A system interaction method based on a trusted computing platform with a double-system structure
A technology of trusted computing and architecture, applied in the field of trusted computing, can solve the problems of being unable to play and prevent the Wannacry ransomware attack, and achieve the effect of improving security performance, facilitating active measurement and active control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0094] A system interaction method based on a dual-architecture trusted computing platform provided by the present invention will be described in detail below.
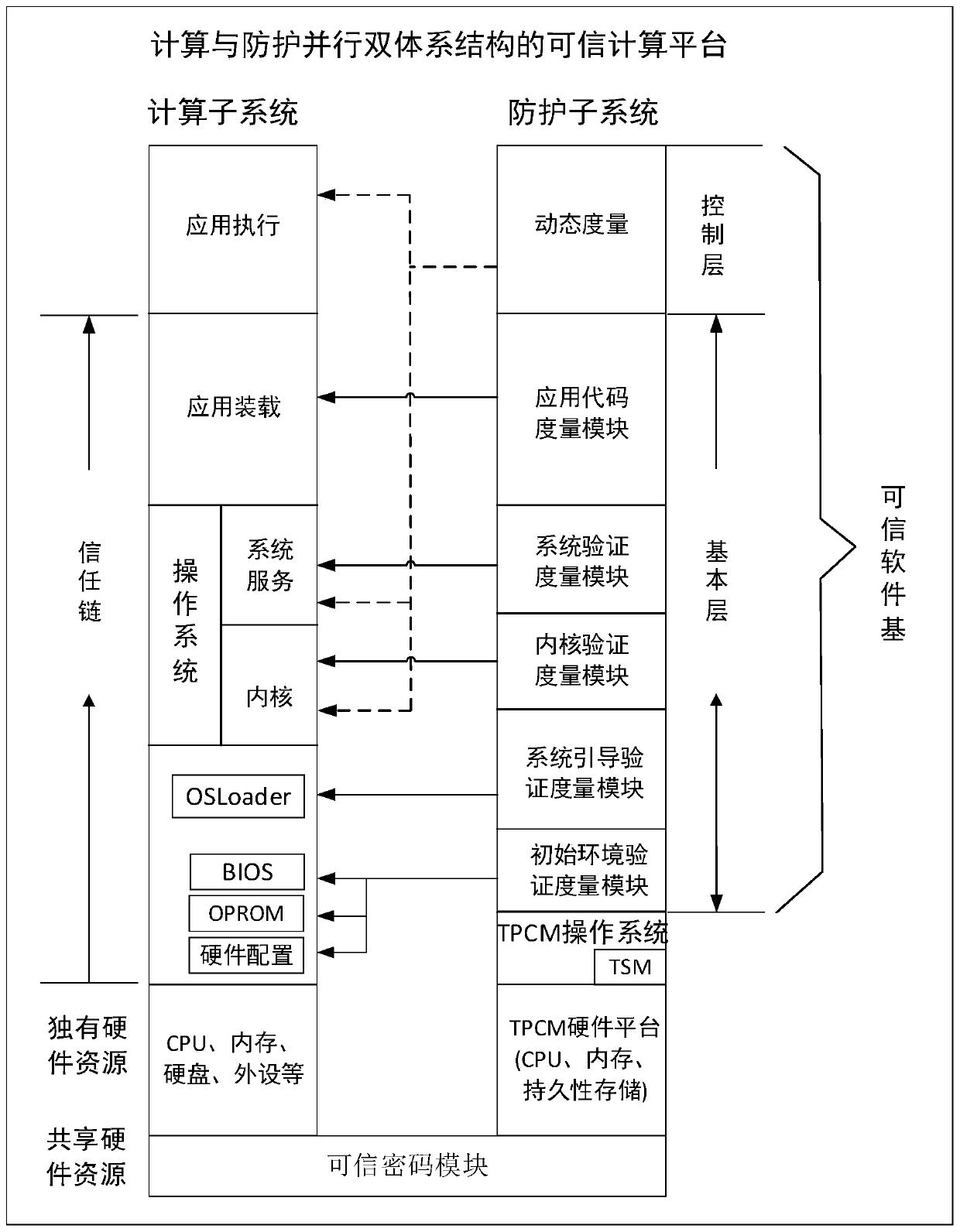
[0095] A system interaction method based on a dual-architecture trusted computing platform, the trusted computing platform includes: a parallel computing subsystem and a protection subsystem, the computing subsystem is used to complete computing tasks, and the protection subsystem is used to control Module, which actively measures and controls the computing subsystem according to the trusted policy; there is a security isolation mechanism between the computing subsystem and the protection subsystem, and they interact through a dedicated access channel;
[0096] System interaction methods include:
