Verification method and device
A verification method and user verification technology, applied in the field of verification methods and devices, can solve the problems of distortion, cracking, and trouble of numbers and letters, and achieve the effect of avoiding the possibility of verification, preventing malicious program attacks, and improving user experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
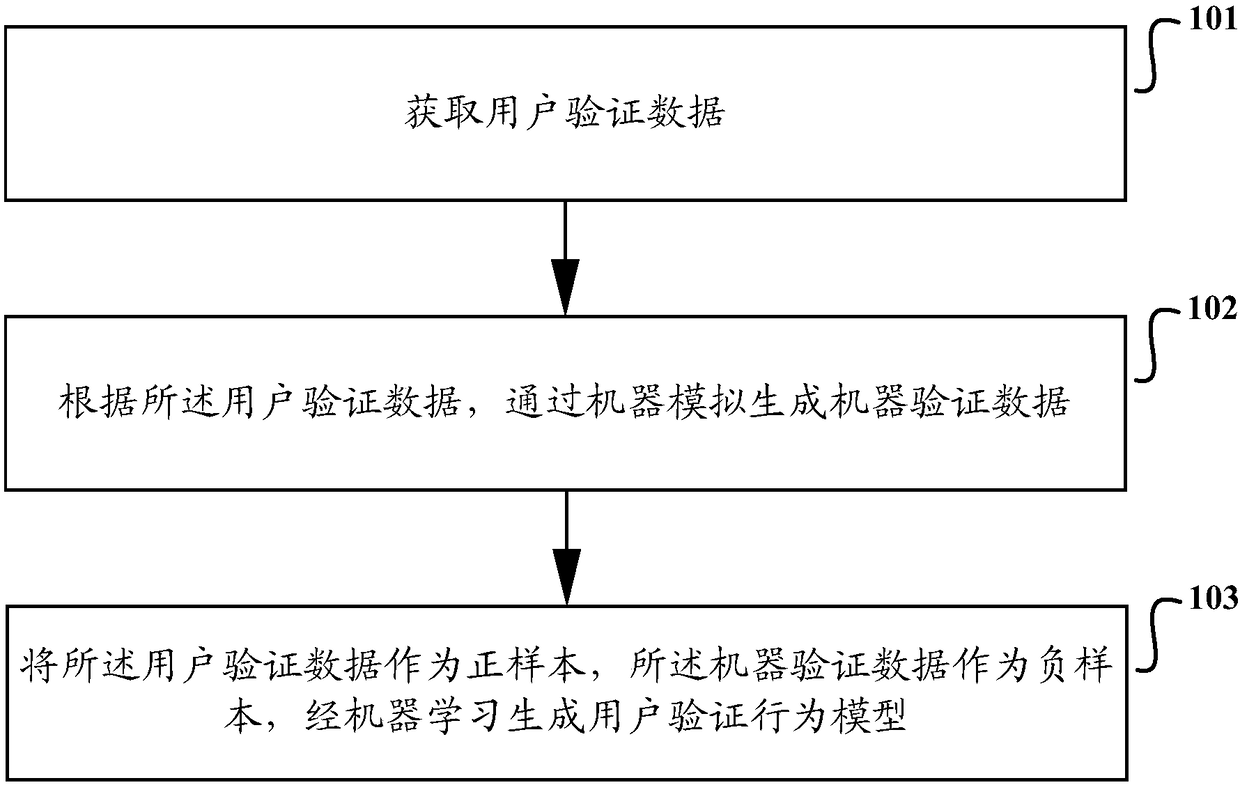
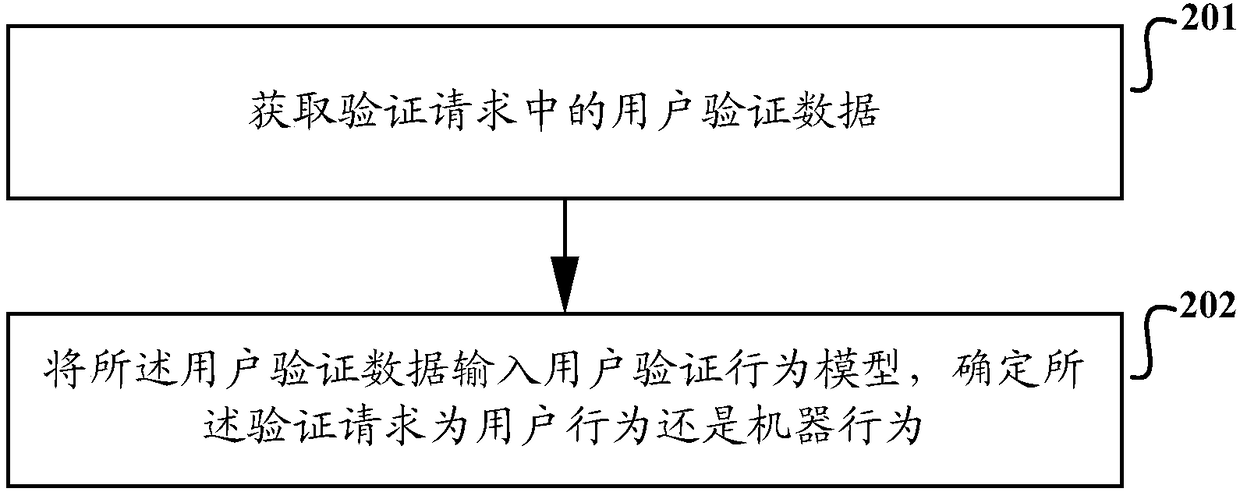
[0059] The specific implementation manners of the verification method, device and server based on the verification picture provided in the embodiment of the present application will be described in detail below with reference to the accompanying drawings.
[0060] At present, the commonly used human-computer identification method is the Turing Test (Completely Automated Public Turing Test to Tell Computers and Humans Apart, CAPTCHA), which is fully automated to distinguish between computers and humans, and its manifestations are character verification codes, SMS verification codes, and voice verification codes.
[0061] The character verification code completes the verification by requiring the user to input the text in the picture. The manifestations include: multiple English characters, adding interference lines or noise points in the background, and the characters are processed by sticking and distorting, which increases the difficulty of cracking; the simple calculation form...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com