Patents
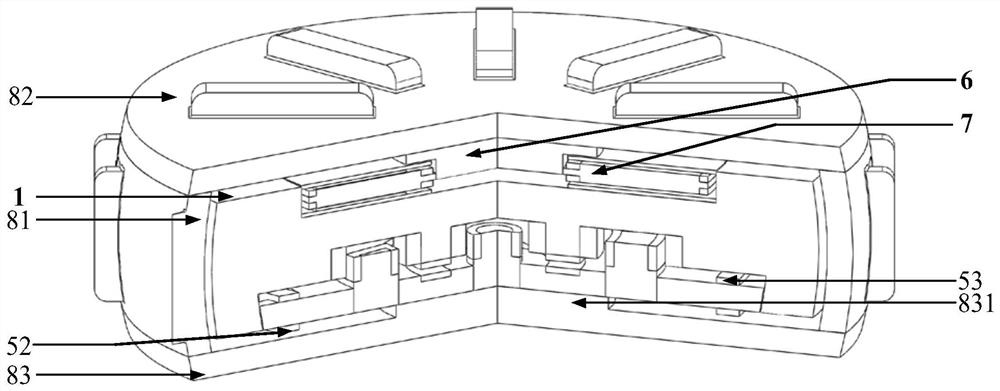
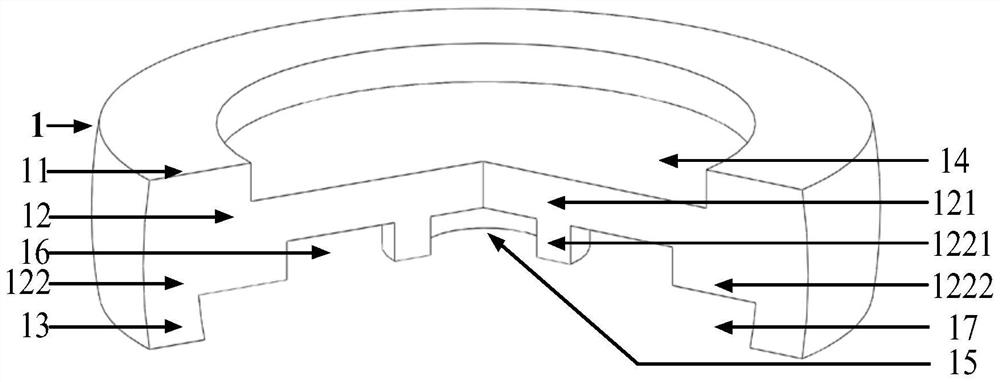
Literature
51results about How to "Implement security protection" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
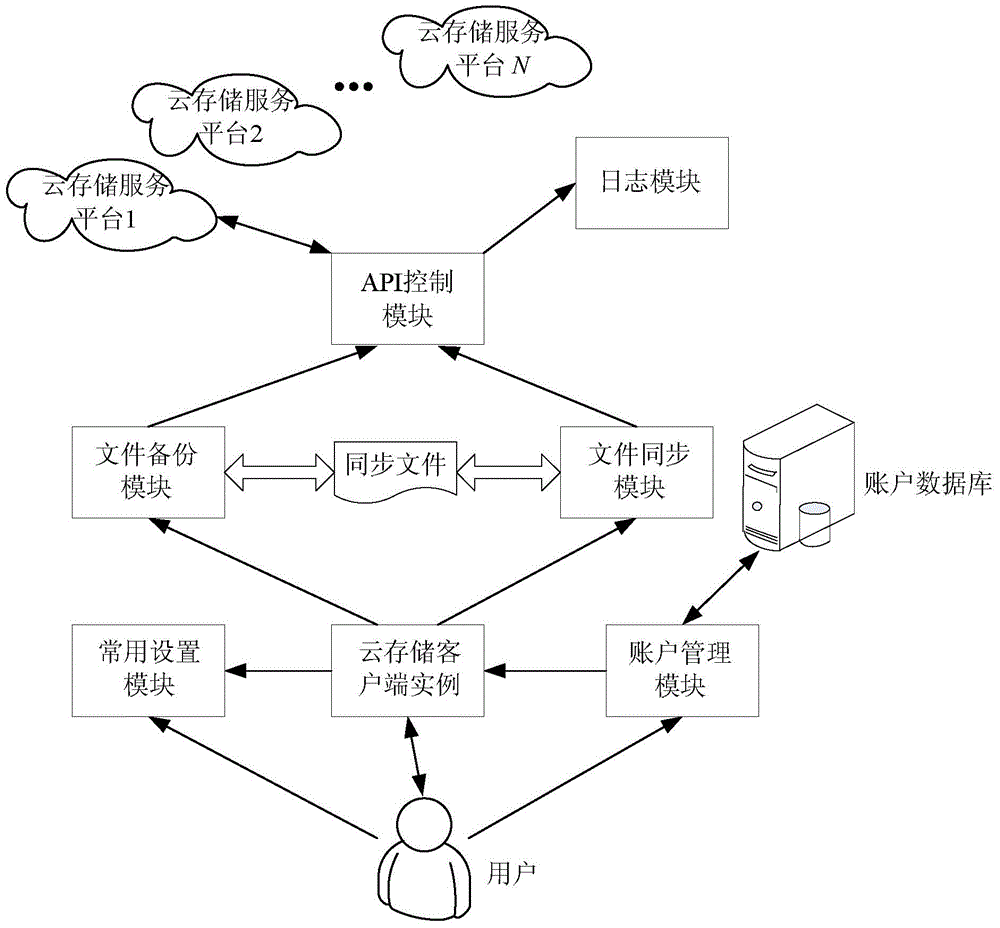
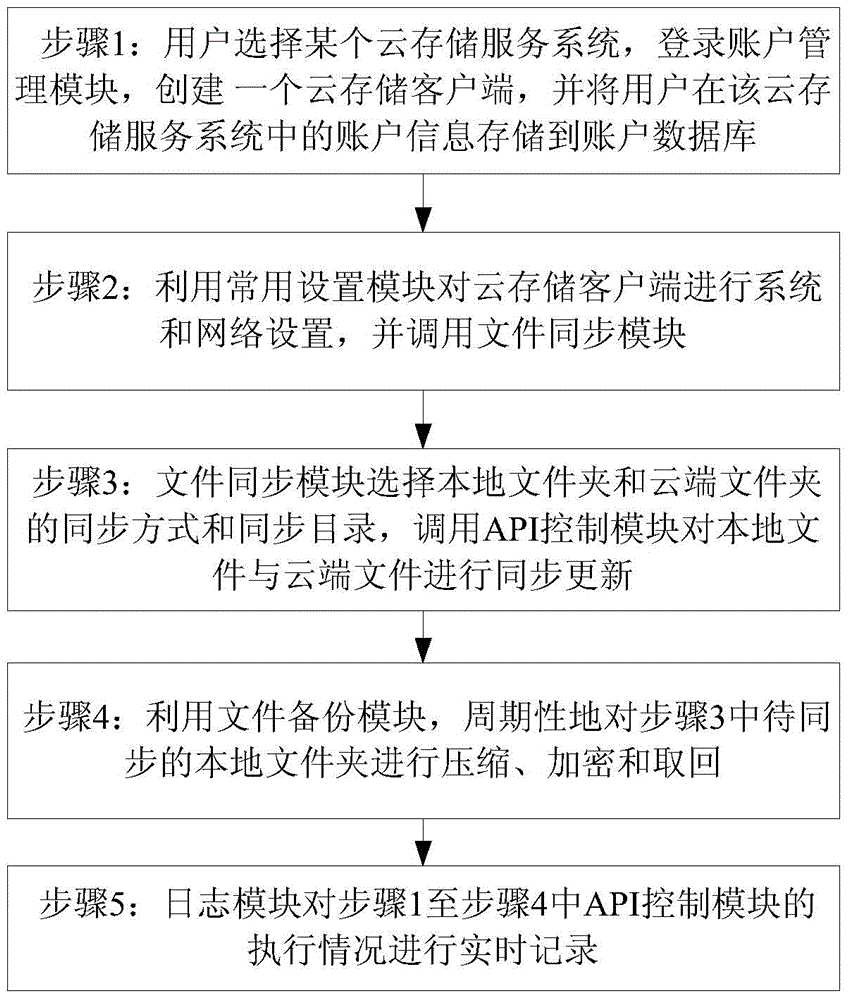
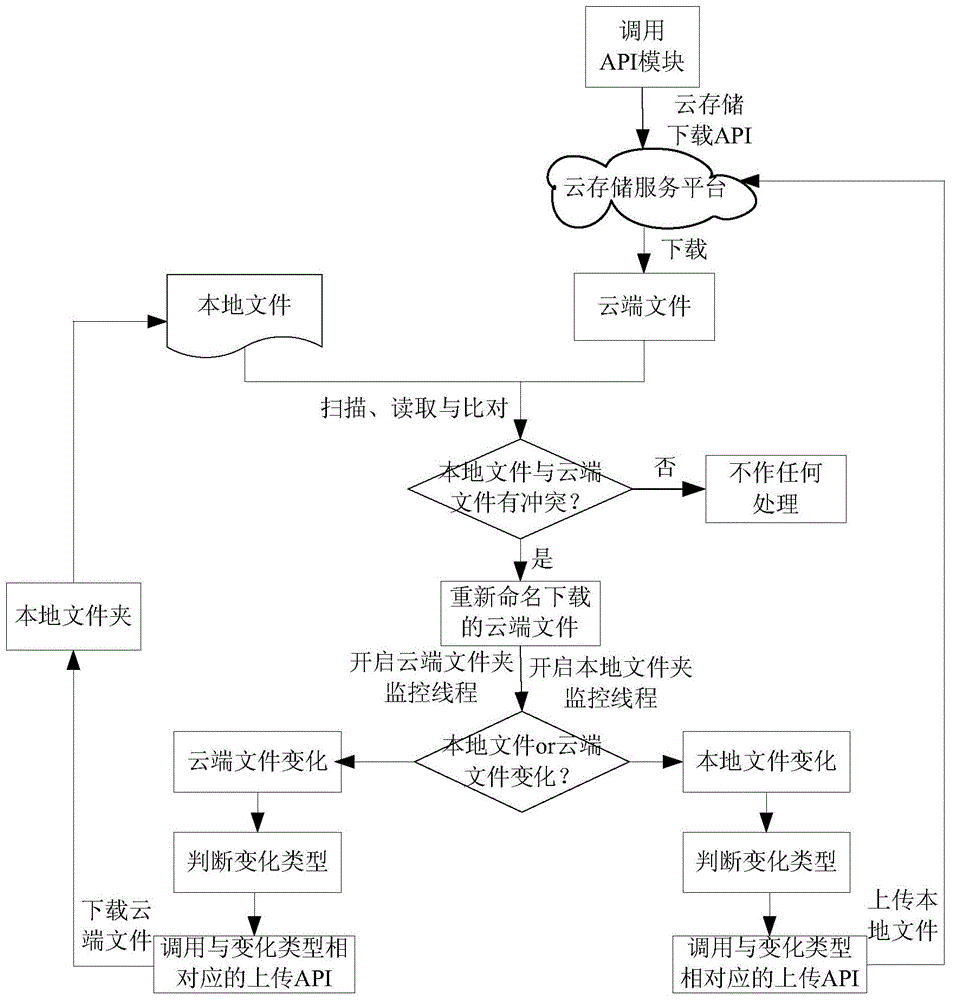
Automatic cloud storage synchronous management system for a plurality of cloud storage service platforms and method thereof
InactiveCN105100170AImplement automatic storageAchieve synchronizationTransmissionFile synchronizationPaper document
The invention relates to an automatic cloud storage synchronous management system for a plurality of cloud storage service platforms and a method thereof. The automatic cloud storage synchronous management system comprises cloud storage service platforms, an account management module, a normal setting module, a file synchronizing module, an API control module, a file backup module and a log module. A user firstly selects a certain cloud storage service platform and logs the account management module for creating a cloud storage client. Then the normal setting module is used for performing system and network setting on the cloud storage client. Furthermore the API control module is called through the file synchronizing module for synchronously updating a local file and a cloud-end file, thereby realizing automatic storage and synchronization for the plurality of cloud storage service platforms. Secondly, the file backup module periodically compresses and encrypts a document file to be backed up and takes the document file back. Finally the log module records the execution state of the API control module in real time. The automatic cloud storage synchronous management system and the method thereof realize safety protection for the backup files which are stored at the cloud end.
Owner:ZHEJIANG OCEAN UNIV
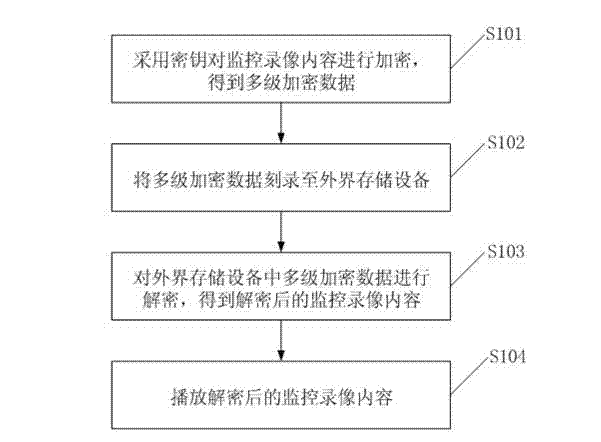
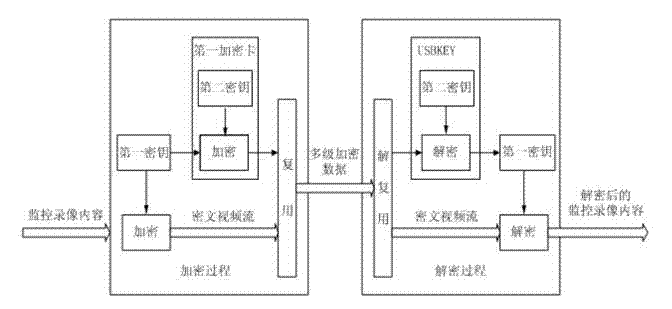
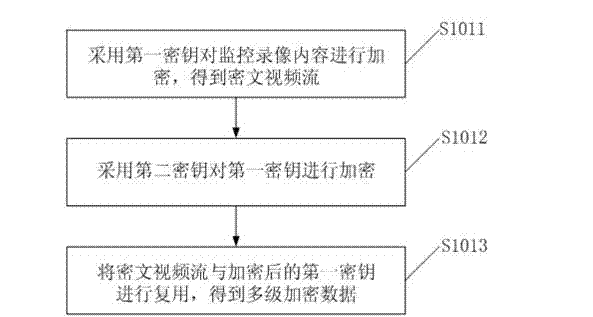
Protection method and protection system of surveillance video content
ActiveCN103200387AImplement security protectionImprove securityTelevision system detailsColor television detailsMultiplexingPlaintext
The invention discloses a protection method of surveillance video content and a protection system of surveillance video content. The protection method of surveillance video content includes the steps: utilizing a first secret key to encrypt the surveillance video content to obtain ciphertext video streaming; utilizing a second secret key to encrypt the first secret key; multiplexing the ciphertext video streaming and encrypted first secret key according to multiplexing rules to obtain multistage enciphered data, and recording to external storage equipment; when the multistage enciphered data are played, demultiplexing the multistage enciphered data according to the multiplexing rules to obtain the ciphertext video streaming and the encrypted first secret key; and deciphering the encrypted first secret key according to the second secret key of USBKEY to obtain the encrypted surveillance video content. The protection method of surveillance video content and the protection system of surveillance video content effectively achieve protection of the surveillance video content and solve the problems that the surveillance video content in the prior art is mainly proclaimed in writing, and leakage of a secret of the video content is easily caused.
Owner:北京视博数字电视科技有限公司
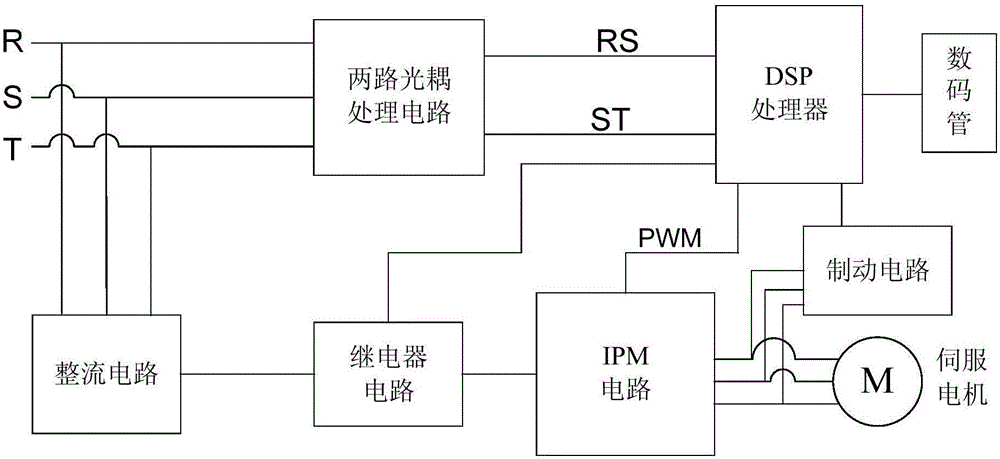
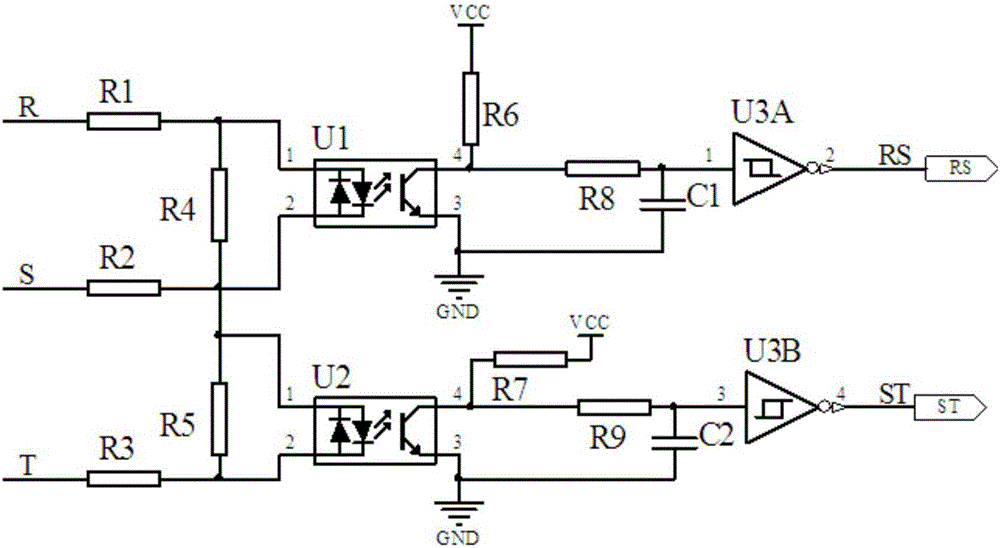
Three-phase power supply default phase and power failure detection system and braking method
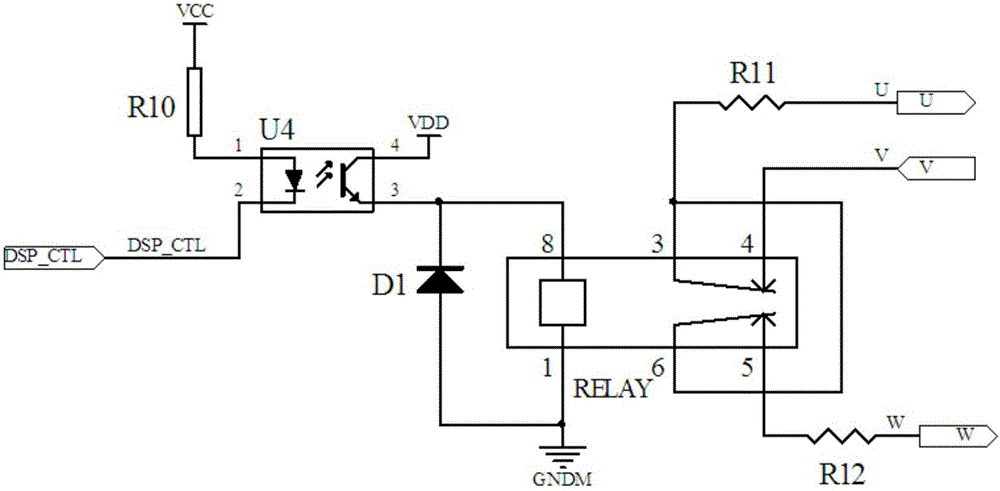
ActiveCN106124872AImplement security protectionSettle the pricePower supply testingPolyphase network asymmetry measurementsElectrical devicesEngineering
The invention discloses a three-phase power supply default phase and power failure detection system and a braking method. The detection system comprises a three-phase power supply RST, a rectification circuit, a relay circuit, an IPM circuit, two optocoupler processing circuits, a DSP processor, a braking circuit, a Nixie tube and a servo motor and is applicable to a motor control system of a servo driver. The braking method comprises the following steps: judging abnormal conditions such as default phase and power failure of the three-phase power supply, then closing a PWM signal by the DSP processor, cutting off a busbar power supply by virtue of the relay circuit, starting and accessing the braking circuit, connecting a braking power resistor among three-phase windings of the servo motor in series for realizing short connection of the three-phase windings, and generating current in a short connection loop by virtue of residual magnetism potential of a stator winding, so that the motor is rapidly braked. The detection system and the braking method, which are disclosed by the invention, have the advantages that security protection effect on electrical equipment and personnel is realized, implementation is easy, cost is low, and the problems that a motor in existing electrical equipment adopts a band-type brake module, price is high, size is large and control and wiring are complex can be solved, so that the detection system and the braking method have a good application prospect.
