Method and system for analyzing boundary data by clustering method
A boundary data and clustering analysis technology, applied in the field of computer technology and data processing, can solve problems such as inability to detect and warn in time, abnormal business transmission, abnormal data format and content, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
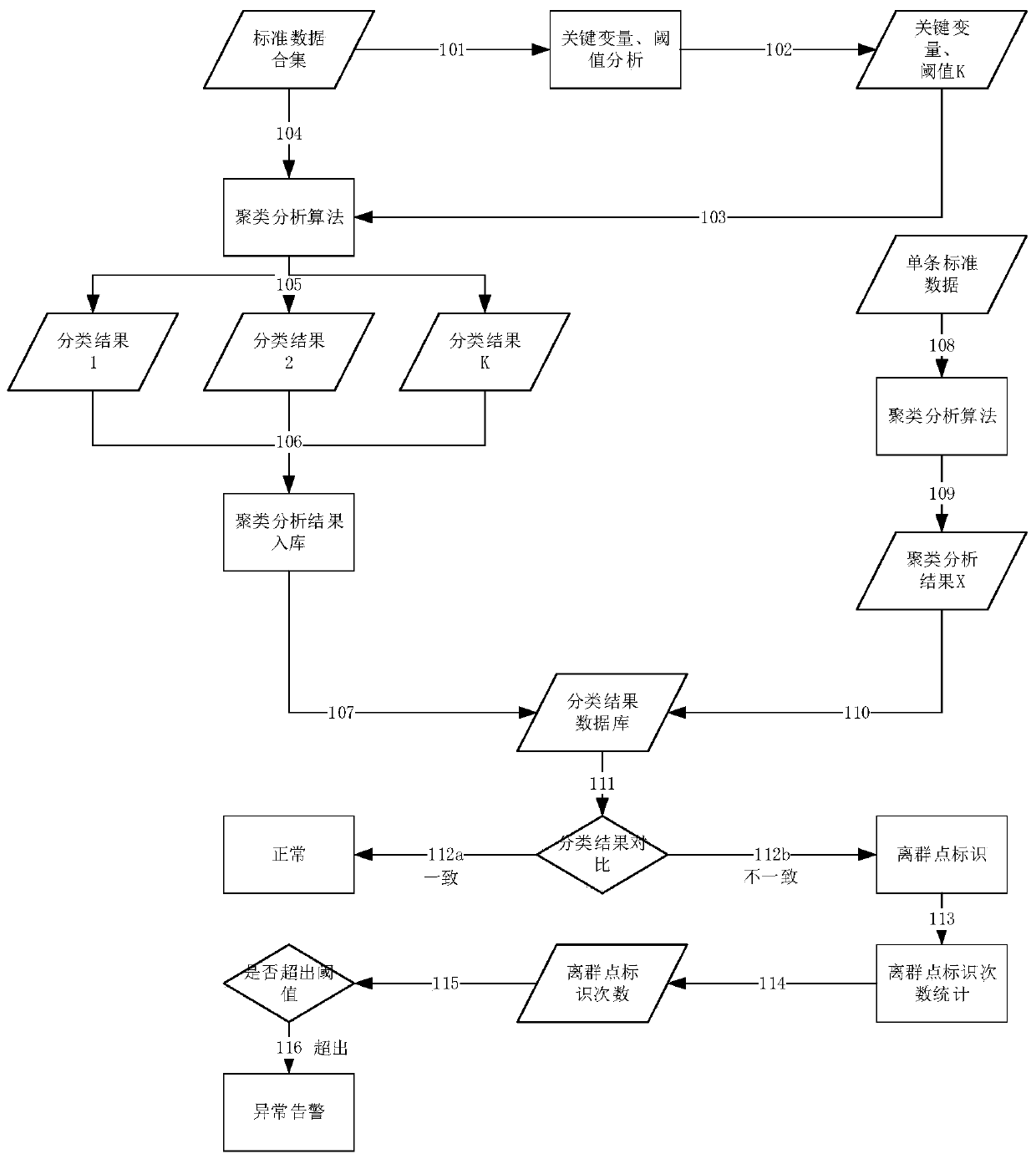
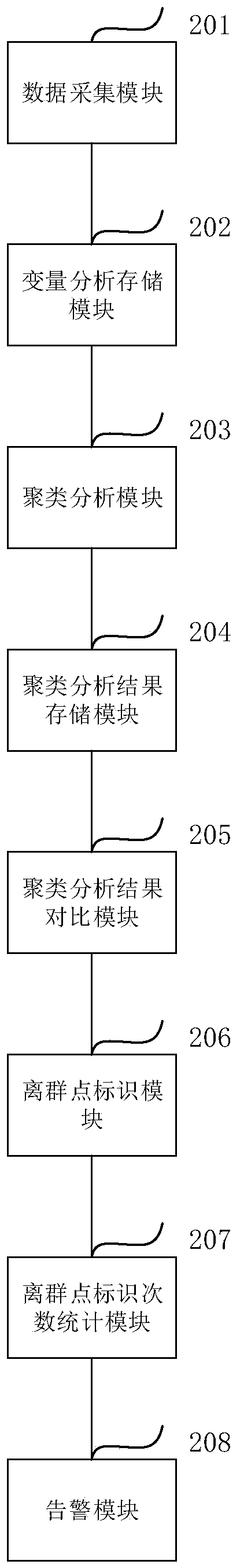
[0048] Such as figure 1 As shown, the specific implementation steps of the method for boundary data analysis by the clustering method in the present invention are as follows:
[0049] Step 1: Collect all kinds of log data generated during the border data exchange process, and obtain a standard data collection. Taking the public security border exchange platform as an example, the standard data collection of log data refers to the data exchange process of a certain business performed by the public security border exchange platform In , all relevant log data generated by relevant equipment, links and data exchange systems;
[0050] Step 2: This example is based on the public security border data exchange platform, taking the passenger accommodation information uploaded by a hotel as an example, based on prior experience, the uploaded file size (KB) and the corresponding transmission time (ms) are used as key variables . The corresponding key variable data are extracted from t...
