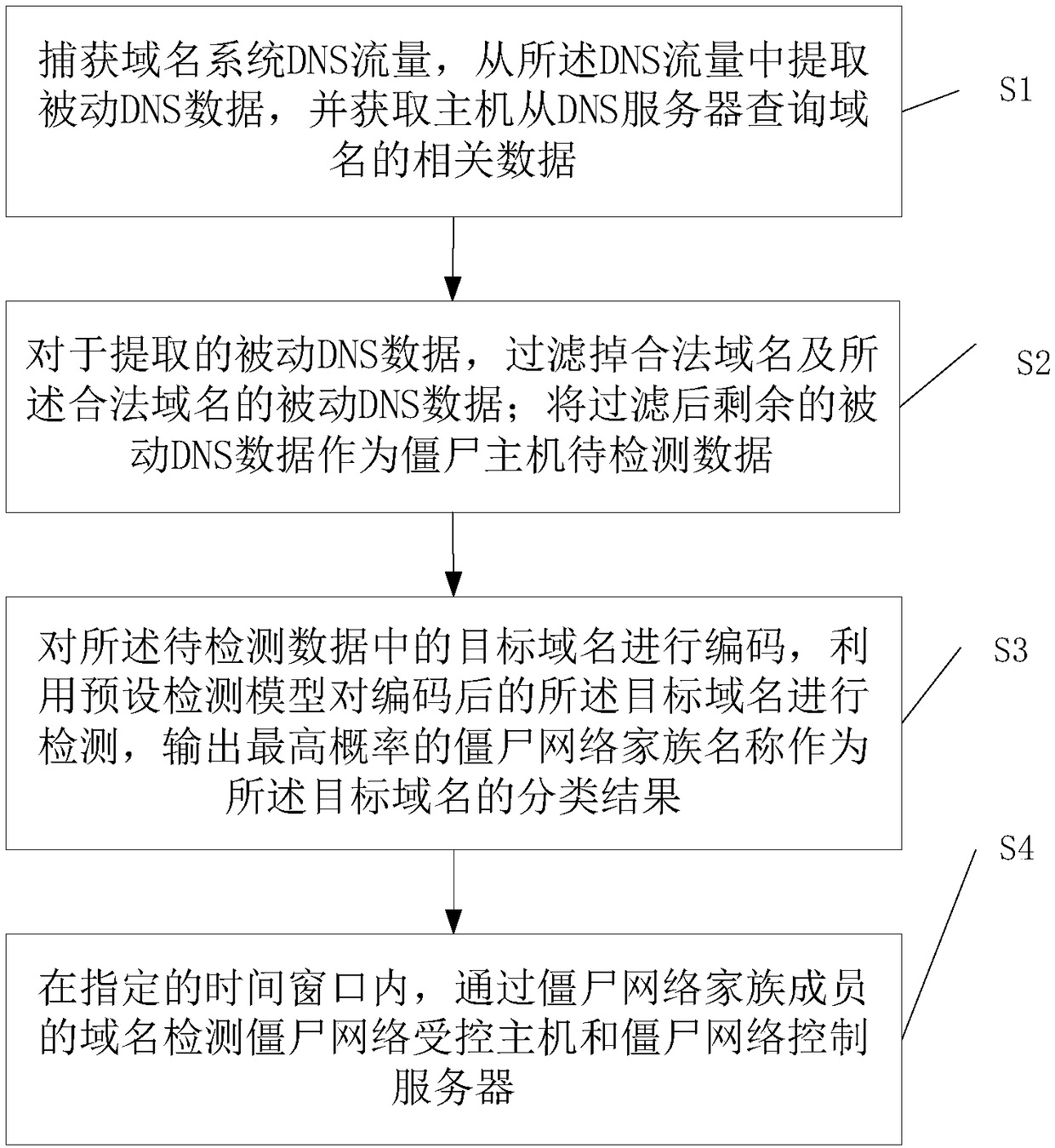
Botnet host detection method
A detection method and zombie host technology, which is applied in the field of zombie host detection, can solve the problems of large multi-classification models, difficulty in guaranteeing false positive rate and false negative rate, and difficult to achieve product-level application, so as to solve the difficulty of extraction and selection , low resource usage, and excellent detection capabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
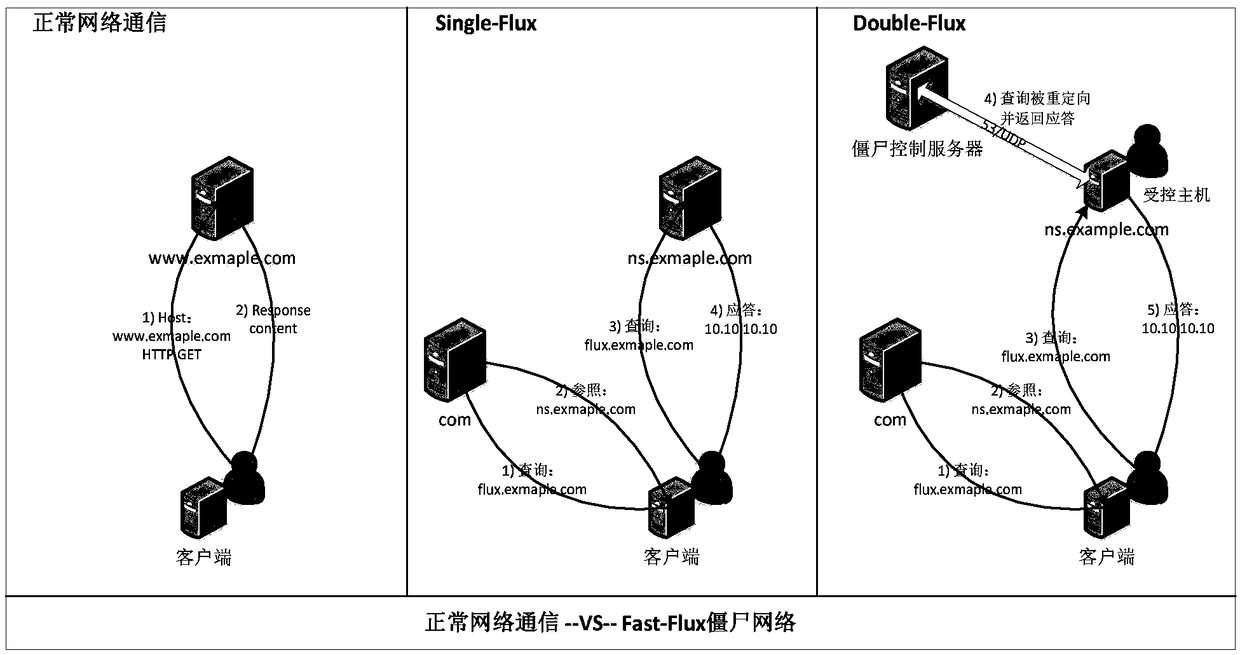
[0215] image 3 It is a schematic diagram of a Botnet structure based on the Fast-Flux technology provided by the embodiment of the present invention. Such as image 3 As shown, the difference between normal network communication and Fast-Flux botnet communication is obvious, and Fast-Flux botnet can be further divided into Single-Flux botnet and Double-Flux botnet.
[0216] For normal network communication, the client initiates a request to the web server, and the web server returns the request content;
[0217]For the Single-Flux botnet, the client needs to resolve the domain name address http: / / flux.example.com. First, query the top-level domain name DNS resolution server ".com", and receive a recommended recursive authoritative server "ns.example.com". Then, the client queries the authoritative DNS server to obtain the real IP address of the domain name. Finally, the client communicates directly with that IP address. For general DNS queries, the IP address remains unc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com