Owner:NANJING KANGNI ELECTRONICS TECH
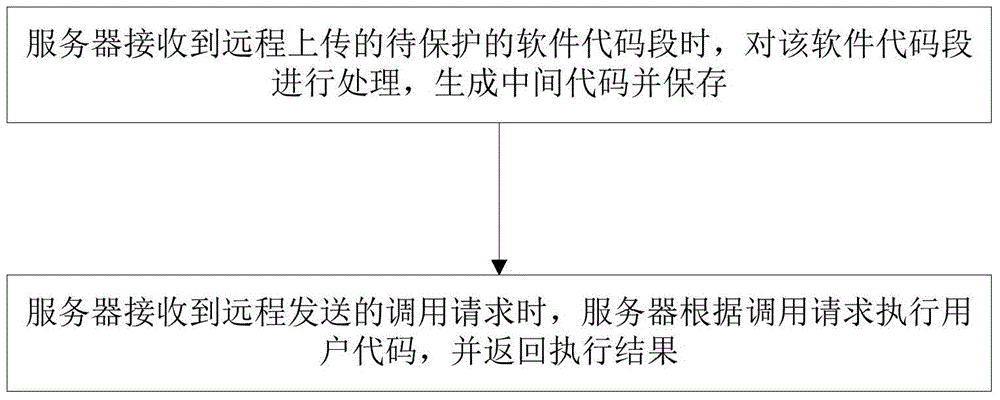
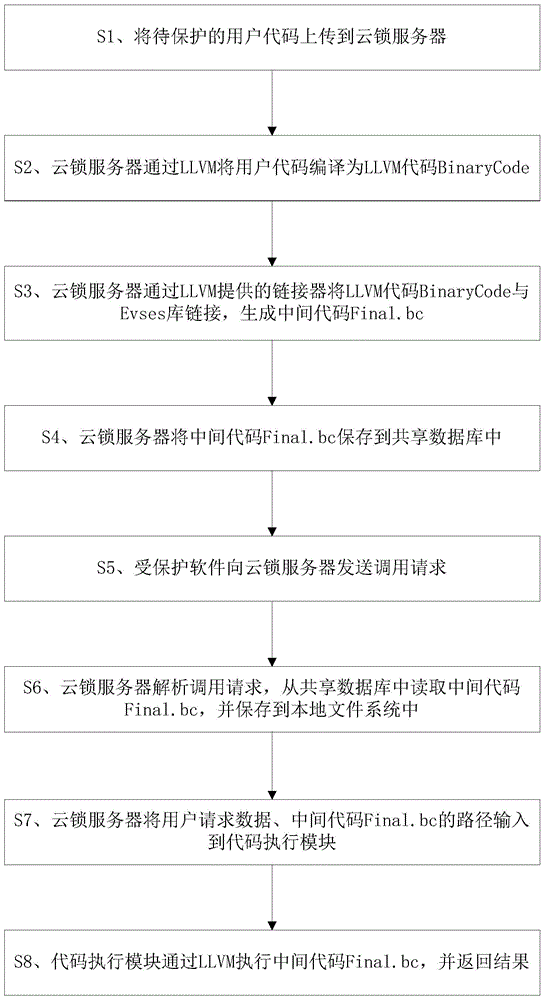
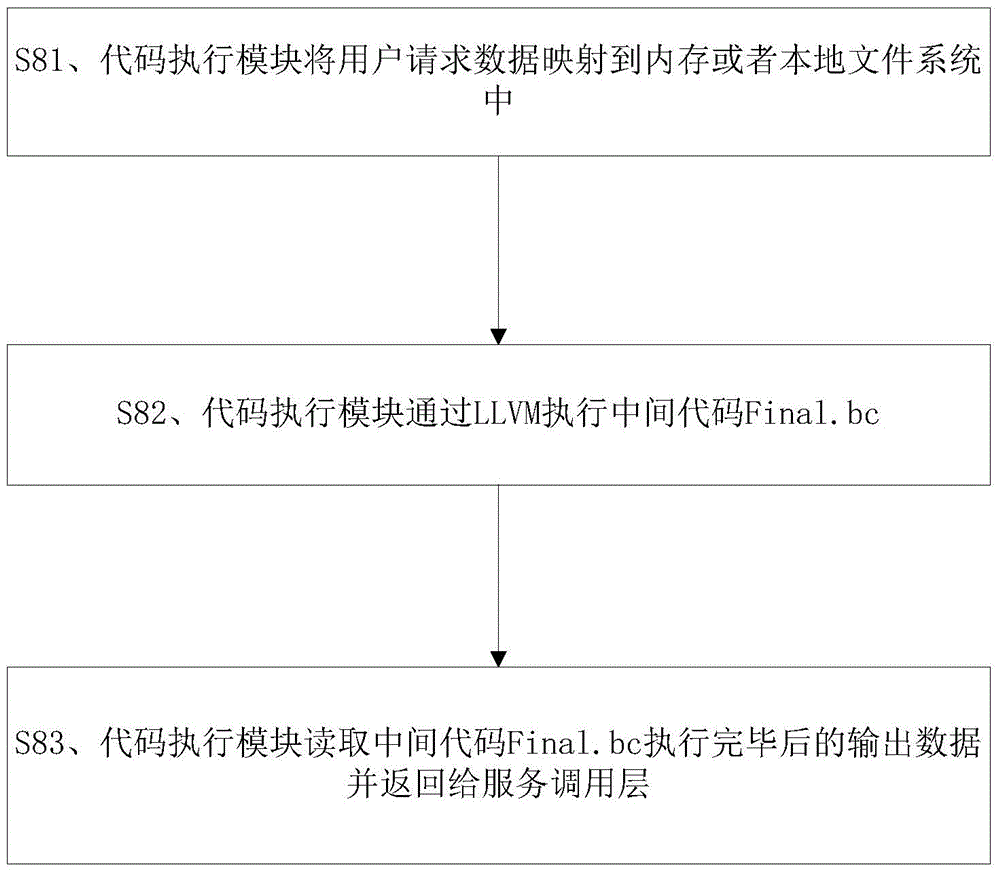
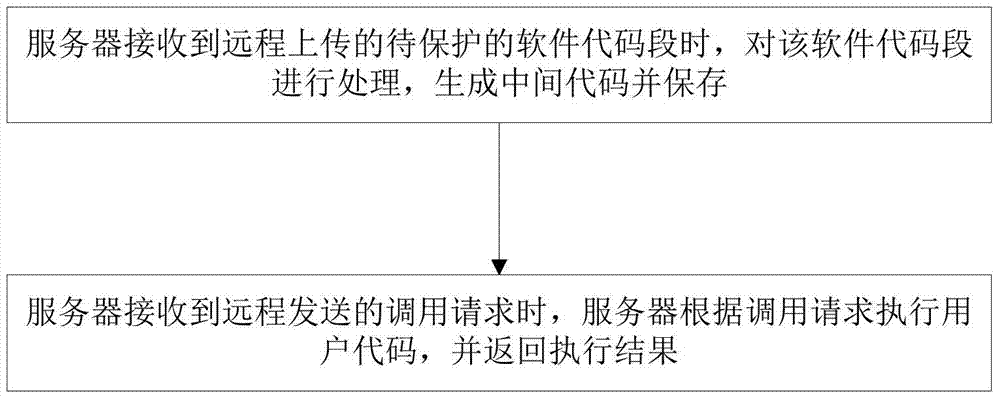
Software protection method and system
ActiveCN104392151AImprove securityAvoid smallProgram/content distribution protectionExtensibilityOperational system
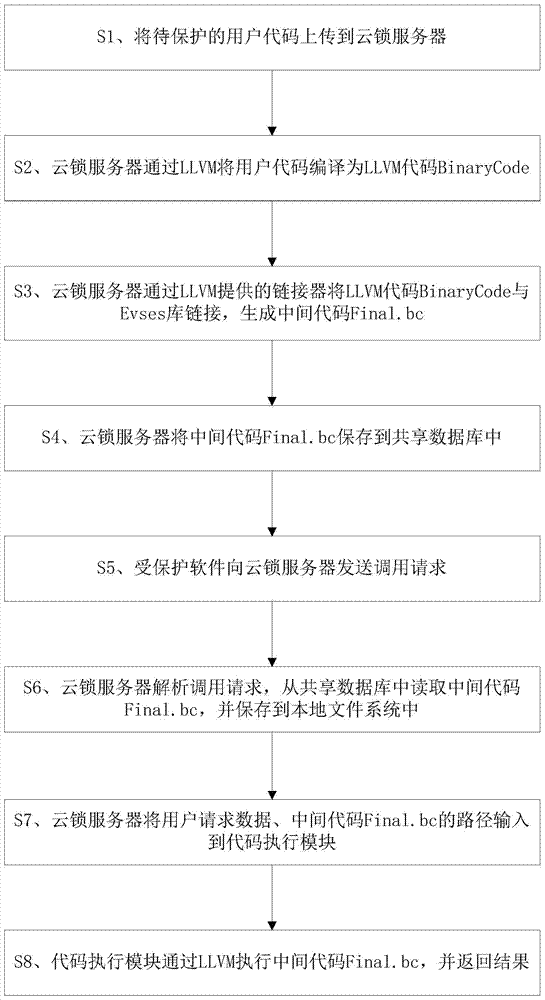
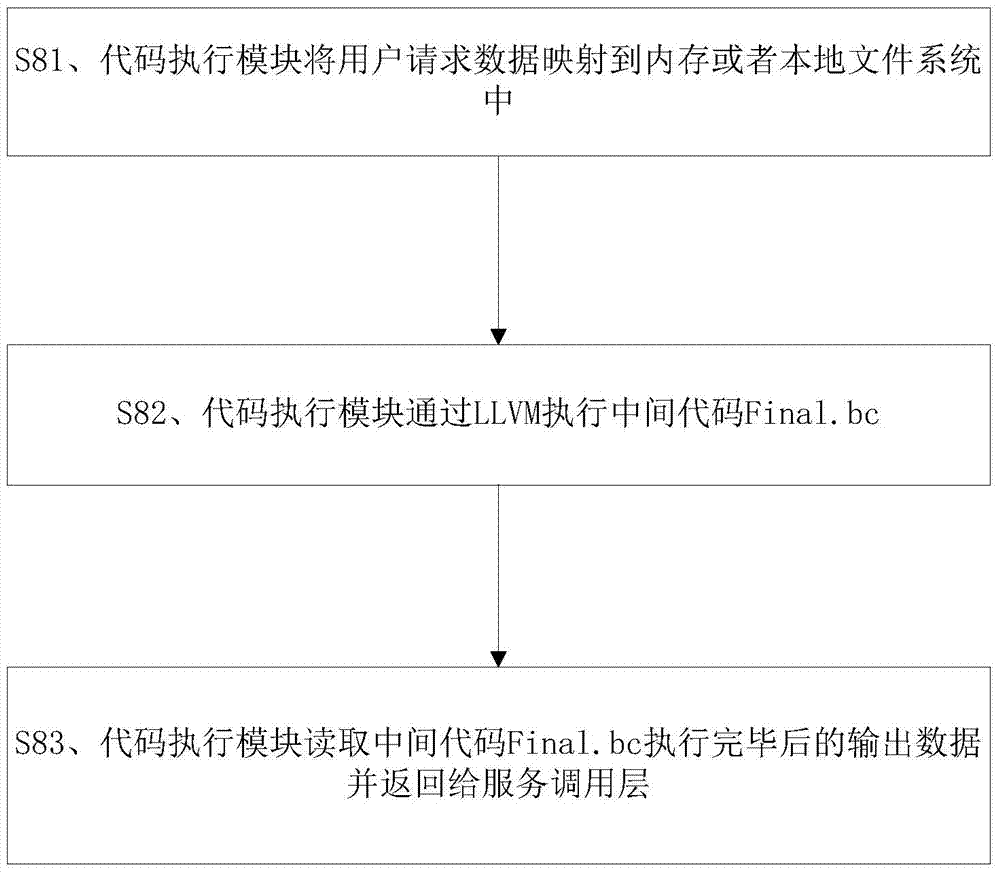
The invention discloses a software protection method. The method includes the steps: on receiving a software code snippet to be protected and remotely uploaded, a server processes the software code snippet into an intermediate code and stores the intermediate code; on receiving a call request aiming at the software code snippet and remotely transmitted, the server executes the intermediate code according to the call request and returns execution results. The invention further discloses a corresponding software protection system. The software protection method and system has the advantages that software security is higher, no limits on operating systems and hardware occur, and extensibility is high.
Owner:BEIJING SENSESHIELD TECH
Network resource access control method under zero trust
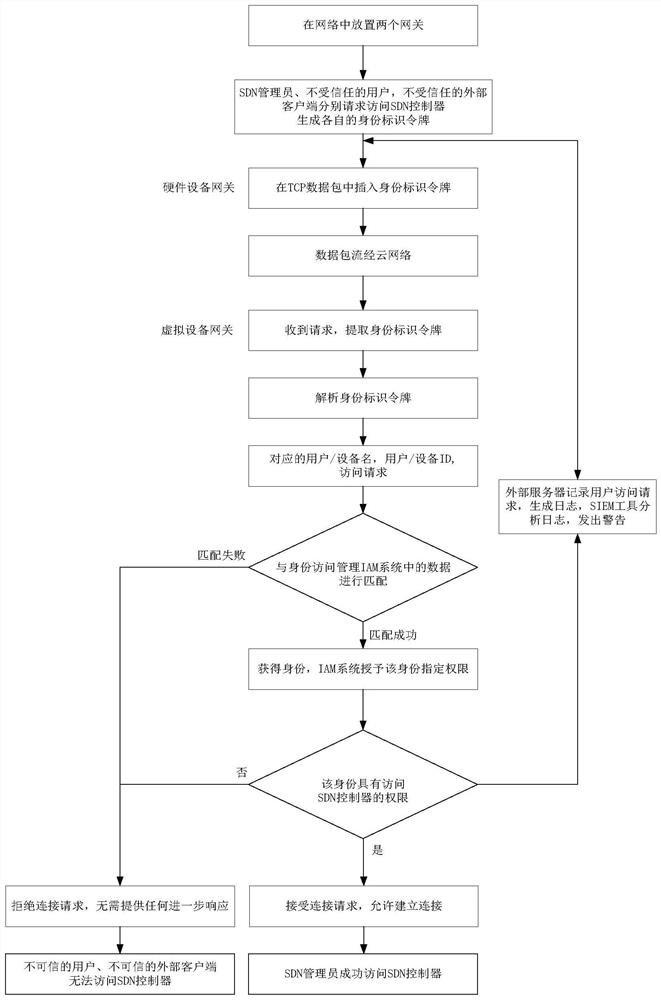
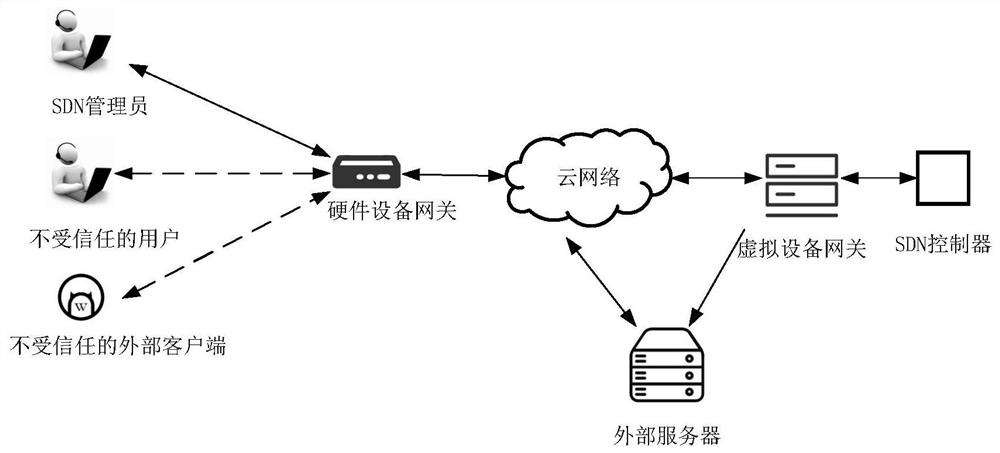
The invention discloses a network resource access control method under zero trust, and mainly solves the problems that illegal access of intranet users or authorized users to network resources cannot be prevented in time and the security of the network resources cannot be ensured in the prior art. According to the implementation scheme, an identity token is generated before a user accesses network resources, and then the identity token is embedded into a TCP data packet and analyzed; whether a connection request of the user is accepted is judged according to an analysis result; according to the method, the authorized user is allowed to access, and the request of the unauthorized user is directly rejected under the condition of not feeding back any related information, so that the access control under zero trust is realized. According to the method and the system, illegal access of intranet users or authorized users to network resources can be effectively prevented, illegal users are prevented from obtaining key information of the network resources, the safety of the network resources is ensured, and the method and the system can be used for resource access to enterprise-level servers or cloud computing environments under zero trust.