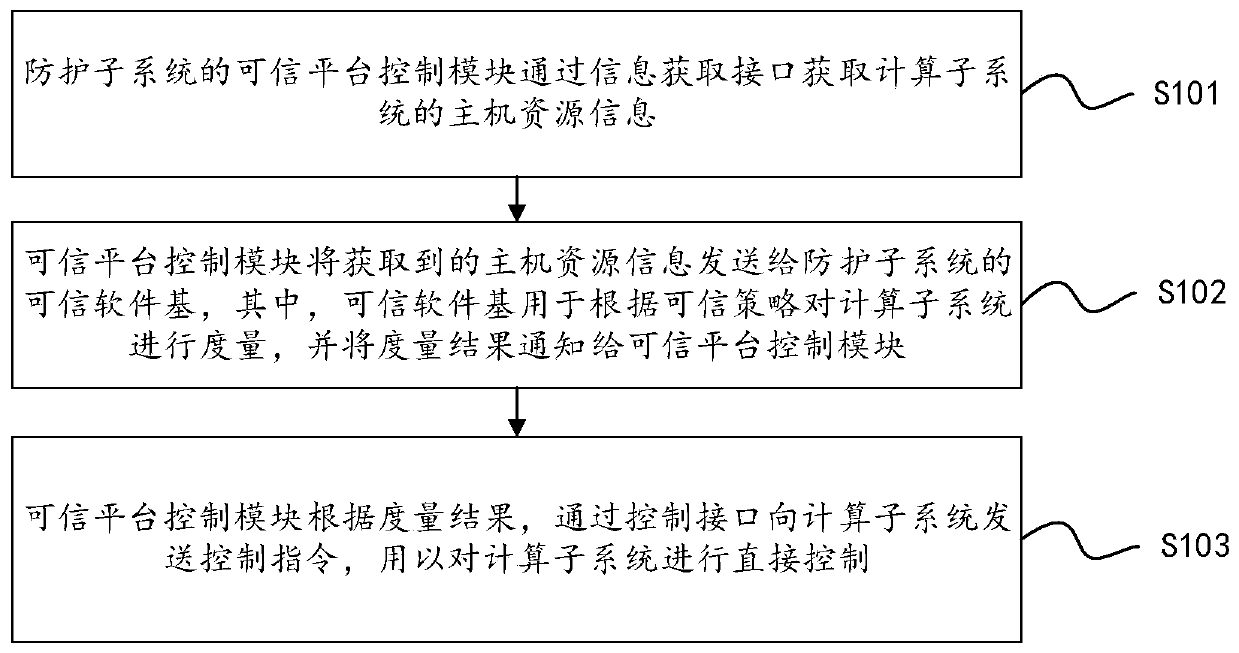
[0097] The protection subsystem obtains the host resource information of the computing subsystem through the host resource access interface and directly controls the computing subsystem, and / or, the protection subsystem per...
Embodiment 2
[0101] The process of one-way interaction between the protection subsystem and the computing subsystem through the host resource access interface will be described in detail below.
[0102] Host resource access interfaces can be divided into two categories: information acquisition interfaces and control interfaces.
[0103] Using the information acquisition interface through the shared bus, the TPCM can directly access the host resources of the computing subsystem without relying on the CPU of the computing subsystem. Use the information acquisition interface TPCM to obtain information such as memory, I / O devices, and CPU status of the computing subsystem.
[0104] The direct control of the protection subsystem to the calculation subsystem can also be realized by using the control interface. For example, host memory read and write, host I / O device control, power control, motherboard signal control, etc.
[0105] The host resource access interface is unidirectional, such as ...
