A verification code identification input method and system based on sliding verification
An input method and input system technology, applied in the Internet field, can solve problems such as single sliding track, cumbersome and complicated operation, and low efficiency, and achieve the effect of solving the blocking effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
[0062] As an implementation manner of the present invention, the vertical size pixel threshold is 20, and the number threshold is 5.
[0063] Described method also comprises, 1, whether the mouse track of verification simulation is verified successfully, if verification " success " will success signal notification service end; Otherwise " failure " will click " retry " and the track notification service end record of failure.
[0064] A verification code identification input system based on sliding verification, which facilitates the realization of the above verification code identification input method, and is characterized in that it includes,
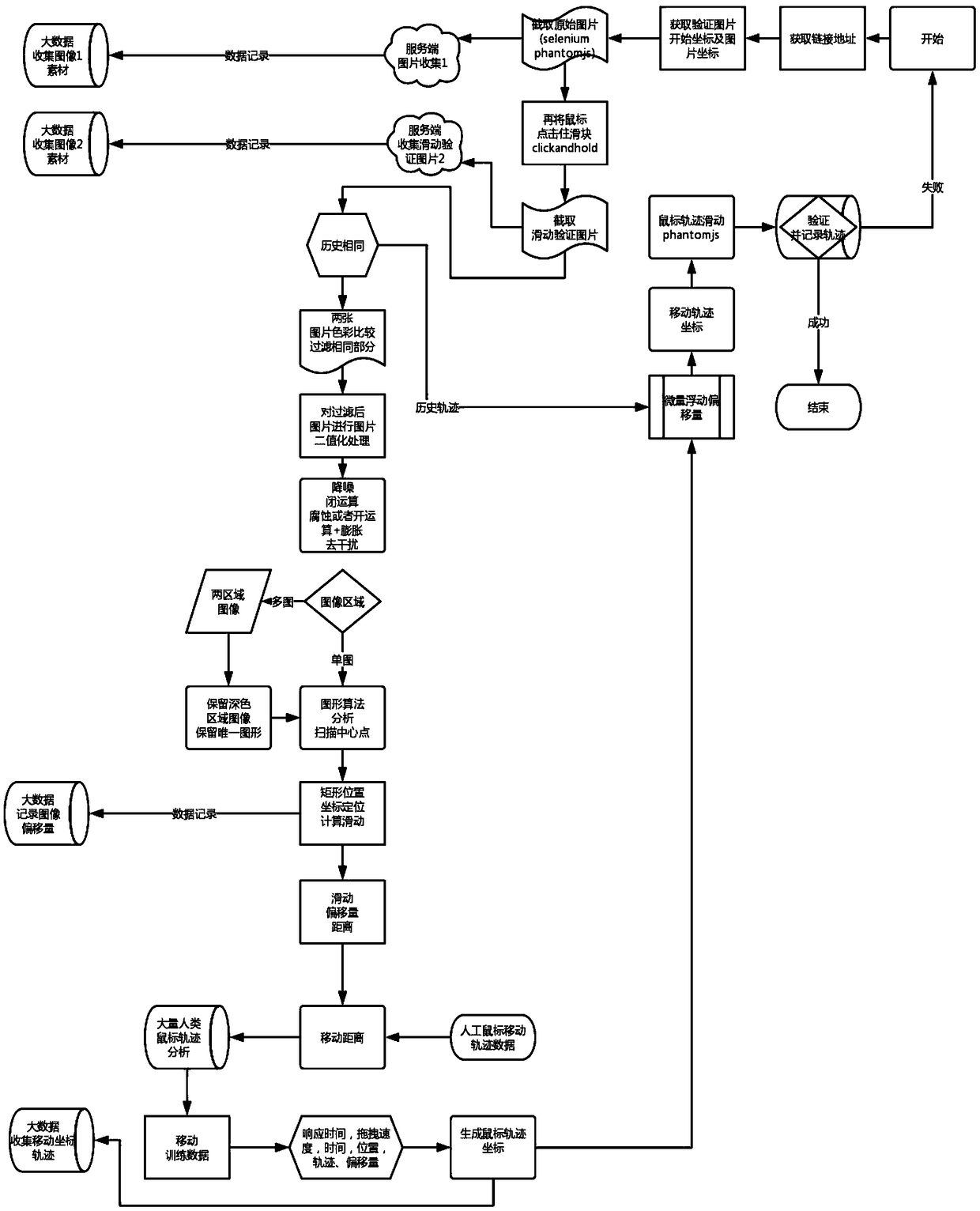
[0065] Image 1 acquisition module, find the position of the puzzle, and obtain the original image through the screenshot function of selenium+phantomjs, that is, image 1; collect image materials, and record the type of image;
[0066] Picture 2 acquisition module, automatically recognizes and controls the mouse cursor to click on the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com