Owner:XIDIAN UNIV
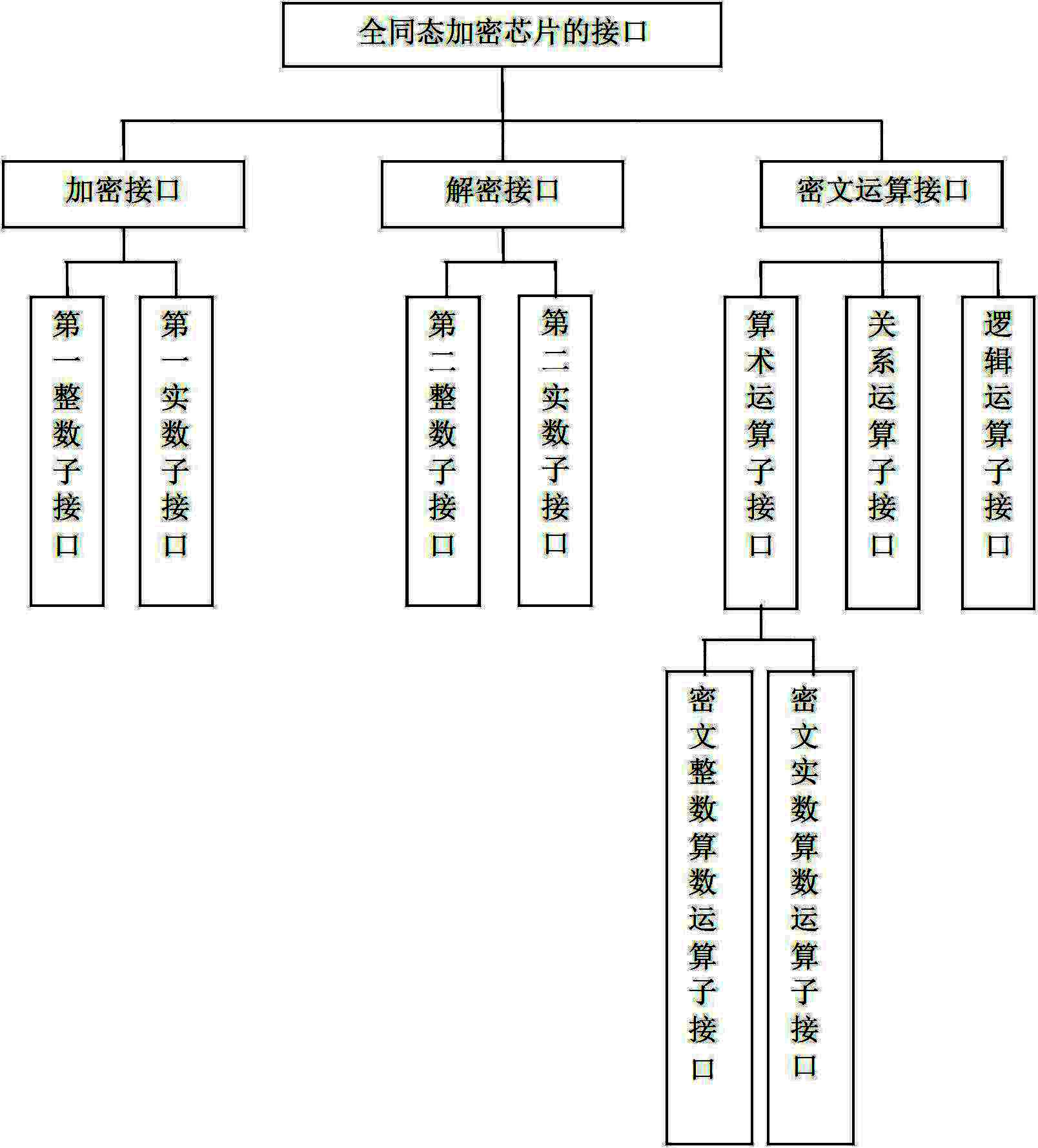
Interface unit for fully homomorphic encryption chip
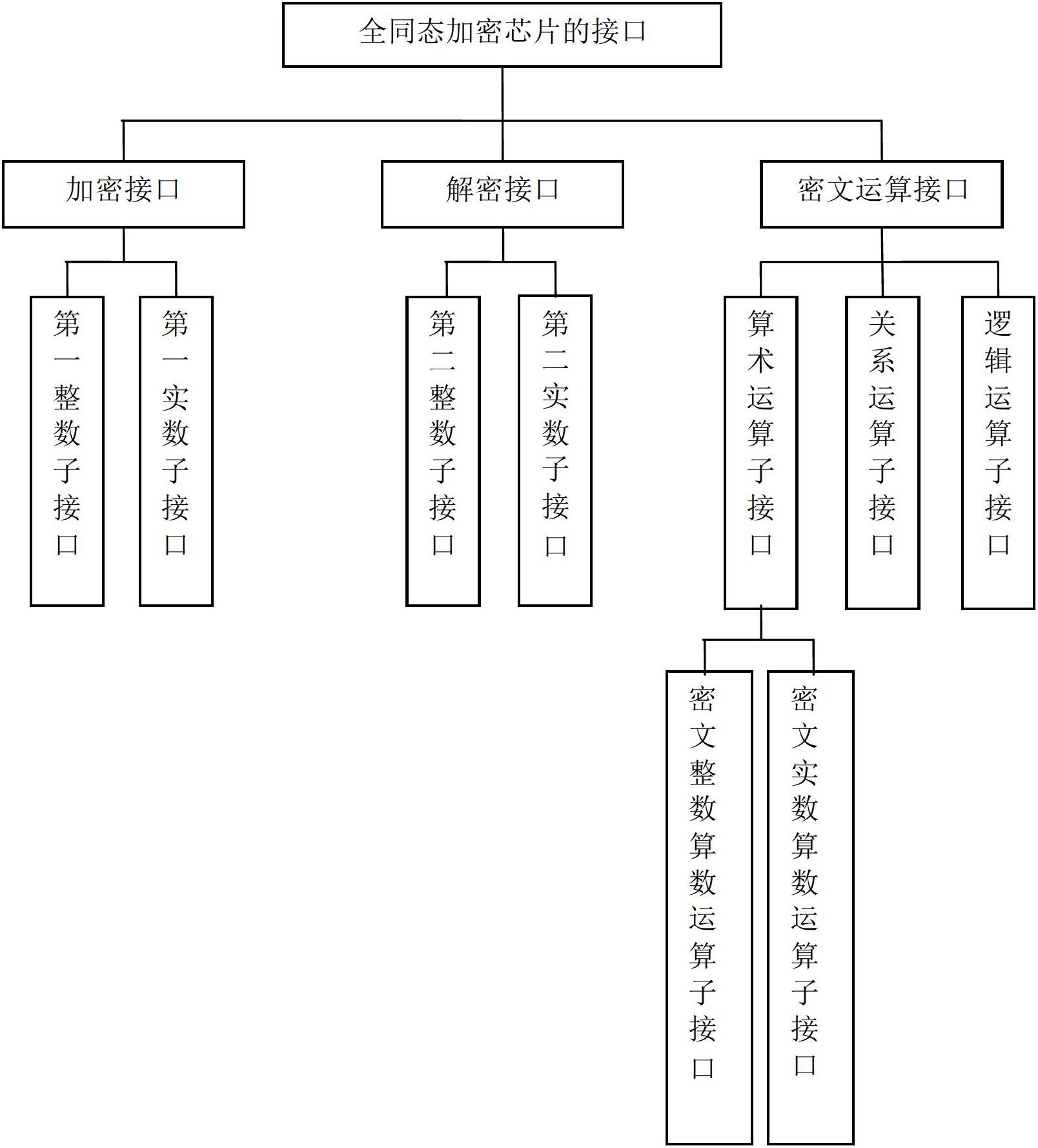
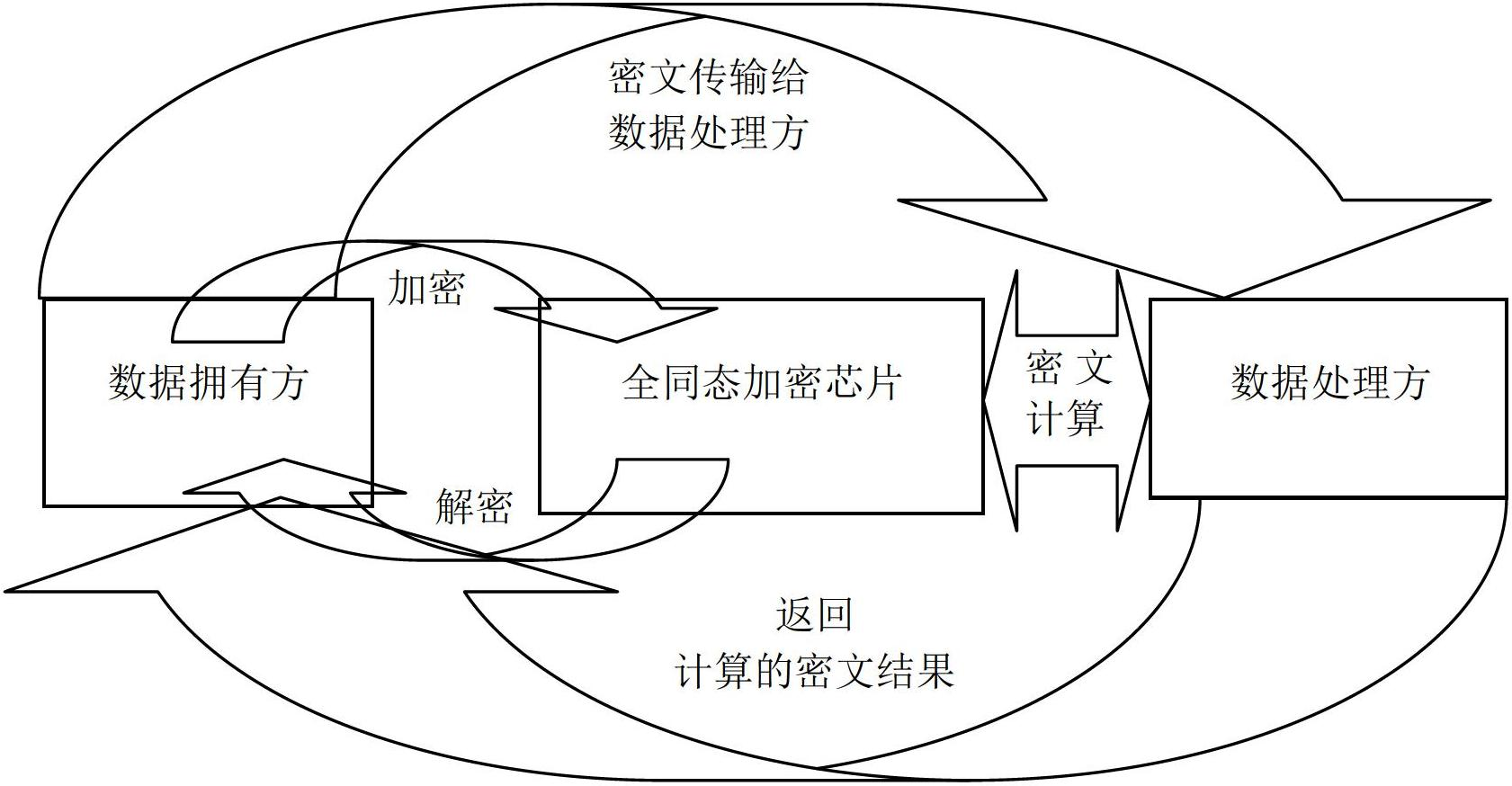
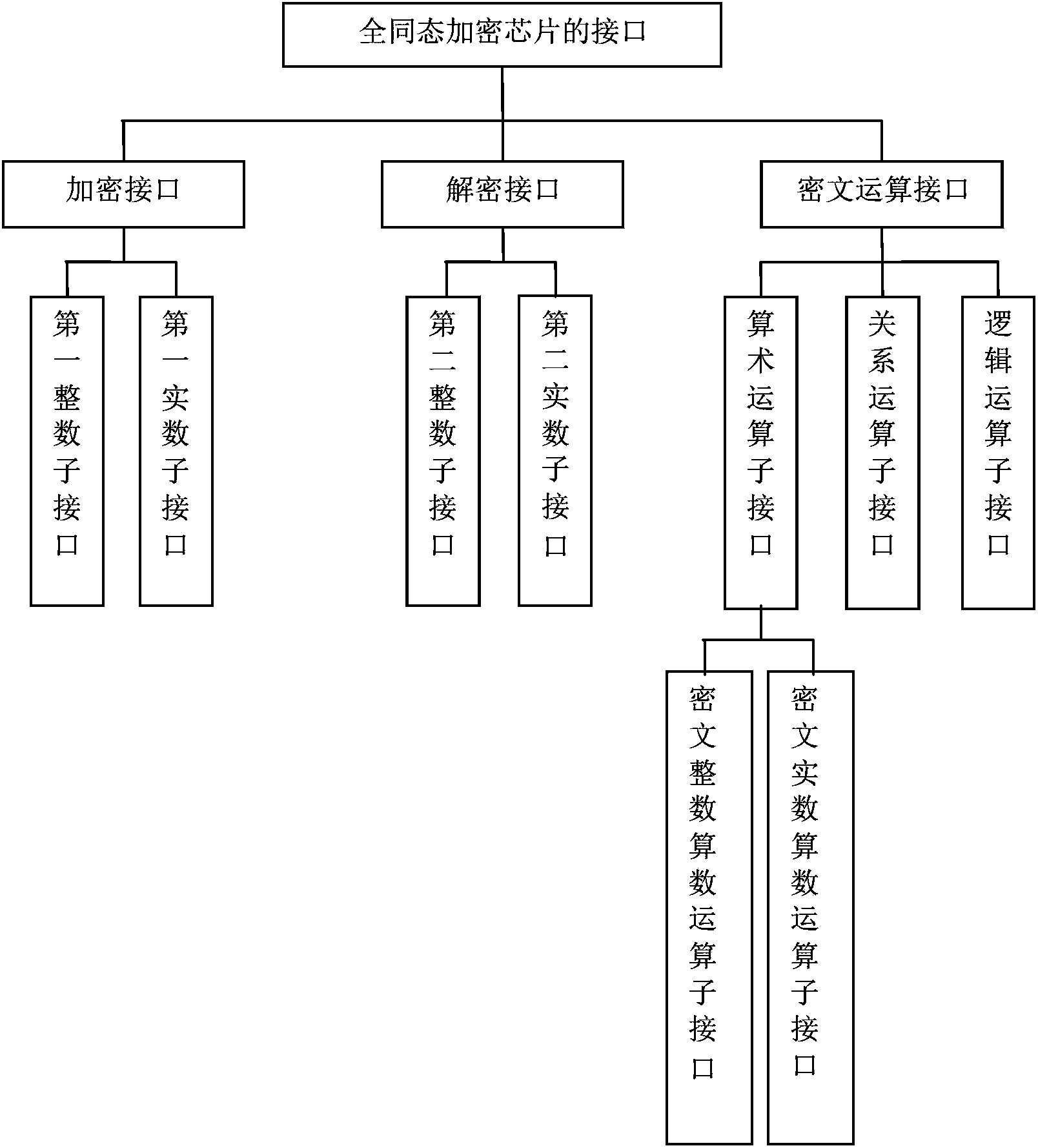
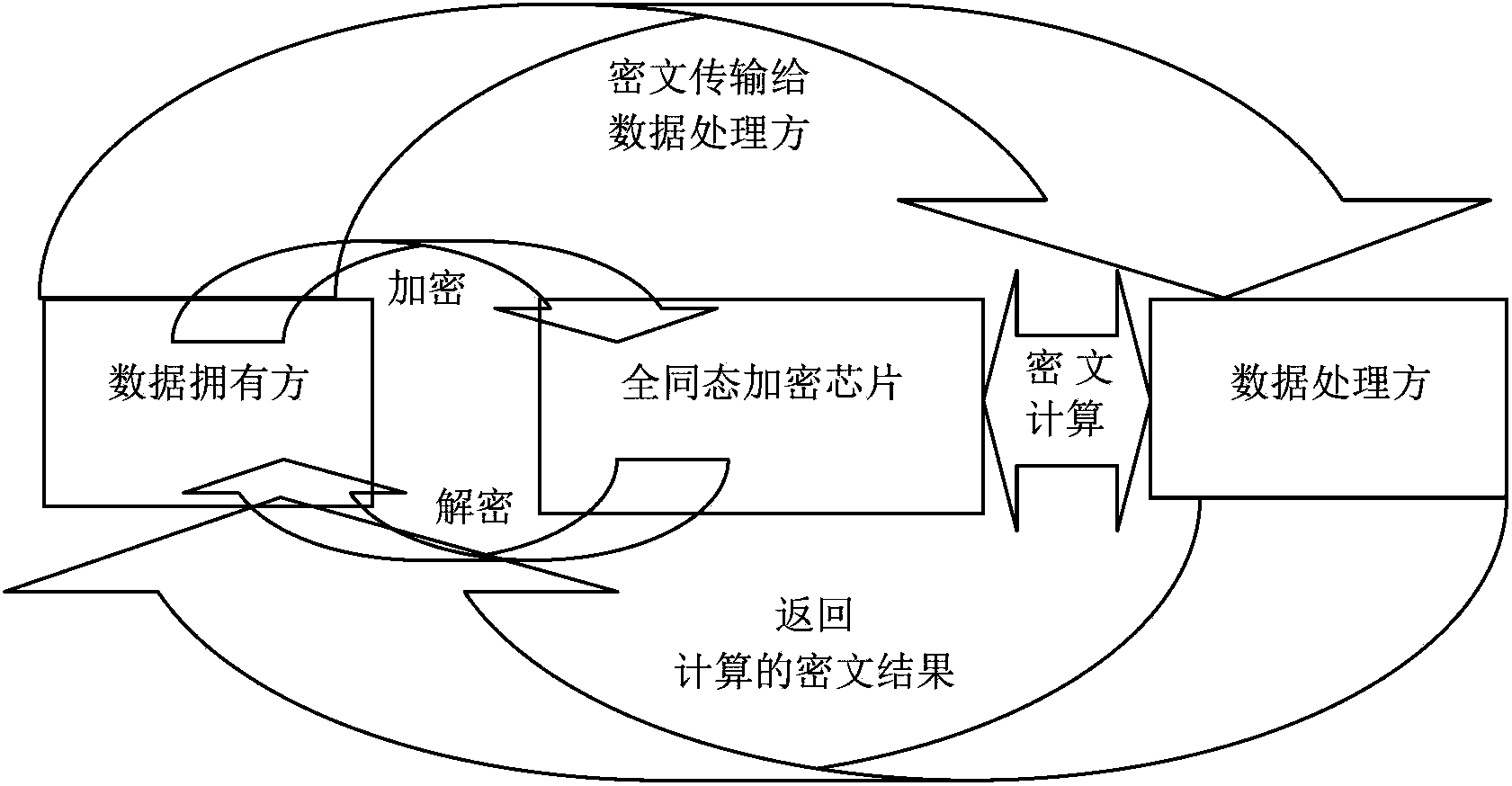
ActiveCN102694644ARealize encryption and decryptionImplement security protectionCoding/ciphering apparatusCommunication with homomorphic encryptionComputer hardwarePlaintext
The invention discloses an interface unit for a fully homomorphic encryption chip. The interface unit comprises an encryption interface, a decryption interface and a cipher text operation interface. The encryption interface is used for encrypting data of a data owner to generate cipher texts and transmitting the cipher texts to a data processor. The cipher text operation interface is used for receiving the cipher texts from the data processor to operate the cipher texts and transmitting the operated cipher texts to the data owner. The decryption interface is used for receiving the operated cipher texts from the data owner, decrypting the cipher texts to generate plain texts, and transmitting the plain texts to the data owner. The encryption interface comprises a first integer sub-interface and a first real sub-interface, wherein the first integer sub-interface is used for encrypting plain text integers and plain text unsigned integers, and the first real sub-interface is used for encrypting plain text real numbers, plain text floating numbers, plain text double-precision floating numbers and plain text format real numbers. The interface unit for the fully homomorphic encryption chip can complete arithmetic operation, relation comparison operation and logical operation under encryption and can guarantee information safety.