Embodiment 2
[0114] This example is in the public security border data exchange platform. Taking the data exchange system as an example, the number of ftp connections and the port bandwidth occupancy rate of the data exchange system are used as key variables. The key variable data are as follows:
[0115] {90,40; 86,41; 89,40; 88,42; 86,39; 92,42; 91,43; 87,38; 82,36; 83,35; ,30; 74,29; 76,32; 73,28; 74,30; 75,29; 99,45; 98,44; 100,46; 101,48; 97,46; 100,47}.
[0116] And preset the threshold K=4, and select 4 points as the initial centroids, namely {90, 40; 82, 33; 75, 30; 100, 46}.
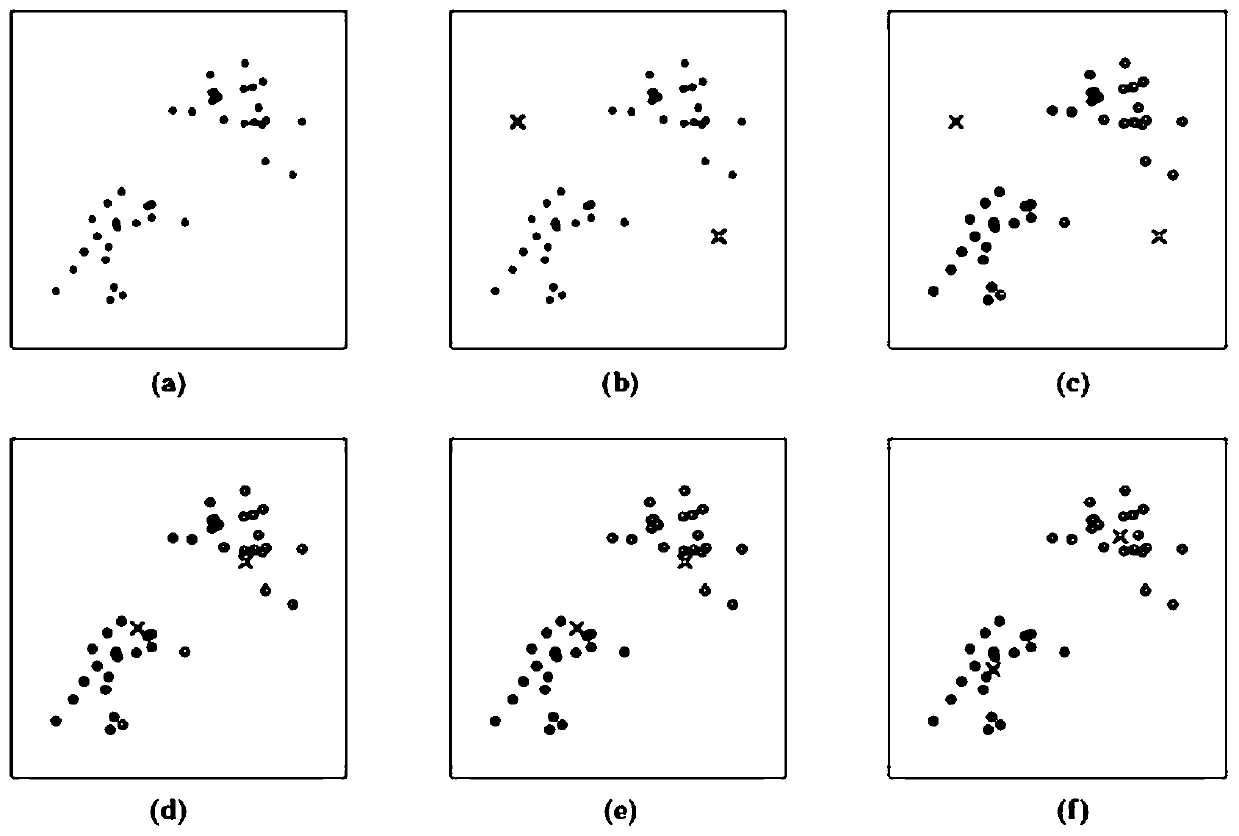
[0117] Substitute the key variable data into the K-means algorithm of the following formula (1) for cluster analysis, and calculate the key variable x and each centroid μ i (i.e. μ 1 ~ μ 4 ) Euclidean distance E:
[0118]
[0119] In the formula, x is the key variable, C i The cluster code after cluster division, that is, C 1 , C 2 , C 3 , C 4 ;
[0120] When first calculated, μ i The initial c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com