Proactive defense system based on truth virtual network, and method
A virtual network and active defense technology, applied in the field of network security, can solve problems such as potential safety hazards, difficulty in accurately identifying attackers' attack paths, complex internal processes, etc., and achieve the effect of reducing the burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
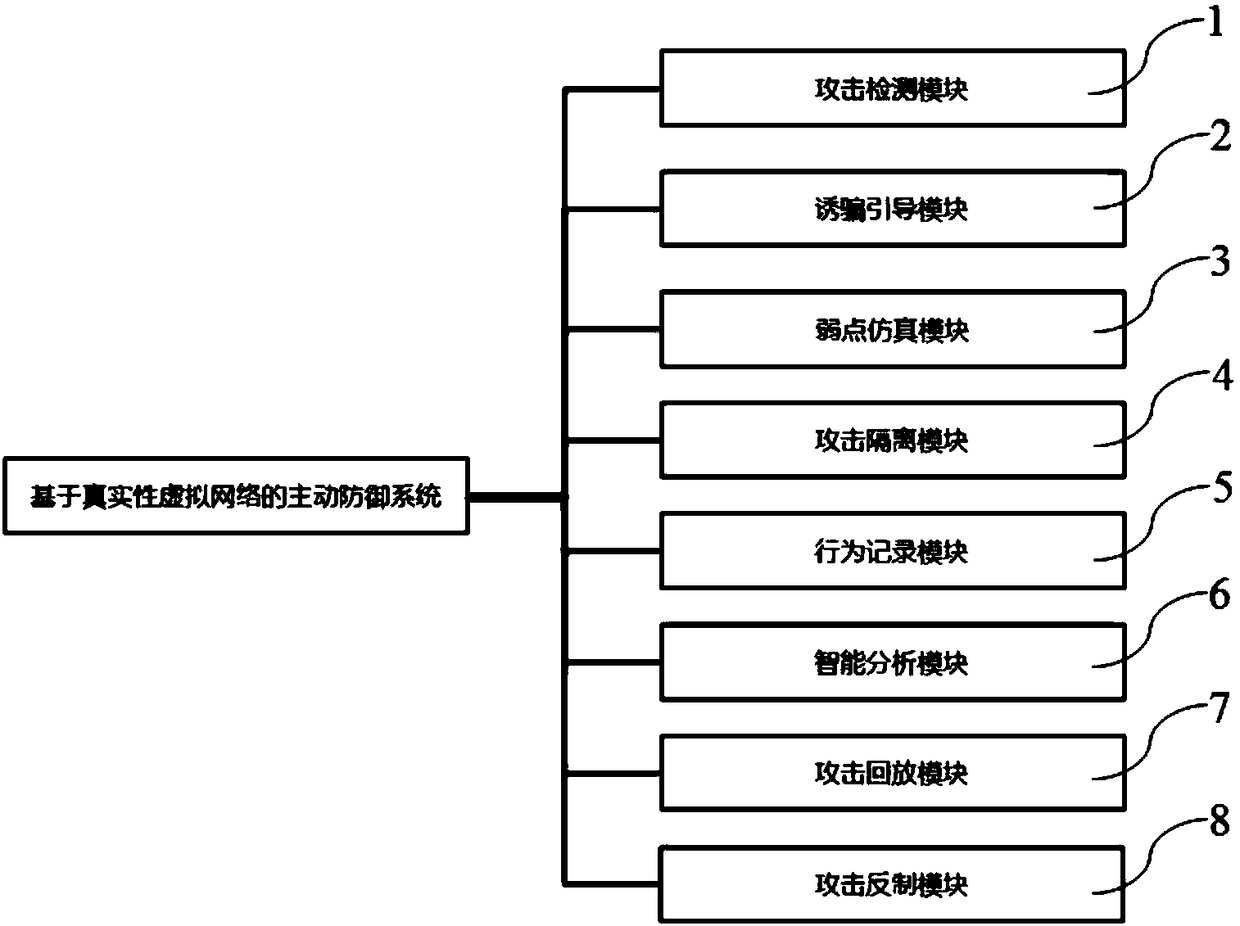
[0044] Such as figure 1 , an active defense system based on an authentic virtual network, including the following modules that communicate with each other in a signal loop:
[0045] Attack detection module 1, used to detect various types of attack behaviors, and achieve real-time alarm;
[0046] Decoy guidance module 2, used to trick attackers into continuously attacking false targets in the system;
[0047] Vulnerability simulation module 3, through the use of real virtual hosts and networks to build a real vulnerability system, attracting attackers to successfully attack;
[0048] Attack isolation module 4, the attacker is completely isolated from the real environment in the authentic virtual network of the system, and the authentic virtual network of the system will not become a springboard for the attacker;
[0049] Behavior recording module 5, which is used to comprehensively record various attack behaviors of attackers;
[0050] The intelligent analysis module 6 is us...