Owner:HUAZHONG UNIV OF SCI & TECH
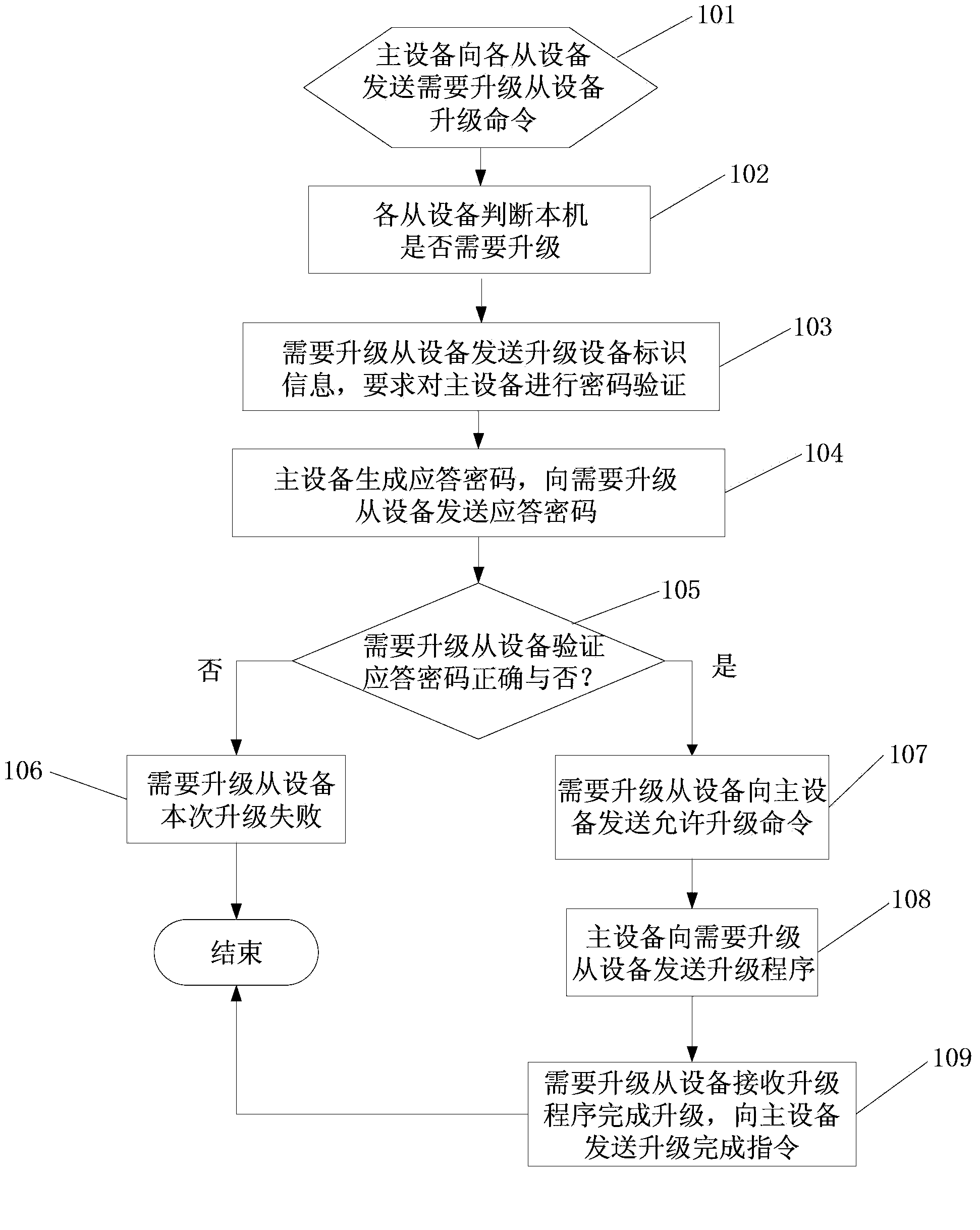
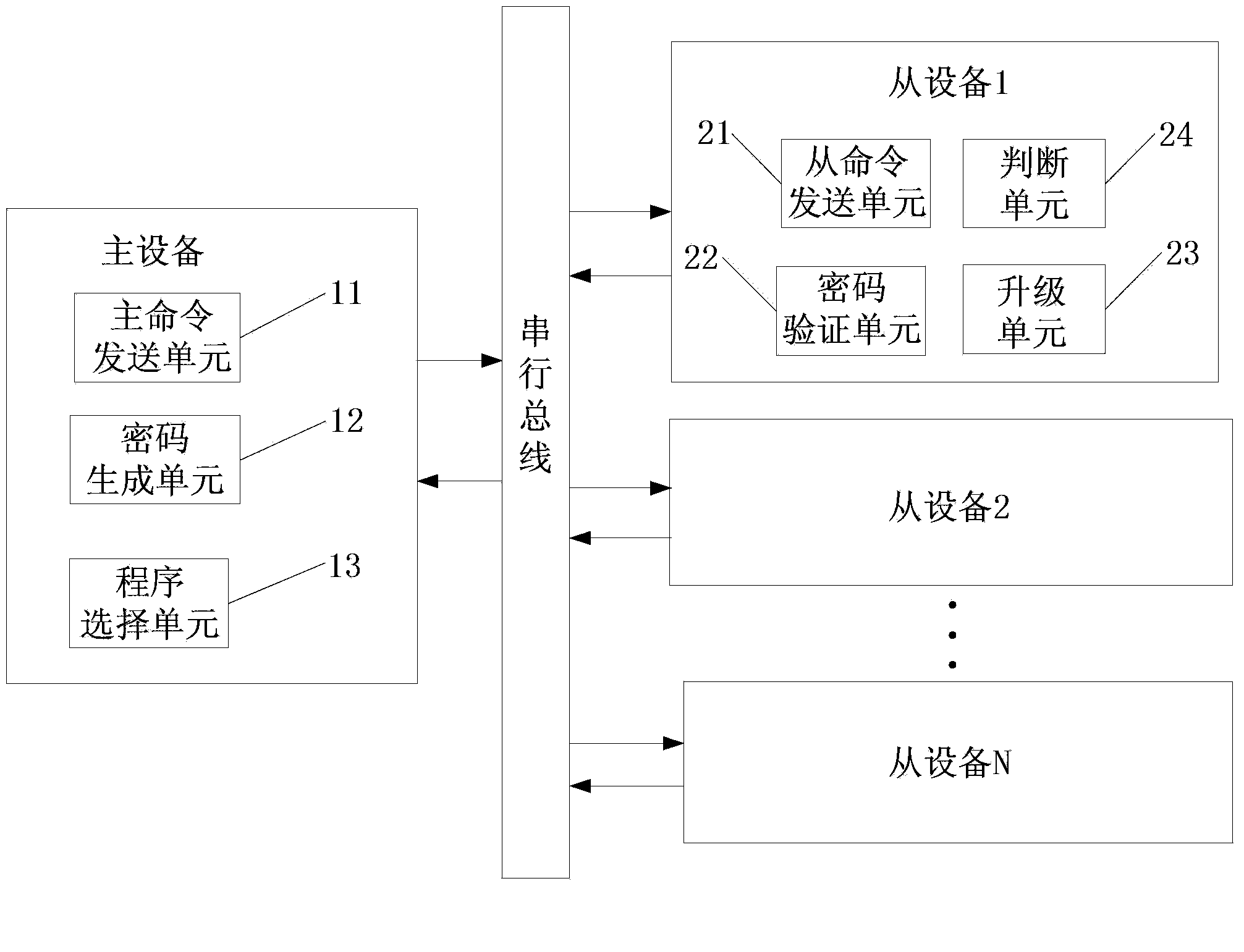
Upgrading method and device of multiple single-chip microcomputers based on serial buses
ActiveCN103838591AImplement security protectionReduce complexityDigital data authenticationProgram loading/initiatingMicrocomputerMicrocontroller
The invention provides an upgrading method and device of multiple single-chip microcomputers based on serial buses, and belongs to the technical field of on-line grading of the single-chip microcomputers. The method comprises the steps that a main device is connected with single-chip microcomputer auxiliary devices through the series buses; the main device sends an upgrading instruction of single-chip microcomputer auxiliary devices needing to be upgraded to the single-chip microcomputer auxiliary devices; the single-chip microcomputer auxiliary devices needing to be upgraded send a password verification requirement instruction to the main device; the main device sends a response password to the single-chip microcomputer auxiliary devices needing to be upgraded; the single-chip microcomputer auxiliary devices needing to be upgraded verify the response password; the main device sends an upgrading program to the single-chip microcomputer auxiliary devices needing to be upgraded; the single-chip microcomputer auxiliary devices needing to be upgraded receive the upgrading program and are upgraded. The upgrading method and device overcome the shortcoming that different application programs are manually ungraded for multiple single-chip microcomputer intelligent devices one by one, a main single-chip microcomputer is not required in the upgrading process, hardware complexity is reduced, a password verification program is added in the upgrading part, and safety protection of the single-chip microcomputers is achieved.
Owner:HAIER GRP CORP +1
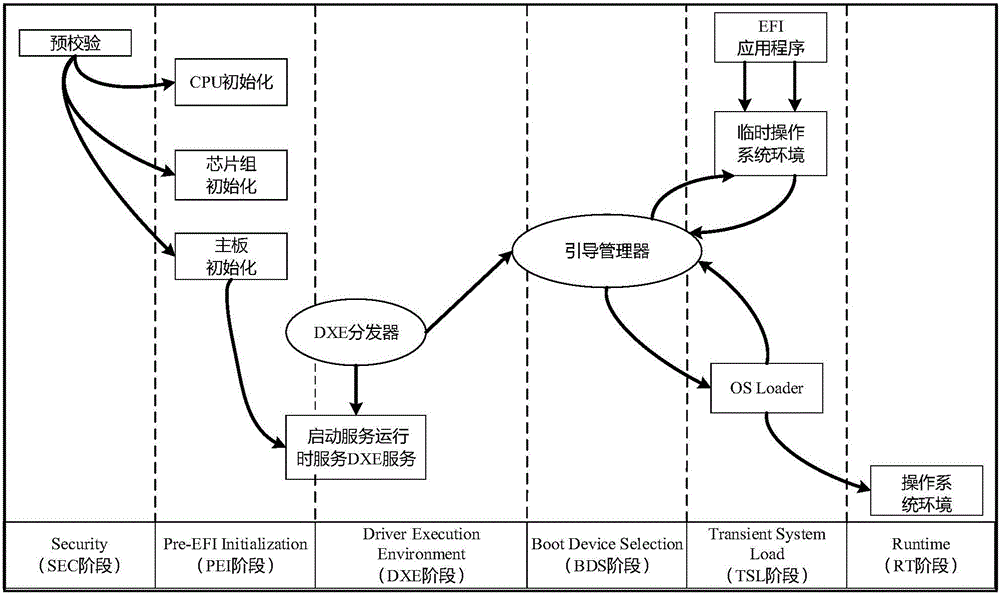
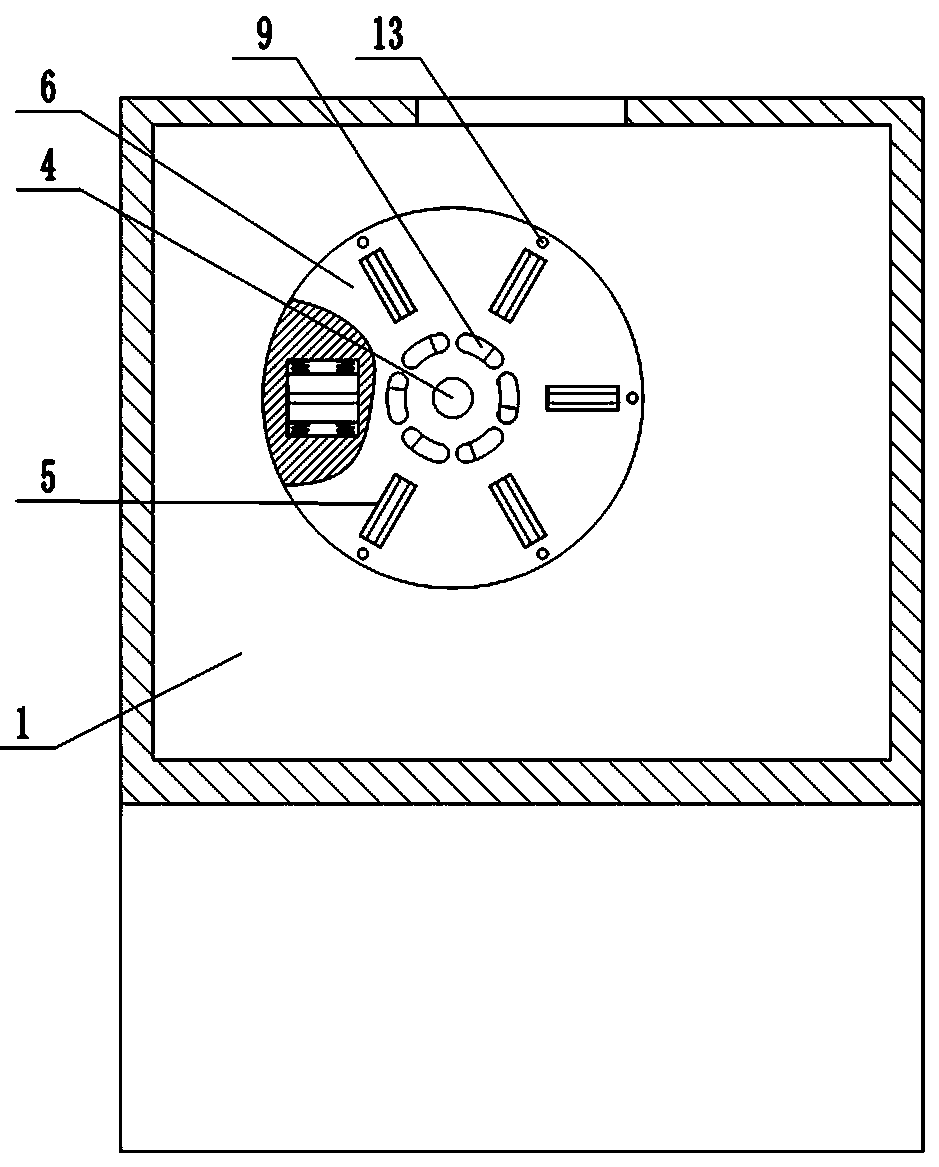
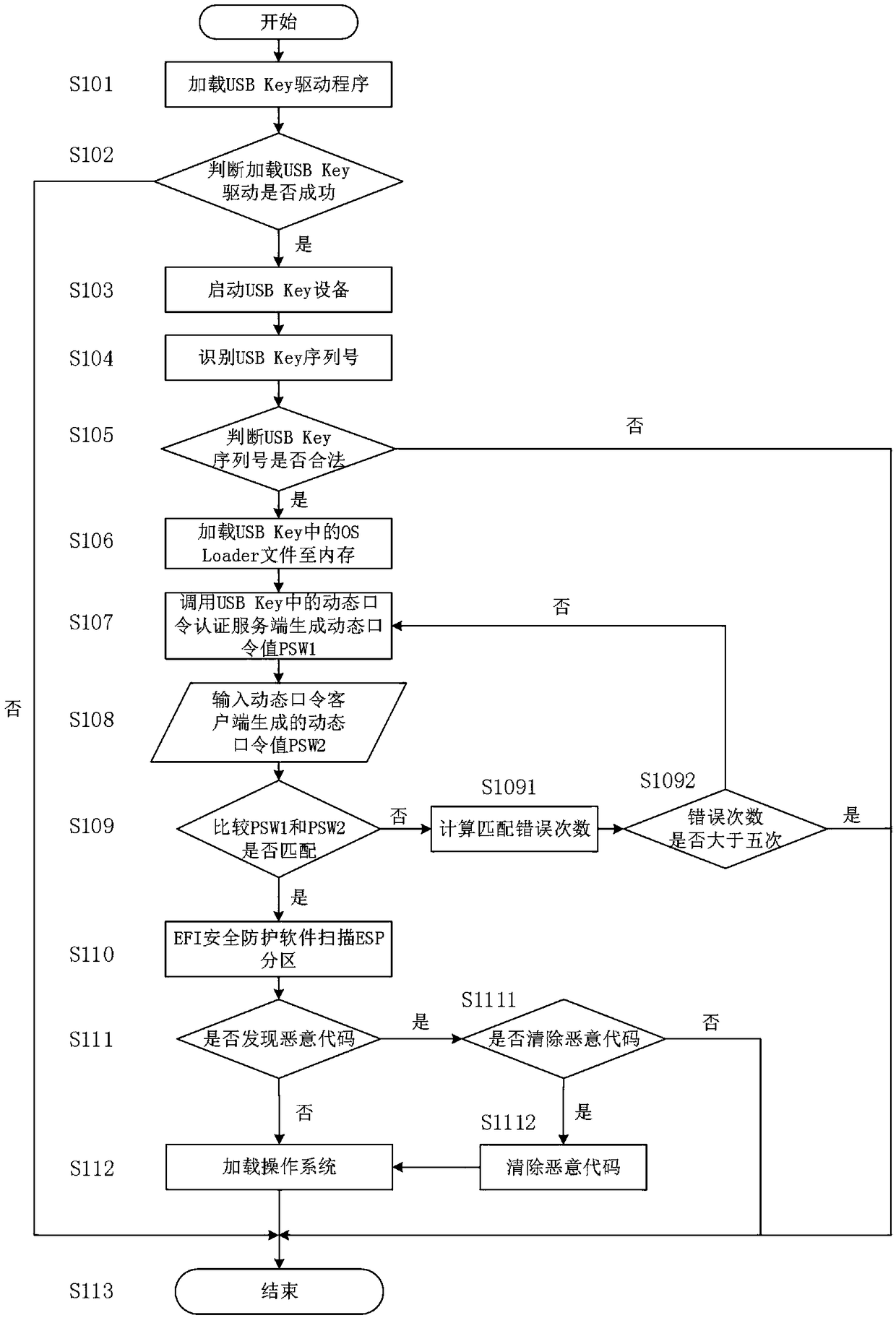
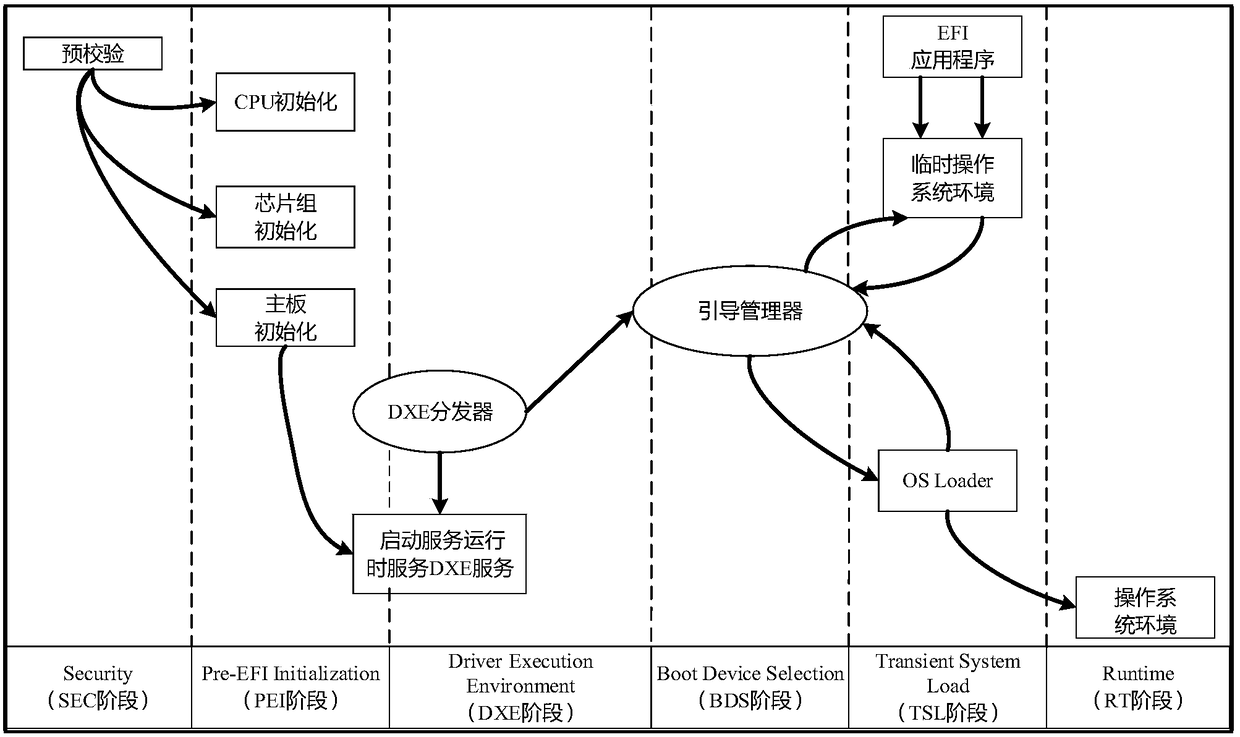
Computer security startup protection method on basis of UEFI (Unified Extensible Firmware Interface)
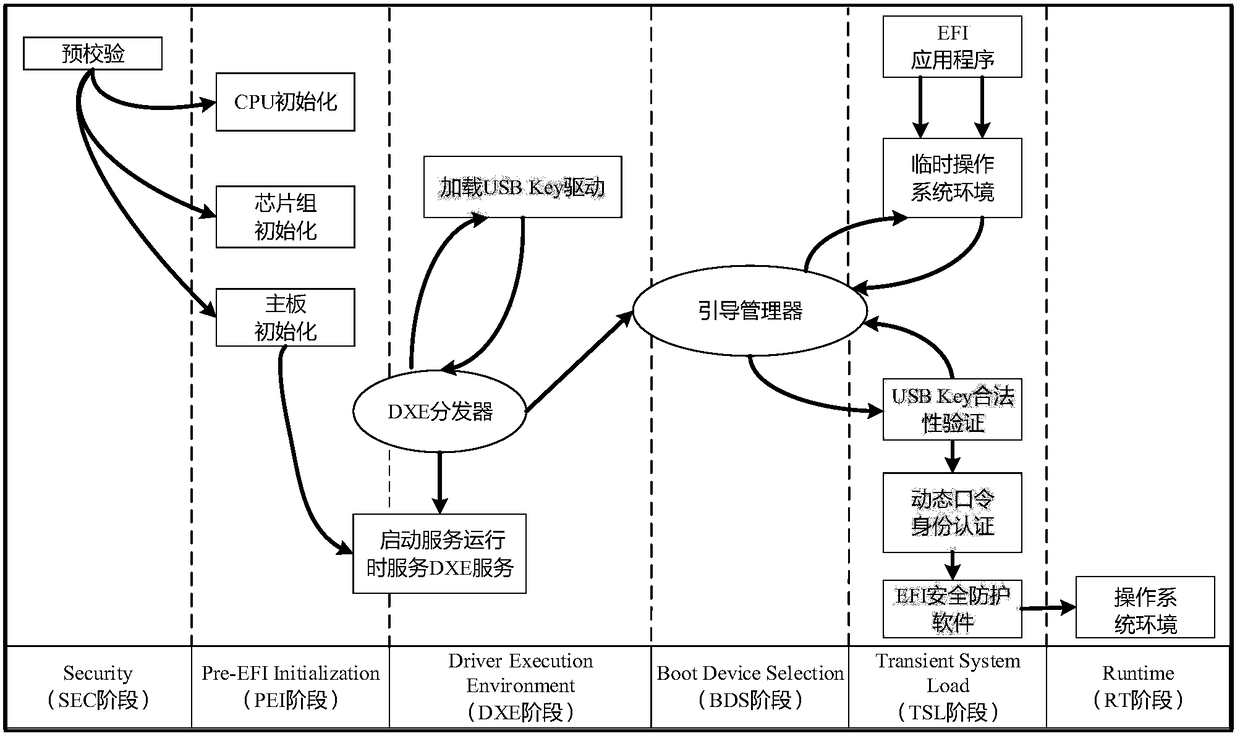
InactiveCN105825131AImplement security protectionPrevent illegal extraction and tamperingInternal/peripheral component protectionDigital data authenticationCritical systemUnified Extensible Firmware Interface
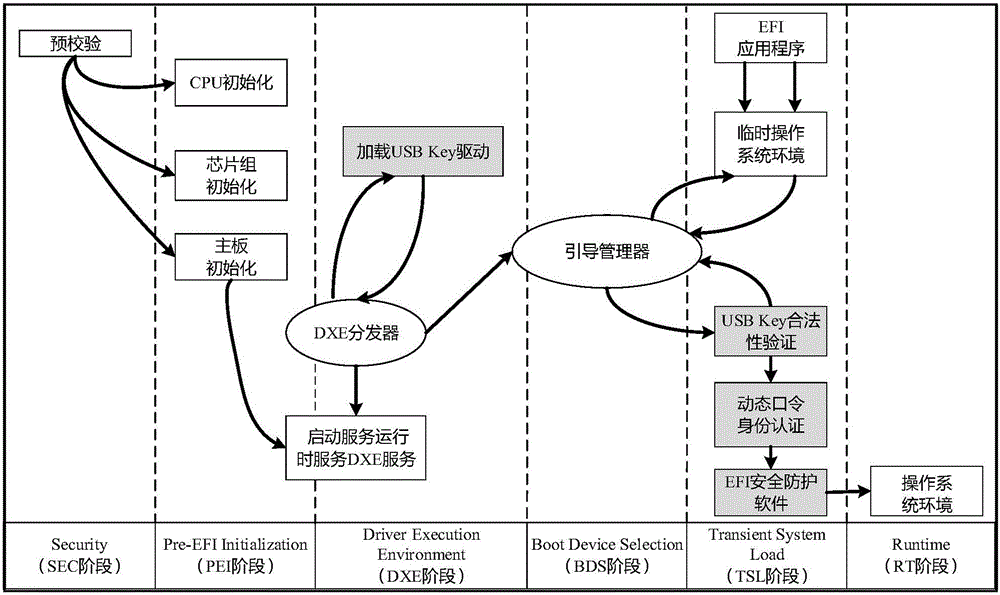
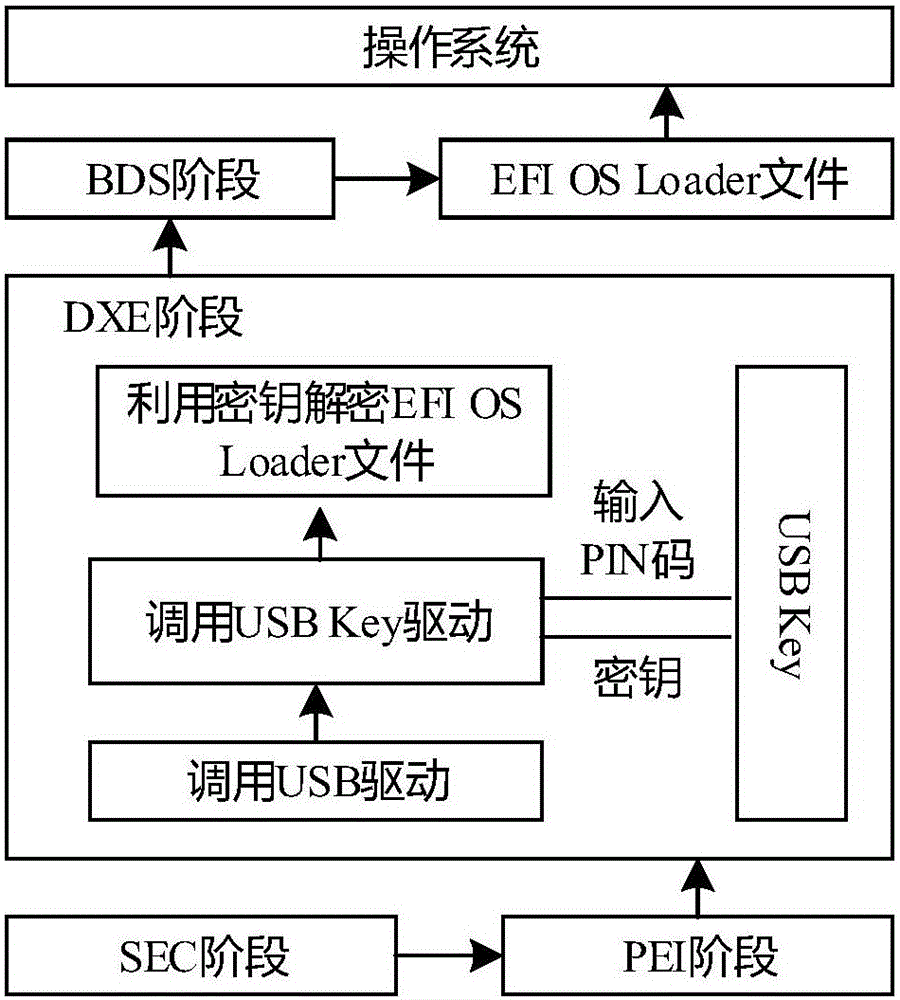
The invention discloses a computer security startup protection method on the basis of a UEFI (Unified Extensible Firmware Interface). The method comprises the following steps of enabling the UEFI to load a USB (universal serial bus) Key driving program in a DXE (Driver Extension Environment) stage, wherein the operation of whether to load the driving program successfully or not can influence to guide a manager to identify USB Key hardware in a BDS (Boot Device Selection) stage; in the BDS stage, guiding the manager to identify the USB Key hardware, and starting USB Key equipment; in a TSL (Transient System Load) stage, verifying a USB Key serial number, loading an OS loader file in a USB Key to a memory, then calling a dynamic password authentication server in the USB Key to perform secondary authentication, finally performing malicious code scanning on an ESP (EFI system partition) partition by means of calling EFI (Extensible Firmware Interface) safety protection software, preventing a key system file in the ESP partition from being invaded, and guaranteeing the security startup of a computer. The method disclosed by the invention has the advantages that the security of a computer startup procedure is enhanced in a manner of combining software and hardware on the premise of not affecting the normal startup of the computer.
