Password misuse vulnerability detection method and system based on Petri net
A vulnerability detection and password technology, applied in the field of network information security, can solve the problems of analysis, direct conclusions, difficult batch samples, etc., achieve good versatility and scalability, improve detection efficiency, and high recognition rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
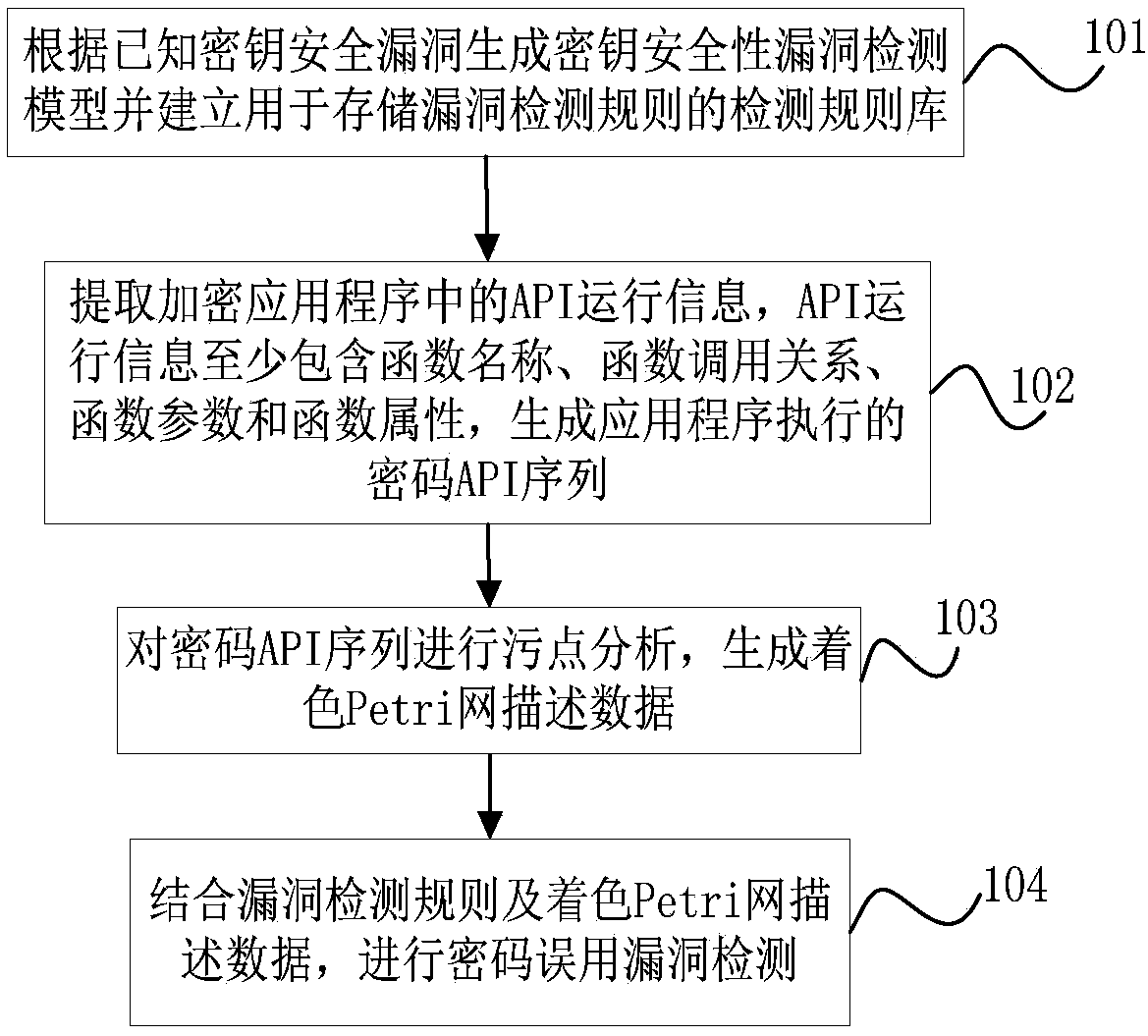
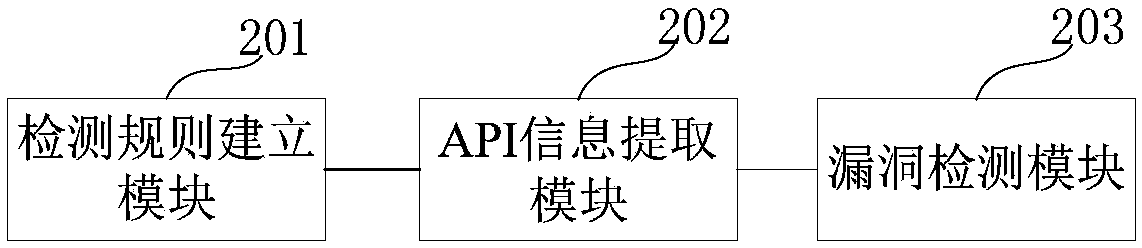
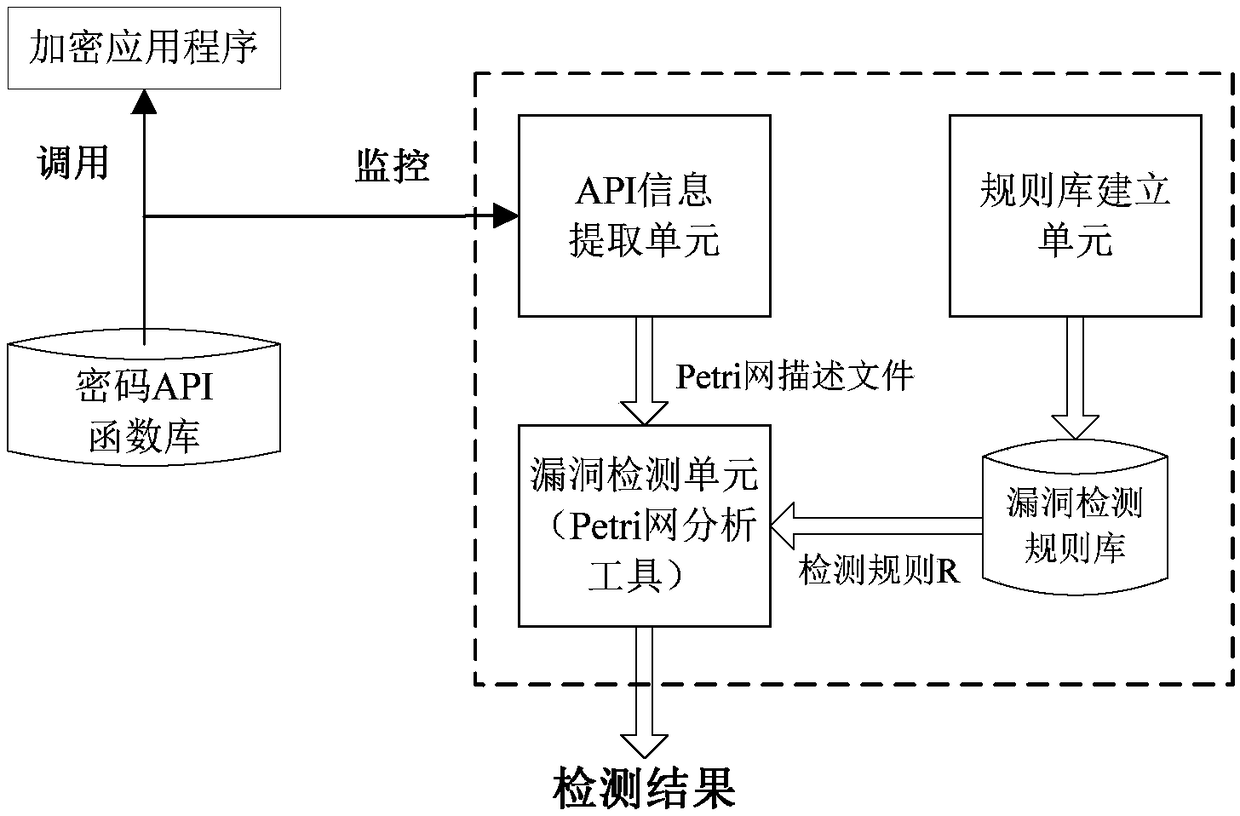
[0032] In order to make the purpose, technical solution and advantages of the present invention more clear and understandable, the present invention will be further described in detail below in conjunction with the accompanying drawings and technical solutions.
[0033] In view of the fact that the reverse analysis method in the prior art cannot provide direct conclusions about vulnerability detection, it needs to manually analyze the reverse results of each target sample and finally draw a conclusion. The correctness of the conclusion depends heavily on the skills and experience of the analyst , and it takes a lot of time and energy, it is difficult to analyze batch samples; and in the vulnerability mining method, because the general method of software vulnerability mining usually seldom considers the unique rules and characteristics of cryptography vulnerabilities, so in the case of password misuse vulnerabilities The detection aspect lacks pertinence, and the effect is often...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com