Extended access control method based on traffic statistics
A technology for traffic statistics and access control, applied in the field of network security, it can solve the problems of limited matching rules, reduced device security, and insufficient flexibility, so as to improve performance and security, refine classification, and improve flexibility. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
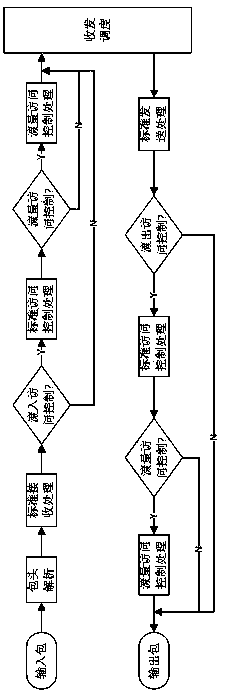
[0032] An extended access control method based on traffic statistics in this embodiment includes the following steps:
[0033] 1. When the data packet flows through a certain port of the network device, the standard second and third layer processing is first performed on the data packet;
[0034] 2. Determine whether the port has enabled the access control function, if enabled, go to step 3, otherwise go directly to step 7;
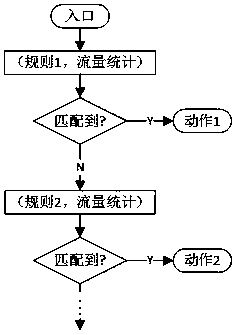
[0035] 3. Perform ACL rule matching on the data packet, if it matches, go to step 4, otherwise, repeat step 3, and continue to match the next rule;
[0036] 4. Determine whether the user has enabled access control based on traffic statistics, if enabled, go to step 5, otherwise go to step 6;
[0037] 5. Calculate the traffic statistics that match the ACL rules, including total traffic or average traffic, byte or packet-based traffic statistics, and continue to match with user configurations. If matched, perform corresponding actions and go to step 7, oth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com