Owner:GUANGDONG UNIV OF TECH
Infrared safety protection alarm device
InactiveCN102930681AImprove interchangeabilityQuick responseBurglar alarmTelecommunicationsInfrared safety
The invention relates to the technical field of safety protection and provides an infrared safety protection alarm device. The device comprises an infrared transmitting circuit and an infrared receiving alarm circuit. The device disclosed by the invention is used for the technical field of safety protection.
Owner:成都江法科技有限公司
Tree barrier clearing aerial robot provided with rope suspended tools
PendingCN108423175AAvoid contactImprove work efficiencyAircraft componentsCuttersShortest distanceAttitude control
The invention discloses a tree barrier clearing aerial robot provided with rope suspended tools. The aerial robot comprises platform supports and operating tools, wherein the platform supports are symmetrically connected to a body, multiple rotor assemblies are connected to the platform supports, the bottom of the body is connected to a tool frame through a rope, tool motors are fixedly connectedto the tool frame, and output shafts of the tool motors are connected with the operating tools. The rotor assemblies and the naturally suspended horizontal operating tools connected with the rope aremounted on the body, the robot is suitable for performing 'haircut' type large-area rapid clearing from the top of a tree barrier from top to bottom or from one side of the tree barrier from outside to inside, is high in operation efficiency, avoids high-voltage power transmission lines in the position where an operator can contact the tree barrier in a short distance and is safer to operate, theclearing operation efficiency can be effectively improved, and the operation risk is reduced; the flexible rope is used for suspending the tools, vibration and impact of the operating tools are automatically isolated, and the attitude control stability of the aerial robot is effectively improved.
Owner:南京太司德智能科技有限公司
Rotary roller elevator capable of achieving stable transmission
PendingCN113830490AGuarantee stabilityConvenient automatic feedingCleaningLifting framesRotary stageControl engineering
The invention discloses a rotary roller elevator capable of achieving stable transmission, which comprises a base; a rotary table rotating around a fixed axis is arranged on the upper surface of the base; a mounting platform is fixedly connected to the upper surface of the rotary table; limiting columns are fixedly connected to the four corners of the upper surface of the mounting platform; a lifting platform is arranged directly above the limiting columns; guide rails are symmetrically arranged on the upper surface of the lifting platform; a conveying platform is arranged on the guide rails; a feeding mechanism is arranged on the conveying platform, and the feeding mechanism comprises a plurality of eccentric rollers I rotating around a fixed axis on the inner wall of the conveying platform, and output shafts of the eccentric rollers I penetrate through the outer wall of the conveying platform and are fixedly connected with gears I; toothed plates I meshed with the gears I are arranged at the bottoms of the gears I; an inclined plate is fixedly mounted on one side of each limiting column; and push rods for feeding of the eccentric rollers I are symmetrically arranged on the side, close to the inclined plate, of the conveying platform. The rotary roller elevator capable of achieving the stable transmission provided by the invention has the advantages of being convenient to feed, safe and stable, and the problems in the background technology are solved.
Owner:江苏历漠智能装备有限公司
Ultrathin vehicle-mounted magnetic suspension flywheel battery and working method thereof
ActiveCN113422467AAxially takes up little spaceHighly integratedElectric machinesMechanical energy handlingMagnetic bearingElectrical battery
The invention discloses an ultrathin vehicle-mounted magnetic suspension flywheel battery for an electric vehicle, and a working method thereof. A motor bracket, an axial magnetic flux motor, a flywheel, an inner stator of a five-degree-of-freedom magnetic bearing, a coil and a permanent magnet are coaxially arranged in a shell from top to bottom, and the flywheel consists of an upper layer, a middle layer and a lower layer which are continuous; an upper annular groove is formed in the middle of the upper annular layer of the upper flywheel, the axial flux motor is placed in the upper annular groove, and an annular inner groove, a middle annular cavity and a lower annular groove are communicated and jointly used for placing the inner stator, the coil and the permanent magnet of the five-degree-of-freedom magnetic bearing; and the five-degree-of-freedom magnetic bearing comprises an axial magnetic bearing, a repulsion magnetic bearing, a torsion magnetic bearing and a radial spherical magnetic bearing from inside to outside. The mode that magnetic bearings with different properties are reused is adopted, advantage complementation is achieved, the bearing capacity and control precision of magnetic bearing supporting can be improved, the stability of a flywheel is remarkably improved, and the problem that the loss of a control coil is large due to complex working conditions can be effectively solved.
Owner:JIANGSU UNIV
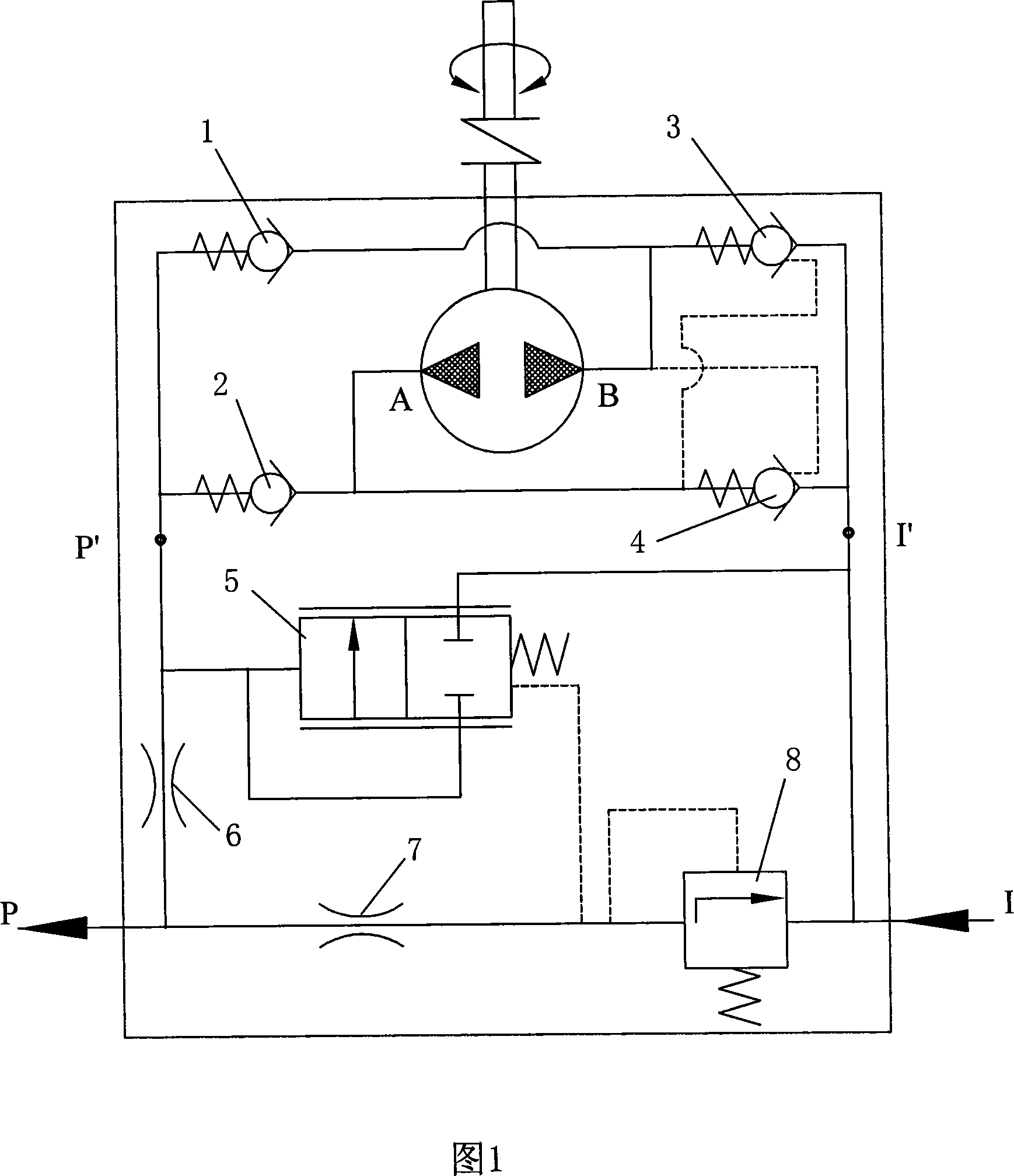
Bidirectional constant flux gear pump
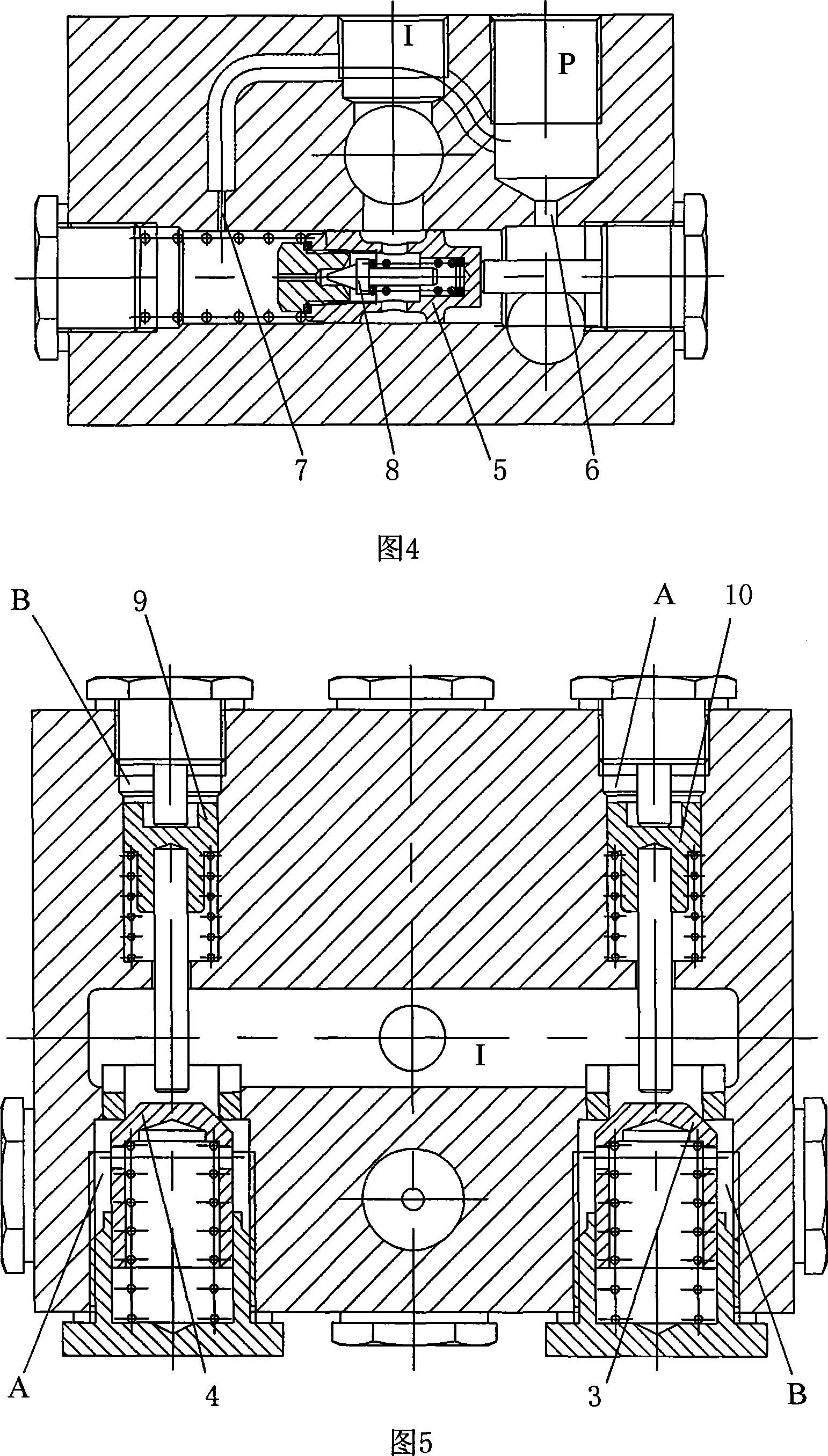
InactiveCN101196189ARealize two-way rotationSmooth oil absorptionRotary piston pumpsRotary piston liquid enginesGear pumpHydraulic pump
The invention provides a double direction constant flow gear pump, which relates to the technical field of double direction rotation of hydraulic pump. The gear pump mainly comprises a double direction constant flow control device, a general oil pump inlet (I), a general oil pump outlet (P), an oil pump inlet (I'), an oil pump outlet (P'), a normative hydraulic pump oil port (A) and a normative hydraulic pump oil port (B). The double direction constant flow control device comprises a one-way valve (1), a one-way valve (2), a hydraulic control one-way valve (3), a hydraulic control one-way valve (4), a slide valve (5), a flow control orifice (6), a pressure control orifice (7), a cone valve (8), a hydraulic control piston (9) and a hydraulic control piston (10). The invention has the advantages that: when the gear pump rotates in two direction, the constant flow gear pump can keep the position of the oil inlet and oil outlet unchanged, at the same time, maintain constant output flow and realize safe restriction for the output pressure.
