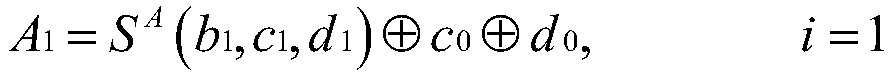Novel method for password S box threshold implementation without random numbers
A technology of random numbers and new methods, applied in the field of information security, can solve problems such as high resource overhead and security risks, and achieve the effects of satisfying uniformity, improving security, and reducing hardware resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
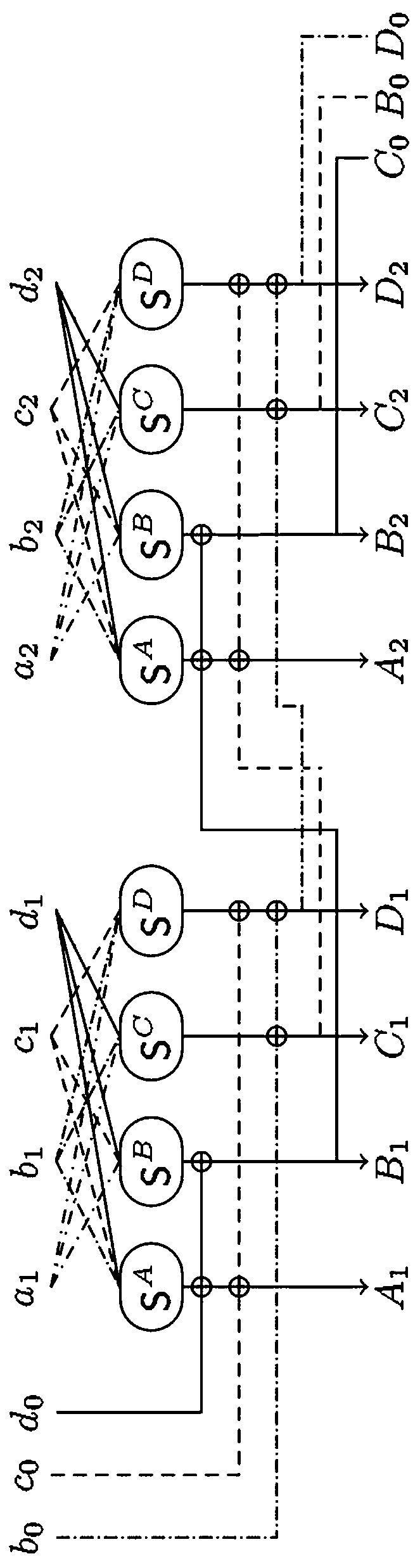
[0026] refer to figure 1 , taking four sharing factors and two parallel S-boxes as an example, but this embodiment is not limited to this S-box.
[0027] A new method for implementing a cryptographic S-box without a random number threshold, including the following steps:
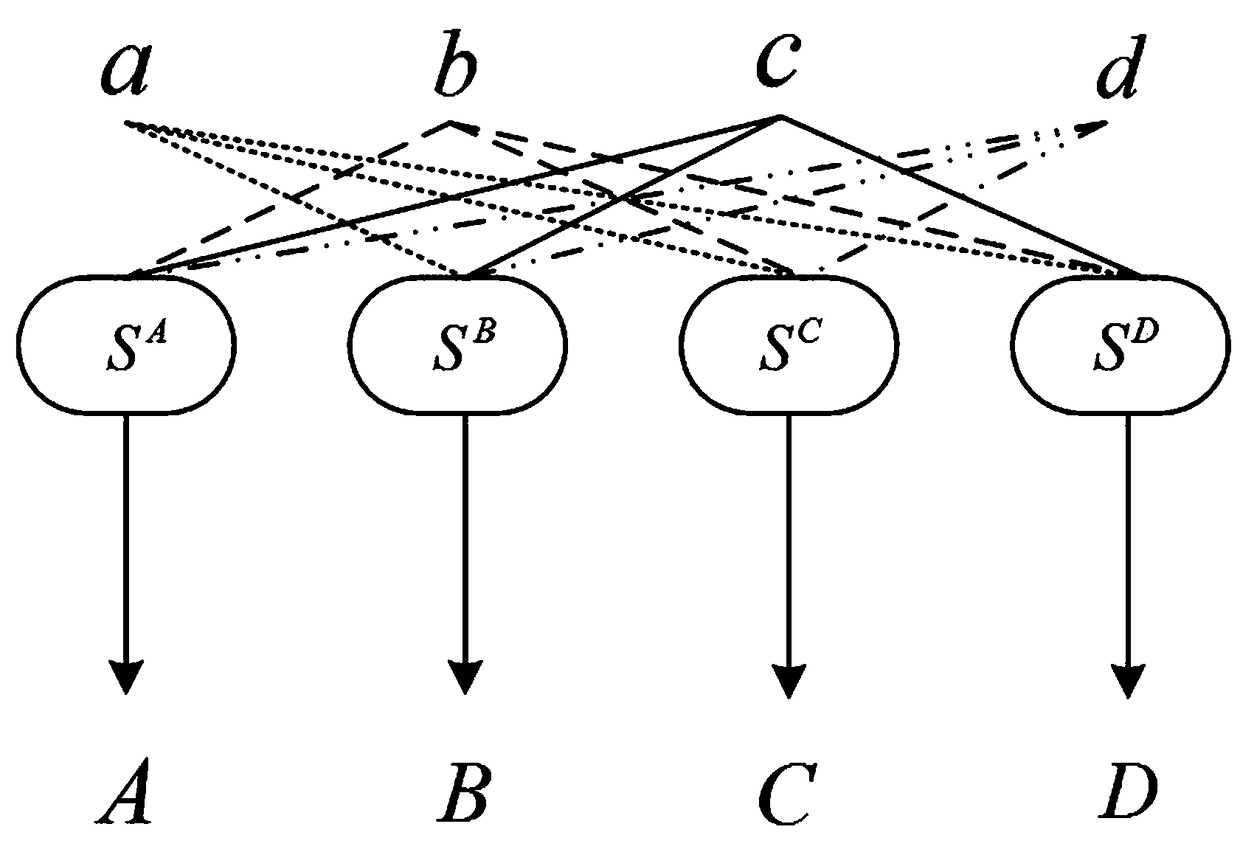
[0028] 1) First set (S A ,S B ,S C ,S D ) is the non-uniform threshold realization function of four shared factor bijective S-boxes, that is, the S-box at this time can be expressed as S=S A +S B +S C +S D , obviously, satisfies the correctness of the threshold implementation.
[0029] 2) Further, let the entire nonlinear layer consist of two identical S-boxes executed in parallel, and the input mask component of the first S-box is (a 1 ,b 1 ,c 1 , d 1 ), the input mask component of the second S-box is (a 2 ,b 2 ,c 2 , d 2 ). At this time, in order to satisfy the first-order incompleteness of threshold realization, the input mask component of each sub-masking function is 3. Taking the first ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com