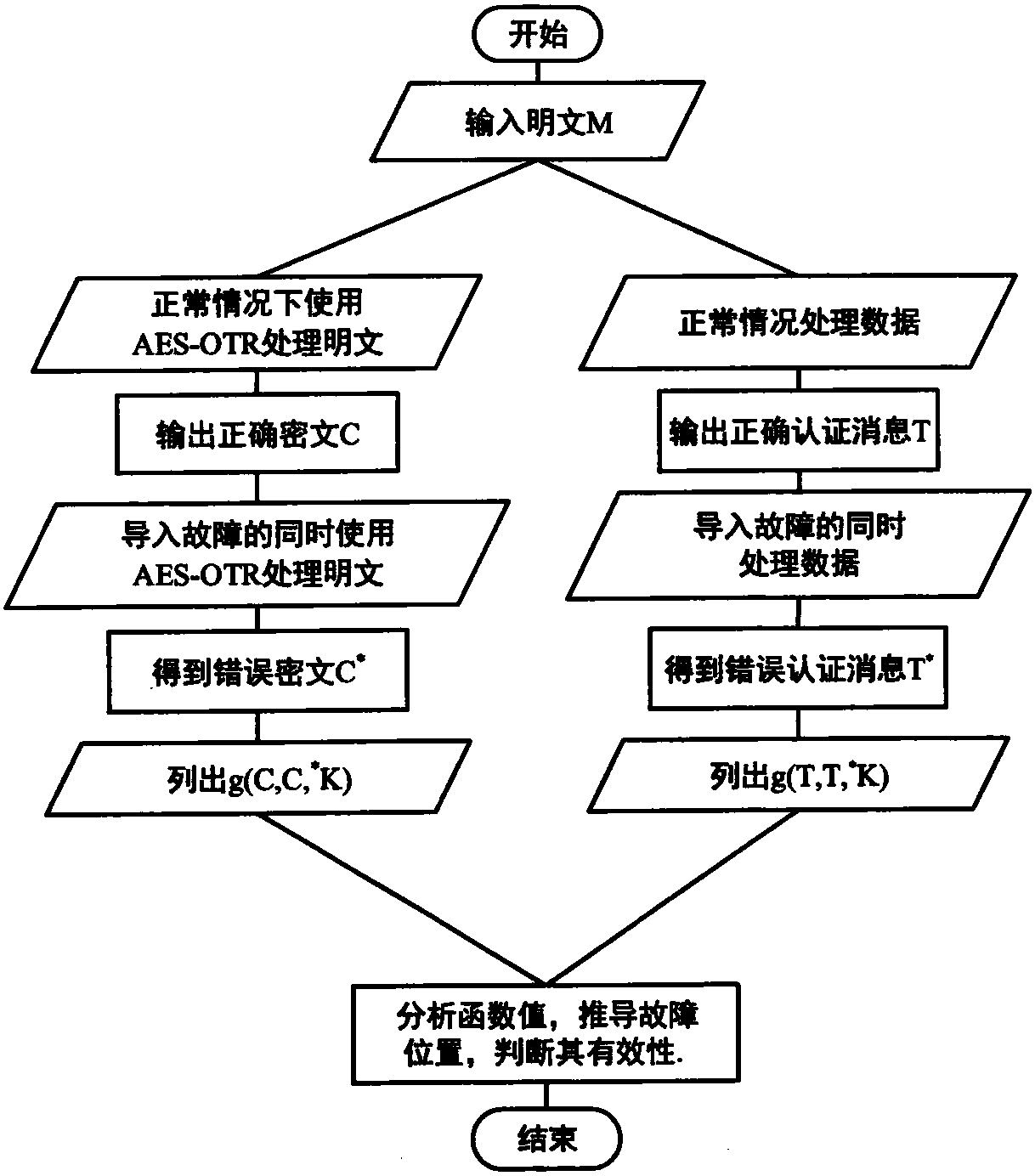
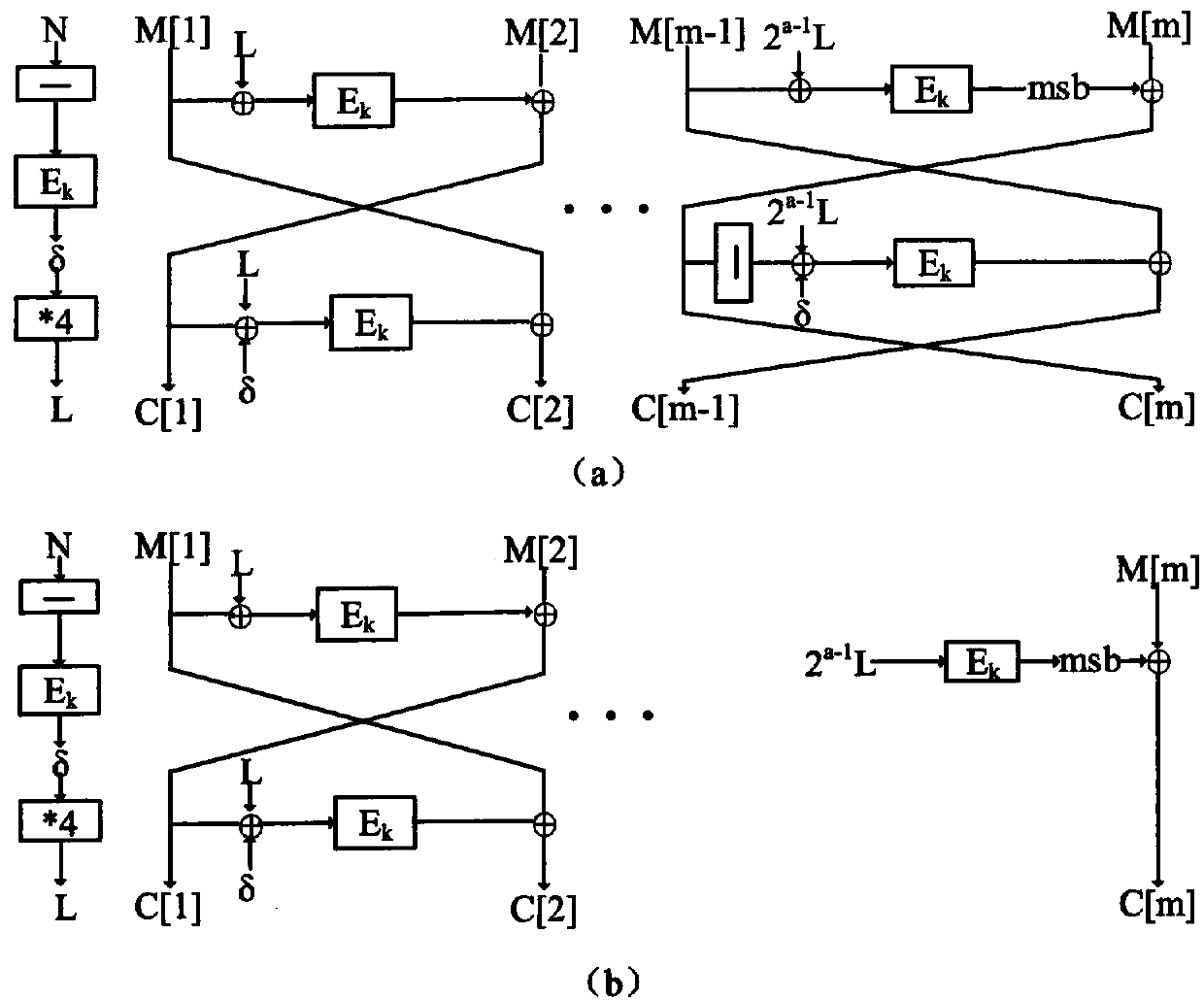
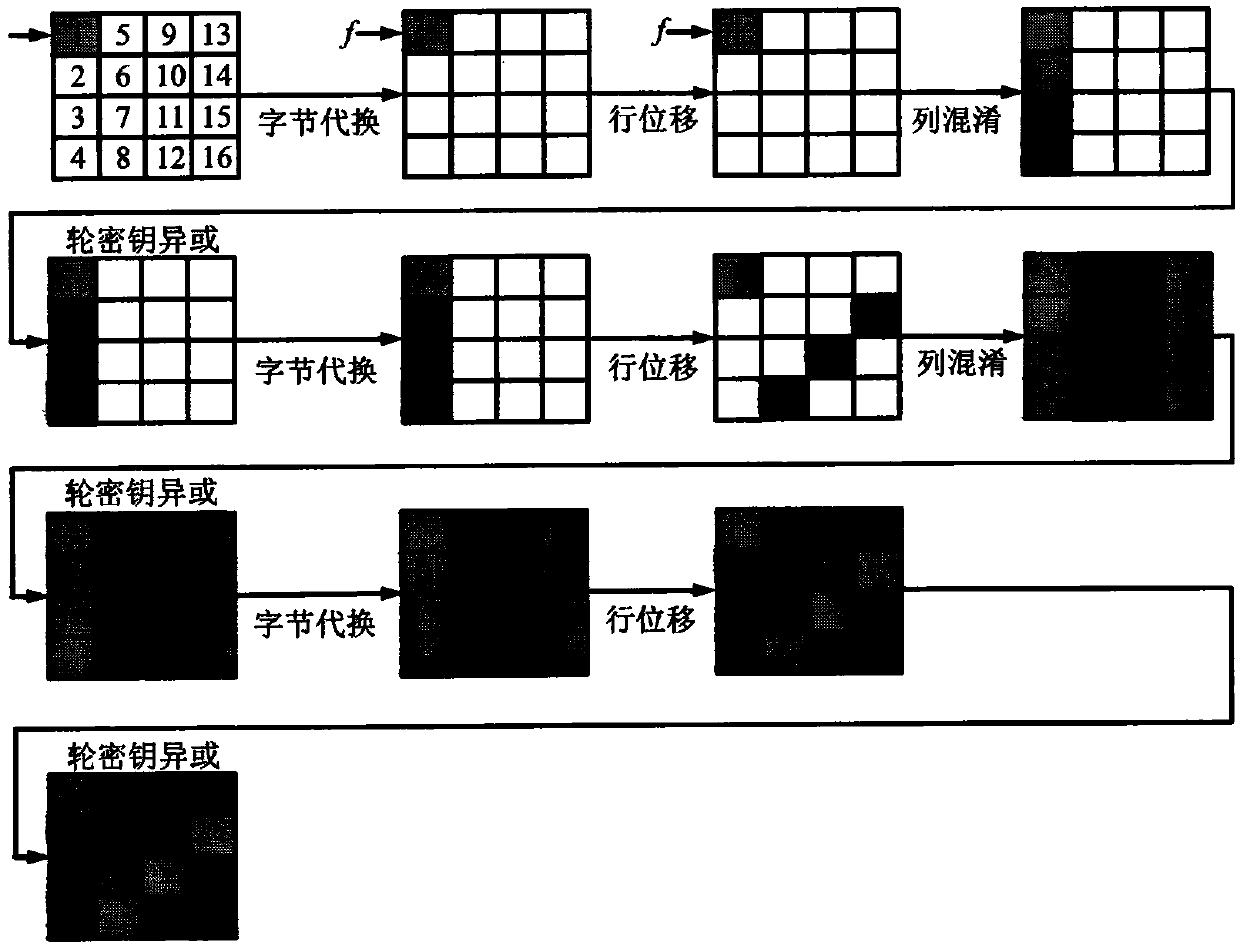
[0048] Below in conjunction with specific embodiment, further illustrate the present invention.
[0049] The symbols used in this embodiment are explained as follows:
[0050] M: plaintext message;
[0051] m: the number of blocks of plaintext or ciphertext;
[0052] M[p]: the pth group of plaintext, where 1≤p≤m;
[0053] C[q]: the pth block of the ciphertext, where 1≤q≤m;
[0054] C i , ΔC i : The i-th byte of the ciphertext, and the fault difference of the i-th byte, where 1≤i≤16;
[0055] K: original key; K i : The i-th byte of the key, where 1≤i≤16;
[0056] : Indicates that the tenth round of the algorithm’s S-box inputs the i-th index value, 1≤i≤16,
[0057] F: Indicates the difference ratio corresponding to the input index value of the tenth round of the S-box of the algorithm
[0058] C: The correct output after the algorithm processes the message;
[0059] C * : When the algorithm processes the message, the error output generated after importing the fault...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com