Owner:孙玉清 +1
A wire end pulling method used for tightly hanging wire construction of transmission lines
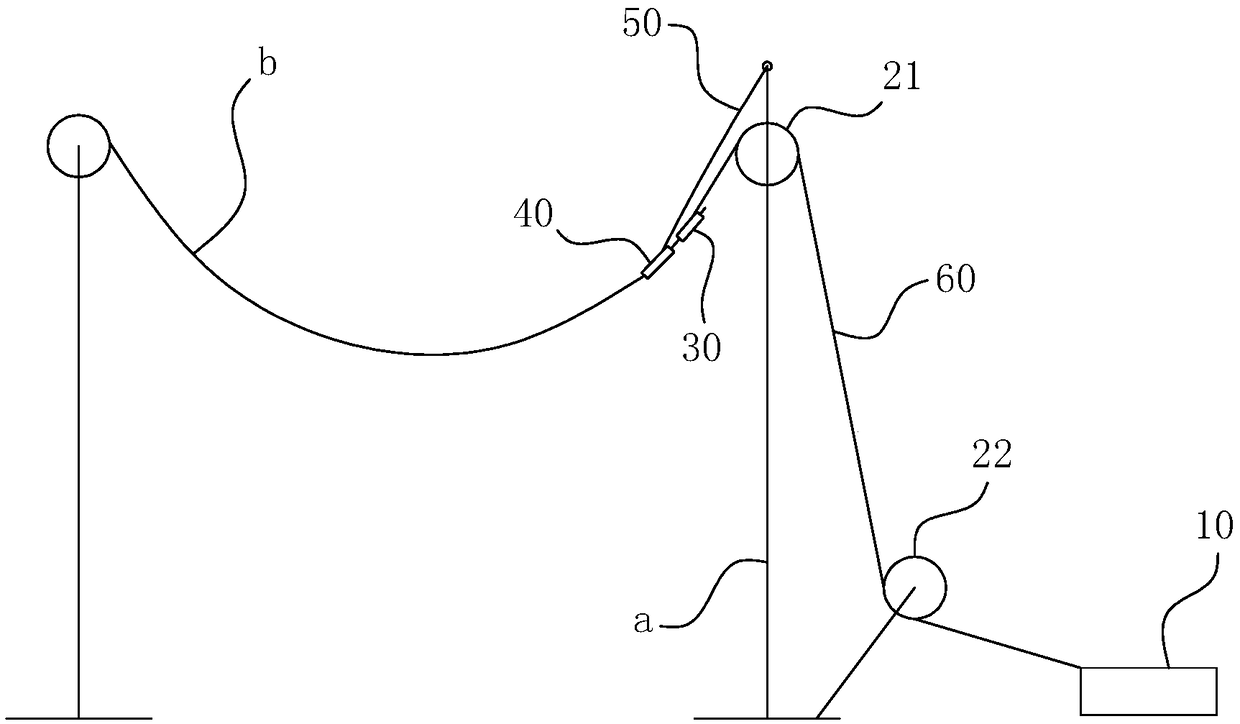
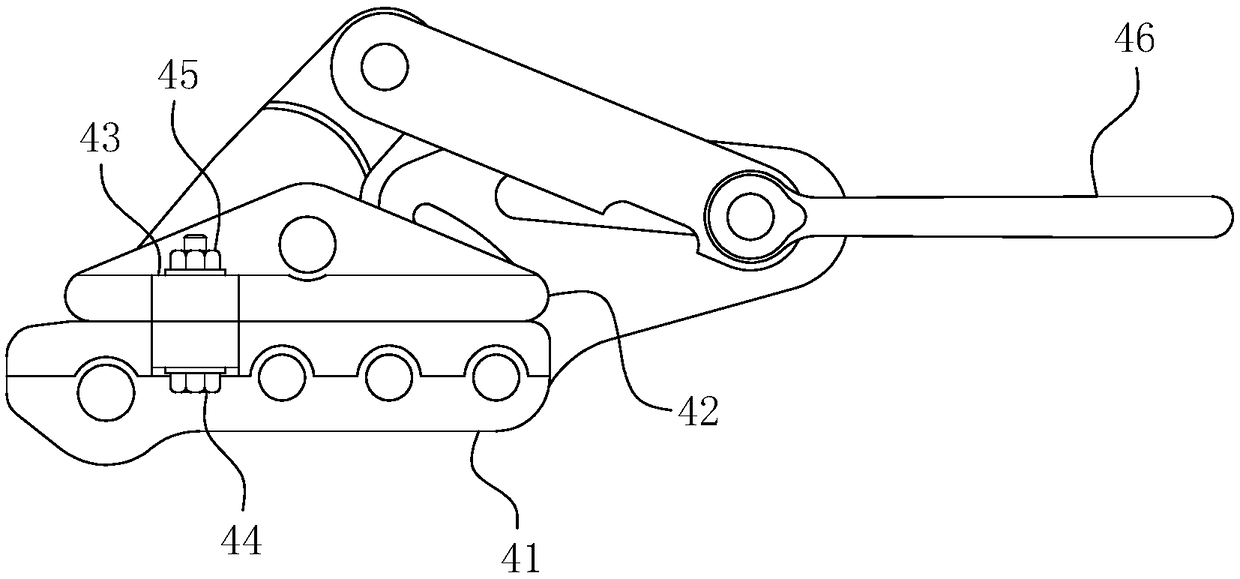
ActiveCN109167302ASolve the problem of slipping and falling off the running lineImplement security protectionApparatus for overhead lines/cablesTraction systemArchitectural engineering
The invention belongs to the technical field of transmission line engineering construction, in particular to a wire end pulling method used for transmission line hanging line construction. The invention comprises the following steps: 1) arranging a winch; 2) arrange a steering block; 3) arrange a main wire card device and a sub wire card device; 4) arrange a hauling rope; 5), arrange that auxiliary rope, finish the wire tightening and hang operation. The invention can avoid the wire running because of the anchor of the wire tightening and hanging traction system or the loosening of the jaw ofthe wire clamp in the wire pulling and placing process, so as to ensure the normal construction efficiency and improve the construction safety, thereby facilitating the effective development of the wire tightening and hanging construction operation of the transmission line.
Owner:ANHUI ELECTRIC POWER TRANSMISSION & TRANSFORMATION ENG +1
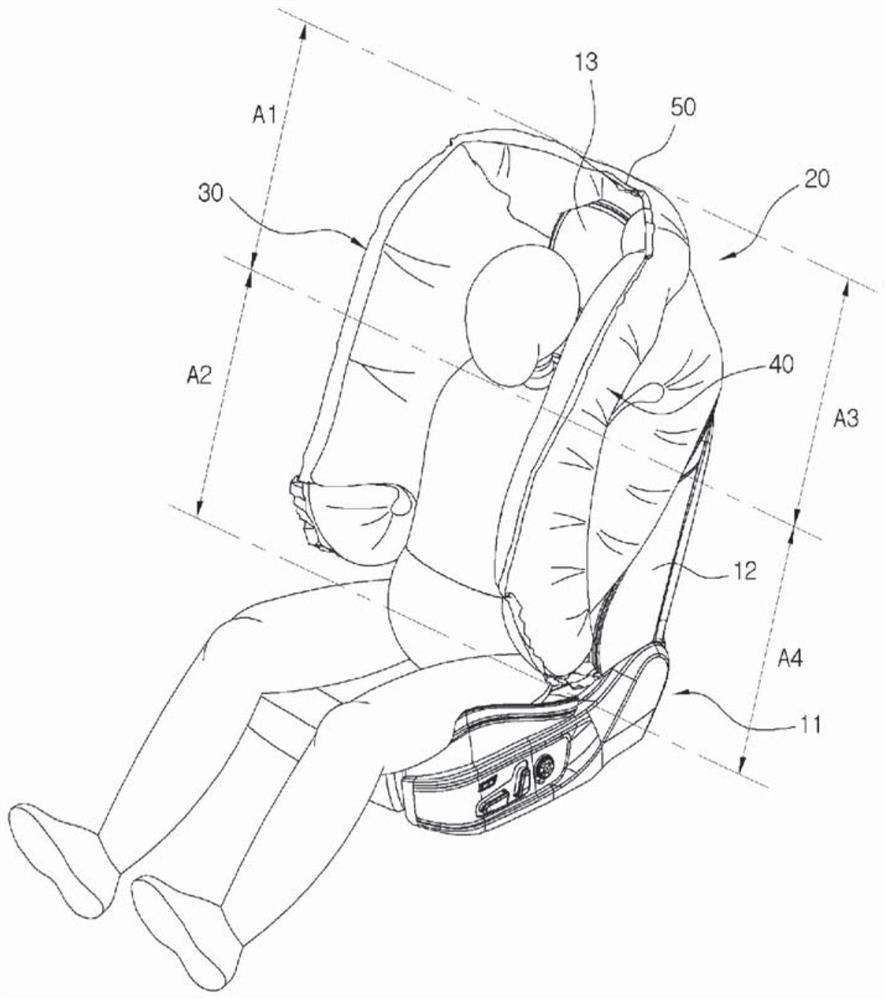
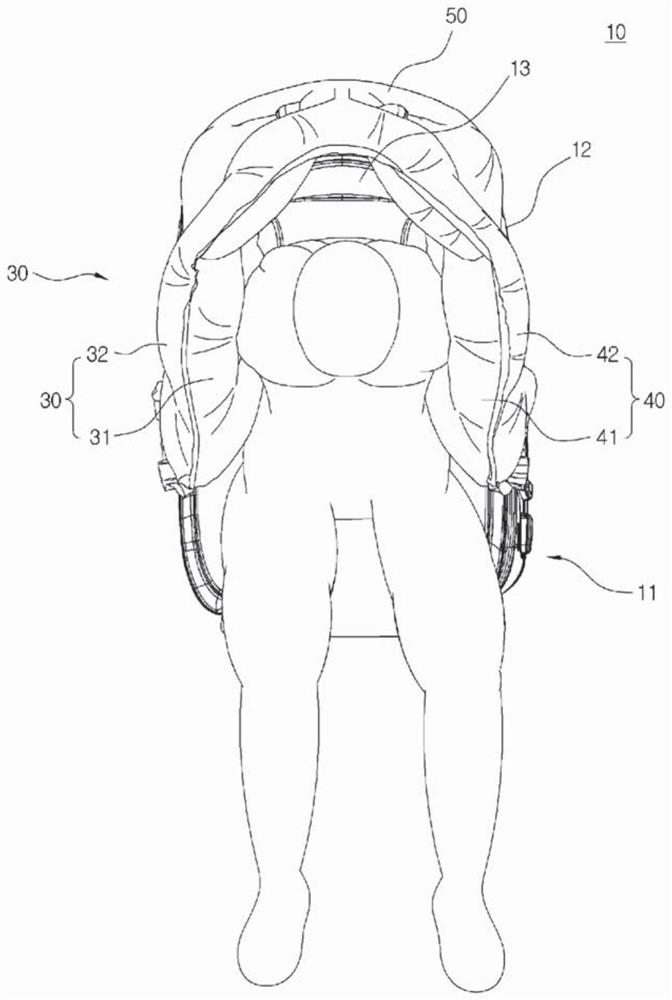
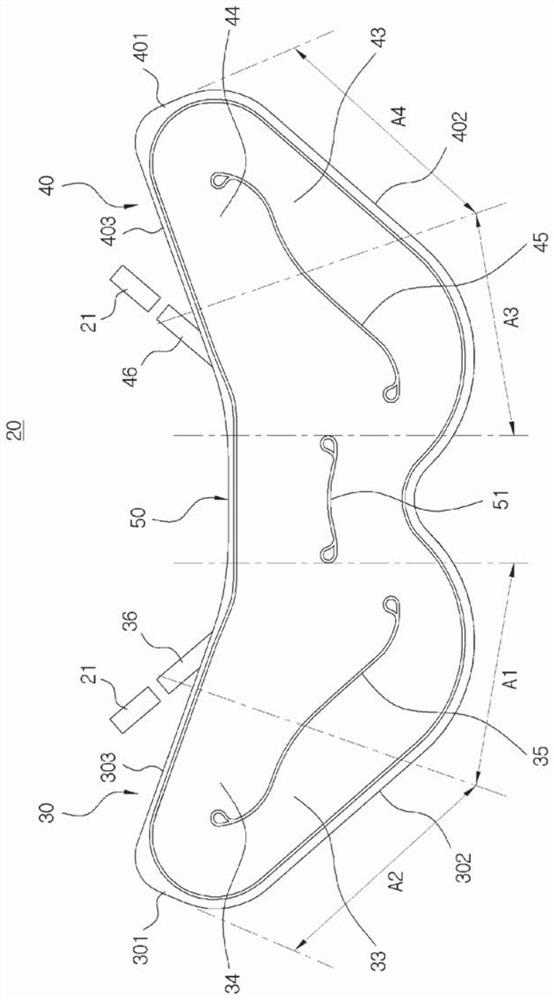
Airbag device for vehicle
PendingCN112313121AImplement security protectionProtect the left sidePedestrian/occupant safety arrangementAirbagControl theory
The present invention relates to an airbag device for a vehicle. The airbag device comprises: an airbag cushion which is formed in a shawl shape and deployed toward both sides of a passenger so as towrap and restrain the entire upper body around both shoulders of the passenger when a vehicle collides; and an inflator for generating gas and supplying the gas to the airbag cushion in response to animpact detection signal when the vehicle collides. Accordingly, when a vehicle collides, the shawl-shaped airbag cushion installed on the back of a seat is inflated and deployed to restrain the bothsides and front area of the upper body of a passenger around both shoulders of the passenger, thereby safely protecting the passenger.
Owner:AUTOLIV DEV AB
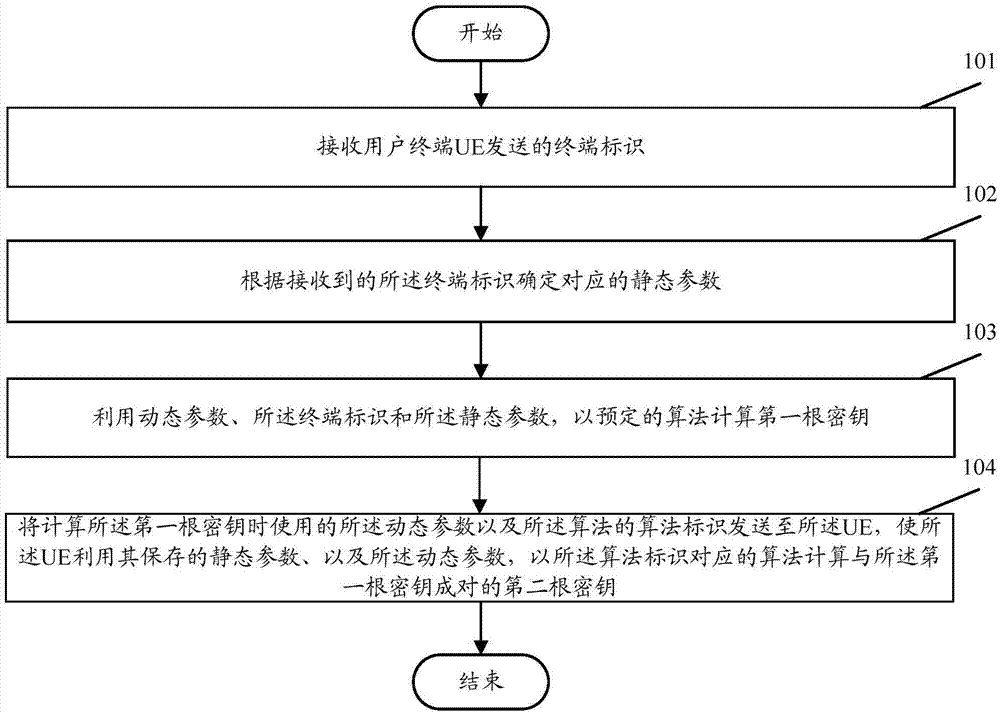
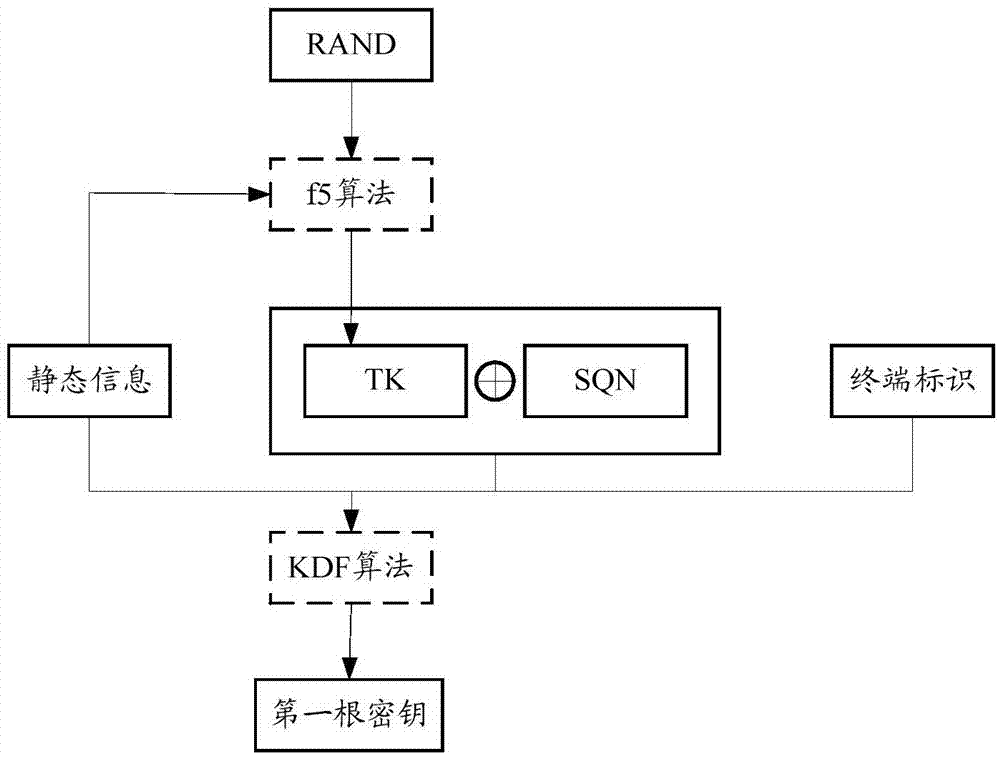
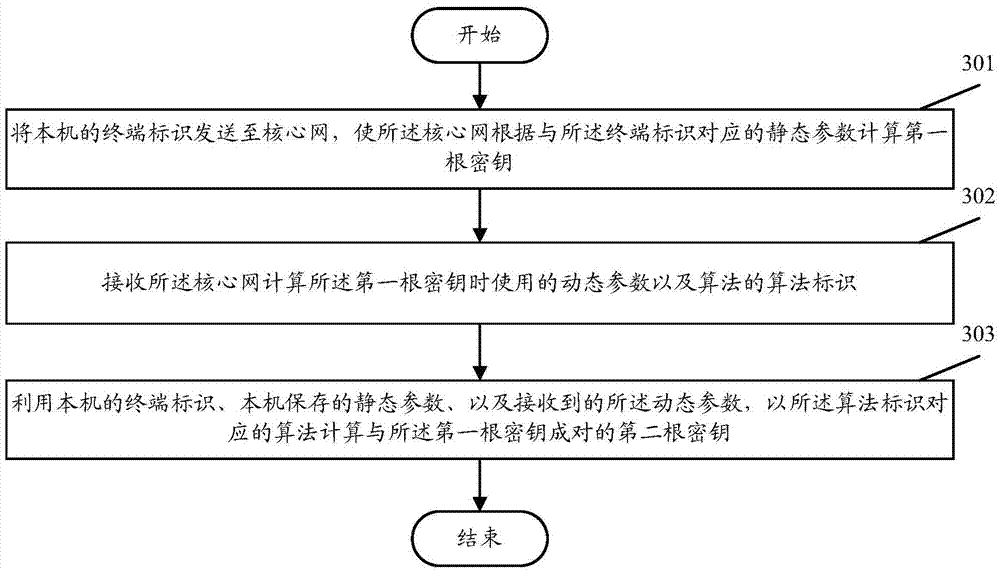
Dynamic root key generating method
The invention discloses a dynamic root key generating method. The method comprises the followings steps, executed in the core network, that a terminal identification is received from UE; a corresponding static parameter is determined according to the received terminal identification; a first root key is calculated in a predetermined algorithm by utilizing a dynamic parameter, the terminal identification and a static parameter; and the dynamic parameter used when the first root key is calculated and an algorithm identification of the algorithm are sent to the UE, so that the UE calculates a second root key paired with the first key in an algorithm corresponding to the algorithm identification by utilizing the stored static parameter, terminal identification and static parameter. According to the invention, the problem of secret key leakage caused by storing the secret key via software is overcome effectively, the safety of root key is protected, and the manual management and maintenance cost of the root key is reduced.