Embodiment 2
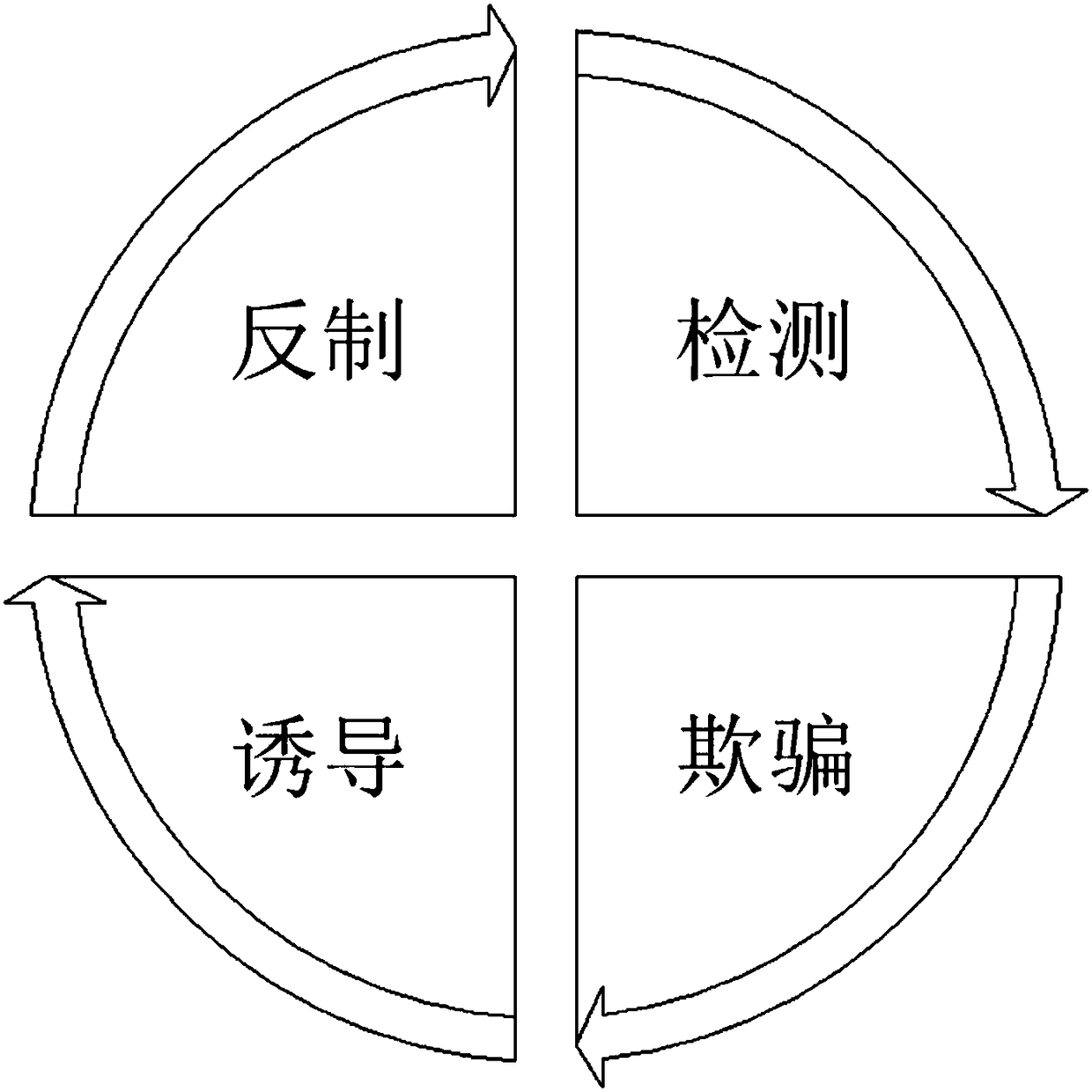
[0054] Such as figure 1 and figure 2 , an active defense system based on an authentic virtual network, including the following modules that communicate with each other in a signal cycle:
[0055] Attack detection module 1, used to detect various types of attack behaviors, and achieve real-time alarm;
[0056] Decoy guidance module 2, used to trick attackers into continuously attacking false targets in the system;
[0057] Vulnerability simulation module 3, through the use of real virtual hosts and networks to build a real vulnerability system, attracting attackers to successfully attack;
[0058] Attack isolation module 4, the attacker is completely isolated from the real environment in the authentic virtual network of the system, and the authentic virtual network of the system will not become a springboard for the attacker;
[0059] Behavior recording module 5, which is used to comprehensively record various attack behaviors of attackers;
[0060] The intelligent analysi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com