Embodiment 3
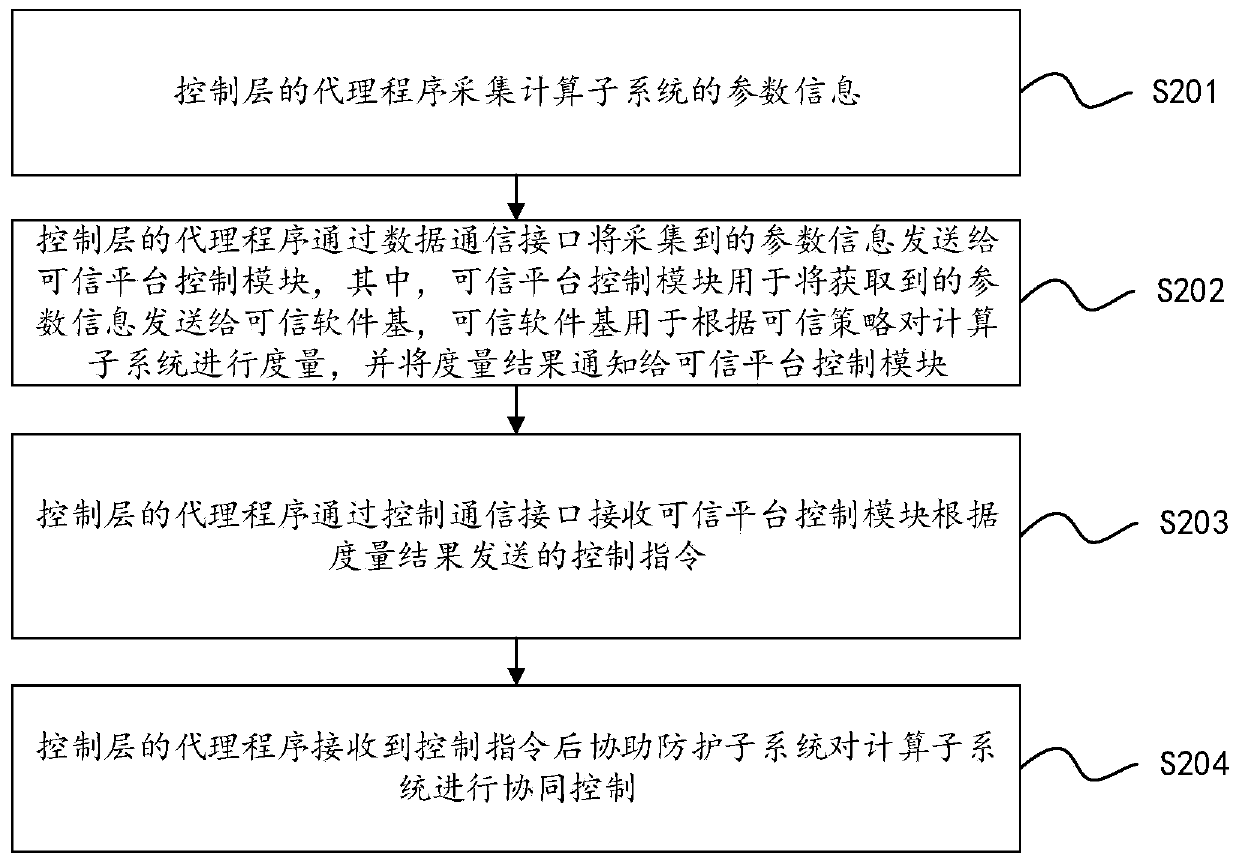
[0111]The process of two-way interaction between the protection subsystem and the computing subsystem through the communication interaction interface will be described in detail below.
[0112] When the protection subsystem adopts the proxy measurement mode, the protection subsystem performs information transmission and collaborative control with the computing subsystem through the communication interaction interface, including:
[0113] The agent program of the trusted software-based control layer of the protection subsystem transmits information with the trusted platform control module of the protection subsystem through the communication interaction interface, and assists the protection subsystem to carry out cooperative control of the computing subsystem;
[0114] Among them, the main program of the control layer is implanted in the protection subsystem, the agent program of the control layer is implanted in the computing subsystem, the operating system of the computing sub...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com