Owner:POTEVIO INFORMATION TECH
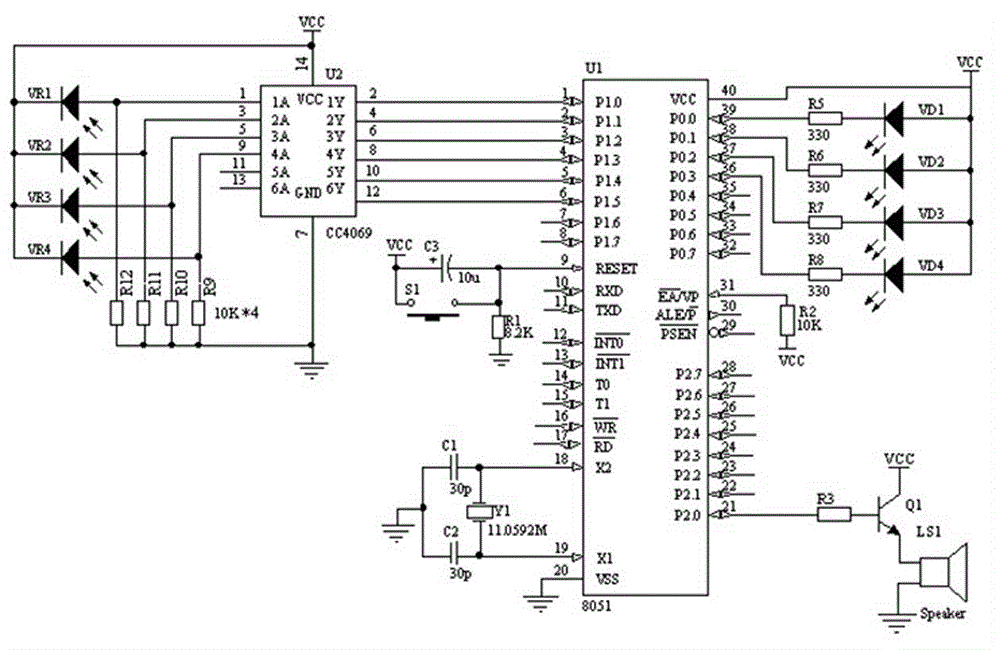
Infrared alarm device
The invention relates to the technical field of security, and provides an infrared alarm device which comprises an inverter CC4069, infrared receiving tubes from VR1 to VR5, infrared transmitting tubes from VD1 to VD4 and a single chip microcomputer. Pins from 1A to 4A of the inverter CC4069 are successively connected with the infrared transmitting tubes from VD1 to VD4. Pins from 1Y to 6Y of the inverter CC4069 are successively connected with pins from P1.0 to P1.5 of the single chip microcomputer. Pins from P0.0 to P0.3 of the single chip microcomputer are successively connected with the infrared receiving tubes from VR1 to VR5. A pin P2.0 of the single chip microcomputer is connected with a resistor R3. The resistor R3 is connected with a triode Q1. The resistor R3 is connected with the base of the triode Q1. The emitter of the triode Q1 is connected with one end of a loudspeaker, and the other end of the loudspeaker is grounded. The collector of the triode Q1 is connected with the positive pole of a power supply. RESET of the single chip microcomputer is connected with a reset circuit. The infrared alarm device provided by the invention has the advantages of good compatibility, fast response speed, strong anti-interference ability, simple peripheral circuit and small size, and carries out infrared transmitting directly through a transmitting module.
Owner:CHENGDU BOSSE INFORMATION TECH
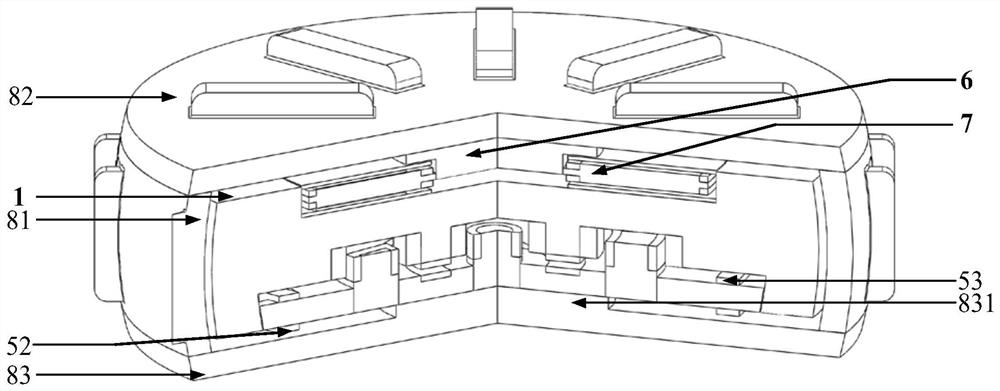
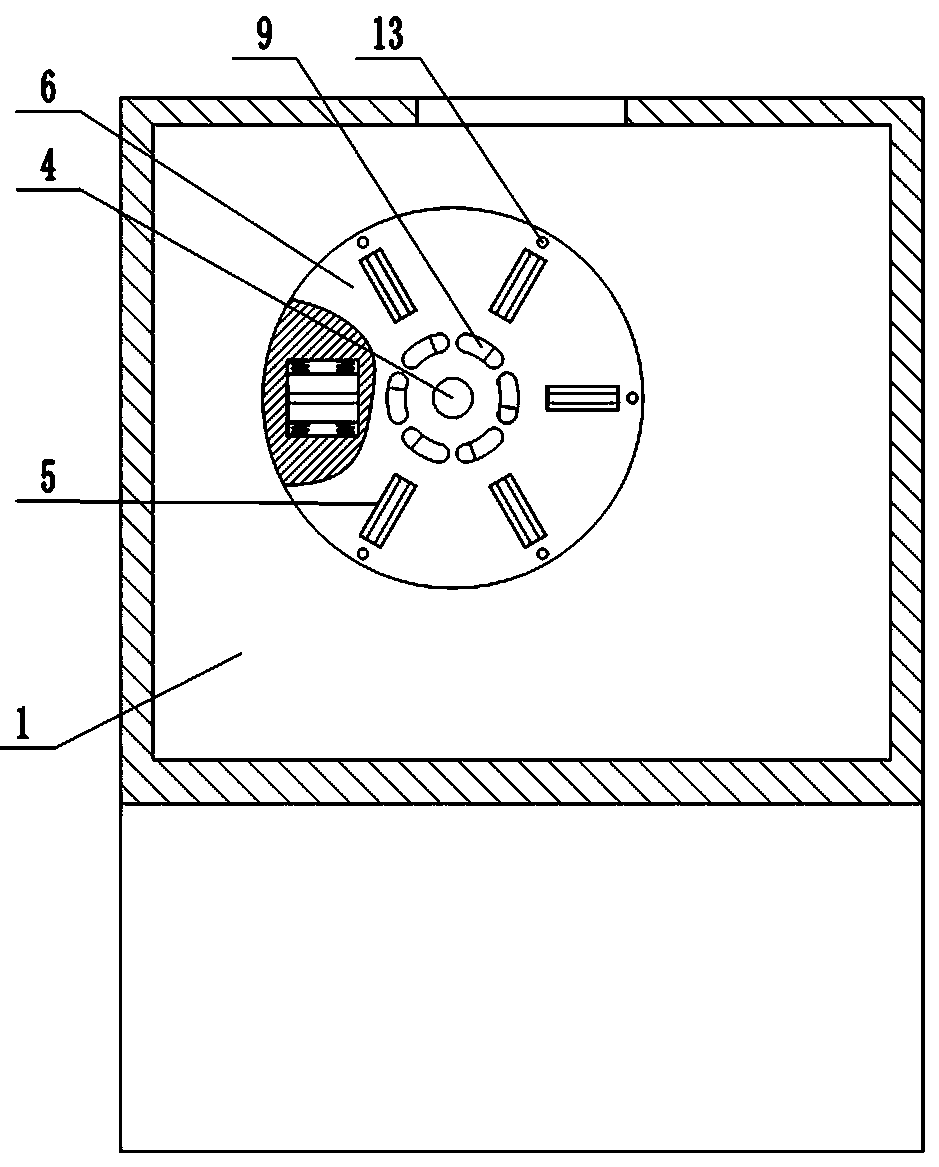
Security protection interface device for cloud computing platform
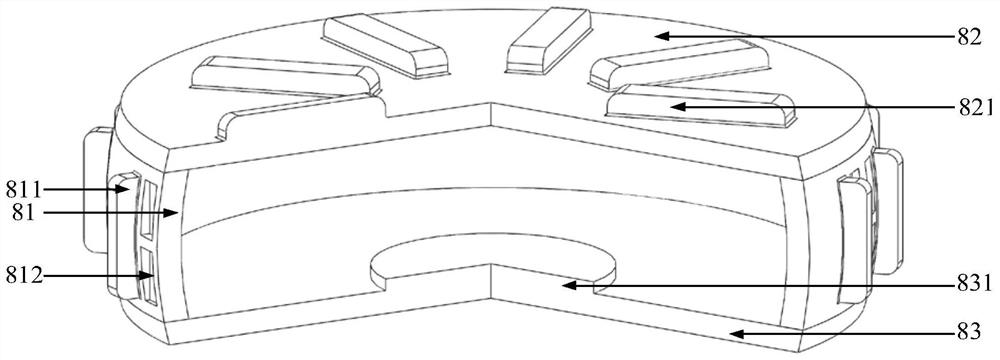
InactiveCN110990904BImplement security protectionPrevent copyingInternal/peripheral component protectionEngineeringStructural engineering
The invention provides a security protection interface device for a cloud computing platform. According to the security protection interface device, security assurance for an information platform canbe well improved. The security protection interface device comprises a machine body, a socket is arranged on machine body, a shield is arranged on the front side of the machine body; through holes areformed in the shield, a rotary disc is arranged in the shield, grooves are formed in the end surface of the rotary disc; a wedge-shaped baffle plate is mounted in each groove; first springs are connected between the wedge-shaped baffles and the grooves; one of the grooves is designed to be a communicating groove, and the other grooves are blind grooves; a wedge-shaped hole is formed in the end face of the rotary disc, a push rod is arranged on the shield, the push rod is pressed to drive the rotary disc to rotate unidirectionally through matching of the push rod and the wedge-shaped hole, a torsional spring is connected between the rotary disc and a base body, and the rotary disc can move forwards and backwards along a connecting shaft and can reset under the action of the torsional spring. According to the security protection interface device, the security protection of the computer platform interface can be well realized, and foreign persons are prevented from copying internal information.
Owner:HUANGHE S & T COLLEGE
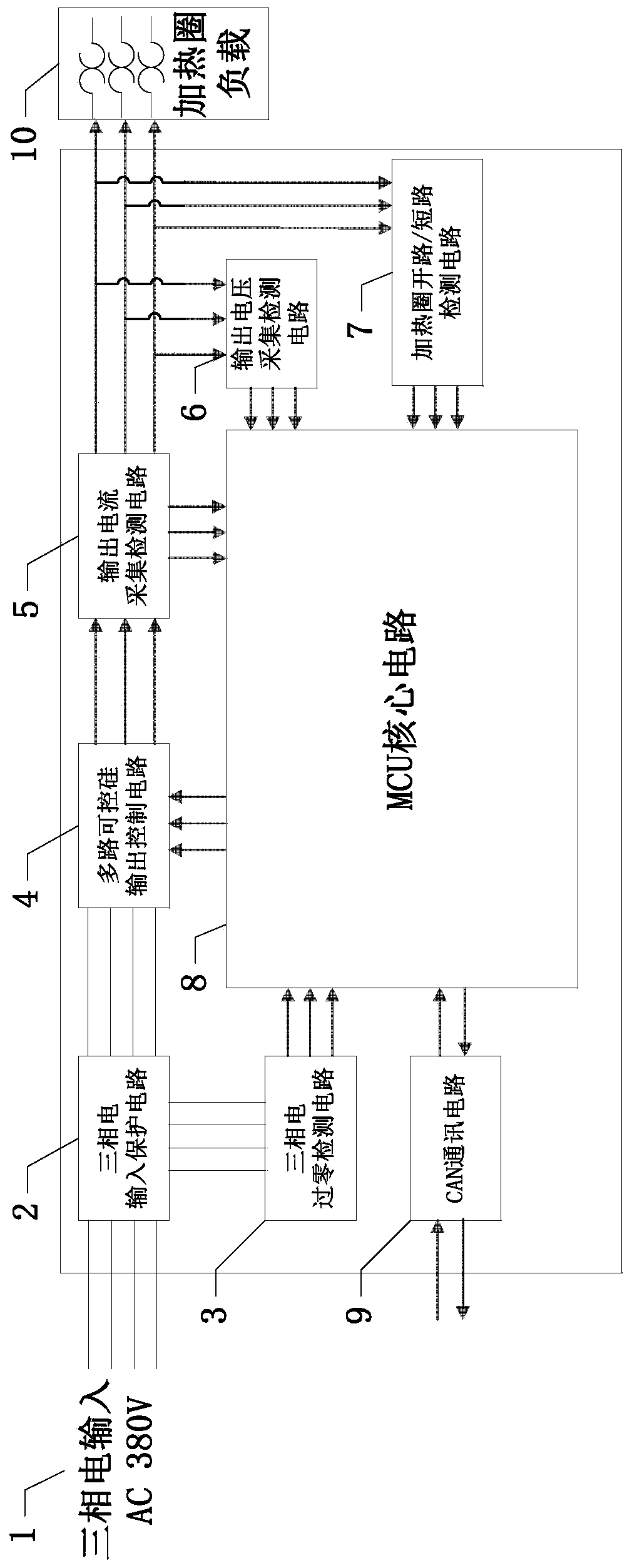
Hot runner three-phase current multichannel voltage control system and control method thereof
ActiveCN109933115AImplement security protectionRealize centralized controlProgramme controlComputer controlHot runnerThree-phase electric power
The invention relates to a hot runner three-phase current multichannel voltage control system, which comprises a three-phase current input end, a three-phase current input protection circuit, a three-phase current zero-crossing detection circuit, a multichannel thyristor output control circuit, an output current acquisition detection circuit, an output voltage acquisition detection circuit, a heating coil open / short circuit detection circuit, an MCU core circuit and a CAN communication circuit, wherein the three-phase current input protection circuit is connected with the three-phase current input end; the three-phase current input protection circuit is connected with the multichannel thyristor output control circuit and the three-phase current zero-crossing detection circuit; the three-phase current zero-crossing detection circuit is connected with the MCU core circuit, and a detection result can be sent to the MCU core circuit; the MCU core circuit is connected with the multichannelthyristor output control circuit, and output parameters are sent to the thyristor output control circuit; and the thyristor output control circuit is connected with a heating coil load.
Owner:广州捷克易自动化设备有限公司
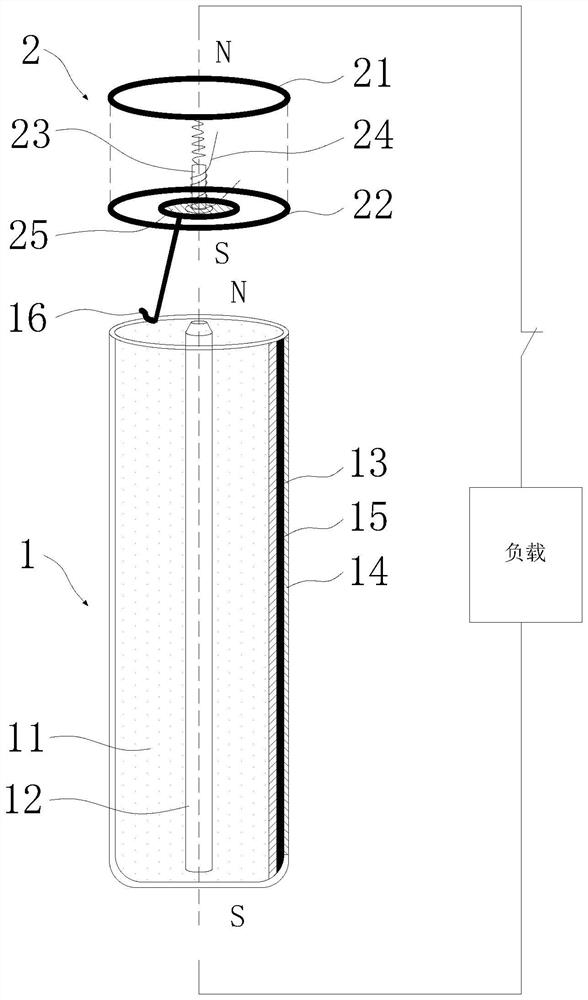
Lithium ion battery magnetic control switch and control method thereof
ActiveCN112530741AControl charge and dischargeImplement security protectionFinal product manufactureSecondary cells charging/dischargingElectrical batteryMagnetic poles
The invention relates to the technical field of battery magnetic control switches, and discloses a lithium ion battery magnetic control switch and a control method thereof. The lithium ion battery magnetic control switch comprises a lithium ion battery, the positive electrode end of the lithium ion battery is provided with a tab, and the tab of the positive electrode end is electrically connectedwith a switch cap which comprises a switch cap upper part and a switch cap lower part; and a conductive block is arranged at the lower part of the switch cap. A first iron core is inserted into a battery cell of the lithium ion battery, spiral current is generated during charging and discharging of the lithium ion battery, and a first magnetic field is formed. A second iron core is arranged between the switch cap upper portion and the switch cap lower portion, a wire winding is wound on the second iron core, and a second magnetic field is formed after the wire winding is powered on. The magnetic pole direction of the first magnetic field is determined by the spiral current flow direction, whether the second iron core is attracted to the conductive block or not is determined by controllingthe magnetic poles of the first magnetic field and the second magnetic field to be the same or different, charging and discharging of the lithium ion battery are controlled, and real-time protection is achieved.
Owner:SINOWATT DONGGUAN
Network information micro-sensing safety helmet
PendingCN110916281AImplement security protectionEasy to openHelmetsHelmet coversStructural engineeringVisor
The invention discloses a network information micro-sensing safety helmet. The network information micro-sensing safety helmet comprises a helmet body, a visor, two power supply pieces, a first rolling shaft buckle base, a second rolling shaft buckle base, an arc-shaped lengthened edge, an electric air bag and a pressure controller. The surface of one side of the helment body is connected with thefirst rolling shaft buckle base in a buckling manner; the surface of the other side of the helment body is connected with the second rolling shaft buckle base in a buckled mode. The helment body is connected to the surfaces of the two sides of the visor in a buckled mode through the first rolling shaft buckle base and the second rolling shaft buckle base. The surface of one side, far away from the helmet body, of the visor is fixedly connected with the arc-shaped lengthened edge; the electric air bag is arranged in the middle of the interior of the helmet body, a pressure controller is fixedly connected to the surface of the upper portion of the exterior of the helmet body, power supply pieces are arranged on the portions, located on the two sides of the visor, of the surface of the helmet body respectively, and a control wire of the pressure controller is connected with the power supply pieces and the electric air bag.
Owner:徐州梦创信息科技有限公司
Water-control type water-return secondary stop safety protector for hydraulic compressor
InactiveCN101551056ASolve potential safety hazardsIncrease the reliability of security protectionEngineering safety devicesAutomatic controlEngineering
The invention discloses a water-control type water-return secondary stop safety protector for a hydraulic compressor. A high-pressure electromagnetic valve is serially arranged on a water return pipeline of a distributor of the hydraulic compressor and is respectively in a water-path opening state and a water-path cut-off state when the high-pressure electromagnetic valve is electrified or power off. The power supply input end of the high-pressure electromagnetic valve is connected with a power supply wire after being connected with a normal-open switch of a corresponding intermediate relay in series, and an automatic control circuit of the intermediate relay comprises a travel switch arranged on an operating disc of the hydraulic compressor. The intermediate relay is a normal-open relay, and the travel switch is respectively in a switched-on state and a switched-off state when the operating disc is not zeroized. In the normal work of the hydraulic compressor, the operating disc is not in the zeroized state, the high-pressure electromagnetic valve is electrified, and the water path is in an open state, or else, the water path is in a cut-off state to prevent the accident. The invention realizes the secondary protection of the hydraulic compressor.
