Security protection interface device for cloud computing platform
A cloud computing platform and security protection technology, applied in the field of cloud computing information security, can solve problems such as high cost and technology, difficulty, and company loss, and achieve the effects of avoiding copying internal information, ingenious structure, and novel ideas
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The specific implementation manners of the present invention will be described in further detail below in conjunction with the accompanying drawings.
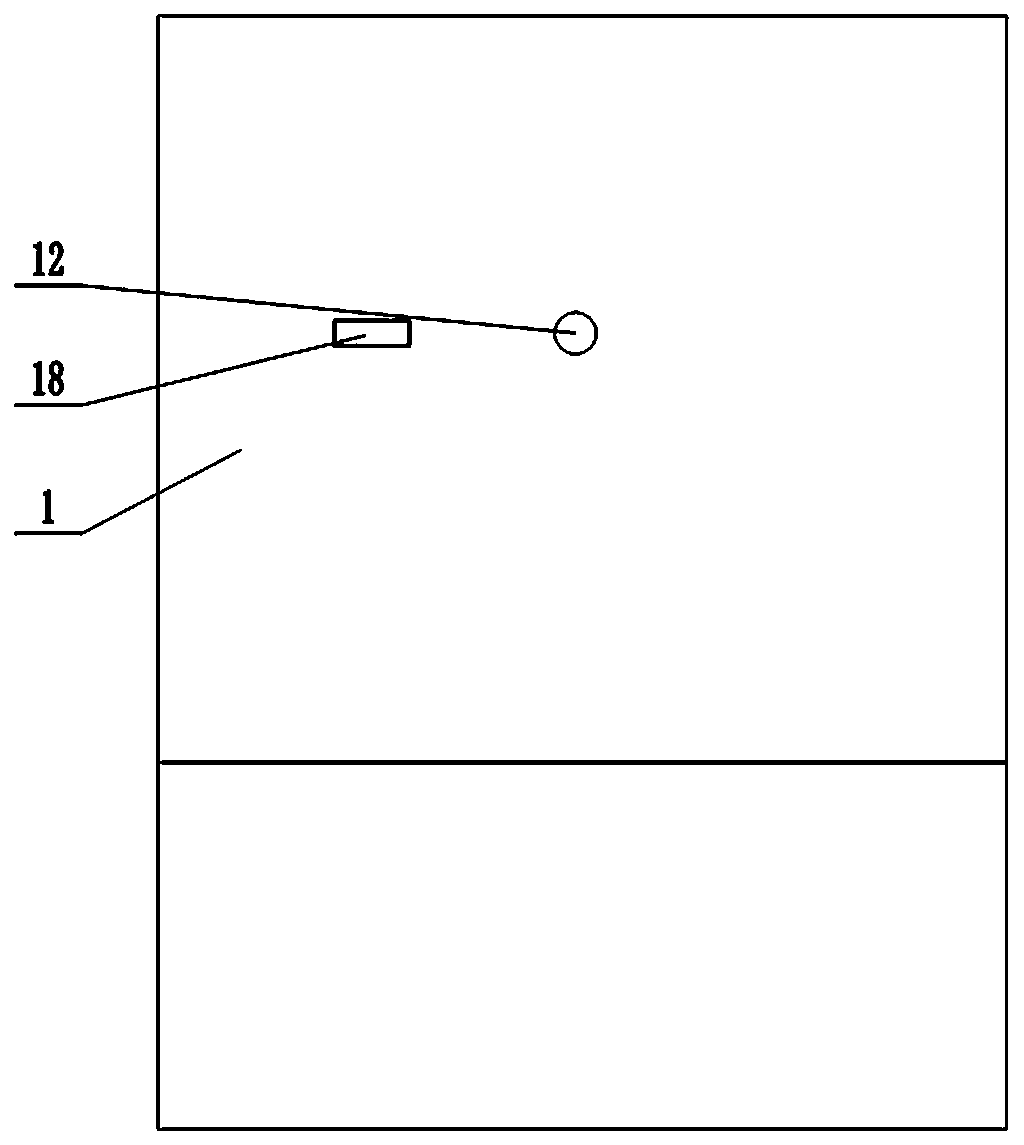
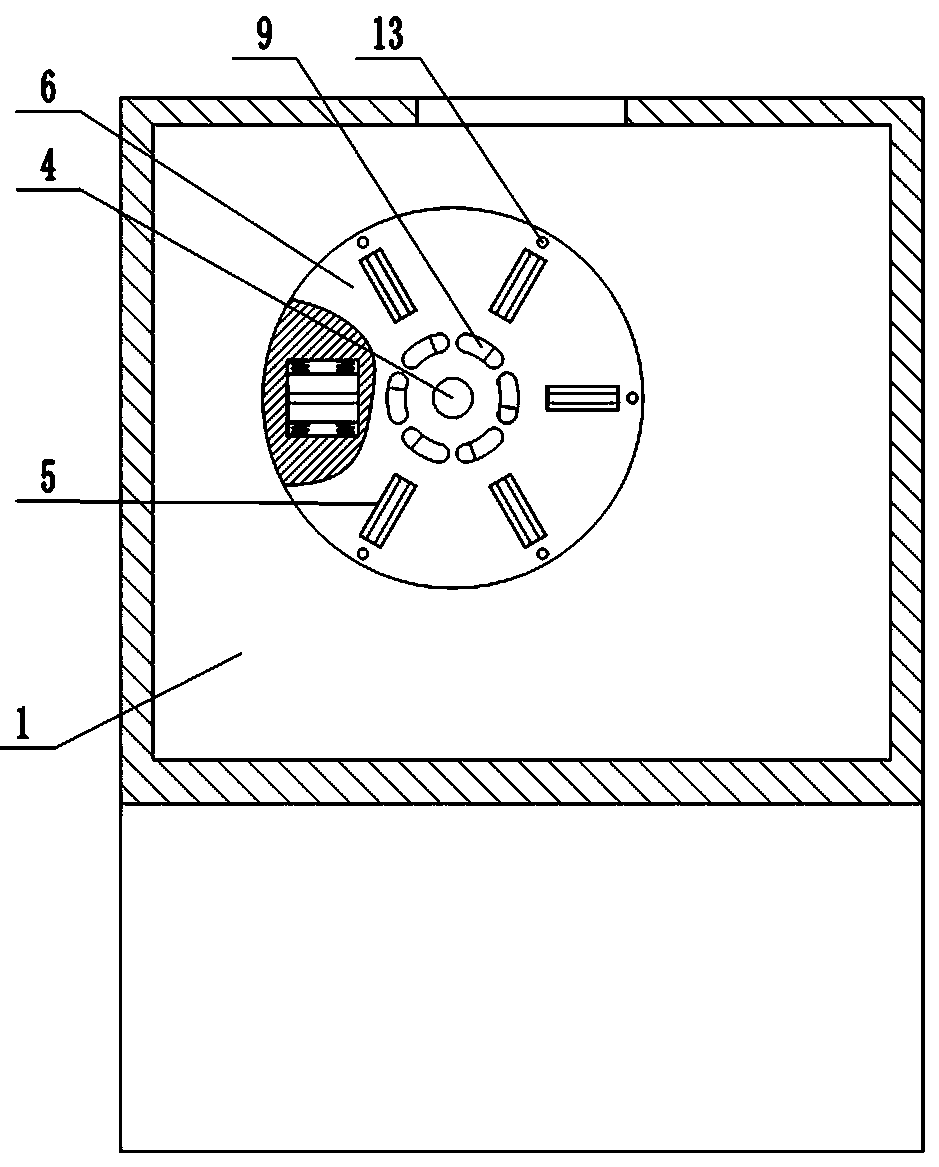
[0027] Depend on Figure 1-10 It can be seen that the present invention includes a body 1, the body 1 is provided with a socket 3, the front side of the body 1 is provided with a shield 2, the shield 2 is provided with a through hole 18 corresponding to the position of the socket 3, the shield 2 and the body 1 A connecting shaft 4 is fixed between them, and the inside of the shield 2 is provided with a turntable 6 mounted on the connecting shaft 4 and rotatable. The end surface of the turntable 6 is provided with a plurality of circumferentially uniform grooves 5, each groove All can be placed on the same straight line with the rotation of the turntable 6 with the through groove and the socket 3, and a mounting groove is provided on the side wall of each groove 5, and a wedge-shaped baffle plate 7 is installed in each mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com