A Routing Protocol Strengthening Method Based on Trusted Cipher Card
A routing protocol and password card technology, applied in the field of routing protocol reinforcement, can solve problems such as complicated methods and increased network maintenance costs, and achieve the effects of preventing theft and tampering, avoiding the risk of key theft, and ensuring confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
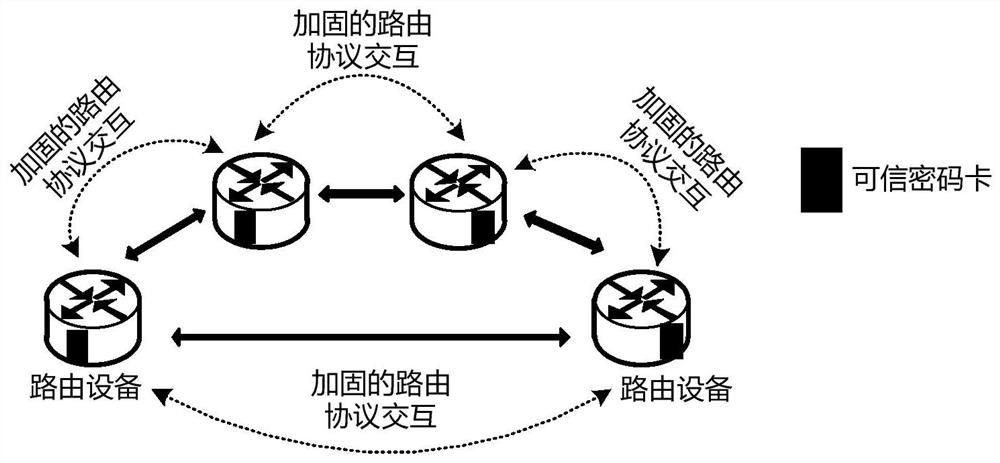
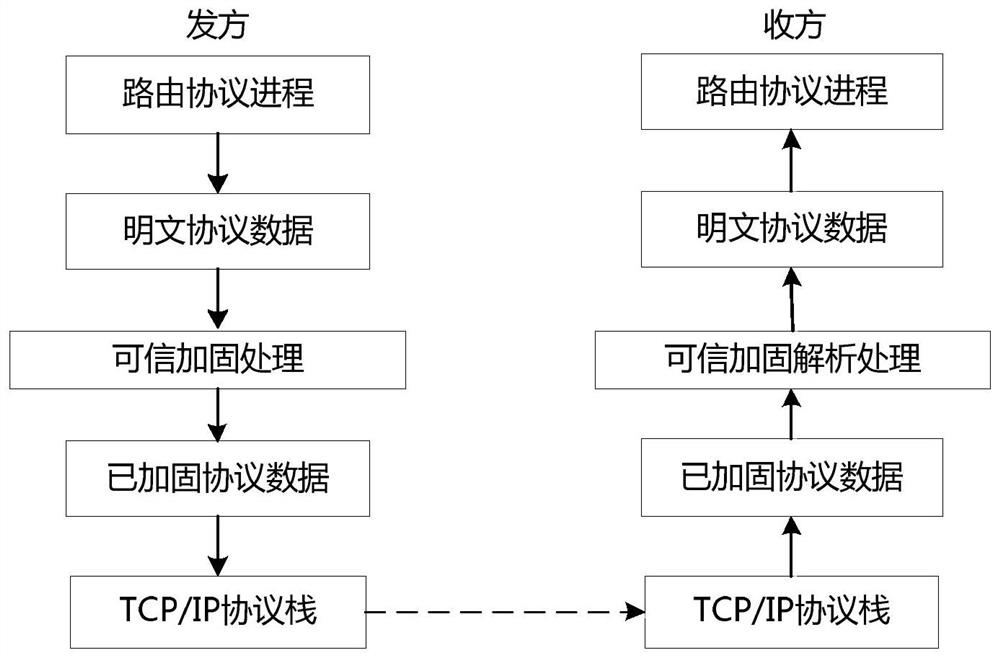
[0047] The invention proposes that the routing equipment in the communication network integrates a trusted cipher card, uses the trusted cipher card as a built-in trusted root, and combines services such as trusted measurement, safe storage, integrity verification, and data encryption and decryption provided by the trusted cryptography module to realize End-to-end entity identity authentication and secure transmission and control of protocol messages between routing devices, realizing functions such as routing protocol data source verification, anti-replay, protocol data integrity verification, and confidentiality protection. Network nodes dynamically maintain the reliability of neighbors. Reliability, relying on the credible recognition rate to dynamically adjust routing to ensure high security and high reliability of the entire communication network. The network diagram is asfigure 1 shown.
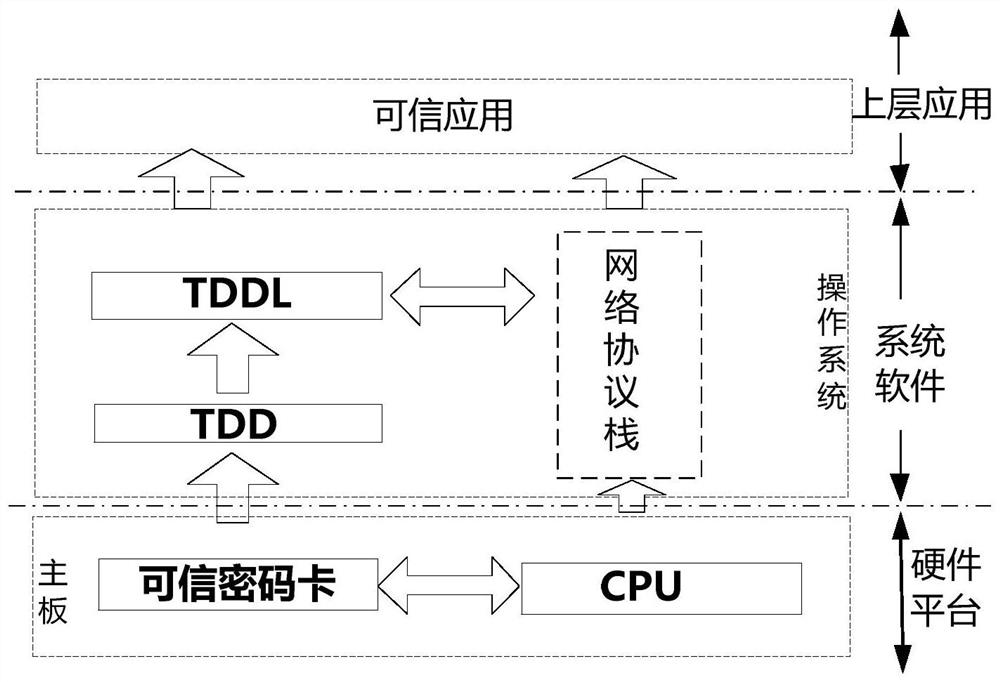
[0048] The function realization of the trusted cryptographic card is composed of tw...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com