Owner:SICHUAN AEROSPACE LONG MARCH EQUIP MFG CO LTD
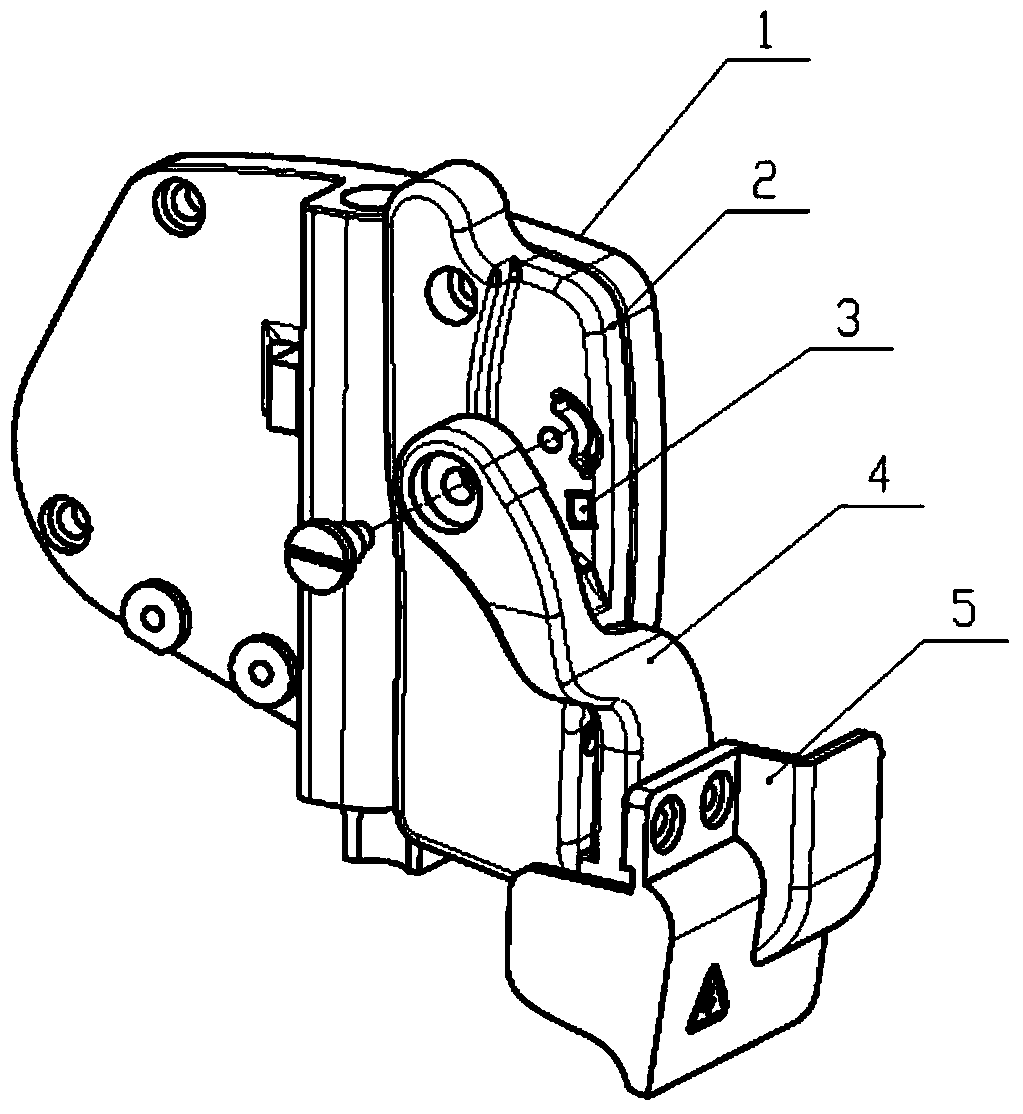
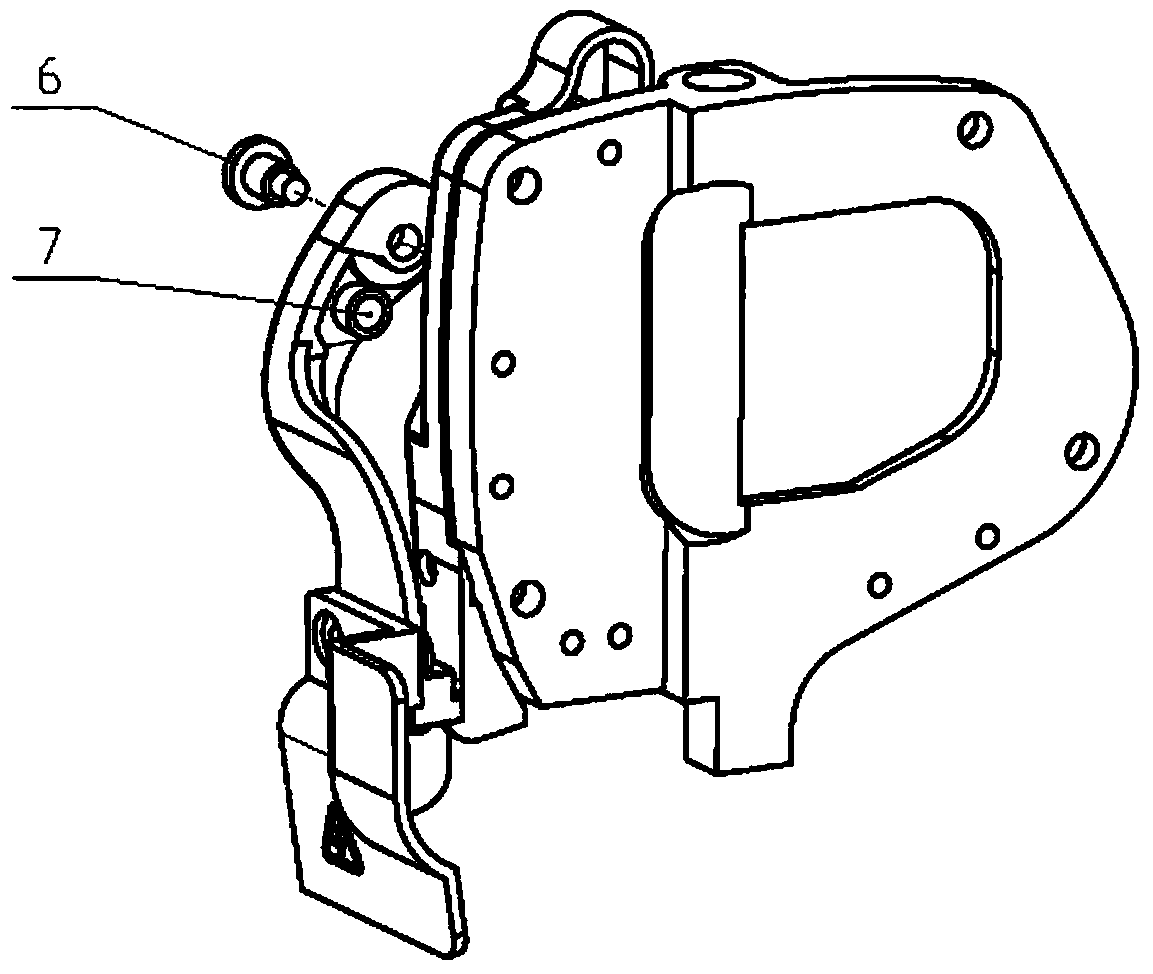
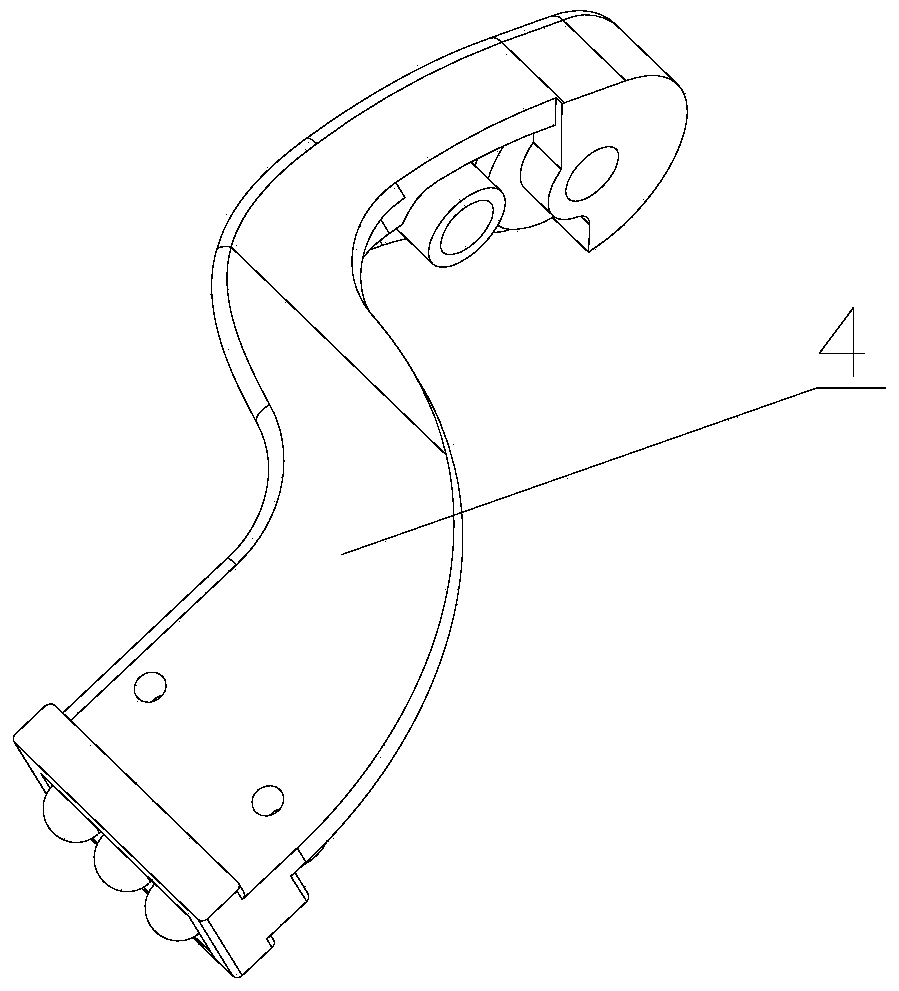
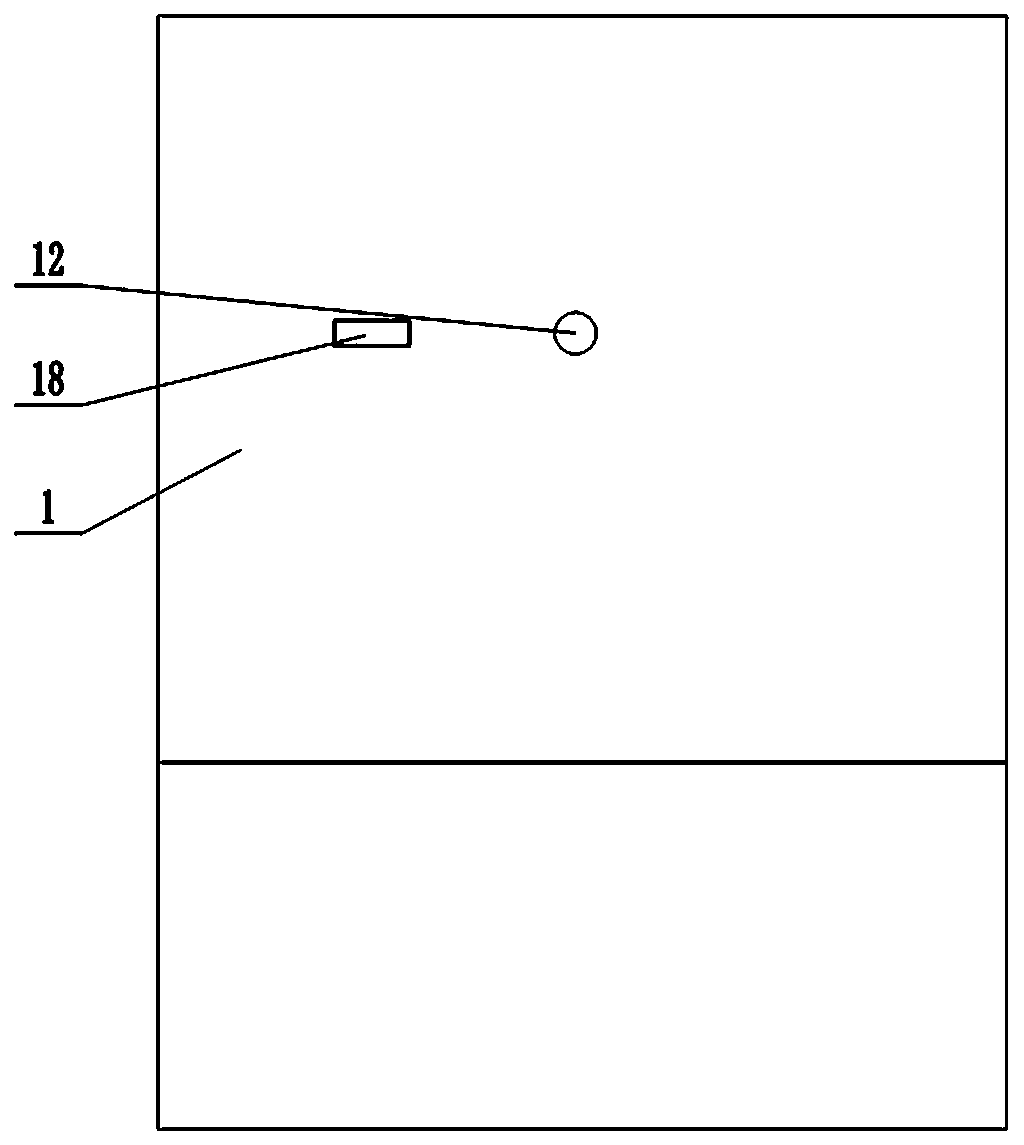
Safety switch structure for cup seaming machine needle bar protection cover
The invention provides a safety switch structure for a cup seaming machine needle bar protection cover. The safety switch structure comprises a shell and a protection cover for protecting a thread guide bar and a needle bar, the protection cover is rotatably connected onto the shell through a protection cover wrench, a safety switch for prohibiting start of a cup seaming machine when the protection cover is opened is arranged between the protection cover wrench and the shell and comprises a sensor and a magnet, the sensor is provided with a Hall switch element and corresponds to the magnet, and the sensor and the magnet are arranged on opposite surfaces of the shell and the protection cover wrench respectively, or arranged on opposite surfaces of the protection cover wrench and the shell respectively. The Hall sensing safety switch is arranged between the protection cover wrench and the shell, so that a protection function is started when the needle bar protection cover is opened. Stability of the Hall safety switch cannot be affected by external environments, the cup seaming machine cannot be started even if in misoperation when maintainers perform threading and change needles, personal injury of the maintainers is avoided, and damage to the machine is prevented.
Owner:JACK SEWING MASCH CO LTD
Security protection interface device for cloud computing platform
InactiveCN110990904AImplement security protectionPrevent copyingInternal/peripheral component protectionStructural engineeringInterface (computing)
The invention provides a security protection interface device for a cloud computing platform. According to the security protection interface device, security assurance for an information platform canbe well improved. The security protection interface device comprises a machine body, a socket is arranged on machine body, a shield is arranged on the front side of the machine body; through holes areformed in the shield, a rotary disc is arranged in the shield, grooves are formed in the end surface of the rotary disc; a wedge-shaped baffle plate is mounted in each groove; first springs are connected between the wedge-shaped baffles and the grooves; one of the grooves is designed to be a communicating groove, and the other grooves are blind grooves; a wedge-shaped hole is formed in the end face of the rotary disc, a push rod is arranged on the shield, the push rod is pressed to drive the rotary disc to rotate unidirectionally through matching of the push rod and the wedge-shaped hole, a torsional spring is connected between the rotary disc and a base body, and the rotary disc can move forwards and backwards along a connecting shaft and can reset under the action of the torsional spring. According to the security protection interface device, the security protection of the computer platform interface can be well realized, and foreign persons are prevented from copying internal information.
Owner:HUANGHE S & T COLLEGE
A UEFI-based computer security startup protection method
InactiveCN105825131BAchieve protectionPrevent tamperingInternal/peripheral component protectionDigital data authenticationPasswordAuthentication server
The invention discloses a computer security startup protection method on the basis of a UEFI (Unified Extensible Firmware Interface). The method comprises the following steps of enabling the UEFI to load a USB (universal serial bus) Key driving program in a DXE (Driver Extension Environment) stage, wherein the operation of whether to load the driving program successfully or not can influence to guide a manager to identify USB Key hardware in a BDS (Boot Device Selection) stage; in the BDS stage, guiding the manager to identify the USB Key hardware, and starting USB Key equipment; in a TSL (Transient System Load) stage, verifying a USB Key serial number, loading an OS loader file in a USB Key to a memory, then calling a dynamic password authentication server in the USB Key to perform secondary authentication, finally performing malicious code scanning on an ESP (EFI system partition) partition by means of calling EFI (Extensible Firmware Interface) safety protection software, preventing a key system file in the ESP partition from being invaded, and guaranteeing the security startup of a computer. The method disclosed by the invention has the advantages that the security of a computer startup procedure is enhanced in a manner of combining software and hardware on the premise of not affecting the normal startup of the computer.
Owner:GUANGDONG UNIV OF TECH
Interface unit for fully homomorphic encryption chip
ActiveCN102694644BRealize encryption and decryptionImplement security protectionCoding/ciphering apparatusCommunication with homomorphic encryptionComputer hardwarePlaintext
The invention discloses an interface unit for a fully homomorphic encryption chip. The interface unit comprises an encryption interface, a decryption interface and a cipher text operation interface. The encryption interface is used for encrypting data of a data owner to generate cipher texts and transmitting the cipher texts to a data processor. The cipher text operation interface is used for receiving the cipher texts from the data processor to operate the cipher texts and transmitting the operated cipher texts to the data owner. The decryption interface is used for receiving the operated cipher texts from the data owner, decrypting the cipher texts to generate plain texts, and transmitting the plain texts to the data owner. The encryption interface comprises a first integer sub-interface and a first real sub-interface, wherein the first integer sub-interface is used for encrypting plain text integers and plain text unsigned integers, and the first real sub-interface is used for encrypting plain text real numbers, plain text floating numbers, plain text double-precision floating numbers and plain text format real numbers. The interface unit for the fully homomorphic encryption chip can complete arithmetic operation, relation comparison operation and logical operation under encryption and can guarantee information safety.
Owner:HUAZHONG UNIV OF SCI & TECH
Water-control type water-return secondary stop safety protector for hydraulic compressor
InactiveCN101551056BImplement security protectionAvoid major safety hazardsEngineering safety devicesAutomatic controlEngineering
Owner:SICHUAN AEROSPACE LONG MARCH EQUIP MFG CO LTD
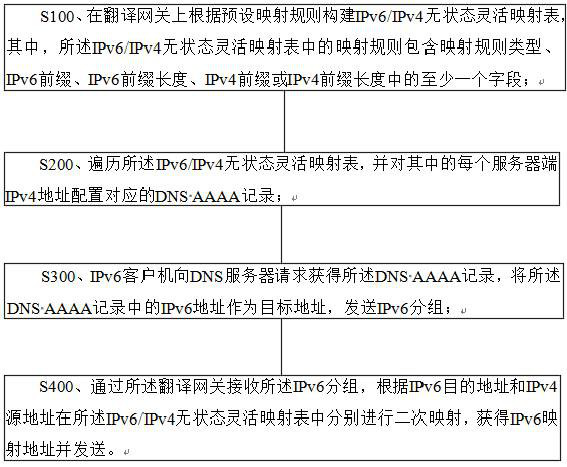
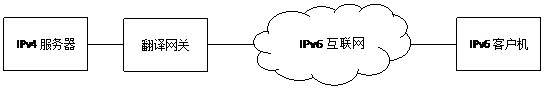
Stateless flexible mapping algorithm for IPv6/IPv4 access
This application relates to a stateless flexible mapping algorithm for IPv6 / IPv4 access. By constructing an IPv6 / IPv4 stateless flexible mapping table on the translation gateway, several fixed mapping tables between specified IPv6 addresses and specified IPv4 addresses are added as needed Items, and merged with the IPv6 / IPv4 mapping algorithm table items stipulated in RFC6052 to realize a unified IPv6 / IPv4 flexible mapping table based on longest prefix matching, which can adapt to various application scenarios and user needs of IPv6 / IPv4 access. The present invention supports hiding the real IPv4 address of the server from IPv6 users, supports IPv4 servers to issue encrypted IPv6 addresses, and realizes security protection. No matter how the IPv4 address of the internal server changes, the externally issued IPv6 address always remains unchanged, maintaining user access to services stability.
Owner:北京英迪瑞讯网络科技有限公司
An ultra-thin vehicle-mounted magnetic levitation flywheel battery and its working method
ActiveCN113422467BAxially takes up little spaceHighly integratedElectric machinesMechanical energy handlingMagnetic bearingElectrical battery
The invention discloses an ultra-thin vehicle-mounted magnetic levitation flywheel battery for electric vehicles and a working method thereof. A motor bracket, an axial magnetic flux motor, a flywheel and an inner stator of a five-degree-of-freedom magnetic bearing are coaxially arranged in a casing from top to bottom. , coil and permanent magnet, the flywheel is composed of continuous upper, middle and lower layers. The middle of the upper ring layer of the flywheel on the upper layer is the upper ring groove, and the axial flux motor is placed in the upper ring groove. The groove, the middle annular cavity and the lower annular groove communicate with each other and house the inner stator, coil and permanent magnet of the five-degree-of-freedom magnetic bearing. The five-degree-of-freedom magnetic bearing is axial magnetic bearing, repulsive magnetic bearing, Torsional magnetic bearing and radial spherical magnetic bearing; adopting the mode of multiplexing magnetic bearings of different properties to realize their complementary advantages, which can not only improve the bearing capacity and control accuracy of the magnetic bearing support, significantly improve the stability of the flywheel, but also effectively compensate for the complex The working conditions lead to the problem of large loss of the control coil.
Owner:JIANGSU UNIV
A software protection method and system
ActiveCN104392151BImprove securityAvoid smallProgram/content distribution protectionExtensibilityOperational system
The invention discloses a software protection method. The method includes the steps: on receiving a software code snippet to be protected and remotely uploaded, a server processes the software code snippet into an intermediate code and stores the intermediate code; on receiving a call request aiming at the software code snippet and remotely transmitted, the server executes the intermediate code according to the call request and returns execution results. The invention further discloses a corresponding software protection system. The software protection method and system has the advantages that software security is higher, no limits on operating systems and hardware occur, and extensibility is high.
Owner:BEIJING SENSESHIELD TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com